Researchers at ESET have identified a newly emerging Rust-based toolkit linked to the distribution of Embargo ransomware. The ransomware threat actor Embargo emerged onto the scene in June 2024, initially identified by cybersecurity researchers at ESET.
ESET has introduced the latest toolkit, featuring a loader and EDR (Endpoint Detection and Response) killer – dubbed MDeployer and MS4Killer, respectively. Notably, MS4Killer stands out due to its tailored compilation for each individual’s unique environment, concentrating exclusively on carefully selected security settings. Instruments written in Rust form part of the Embargo group’s arsenal, serving as their chosen language for developing ransomware.
- Embargo continues to explore and evaluate emerging Rust-based technologies, expanding its toolkit capabilities.
- Despite exhibiting signs of deployment, lingering issues, bugs, and residual remnants suggest that these tools remain under active development.
- Malicious actors exploit vulnerabilities in Protected Mode to deliberately circumvent security safeguards.
- With precision-crafted tools tailored to each individual’s unique needs, Embargo provides compassionate care for those in pain.
Overview
By mid-July 2024, a surge in ransomware attacks targeting prominent US-based corporations was observed, with the perpetrators leveraging their newly developed capabilities. The similarities between MDeployer and MS4Killer variants, observed across each intrusion, imply ongoing development of these tools. We observed two distinct versions of MDeployer within a single intrusion, strongly suggesting an attempt to modify and improve the initial approach after an initial failure.
A comprehensive evaluation of MDeployer and MS4Killer precedes the hands-on execution of the notorious Embargo ransomware. The MDeployer is a notorious malware loader responsible for the widespread deployment of both MS4Killer and Embargo ransomware variants. The MS4Killer malware exploits a vulnerable driver to subvert endpoint detection and response (EDR) solutions, thereby compromising system security by disabling critical safety features on infected machines.
Embargo
Noted for the first time in ESET telemetry data in June 2022, Embargo made its public debut. Beyond its impressive capabilities in breaching prominent targets with ease, the group garnered attention for its unconventional choice of programming languages used in developing its ransomware payloads. Researchers have lifted an embargo on Rust, a cross-platform programming language, enabling the development of more sophisticated ransomware that can target both Windows and Linux systems. Following the emergence of BlackCat and Hive, a new threat actor known as Embargo has surfaced, specializing in crafting ransomware payloads within the Rust programming language.
