ESET Analysis
ESET researchers uncovered a previously unknown vulnerability in Telegram for Android, allowing hackers to transmit malicious data disguised as movie files.

ESET researchers discovered a zero-day exploit targeting Telegram for Android, initially posted on an underground forum on June 6, with its value remaining undisclosed.th, 2024. Attackers exploiting the EvilVideo vulnerability can disseminate malicious Android payloads via Telegram channels, teams, and chats, disguising them as multimedia content.
Upon investigating the exploit, we found a vulnerability that allowed us to delve deeper into its workings and submit a report to Telegram on June 26.th, 2024. On July 11thThey subsequently released a patch that addresses the vulnerability in Telegram versions 10.14.5 and higher.
The video demonstrates and rationalizes the EvilVideo vulnerability, specifically highlighting its potential impact on unsuspecting users who may fall prey to malicious attacks.
- On June 26thIn January 2024, a clandestine online forum exposed a commercial offering a zero-day exploit specifically designed to target Telegram for Android.
- The vulnerability was dubbed EvilVideo and we promptly disclosed our findings to Telegram’s security team, who promptly addressed the issue with a patch released on July 11.th, 2024.
- Unpatched versions of Telegram for Android permit malicious actors to deliver malevolent payloads disguised as video content via EvilVideo.
- The vulnerability exclusively affects Android Telegram versions 10.14.4 and prior.
Discovery
We found the exploit being advertised on a dark web forum; refer to Figure 2.
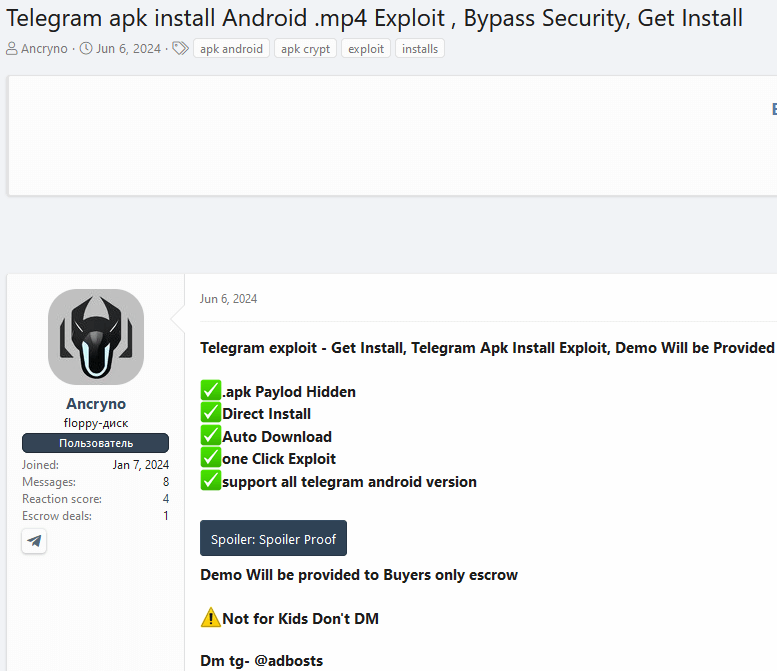
The vendor publicly demonstrates the exploit’s effectiveness by sharing screenshots and a video showcasing its functionality within a publicly accessible Telegram channel. We have successfully established the channel, despite the existing exploit still being available. With this access, we were able to inspect the payload up close.
Evaluation
The evaluation of the exploit confirmed its efficacy on Telegram versions 10.14.4 and below. We suspect that the custom payload is likely created using Telegram’s Application Programming Interface (API), as this allows developers to programmatically send specifically designed multimedia content to Telegram chats or channels.
Without further exploitation, the vulnerability appears to rely on an attacker’s capacity to craft a payload that displays an Android application as a multimedia preview rather than a binary attachment. As soon as the malicious payload is shared in the chat, the malware masquerades as a 30-second video.
