Researchers at ESET have identified a cluster of Linux-based backdoors, dubbed WolfsBane, and confidently linked them to the notorious Gelsemium superior persistent threat (APT) group. This China-aligned threat actor, with a documented history dating back to 2014, surprisingly lacks any publicly reported instances of employing Linux malware until the present day. Furthermore, our investigation uncovered another malicious Linux implant, dubbed FireWood, demonstrating the ongoing threat of sophisticated cyberattacks. While it is uncertain whether FireWood is definitively linked to various Gelsemium instruments, its occurrence within the examined archives might simply be fortuitous. Based on our analysis, there is a moderate likelihood that the threat actor behind FireWood may share ties with multiple China-aligned Advanced Persistent Threat (APT) groups, warranting cautious attribution to Gelsemium but acknowledging limitations in our confidence level.
Two notable backdoors, similar to Windows malware used by Gelsemium, are presented as key samples in our VirusTotal archives. While Wolfsbane may have a Linux equivalent in Gelsevirene, Firewood’s connection to Undertaking Wooden remains unclear without further context or explanation. The research revealed a diverse array of instruments linked to Gelsemium’s activities. The primary objective of these discovered backdoors and tools appears to be cyber espionage, targeting sensitive information such as system data, user credentials, and specific files and directories. These sophisticated instruments are engineered to sustain relentless surveillance, quietly executing covert operations while avoiding detection, thereby facilitating prolonged intelligence collection.
As a result, the emergence of APT teams with expertise in Linux malware has become increasingly prominent. The shift is likely attributed to advancements in Windows email and endpoint security, including the widespread adoption of endpoint detection and response (EDR) tools and Microsoft’s decision to disable Visual Basic for Applications (VBA) macros by default. As cyber threats evolve, malicious actors are increasingly targeting vulnerabilities in internet-facing systems, many of which rely on Linux operating systems, prompting concerns about the potential for devastating attacks.
Here is the rewritten text:
In this blog post, our team provides a technical analysis of a Linux-based malware, with a focus on two distinct backdoors that warrant special attention.
- ESET researchers uncovered an extensive archive of Linux samples, harboring two previously unidentified backdoors.
- The primary backdoor, known as Wolfsbane, is a Linux variant of the Windows-based malware Gelsevirine, which is used by the cybercriminal group Gelsemium.
- Its dropper is equivalent to the Gelsemine dropper, integrating a hider rooted in an open-source userland rootkit.
- The second backdoor, known as FireWood, is connected to Undertaking Wooden. A Windows variant of the Project Wooden backdoor was previously employed by the Gelsemium group during Operation TooHash.
- Alongside the identified backdoors, our investigation uncovered additional tools, predominantly internet shells built upon publicly available code.
Overview
In February 2023, an examination of archived files uploaded to VirusTotal revealed samples from Taiwan, the Philippines, and Singapore, likely stemming from an incident response effort following a server compromise. Gelsemium exhibits a concentrated presence in Japanese Asia and the Middle East.
The primary backdoor forms a crucial component in a sophisticated loading chain comprising a dropper, launcher, and ultimately, the backdoor itself. We named this malware WolfsBane. Wolfsbane, as described in both the and sections, serves as a Linux equivalent of Gelsemium’s Gelsevirine backdoor, with its corresponding dropper resembling that of Gelsemine. The origin of our Gelsemium’s name stems from a plausible interpretation of the term wolf-poison grass, as recorded in the report from a certain party who referred to the group as 狼毒草. The genus of flowering plants known as Gelsemiaceae comprises the species that produces toxic compounds such as gelsemine, gelsenicine, and gelsevirine, which we have dubbed the namesake for the three components of this malware family. Previously, we thoroughly examined Gelsevirine and Gelsemine. An integral component of the WolfsBane assault chain is a customised open-source userland rootkit, which is a type of sophisticated software that resides within the end-user’s operating system and conceals its activities.
The second identified backdoor, dubbed FireWood, shares a connection with the Undertaking Wood malware variant monitored by ESET researchers, previously scrutinized in a separate analysis. By 2005, we had successfully tracked the phenomenon back to its roots, observing how it transformed into increasingly nuanced manifestations.
Our analysis of the archives revealed a collection of additional tools, primarily webshells, which enable remote control for an attacker once installed on a compromised server, alongside simple utility tools.
Attribution and connection
We pinpoint the parallels that substantiate our assignment of WolfsBane malware to the Gelsemium Advanced Persistent Threat (APT) group, while also establishing a link between the FireWood backdoor and the Undertaking Wooden malware.