Initially appearing robust in its operational approach, Embargo seems to possess significant resources. Establishing its own communication infrastructure, Whisper enables direct interaction with users (Determine 1). It also facilitates secure messaging via the Tox protocol. The perpetrators exploit their victims through a tactic of double extortion, subsequently posting the compromised data on their notorious leak website. The cybersecurity report reveals that the consultant casually references a primary payment structure for associates, implying that the organization may be involved in providing RaaS (ransomware as a service) to clients. Recent regulatory enforcement actions, impacting notorious groups such as one and two, have prompted a reshuffling in the Ransomware-as-a-Service (RaaS) ecosystem. In the RaaS environment, these transformations facilitate the rise of a complex, newly emerged actor. Considering the group’s advanced nature, the prevalence of a conventional leak website, and their assertions, it is reasonable to infer that Embargo likely functions as a Ransomware-as-a-Service (RaaS) provider.
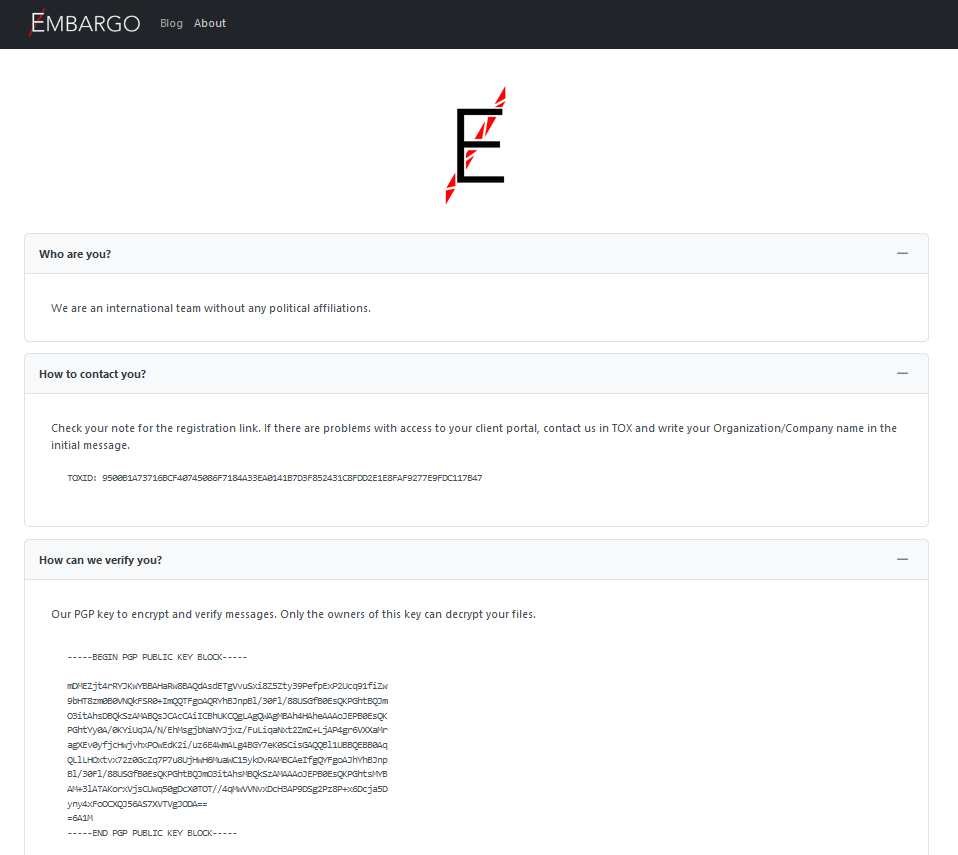
The following embargoed ransomware payloads, observed during the July 2024 incidents, exhibit the following characteristics:
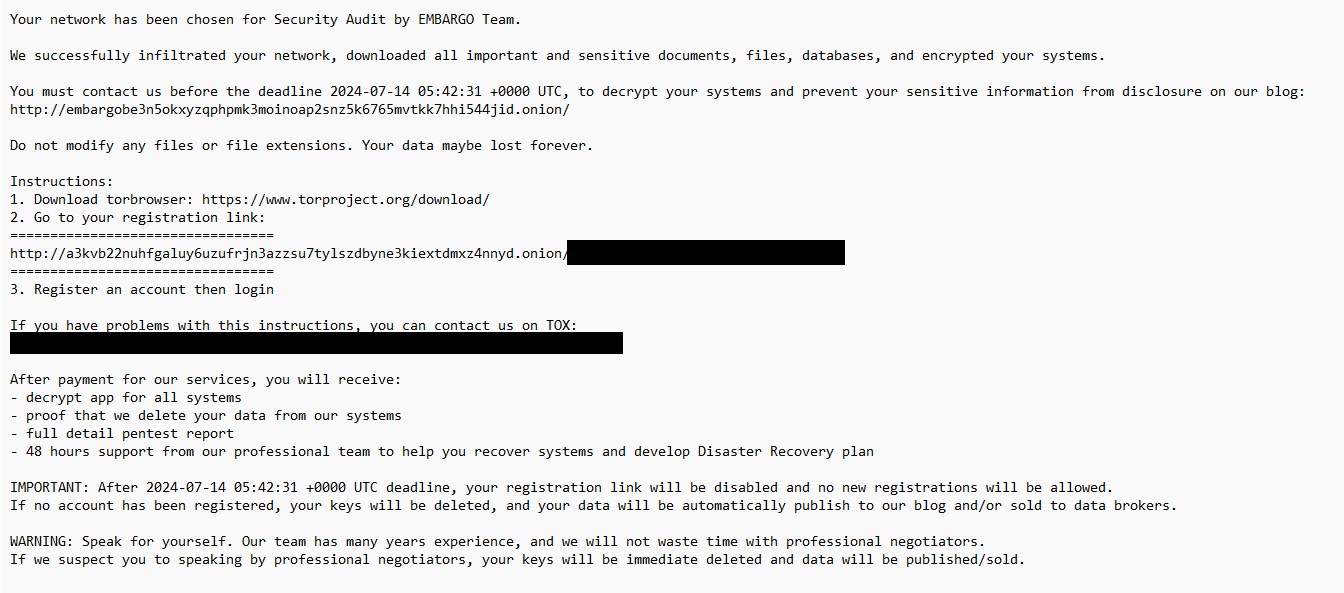
- The Embargo ransomware deposits a ransom note (dubbed Determine 2) alongside each encrypted file.
- Encrypted record files obtain a randomly generated six-character extension comprising hexadecimal digits, for instance, `.7b34a9` or `.e12c3d`.
- Payloads create the mutex .
Researchers’ earlier evaluations revealed that payloads generated mutexes. Noticeably, mutex names primarily derive from the lyrics of songs. widespread rock songs. Our findings align with those presented in the Cyble report.
MDeployer
The primary malicious loader that MDeployer aims to deploy on compromised machines is MDLoader, which enables the subsequent attack stages, ultimately resulting in ransomware execution and file encryption.
Based on the area within the relevant part of its PE header, it becomes clear that Embargo refers to this instrument. So, let’s converse with it as an MDeployer – Embargo Deployer.
The primary objective of this malware is to decipher two encrypted files, allegedly dropped by an unidentified earlier phase, and subsequently execute two payloads: the MS4Killer and Embargo ransomware components.
- The script initially tries to decrypt the MS4Killer payload from the file, then saves the decrypted content in and runs it.
- Subsequently, the ransomware payload is decrypted from its encrypted state, saved with a designated filename, and then executed.
- When the ransomware completes its encryption process, MDeployer ceases execution of MS4Killer, erases any decrypted payloads and a dropped driver file, before ultimately rebooting the system.