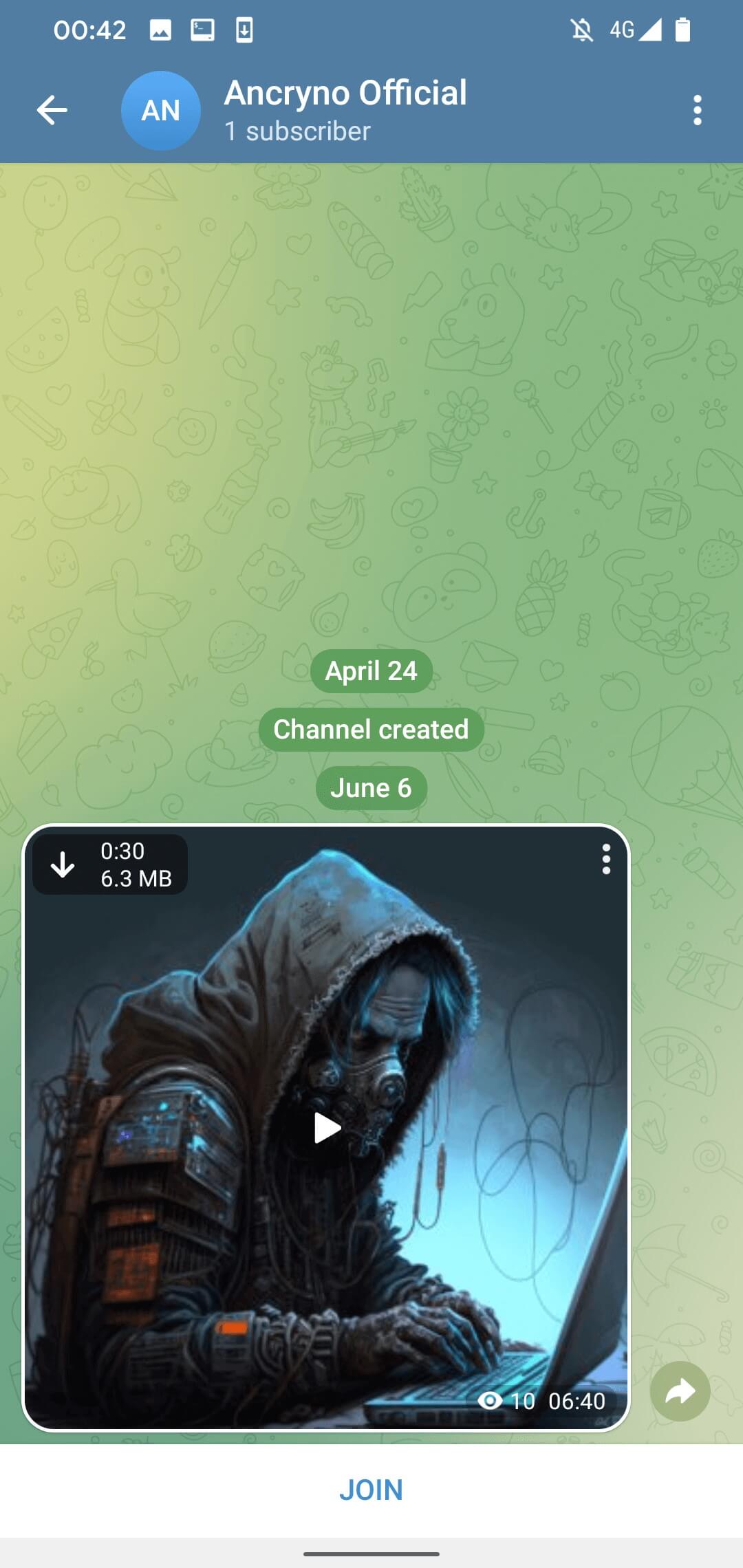
By default, media information obtained through Telegram is set to be retrieved automatically. When customers enable this option, they’ll unwittingly download and initiate the malicious payload upon opening the associated dialogue box where it was initially disseminated? The manual disabling option allows for continued payload downloading; when enabled, users can still access the content by tapping the “Obtain” button located at the top-left corner of the shared video, as depicted in Figure 3.