The software program Wolfsbane creates a direct connection to Windows.
It appears to be a Linux variant of the infamous WolfCrypt malware. Given the evident indicators and telltale signs, the attribution of WolfsBane to the Gelsemium Advanced Persistent Threat (APT) group is made with unwavering certainty.
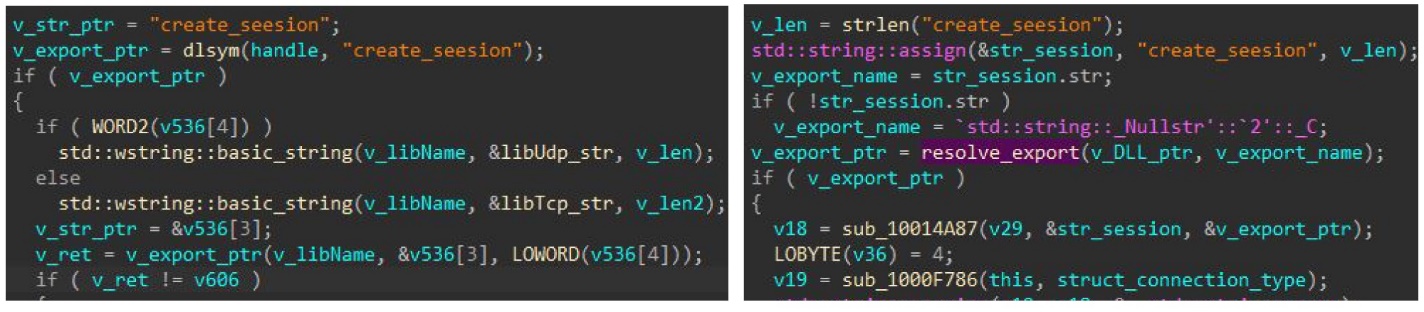
- The Linux and Windows versions each load a custom-embedded library for network communication, featuring separate libraries for distinct protocols utilized. The backdoor exploits the library’s functionalities by invoking its ‘export image’ function, where a noticeable typographical error persists across different iterations (as depicted in Figure 1).
- Each variations use the identical mechanism for executing instructions acquired from the C&C server. The backdoor generates a workstation with hashes derived from the ‘identify’ command, accompanied by suggestions that elucidate its functional capabilities in accordance with predetermined guidelines. We provide additional details within this section.
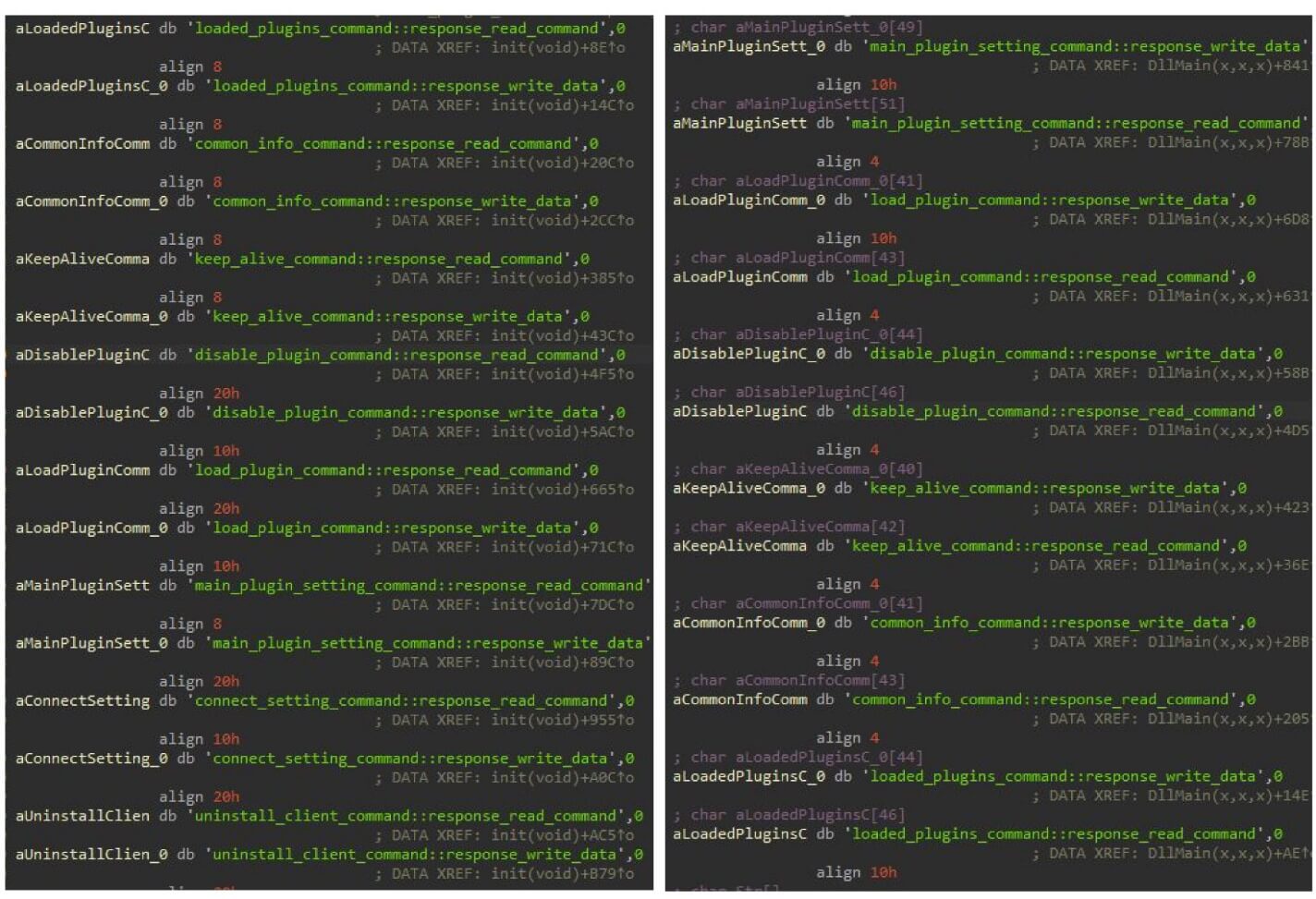
- Each backdoor employs a highly specific configuration setup. While the Linux framework exhibits some absent fields and supplementary ones, numerous area designations remain consistent. The value discovered within this configuration is comparable to those found in all Windows Gelsevirine samples from 2019. Furthermore, the corresponding value patterns in the Linux model configuration exhibit a remarkable alignment with those found in the Gelsevirine samples.
- Researchers at ESET had previously identified this area as a key indicator of compromise associated with the notorious Gelsemium APT group.
FireWood connection to Undertaking Wooden