The MS4Killer service is expected to operate continuously, and MDeployer confirms this by invoking the perform API call, awaiting a response with value. If MDeployer is not functioning correctly, it will log an error message and terminate without processing the subsequent payload. Logging will be discussed in greater detail later on in this blog post.
Across all MDeployer variants examined, a common trait has emerged: each payload is decrypted using the same, hardcoded RC4 key.
During its operation, MDeployer engages with a multitude of records. To facilitate comprehension, Determine 3 illustrates the correlation between data sets.
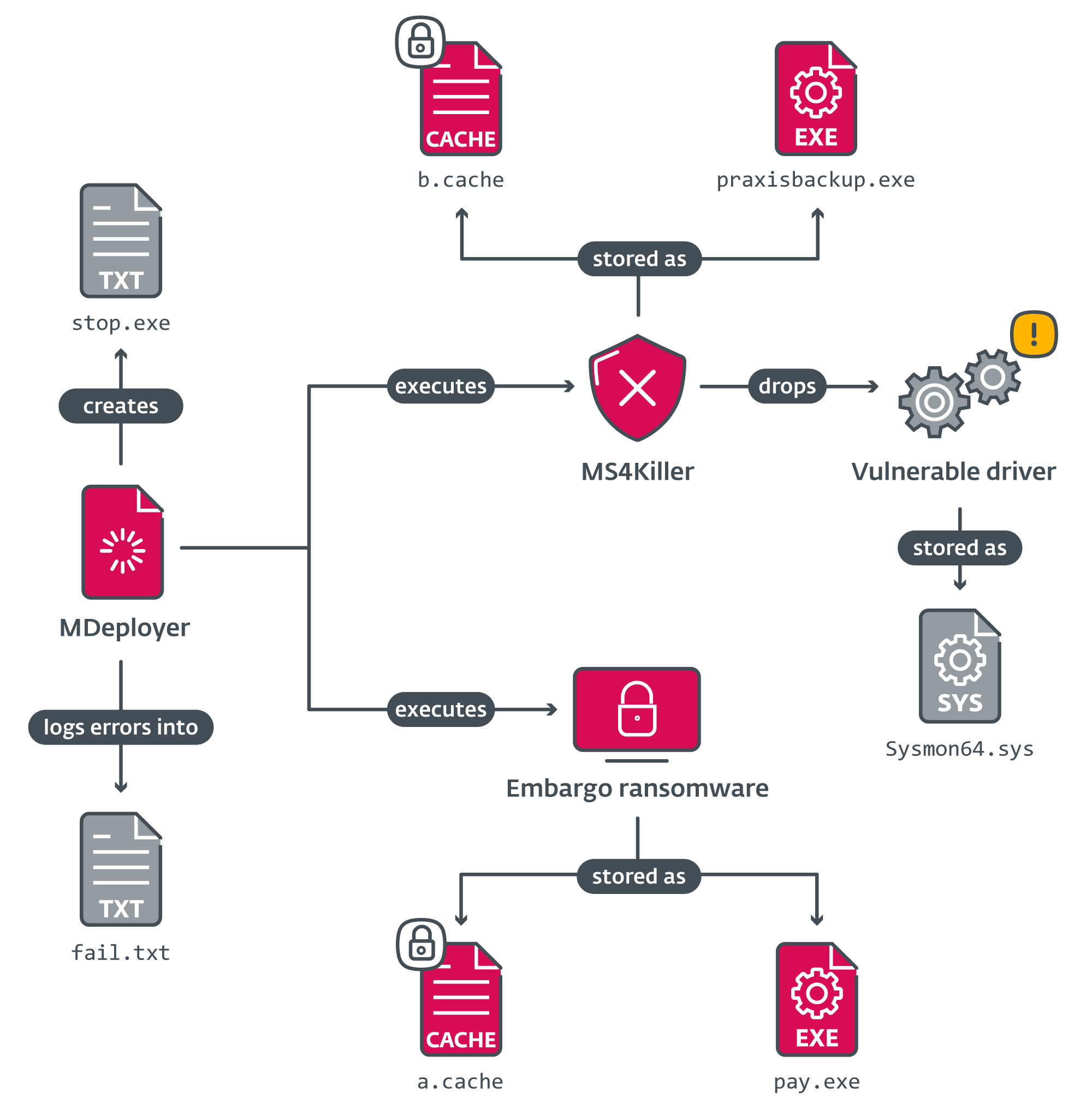
Desk 1 lists their functions.
| RC4-encrypted MS4Killer | |
| RC4-encrypted Embargo ransomware. | |
| Decrypted MS4Killer. | |
| Decrypted Embargo ransomware. | |
| Log file. | |
| Placeholder file for organizational purposes. | |
| Unreliable weak driver, abandoned by MS4Killer. |
Protected Mode abuse
Among the numerous incidents we scrutinized, the lone exception revealed that MDeployer, with one solitary deviation from its typical behavior, was compiled as an executable (EXE) rather than deploying as a dynamic link library (DLL). The DLL variant includes the additional feature to temporarily disable critical safety features.