When attempting to play a video in Telegram, users may encounter an error message indicating that playback is not possible, with the suggestion to utilize an external player (refer to Figure 4). We uncovered a genuine Telegram alert embedded in the source code of the official Telegram for Android application, confirming its authenticity rather than being manipulated by a malicious payload.
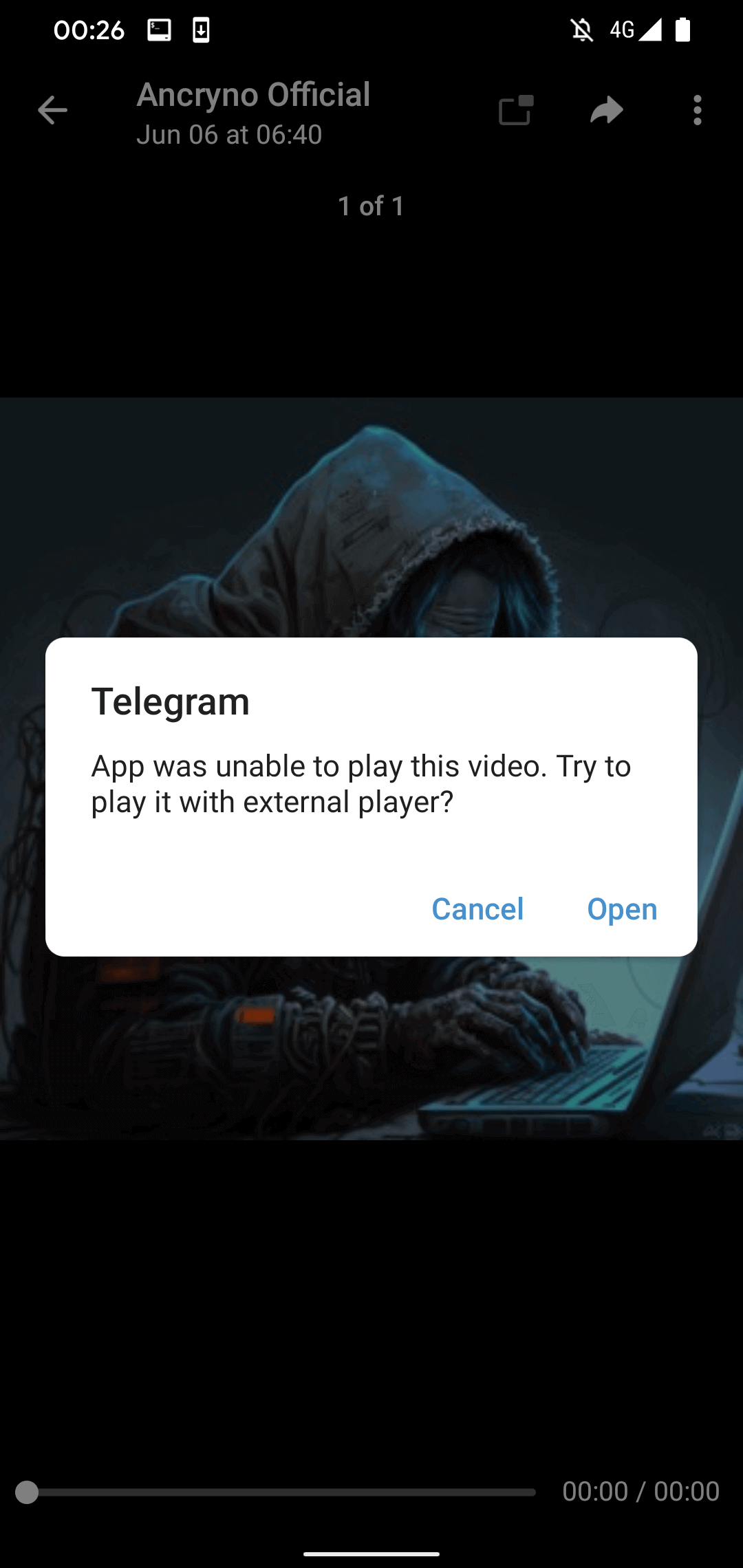
If the user taps the Open button within the displayed message, they will be prompted to install a malicious app masquerading as the supposed external participant. Before proceeding, Telegram may prompt you to grant permission for installing unauthorized apps.