We’ve identified code correlations between the Firewood malware pattern and a backdoor component used in Operation TooHash, which is linked to the DirectX rootkit developed by group . Researchers at ESET have dubbed this discovered backdoor. These similarities embody:
- The Wooden Wonders of Our Time? While referencing images and mutex identification are essential components in configuring a backdoor, the Firewood backdoor specifically utilizes these elements to facilitate unauthorized access.
- Each sample shares a particular filename extension, such as .txt.
- The TEA encryption algorithm’s implementation with a variable number of rounds exhibits similarity across various examples.
- Each samples use the identical strings within the code answerable for C&C communications, XORed with the identical single-byte key ().
- The networking code within each sample may exhibit a high degree of similarity.
Based on these findings, our assessment indicates near-certainty that FireWood is the Linux evolution of the Undertaking Wood backdoor, solidly linking the two malware variants. While a link between the FireWood backdoor and various Gelsemium instruments remains unsubstantiated, it is plausible that their coexistence in examined archives might be merely fortuitous.
Our confidence in attributing Gelsemium to specific actors is low, and we acknowledge that it could be a software shared among multiple Chinese-language advanced persistent threat (APT) groups, possibly facilitated by a digital quartermaster like those used by other China-aligned teams, as we’ve seen previously.
Technical evaluation
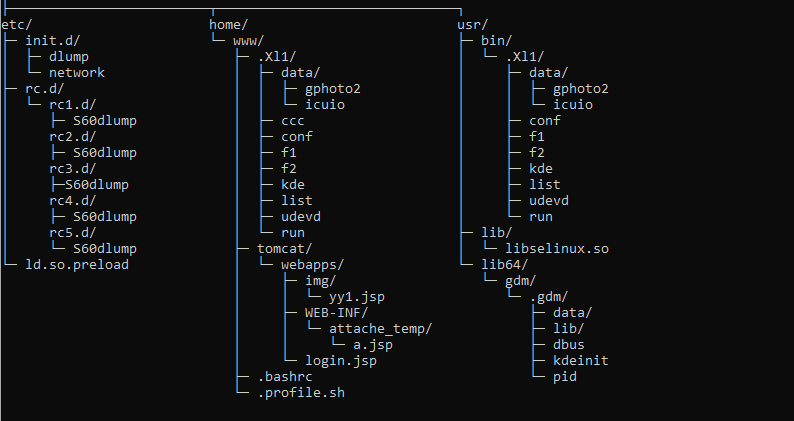
The malware was uploaded to VirusTotal on March 6.th, 2023, from Taiwan. Subsequent archives have been uploaded from both the Philippines and Singapore in addition. Based primarily on the folder structure depicted in Figure 3, it is likely that the objective was to deploy an Apache Tomcat web server running an unnamed Java-based web application.