What are the key steps involved in the execution process of a dynamic link library (DLL)?
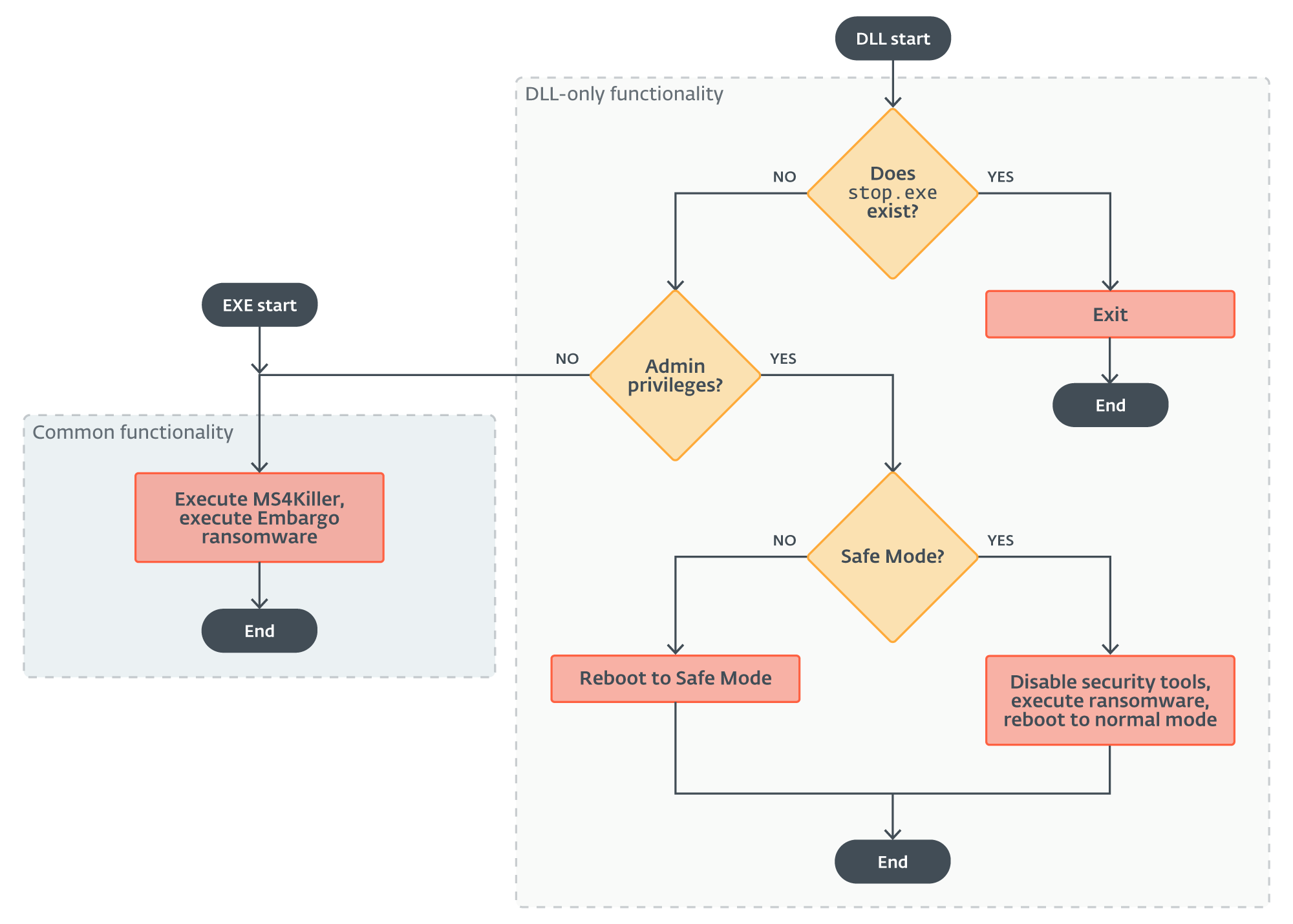
The primary difference emerges immediately upon initializing the DLL, as this mechanism first verifies the file’s existence. The presence of this file suggests that a previous execution of MDeployer has occurred, either successfully deploying the ransomware payload or terminating abnormally due to an error. If the file is discovered, the loader initiates a seamless cleanup procedure before terminating operation. Although EXE variations successfully generate files, they do not include checks for their existence.
One feature of the DLL model in MDeployer is a built-in check that verifies whether the application was launched with administrator privileges, thereby ensuring proper functionality and security. Without being able to verify this assumption? Indeed, the truth is that various EXE iterations were undoubtedly compiled using a single execution unit’s source code.
Notwithstanding its execution with administrative privileges, the malicious code strives to reboot the compromised system into Safe Mode in a bid to circumvent crucial security measures.
In Protected Mode, Windows’ diagnostic mode operates the system at an extremely low level of functionality. Because of this, many cybersecurity safeguards are rendered ineffective in Protected Mode, leaving attackers with the opportunity to evade detection. Is a tactic considered sophisticated among mature ransomware groups and has been exploited in the past, as noted by cybersecurity researchers.