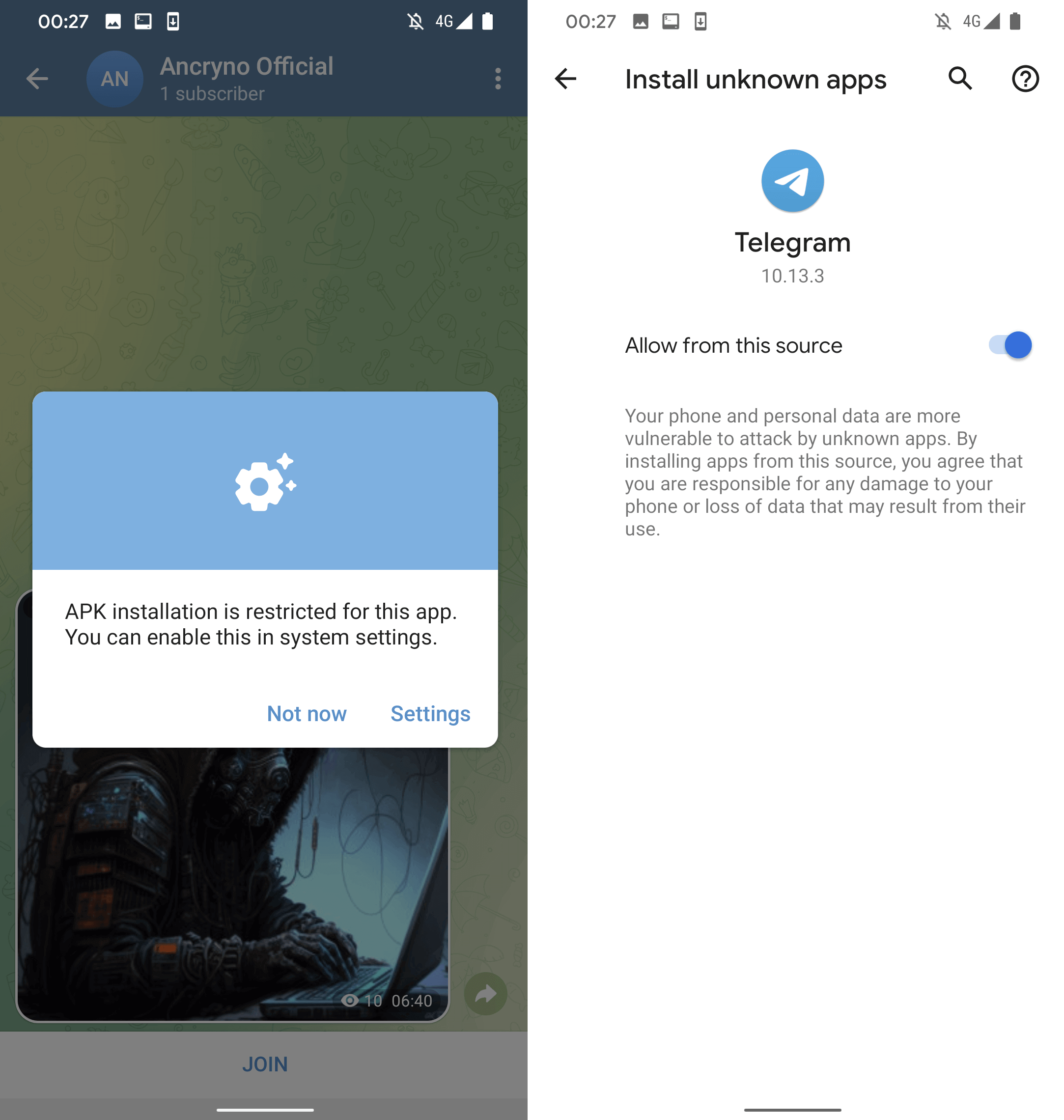
Because the malware’s disguise as a benign video file is so convincing, users at this level have already unwittingly downloaded it. The cleverly disguised malware masquerades as a video due to the inherent characteristics of the vulnerability, rather than any modification to the malicious application itself, suggesting an exploit of the attack vector may have been successful. The malicious app’s setup request could be detected in Figure 6.
