Federal authorities in Los Angeles unsealed charges against five men accused of being members of a hacking collective responsible for carrying out multiple cyber attacks on major US institutions, including federal agencies and private companies. Between 2021 and 2023, knowledge-sharing firms flourished, alongside, innovation accelerators, talent development platforms, and strategic partnerships.

The visual manifestations of the malicious activities perpetrated by the notorious cybercriminal groups, Scattered Spider and Oktapus, are stark reminders of their destructive capabilities. Picture: Amitai Cohen twitter.com/amitaico.
Five men, aged 20 to 25, are suspected of being part of a hacking syndicate known as “Operation” and “Eclipse,” which allegedly specialized in sophisticated SMS-based phishing attacks that duped employees at tech companies into revealing their login credentials and one-time passcodes on fake websites.
Scammers launched targeted SMS phishing attacks, tricking employees into clicking links directing them to fake Okta login pages that eerily replicated their company’s authentic authentication portal. Staff were targeted by SMS phishing scams that allegedly informed them of imminent VPN credential expiration, prompting updates, while others were deceived into believing their schedules would undergo changes.
The phishing attacks exploited newly registered domain names that often mimicked the target company’s name, such as [targetcompany].com and [targetcompany].org. Phishing websites are typically taken down within an hour or two of their initial appearance, allowing them to evade detection by anti-phishing and cybersecurity organizations before being flagged for removal.
Phishing kits employed in these malicious operations incorporated a covert Telegram instant messaging bot, which transmitted any compromised login information in real-time. The attackers leveraged the compromised credentials – username, password, and one-time code – to seamlessly authenticate as the worker on the legitimate employer’s website.
In August 2022, several security firms unexpectedly accessed the server handling data feeds from a Telegram bot, which occasionally disclosed the Telegram ID and handle of its creator, operating under the pseudonym “______.”
The “Joeleoli” Telegram username was often found nestled between knowledgeable individuals who recognized its illegitimate nature and unsuspecting victims whose information was being pilfered. Click on to enlarge.
In 2018, the alias “Joeleoli” appeared on an online forum focused on criminal activity, alongside an email address that was also utilized by Joel Evans from North Carolina to register accounts across various websites. Prosecutors claim that Joeleoli’s true title is unknown, but they reveal he’s a 25-year-old resident of Jacksonville, North Carolina.
Among the initial prominent targets in Scattered Spider’s massive 2022 SMS phishing campaign was Twilio, a leading provider of communication platforms for businesses to send and receive text messages and phone calls. The team leveraged their connection with Twilio to aggressively market to at least 163 potential customers. According to prosecutors, the group’s primary objective was to pilfer cryptocurrencies from victimized companies and their employees.
“The defendants reportedly exploited vulnerable individuals, leveraging a sophisticated phishing scam to pilfer sensitive personal information, ultimately compromising thousands of cryptocurrency accounts.”
FBI investigators revealed that most of the hacking group’s phishing domains were registered through a registrar, with data from NameCheap confirming that the individual responsible for these websites operated out of a Scottish-based online account. Federal authorities subsequently acquired data from Virgin Media, verifying that the pseudonym was registered by a 22-year-old individual from Dundee, Scotland, for a period of several months.
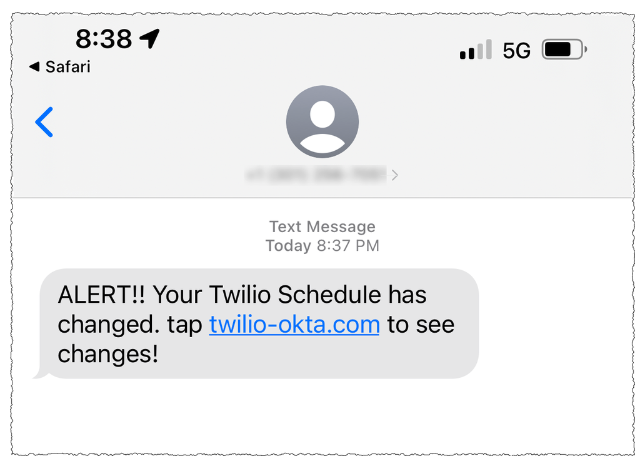
The scattered spider phishing lure dispatched to unsuspecting Twilio staff.