The disabling of performance for safety reasons unfolds in a sequential manner, comprising two distinct stages.
Step 1
The primary objective of Step One is to reboot the system and enter a secure mode known as Protected Mode. Utilizing a combination of Windows command-line tools, the loader effectively accomplishes this by employing a blend of:
- Enable Protected Mode as the default boot configuration.
- Disable Windows Defender while operating in Safe mode.
- Upon creating a service, we initiate the execution of the loader once the system reboots into Protected Mode.
- restart the system.
Which specific loading instruction set does this refer to? The total number of instructions executed by the loader varies greatly depending on the type of loader and its functionality.
Step 2
Once loaded into Protected Mode, the malware disables certain security measures by modifying the directory setup of targeted anti-virus tools, and subsequently executes the Embargo ransomware payload.
The system then initiates a “Protected Mode cleanup” procedure, which involves eliminating the decrypted ransomware file, generating a management movement file to prevent secondary encryption, erasing the persistence service, and rebooting the computer into its normal operational state once more.
BAT disabler
During further analysis, we observed another significant benefit from utilizing the DLL loader as a BAT script: enhanced performance. The script focuses on a solitary safety resolution, a concept that will reappear in the context of this article. Using the same approach, the malware employed a persistence mechanism to initiate a reboot into Safe Mode, then proceeded to rename the installed security software’s installation file. The system utilized a duplicate file for managing movements and recorded error logs into fail.exe within MDeployer.
Embargo’s versatility in customizing its instruments underscores its commitment to harmonizing with each individual’s unique environment.
Logging
When encountering errors, MDeployer captures error messages and saves them to a file before creating the file.
The four phases that attackers differentiate in their log messages involve the use of a distinct prefix to categorize error logs within each phase.
- – payload decryption,
- – ransomware execution,
- – MS4Killer execution, and
- MS4Killer crashes – a trigger for this prefix indicating unexpected exit.
Within the DLL model, there exist additional log message prefixes that differ from those found in the EXE variations.
- Creating or deleting a service?
- Modifying the Windows Registry –
- Utilizing the command-line instrument to enable and subsequently apply Protected Mode upon reboot.
Cleanup
The MDeployer features multiple iterations of a cleanup procedure triggered by distinct occasions. After the loader successfully executes the ransomware payload, any potential errors that may arise during its execution are also addressed.
During cleanup, the loader terminates the MS4Killer process, removes decrypted payloads and the weak driver dropped by MS4Killer, and generates a movement management file.
When the cleanup routine is triggered due to the presence of something, MDeployer also eliminates its own .exe file.
Lastly, it reinitializes the system by executing a shutdown command.
Execution
Despite these observed scenarios, the loader’s perseverance was attributed to a pre-scheduled task (designated as Determine 5) crafted by a system administrator who had already attained elevated privileges.
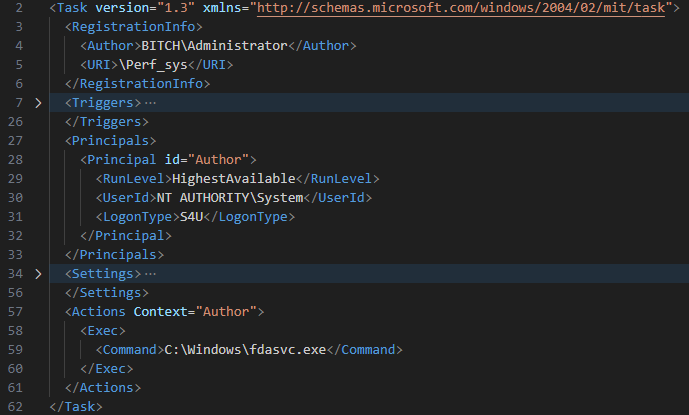
In some instances, our team also obtained a PowerShell script that led to the activation of MDeployer. Given the similarities between the scripts, we infer with moderate certainty that Embargo likely employed a similar tool, possibly even the identical instrument, to transfer the loader from an unsecured device.
Lively growth
Notwithstanding the varying degrees of complexity observed within the loader samples, it is evident that the group’s processes remain in a state of dynamic flux, rather than being fully refined or standardised.
As it becomes apparent that MDeployer eliminates the vulnerable drivers discarded by MS4Killer, this revelation gains significant attention due to its implication that these two tools are being co-developed. While the MS4Killer and the DLL model of MDeployer share some similarities in their approach, they both attempt to bypass or disable safety features.
It’s not uncommon for a loader to eliminate payload records and then attempt to execute one of them immediately afterwards. In the context of Determine 6, a peculiar scenario arises where the MDeployer initiates a cleanup operation, resulting in the deletion of a file; subsequently, it attempts to re-execute that very same file.