Regrettably, our attempts to reproduce the vulnerability were unsuccessful, leading us to solely verify and document the pattern disclosed by the vendor.
Telegram Internet and Desktop
Notwithstanding its primary purpose being tailored specifically for Telegram for Android, we endeavored to test its performance across various Telegram platforms. Upon examining Telegram’s Internet shopper and Desktop shopper for Windows, we found that, as expected, the exploit was ineffective against both applications.
Upon attempting to view a “video” in the context of Telegram’s internet platform, the customer encountered an error message advising them to open the video using the desktop application instead (see Figure 7). Downloading the connected file manually revealed its title and filename to be . As the APK file was indeed a true Android executable binary, Telegram’s mistaken classification of it as an MP4 file thwarted the exploit’s effectiveness; conversely, had the attachment possessed the correct .apk extension, success would have been assured.
A similar anomaly arose when downloading the Telegram Desktop client for Windows: the file was saved as “telegram_desktop_windows_(version number).apk”, effectively disguising a binary executable file with an Android package manager extension. Although an attacker might craft a Windows executable masquerading as an Android APK, the file would still be treated as a multimedia file, rendering the exploit ineffective.

Menace actor
Despite the anonymity surrounding the risk actor, our investigation uncovered another suspicious service being offered by them, as revealed through the Telegram channel’s discussion forum post shared by the vendor. The actors have leveraged the same clandestine online forum to market an Android-based cryptocurrency service, claiming it is fully undetectable since January 11.th, 2024. The discussion board posted on Determine 8.
Vulnerability report
After uncovering the EvilVideo vulnerability on June 26ththBy January 2024, we had adopted a new strategy and promptly reported it to Telegram, yet unfortunately received no response within a reasonable timeframe. On July 4, we reiterated our report of the vulnerability.thTelegram contacted us on the same day to confirm that their team was indeed looking into EvilVideo. They successfully deployed version 10.14.5 of Transport Model on July 11.thSKIPPED
The vulnerability impacted all versions of Telegram for Android up to and including 10.14.4; it was subsequently patched in version 10.14.5. We have confirmed that the chat’s multimedia preview correctly identifies the shared file as a utility, specifically Determine 9, rather than a video.

Conclusion
A zero-day vulnerability in Telegram for Android has been discovered and is currently being traded on an online black market forum. The vulnerability exploited allows attackers to transmit malicious payloads disguised as multimedia content via Telegram chat. When attempting to stream a video, users are often prompted to download and install a third-party application that, unbeknownst to them, contains malware. Unfortunately, the vulnerability had been exploited as of July 11.thIn January 2024, following our formal complaint to Telegram,
IoCs
A comprehensive digital repository, such as a centralised database, could house a complete record of Indicators of Compromise (IoCs) and samples.
Information
| Teating.apk | Android/Spy.SpyMax.T | EvilVideo payload. |
Community
| Administrator Beam Cable System | 2024‑07‑16 | C&C server of EvilVideo payload. |
MITRE ATT&CK methods
This desk was constructed utilizing of the MITRE ATT&CK cell methods.
| Exploitation for Preliminary Entry | A newly discovered vulnerability, dubbed EvilVideo, poses a significant risk as malicious Android malware can exploit it to gain initial system access. | ||
| Exploitation for Shopper Execution | The Evil Video vulnerability deceives victims into installing a malicious application that disguises itself as a multimedia file. |