Preliminary entry
Though concrete proof of the preliminary entry vector is lacking, the presence of webshells (as demonstrated in Desk 1 and detailed elsewhere) and the tactics, techniques, and procedures employed by the Gelsemium APT group recently, allow us to conclude with medium confidence that the attackers likely exploited an unpatched internet utility vulnerability to gain server access.
| Modified webshell. | ||
| webshell. | ||
| Obfuscated JSP webshell. |
Toolset
WolfsBane
The Wolfsbane parts and chain of execution are depicted in Figure 4.
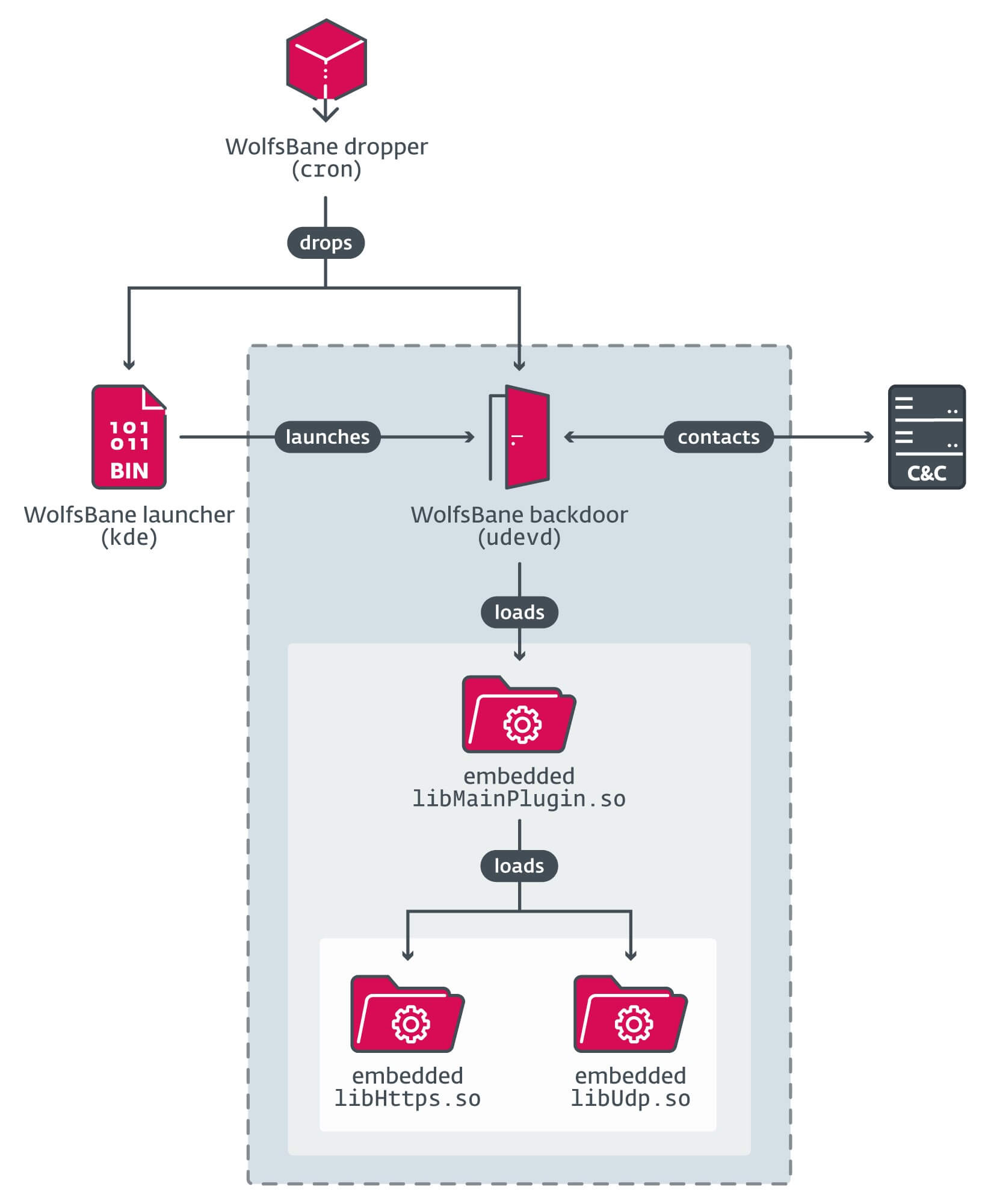
Stage 1: WolfsBane dropper
The malware’s configuration file, disguised as a legitimate . During execution, the malware initially locates the launcher and the primary backdoor within the clandestine listing (designated by the letter ‘l’), which was crafted by the dropper. The `X11` directory appears to have been deliberately named after the widely recognized Unix-based folder identifier.