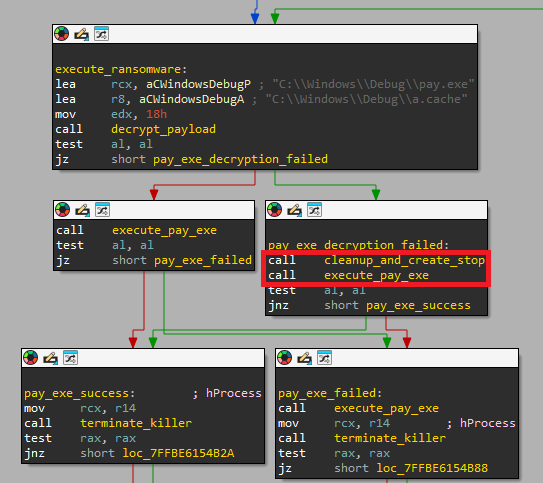
In reality, the DLL-based loading mechanism we’ve examined is plagued by numerous defects that render it completely ineffective. The proliferation of various loaders observed in a single incident may be attributed to the attacker’s ability to discover and adapt to vulnerabilities in real-time, necessitating adjustments to their tactics.
MS4Killer
The MS4Killer malware uses the BYOVD technique to terminate security process execution, allowing it to evade detection by evading safe-guarded driver processes. Written, akin to the loader, in Rust. We believe that MS4Killer was heavily influenced by a Proof-of-Concept (POC) developed for GitHub and written in Rust, a testament to its innovative potential.
The POC’s resemblance to our current iteration prompts us to refer to it as MS4Killer, an abbreviation standing for “EMbargo s4killer.”
Extending the performance
Is engineered to identify an operating process and detach it from the kernel. The vulnerability arises from exploiting a weak driver that has been embedded within the compiled code. The termination method for the specified task is passed to s4killer as a command-line argument. Termination is typically implemented through formal processes and procedures outlined in the relevant company policy or employee handbook.
The embargo has protracted the POC’s performance, offering the following alternatives:
- The MS4Killer utility perpetually cycles through a never-ending scan, persistently monitoring the system’s operational processes.
- The list of targets for elimination is embedded directly in the program’s executable code.
- The embedded driver blob uses encryption via RC4 to secure its contents.
- Binary strings are encrypted using simple XOR, specifically for log messages, course names, and the RC4 key employed for decrypting drivers.
- When the termination process unfolds, MS4Killer instantiates a new instance of itself, designating it as a “baby” course and transmitting the original kill method as a parameter.
- Scanning and termination processes are decomposed into multiple threads utilizing the `,` library for Rust, enabling parallel processing of information.
BYOVD
A vulnerability in your system arises when a malicious actor exploits weak kernel drivers to execute arbitrary code at the kernel level. Typically, ransomware actors integrate BYOVD tooling into their exploitation chain to manipulate security settings and gain a foothold in targeted infrastructures under attack. Associates can effortlessly execute the ransomware payload without any concerns about detection after deactivating the security features.
Here is the improved text in a different style:
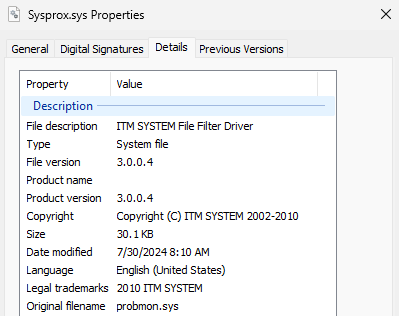
The malware, identified as MS4Killer, exploits a vulnerable version of a minifilter driver, specifically model 3.0.0.4, which is dated back to Determine 7 and bears a digital signature that has already been revoked by . The driving force behind the malicious activity lies hidden within the MS4Killer binary, encrypted using the RC4 algorithm and presented as a compact, self-contained blob. We promptly notified Microsoft about the ITW’s improper use of this driver.
String decryption
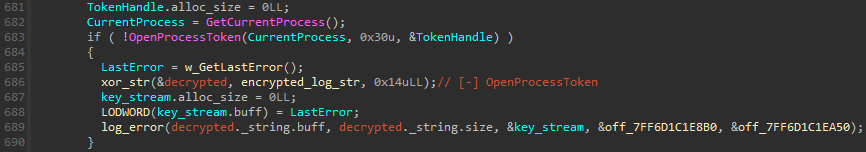
The MS4Killer malware employs cryptographic techniques to conceal embedded strings within its binary, thereby rendering them inaccessible to casual inspection. Specifically, it utilizes XOR operations to encrypt log message strings, the RC4 decryption key for embedded drivers, and a list of course names used for termination purposes. The Windows API called that instantiates an instance of log message decryption is determined to be? If the performance fails, a user-defined function renamed to `perform` in Determine 8 decrypts the XORed string and stores the result, storing it into its first argument passed by reference. The decrypted string, appended with error data, is subsequently written to the ‘plain.out’ file.
Loading probmon.sys
The professional weak driver is incorporated into the MS4Killer binary as a blob encrypted using RC4 encryption and potentially further protected through XOR encryption, leveraging its key. Now, our analysis has revealed two distinct file paths where MS4Killer deposits its vulnerable driver.
