A severe safety vulnerability has been present in in style stalkerware apps, exposing the delicate private data and communications of hundreds of thousands of individuals.
Stalkerware is a kind of spy ware, ceaselessly used to spy on each message despatched or acquired by a romantic associate, be taught who they’re talking to on their telephone, be taught their location, or view the photographs they’ve taken.
Though stalkerware is ceaselessly marketed as a approach to monitor your youngsters’s or workers’ behaviour on-line, or to maintain your loved ones secure, the truth is that it’s usually jealous companions or these with unhealthy curiosity in a person who find yourself buying such apps and putting in them on their goal’s units.
It has ceaselessly been the case that victims of home abuse are the targets of stalkerware, which regularly makes an attempt to cover its presence on a compromised smartphone.
So it’s extremely comprehensible that curiosity could be piqued when a safety researcher unearthed a safety vulnerability current within the Cocospy and Spyic phone-monitoring apps.
As TechCrunch stories, the flaw has leaked the e-mail addresses of people that signed-up for Cocospy or Spyic, with the intention of planting the app on one other particular person’s system covertly.
In response to the nameless researcher, Cocospy is among the largest recognized stalkerware operations on the planet, with nearly 1.8 million registered customers. Spyic, which shares its IT infrastructure with Cocospy, has 875,000 registered customers.
Each apps have been linked to a Chinese language cellular app developer, who has up to now remained silent concerning the safety gap and on the time of writing haven’t resolved the difficulty.
It is laborious to really feel an excessive amount of sympathy for the purchasers of stalkerware who’ve had their particulars leaked on this approach. Most of our consideration ought to in all probability be directed in direction of these harmless people who have no idea that their units are being spied upon.
And it is with them in thoughts that it is refreshing to share with them a easy approach to inform if Cocospy or Spyic have been put in on their Android units.
As TechCrunch describes, getting into the Android telephone app, typing ✱✱001✱✱ on the keypad, after which presssing the “name” button will make the stalkerware apps seem on-screen if they’re put in.
This performance was constructed into the stalkerware to permit the one that planted the apps to regain entry on their sufferer’s units – however will also be utilized by the sufferer to find out if the spy ware has been put in.
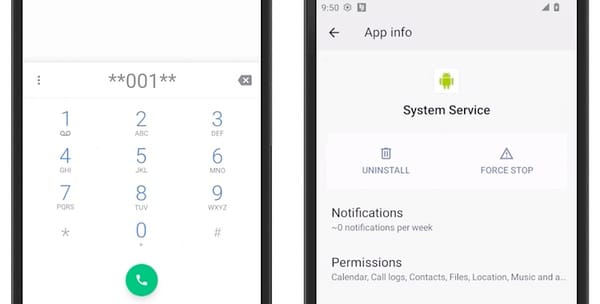
Each Cocospy and Spyic disguise themselves as a generic-looking app known as “System Service.”
In case you are involved about stalkerware, remember to learn the EFF information to surveillance self-defence.