The dropper subsequently achieves persistence primarily by exploiting vulnerabilities in the system’s configuration and execution context.
If executed as :
- Does the software development kit include the required set of tools for building, testing, and deploying a robust application?
- If current, write the file with the path leading to the subsequent stage (Wolfsbane Launcher) as per the specified entry (refer to Determination 5). This configuration ensures that the launcher operates as a system service, causing records from this folder to be processed during system initialization.
- Disables the safety module by altering the entry within the SELinux configuration file to.
[Unit] Description=Show-Supervisor [Service] Kind=easy ExecStart=<PATH_TO_LAUNCHER_EXECUTABLE> [Install] WantedBy=multi-user.targetComment
If it’s not current, the dropper creates an easy-to-execute bash script that runs the launcher (step 6) in every startup folder, saving the file as ___.
#!/bin/bash /usr/bin/.Xl1/kde
If run as an unprivileged user on a Debian-based system, it:
- Writes the same Bash script to the file,
- The command to install and record data within the user’s residence folder, ensuring that the Wolfsbane launcher starts automatically after the user logs in is:
For various Linux distributions, it generates an identical file and simply returns its path to a dot.
When run with root privileges, the dropper executes the WolfsBane Hider rootkit, injecting the library into every process. This ensures seamless integration, allowing the rootkit to remain hidden from detection.
The dropper, once its task is complete, extracts itself from the disk’s surface before executing the next phase: the launcher.
Stage 2: WolfsBane launcher
Here’s the improved text: A tiny binary, masquerading as a trustworthy entity, is employed to maintain persistence, cleverly concealed to evade detection and ensure continuity of operation. Regardless of institutional techniques, the primary objective is to run a binary that parses its embedded configuration, ultimately triggering the execution of the WolfsBane backdoor from a specified file defined in the configuration.
Stage 3: WolfsBane backdoor
The Wolfsbane backdoor, saved in a file named, initiates its malicious activity by dynamically loading an embedded library and invoking its export function, thereby integrating the core backdoor capabilities. Here is the rewritten text in a different style:
The ‘library’, dubbed by its creators, bears striking resemblance to the mechanisms employed within the Windows framework of the Gelsevirine malware.
Like its Windows counterpart, the Wolfsbane backdoor leverages various embedded libraries to facilitate network communication. Among the samples we’ve gathered are named ‘and’, with each exporting an image identical to that found in the Windows version of the Gelsevirine TCP module. These shared libraries present C&C communications through UDP and HTTPS protocols, respectively.
The backdoor encrypts the library using the RC4 algorithm, obtaining the key from a value specified in the configuration, and then saves it as a file with a ‘. Upon subsequent runs, the backdoor initially verifies the presence of this specific file; if it’s found, the encrypted contents are decoded and utilized in place of the preloaded configuration. This mechanism enables real-time updating of the backdoor by seamlessly overriding the underlying file.
The WolfsBane backdoor makes use of the same strategy to its Home windows counterpart for executing instructions acquired from its C&C server.
WolfsBane Hider rootkit
The Wolfsbane backdoor leverages a customized open-source userland rootkit to conceal its activities. The rootkit leverages the operating system’s preload mechanism to load itself ahead of other libraries by appending its path to the sysctl configuration file, thereby enabling it to hook privileged processes.
The Wolfsbane Hider rootkit exploits several fundamental C library functions akin to read(), write(), and open(). While these features leverage their distinct strengths, they effectively screen out any repercussions linked to the notorious WolfsBane malware. Unlike the distinctive BEURK rootkit that leverages an embedded configuration file for filtering, WolfsBane’s creators deliberately kept the default configuration intact while altering the source code to eliminate information tied to hardcoded filenames of the malware executables. The BEURK rootkit’s distinctive feature of concealing community traffic is strikingly absent from its offerings.