- (Determine 9)
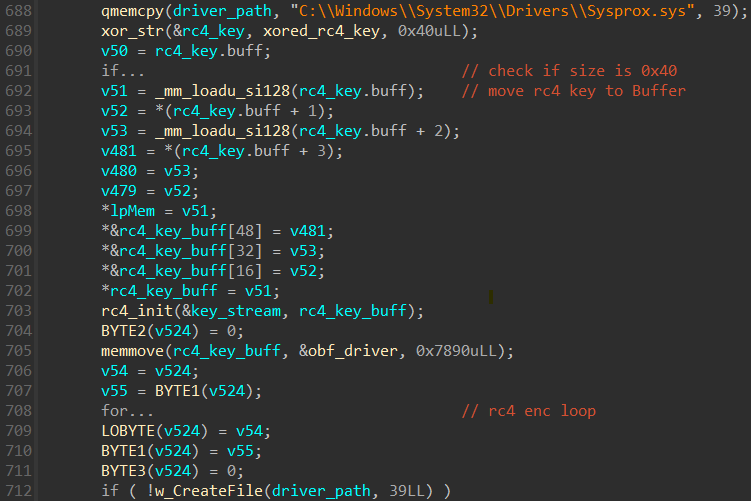
Driver loading is consistent with industry standards, efficiently initializing software components to ensure seamless system functionality.
- Enabling the mandatory prerequisite for seamless loading and unloading of system drivers.
- Providing a service through
- Creating extra registry keys, as required for filter loading, in HKEY_LOCAL_MACHINE\SOFTWARE\Company Name\Applications\Filter Key, and similarly in HKEY_CURRENT_USER\SOFTWARE\Company Name\Applications\Filter Key.
- Loading a Minifilter Driver into the System via PowerShell?
We’ve identified that MS4Killer has employed a diverse array of service pseudonyms to date: MS4Killer, KillerSoft, and SoftServe.
Hidden course of listing
The company MS4Killer consistently cross-references operational procedures against a comprehensive inventory of security software process names, which are also encrypted using advanced XOR techniques. Following the motive force’s hundreds, MS4Killer uncovers the list of course names, a total of ten.
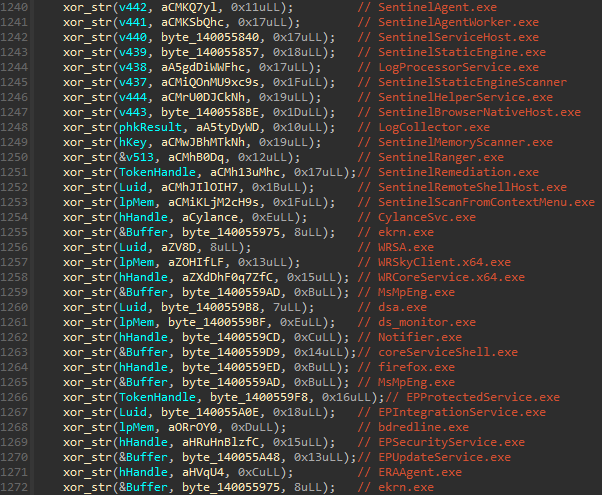
The courses of names reference processes from a variety of safety products.
The code snippet in Determine 10 indicates that duplicate course names exist, such as “Duplicate Course”. A closer examination reveals that certain strings decrypt to the same location, with variables x, y, and z illustrating this point. Moreover, a single dummy course identifier is present. Furthermore, tracing the cross-references between decrypted string variables yields comparable logic, where only a specific subset of process names is employed. Here is the rewritten text:
A snippet within the Determine 11 software compares process names related to ESET products with operating system processes. A thorough examination of multiple MS4Killer samples consistently indicates that only specific security protocols are tracked during each intrusion, unaffected by the constantly updated list of process names sourced from various security products.
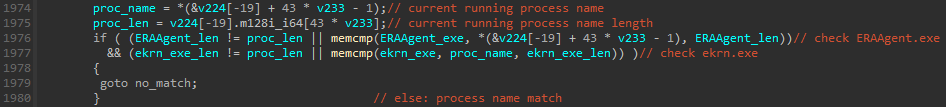
New analysis suggests that malicious MS4Killer code was compiled just before the attacks, specifically targeting the security measures protecting the victim’s device.
Conclusion
We recently published a review of the latest Rust-based tools, specifically the MDeployer and MS4Killer, which have been adopted by the notorious ransomware group Embargo. The relatively unknown Embargo ransomware operator has emerged onto the scene, seeking to leave its mark by emulating the tactics employed by established groups in this nefarious space. Now we’ve presented reasons justifying our stance that the Embargo group offers Remote Access Services.
The primary objective of the Embargo toolkit is to ensure a lucrative deployment of the ransomware payload by disabling security measures within the victim’s infrastructure, thereby creating an environment conducive to successful extortion. The Embargo tool invests significant resources in replicating its performance across multiple stages of the attack, specifically disabling security solutions through scripts such as BAT, MDeployer, and MS4Killer. As we’ve now observed, attackers can dynamically adjust their tools in real-time during an active intrusion to evade detection by a specific security solution.