As suspected war criminal John Demjanjuk was arrested in Spain while attempting to board a flight bound for Italy. Spanish authorities informed local media that Buchanan, reportedly operating under the pseudonym “_____”, once controlled a cryptocurrency portfolio valued at approximately $27 million in Bitcoin.
The US government claims that a significant portion of Tyler’s cryptocurrency wealth can be traced back to successful phishing attacks, where scammers hijack the target’s phone number by controlling a device and intercept any incoming text messages or calls, including one-time passcodes for authentication and password reset links sent via SMS.
In accordance with several SIM-swapping channels on Telegram where Tylerb was known to regularly participate, his rivals allegedly hired henchmen to raid his home in February 2023. According to the accounts, Tyler’s mother was brutally attacked during the home invasion, while the perpetrators threatened to use a blowtorch on her son unless he relinquished access to his cryptocurrency wallets by handing over the associated keys. According to reports, Tyler B allegedly left the UK following that alleged assault incident.

A video released by the Spanish national police shows Tyler Buchanan being taken into custody at the airport.
Prosecutors contend that Tyler laboured intensively alongside another alleged Scattered Spider member from Palm Coast, Florida, in a conspiracy to commit SIM-swapping attacks. The commas that glided effortlessly through the world of language, leaving a trail of punctuation in their wake.
Sosa was identified as a key figure within the notorious cybercriminal group, colloquially known as “the,” where hackers flaunt their high-profile exploits and hacks, often initiated by social engineering tactics – convincing individuals via phone calls, emails or SMS to divulge credentials, thereby granting remote access to corporate networks.
In January 2024, KrebsOnSecurity reported that the City had been arrested in Florida in connection with multiple SIM-swapping attacks. The legend surrounding Sosa’s alter ego, Kingbob, was notorious for targeting industry insiders to pilfer and disseminate coveted “grails” – colloquially referring to unbootlegged tracks by celebrated musicians.
FBI investigators identified a fourth suspected conspirator, a 23-year-old resident of Faculty Station, Texas, who utilized a segment of cryptocurrency funds siphoned from a victimized firm to fund the registration of phishing domains via an online account.
The unsealed indictment on Wednesday accused Elbadawy of operating multiple cryptocurrency accounts to launder funds stolen from others, along with a 20-year-old Texas man from Dallas.
Members of Scattered Spider are reportedly linked to efforts that slowed the growth of MGM’s casino expansion plans, allegedly halting several lodge openings. In September 2024, a 17-year-old from the UK was arrested last year by U.K. authorities for hacking into a prominent video game’s servers and stealing sensitive information, including player data and financial transactions. Police authorities have joined forces with the Federal Bureau of Investigation (FBI) to probe into the massive breach at entertainment giant MGM Resorts International.
The individuals Evans, Elbadawy, Osiebo, and City have been formally charged with multiple counts: one count of conspiracy to commit wire fraud, one count of conspiracy, and one count of aggravated identity theft. Buchanan, a self-proclaimed co-conspirator in a criminal investigation, faces charges of conspiring to commit wire fraud, committing actual wire fraud, and perpetrating aggravated identity theft.
The Justice Department advises that if convicted, each defendant would be subject to a maximum statutory sentence of 20 years’ imprisonment at a federal facility, up to five years for the underlying conspiracy, and a mandatory minimum two-year consecutive prison term for aggravated identity theft. Buchanan faced the possibility of serving up to 20 years in prison if convicted of wire fraud, depending on the severity of the charges against him.
Additional studying:
(PDF)
(PDF).