FireWood backdoor
The Firewood backdoor, contained in a file named _, is a Linux operating system continuation of the notorious Undertaking Wooden malware, infamous within the cybersecurity community. The analyzed code suggests that the file is a kernel driver module functioning as a rootkit, masking and concealing process activity. The FireWood malware’s backdoor component interacts with the operating system’s kernel-mode drivers using.
The Firewood framework employs a configuration file encrypted using single-byte XOR encryption, where the decryption key is also a single byte in length. The configuration file’s construction is elaborately described in Desk 2.
| Unknown timestamp. | ||
| Placeholder for backdoor working listing. | ||
| C&C IP deal with (if 0.0.0.0, the backdoor makes use of the C&C area). | ||
| C&C area. | ||
| Spoofed course of identify. | ||
| TEA encryption key. | ||
| Connections Day; every four days, a backdoor link appears. | ||
| Delay time. | ||
| Connection time (in minutes). |
FIREWOOD reconfigures its courses primarily based on valuation in the setup.
During startup, the system generates a file with no extension. During startup, all files with an extension in the specified directory are parsed, and any commands listed in the configuration entry are executed. The contents of the file may be reviewed in Determine 7.
[Desktop Entry] Kind=Utility Exec=<PATH/TO/OWN/EXECUTABLE> Hidden=false NoDisplay=false X-GNOME-Autostart-enabled=true Identify[en_US]=gnome-calculator Identify=gnome-control Remark[en_US]=
FireWood communicates with its C&C server through TCP, as laid out in its configuration. Knowledge is securely encoded using the TEA (Tiny Encryption Algorithm) protocol, with adjustable round counts for enhanced protection. The FireWood configuration file furnishes the encryption key and number of rounds, as depicted in Table 2.
The construction of dispatched and acquired messages is illustrated in Figure 8. The outcome of executing a command depends on its type; typically, indicates successful execution, whereas denotes an error occurred.
Struct knowledge { DWORD commandIDOrReturnCodeValue; std::vector knowledgeData; };
The backdoor enables execution of various instructions, as outlined in Desk 3.
| Obtain an executable file from the C&C to and execute it with the parameter. | |
| The `operate` command is not a standard Unix shell command. It’s possible that you meant to type `execute`, which is not a valid command either. However, I’m assuming you want to execute a shell command using the `!` (exclamation mark) operator. If so, here’s an example: “`shell This will run the `ls -l` command as if it were entered in the terminal. | |
| Configure the connection time value within your settings. | |
| Develop a comprehensive understanding of implementing the kernel module by diving into its fundamental concepts and practical applications. | |
| Change delay time in configuration. | |
| Configure connection day worth in accordance with your organization’s needs. | |
| Clear up and exit. | |
| Maintain a detailed log of the preferred directory’s specifications. | |
| Exfiltrate specified file to C&C server. | |
| Delete specified file. | |
| Rename specified file. | |
| Run the specified file using the operate command. | |
| Obtain file from C&C server. | |
| Exfiltrate specified folder to C&C server. | |
| Loads a specified kernel module or shared library into the system’s memory. | |
| Remove a designated kernel module or shared library from operation to prevent interference with system functionality. | |
| Modify specified file timestamp. | |
| Delete specified listing. | |
| Learn content material of the desired file and ship it to the C&C server. | |
| Search for the specified file within the designated directory as dictated by the command. |
Different instruments
Two previously undiscovered instruments were unearthed from the archives, potentially linked to the Gelsemium exercise: an SSH password stealer and a compact privilege escalation tool.
The SSH password stealer is a malicious tool rooted in open-source software, reconfigured to capture users’ SSH credentials necessary for authenticating access to a server. The adversaries replaced the authentic SSH client binary with a trojanized version. While functioning as a conventional SSH client, this tool stores all authentication details in a secure format within a file.
The privilege escalation tool is a compact executable, denoted by `, which straightforwardly amplifies user rights by configuring the execution context’s UID and GID to ` and subsequently runs a program located at a path provided as an input argument. To execute this method, users must possess root privileges in order to grant the executable SUID permissions beforehand, transforming it into a tool that preserves existing privileges rather than seeking new ones.
Webshells
A malicious Java-based web shell, dubbed “the,” has been discovered executing attacker-controlled code from compromised websites. The payload—a Java class file—has been base64-encoded and transmitted as part of an HTTP POST request’s parameter. This innovative webshell enables remote access to terminals, files, and databases.