The two tools, MDeployer and MS4Killer, are implemented in the Rust programming language. The identical pattern holds true for the ransomware payload, implying that Rust has become the preferred programming language for the group’s developers. Now, we’ve observed the deployment of two distinct versions of MDeployer across a single incident, raising concerns about potential inconsistencies and impact on overall performance. The deployed loader also included several logical flaws that hindered its optimal functioning. Given the swift adjustments made to instrumentation settings and the proximity of compilation timestamps to actual intrusion times, it is reasonable to infer that the attacker possesses the capability to dynamically manipulate source code and recompile tools during an incident.
IoCs
Recordsdata
| dtest.dll | Win64/Agent.ECY | A newly discovered MDeployer loader has been found to deploy MS4Killer and Embargo ransomware, potentially posing a significant threat to targeted victims. | |
| fxc.exe | Win64/Agent.ECY | M Deployer: A sophisticated malware deployment tool responsible for spreading MS4Killer and Embargo ransomware variants. | |
| fdasvc.exe | Win64/Agent.ECY | The MDeployer: a malicious tool that deploys the MS4Killer and Embargo ransomware variants, wreaking havoc on compromised systems. | |
| praxisbackup.exe | Win64/Agent.ECW | MS4Killer – Embargo EDR Killer. | |
| praxisbackup.exe | Win64/Agent.ECW | MS4Killer – Embargo EDR Killer. | |
| pay.exe | Win32/Filecoder.Embargo.A | Embargo ransomware. | |
| win32.exe | Win32/Filecoder.Embargo.A | Embargo ransomware. | |
| Sysmon64.sys | Win64/ITMSystem.A | Reliably disabling the weak driver, Proximity Monitor (probmon.sys), is achieved through utilization of MS4Killer. | |
| Sysprox.sys | Win64/ITMSystem.A | Reputable system component, Proactive Memory Monitor (probmon.sys), was temporarily disabled and exploited by malicious software (MS4Killer). |
Certificates
| ITM System Co.,LTD | |
| ITM System Co.,LTD | |
| Guro-gu | |
| N/A | |
| KR | |
| 2011-06-08 06:01:39 | |
| 2014-06-07 08:32:23 |
Further MDeployer file paths
Instructions utilized by MDeployer
MITRE ATT&CK methods
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Develop Capabilities: Malware | The Embargo Group forges a trio of tailored tools: MDeployer, MS4Killer, and Embargo Ransomware. | ||
| The Windows Command Shell: A Legacy of Productivity | The Embargo group executes a batch script that temporarily suspends key safety measures, rendering critical safeguards inoperable. | ||
| Command-Line Interface: PowerShell | The Embargo group leverages PowerShell to remotely deploy malware to unsuspecting victims’ machines via the MDeployer platform. | ||
| Scheduled Job/Job: Scheduled Job | The Embargo group leverages pre-scheduled tasks to execute MDeployer on vulnerable endpoints, facilitating malicious activity. | ||
| System Providers: Service Execution | The Embargo group leverages a Windows service to run MDeployer in Safe Mode. | ||
| The boot or logon autostart execution process allows you to set up programs to automatically start when a user logs onto their Windows system. This can be achieved by modifying the registry and creating shortcuts in the startup folder. To access the registry, open the Registry Editor (Regedit.exe) on your Windows system. The paths for the boot or logon autostart execution are as follows: * For 32-bit applications: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Alternatively, you can also use the startup folder to add shortcuts for autostart programs. To do this: 1. Open File Explorer on your Windows system. Note that these registry keys and startup folders are specific to each user’s Windows system, so changes made here will only affect the current user and not the entire system. | The Embargo group modifies the Windows Registry to initiate a bespoke service within a secured environment of Safe Mode. | ||
| Create Account: Area Account | The Embargo Group establishes personalized online profiles to streamline communication and collaboration. | ||
| Imperiling Defences: Disabling or Modifying Instruments | MS4Killer, MDeployer, and a batch script collectively circumvent critical safety features. | ||
| Impair Defenses: Protected Mode Boot | The MDeployer and associated BAT scripts seamlessly reboot into Protected Mode. | ||
| Indicator Removing: File Deletion | The MDeployer eliminates any dropped records during its cleanup process. | ||
| Modify Registry | MS4Killer configures the registry to enable loading of a pre-configured, commercially available network driver with reduced functionality. | ||
| Cryptographic Data Files: Securely Wrapped Information | Payloads loaded by MDeployer are encrypted using the outdated and potentially vulnerable RC4 algorithm. | ||
| Community Share Discovery | The Embargo ransomware exploits community shares to facilitate discovery. | ||
| File and Listing Discovery | The Embargo ransomware conducts file and directory exploration. | ||
| Inhibit System Restoration | The Embargo ransomware malware effectively renders Windows System Restore functionality inaccessible. | ||
| Information Encrypted for Affect | Embargo ransomware encrypts files and data on infected computers. |