The Icesword JSP webshell originates primarily from Chinese-language online forums. The IceSword JSP webshell features a fully functional graphical user interface embedded in its server-side code, enabling it to render a GUI directly within the attacker’s browser. The operating system isn’t intentionally obscured and gathers essential system information, carries out low-level system commands, and manages file interactions with precision. The malware also exploits its access to execute malicious SQL queries on any connected databases residing on the vulnerable host.
The webshell, akin to its obfuscated counterpart, conceals a binary Java payload that is encrypted using Advanced Encryption Standard (AES) and then base64-encoded for transmission. The payload is provided as input to the function through a parameter. The complexity includes misleading comments, backslash-escaped Unicode characters that hinder comprehension, and unpredictable variable and function names. The final outcome, base64-encoded and seamlessly integrated into the response body, is then disseminated to the malicious actors.
Conclusion
The report delves into the intricate details of the Linux malware toolset, tracing its links to Windows malware specimens exploited by the notorious Gelsemium APT group. Now that we’ve honed in on the capabilities of WolfsBane and FireWood backdoors, and scrutinized the WolfsBane execution chain and its deployment of a userland rootkit. Notably, this report serves as the principal public document detailing Gelsemium’s adoption of Linux malware, signaling a significant transformation in their tactics.
Malware developers are increasingly adopting Linux-based techniques within the advanced persistent threat (APT) community, suggesting a significant shift in their approach. As we see it, this enhancement is largely due to advancements in electronic mail security and endpoint protection measures. As the proliferation of EDR options accelerates and Microsoft’s standard practice of disabling VBA macros takes hold, malicious actors are being forced to explore alternative entry points.
As a result, the vulnerabilities inherent in internet-facing infrastructure, particularly those with Linux-based foundations, are increasingly under scrutiny. Due to their increasing prominence, these Linux techniques have become the newest and most sought-after targets for malicious actors.
IoCs
A comprehensive log of indicators of compromise (IoCs) and samples may potentially reside within.
Recordsdata
| Linux/Agent.WF | FireWood backdoor. | ||
| Linux/Rootkit.Agent.EC | WolfsBane Hider rootkit. | ||
| Linux/Agent.WF | WolfsBane backdoor. | ||
| Linux/Agent.WF | WolfsBane launcher. | ||
| Linux/Agent.WF | WolfsBane dropper. | ||
| Linux/Agent.WF | Privilege escalation helper software. | ||
| Linux/SSHDoor.IC | Trojanized SSH shopper. | ||
| Java/Agent.BP | JSP webshell. | ||
| Java/JSP.J | icesword webshell. | ||
| Java/Webshell.AM | Modified AntSword JSP webshell. | ||
| Linux/Agent.WF | VirusTotal archive. | ||
| Linux/Agent.WF | VirusTotal archive. | ||
| Java/Agent.BP | VirusTotal archive. | ||
| Linux/Rootkit.Agent.EC | VirusTotal archive. | ||
| Linux/Rootkit.Agent.EC | VirusTotal archive. | ||
| Linux/Rootkit.Agent.EC | VirusTotal archive. | ||
| Linux/Rootkit.Agent.EC | VirusTotal archive. | ||
| Linux/Agent.WF | VirusTotal archive. |
Community
| N/A | N/A | 2020-08-16 | WolfsBane backdoor C&C server. | |
| N/A | N/A | 2022-01-26 | FireWood backdoor C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Purchase Infrastructure: Domains | Gelsemium has acquired domain registrations through strategic partnerships with reputable business suppliers. | ||
| Purchase Infrastructure: Server | It appears that Gelsemium likely sources virtual private servers (VPS) from business suppliers. | ||
| Develop Capabilities: Malware | The Gelsemium strain of malware has been engineered to create highly specialized and tailored infections. | ||
| Command-Line Interface: Unix Shell | The Gelsemium malware has been found to have the capability to execute Linux shell commands. | ||
| Can a simple shell script be used to automate system initialization tasks in Windows and Unix/Linux systems? | The Wolfsbane launcher remains persistently installed on the system via its integration with RC startup scripts. | ||
| The systemd service course will consist of the following topics: ? Introduction to systemd | The Wolfsbane dropper can dynamically create a novel system service for persistent command and control (C2). | ||
| Hijacking the Execution Path: A Deeper Dive into Dynamic Linker Manipulation | The Wolfsbane Hider rootkit exploits the preload method’s vulnerability. | ||
| The boot autostart execution and logon autostart execution are two distinct processes that involve the activation of applications at different stages of system startup. The primary distinction between these two phases lies in their timing, with boot autostart happening before logon. During the boot process, the Linux system executes scripts and programs defined by XDG Autostart entries to perform tasks such as setting up networking or launching services. These actions occur prior to user login, allowing the system to initialize and prepare itself for subsequent interactions. In contrast, logon autostart execution takes place after a user has successfully logged in to their account. At this stage, the system executes additional scripts and programs specified by XDG Autostart entries to perform tasks such as launching desktop environments or starting up specific applications. Understanding the differences between these two autostart phases is crucial for administrators seeking to effectively manage and configure their Linux systems, including those requiring specific services or applications to be launched during startup or at user logon. | The FireWood backdoor continues to persist on the system by covertly generating an autostart file. | ||
| When you log in to a Linux system, certain commands are executed automatically from specific files. These files include .bash_profile and .bashrc. The .bash_profile file is read when a new shell session begins. This typically happens when you start a new terminal window or log in to the system. The .bashrc file, on the other hand, is read whenever a new interactive shell process starts, which can occur when you open a new terminal window or type “bash” from another shell. The primary difference between these two files lies in their execution points. .bash_profile is triggered only once per login session, whereas .bashrc is triggered every time a new interactive shell is started. As a result, if you have commands that need to run each time you start a new terminal window or log in to the system, place them in your .bashrc file. However, if you have commands that should only run once per login session, put them in your .bash_profile. For instance, setting environment variables or aliasing frequently used commands could be placed in either .bash_profile or .bashrc, depending on your specific needs and preferences. | The Wolfsbane malware exploits multiple shell configuration files to achieve persistence. | ||
| The Abuse of Elevation Management Mechanisms: setuid and setgid | The Gelsemium exploit leverages a vulnerability in software that utilises setuid and setgid permissions to maintain elevated privileges. | ||
| Indicator Removing: File Deletion | The WolfsBane dropper removes itself. | ||
| Indicator Removing: Timestomp | The Firewood backdoor includes a command to alter the modified access time (MAC time) of files. | ||
| Indicator Removing: Clear Persistence | The Wolfsbane dropper self-removes from disk. | ||
| Undiscovered Files: Concealed Data and Folders | The two backdoors, Wolf’s Bane and Fire Wood, are concealed within secret directories. | ||
| Linux and macOS have distinct file permission systems. In Linux, permissions are determined by the owner, group, and other users. The command `chmod` is used to modify these permissions. To change permissions in Linux, you can use the following syntax: “` The `[permissions]` field should contain a three-digit number where the first digit represents the owner, the middle digit the group, and the last digit other users. The values 1, 2, or 3 correspond to execute, write, and read permissions, respectively. For example: * `chmod 755 file.txt` gives owner full control, group read-execute permission, and other users read-only permission. On macOS, you can use the `chmod` command with similar syntax. However, the default permissions are set according to the system’s security settings. | The Wolf’s Bane dropper leverages Linux chmod directives to dynamically modify the permissions of executed binaries upon deployment. | ||
| Data Hiding in Plain Sight: Uncovering Hidden Payloads | The Wolf’s Bane dropper features all payloads stored in a compact, embedded format, awaiting extraction. | ||
| Rootkit | Malware such as Wolfsbane and Firewood exploit rootkits to ensure their covert presence on infected systems. | ||
| The art of masquerade has been an intriguing concept for centuries, allowing individuals to conceal their true identities and blend in with the anonymity of a mask. However, with the rise of digital technology, this phenomenon has taken on a new form as people choose to hide behind pseudonyms, handles, or profiles online. In today’s professional setting, masquerading can manifest in various ways. A person may adopt a different persona for business purposes, creating an illusion that is far removed from their real-life identity. This could be done to protect personal information, maintain confidentiality, or simply to present themselves in a more polished and professional light. But what are the implications of this digital masquerade? Is it a harmless ruse, allowing individuals to showcase their expertise and build a reputation without compromising their privacy? Or does it foster distrust and undermine authenticity in our online interactions? The answer lies in understanding the motivations behind each individual’s decision to masquerade. | The Gelsemium malware names its files and directories according to genuine system resources. | ||
| System Data Discovery | The Wolf’s Bane dropper utility provides a concise enumeration of system data. | ||
| File and Listing Discovery | The Firewood backdoor enables searching within a machine’s file system for specific files and directories. | ||
| Enter Seize | A malicious script captures unsuspecting users’ login credentials over SSH. | ||
| Exfiltration Over C2 Channel | The FireWood backdoor exfiltrates collected knowledge using C&C communications. |

