At Microsoft, safe design begins on the basis of our computing stack—the silicon degree—and extends by means of each layer of the cloud.
At Microsoft, safe design begins on the basis of our computing stack—the silicon degree—and extends by means of each layer of the cloud. Since launching the Safe Future Initiative (SFI)—a company-wide dedication to safety, we proceed to prioritize delivering merchandise and options which might be safe by design, safe by default, and safe in operation.
SFI sits on the core of Azure’s strategy to designing {hardware} methods, reshaping the structure, deployment, and operations of our bodily cloud and AI infrastructure. Azure is redefining workload safety from the datacenter to the sting. Our complete strategy consists of Azure Enhance, which isolates management and information planes for digital machines; the Azure Built-in HSM, a customized safety chip offering FIPS 140-3 Stage 3 key safety inside our servers; and confidential computing, which protects information in-use by means of hardware-based trusted execution environments (TEEs).
Microsoft has additionally made ongoing efforts to advance systematic safety audits and contribute to the open-source group by means of Caliptra—a silicon root-of-trust designed to anchor safety in {hardware}. Combining these initiatives with applied sciences similar to confidential computing and code transparency providers, our purpose is to make sure that each part within the provide chain may be securely verified.
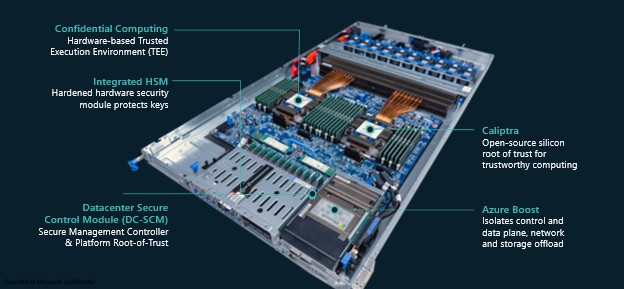
Objective constructed silicon for defense-in-depth
Azure Enhance serves because the system’s safety controller, managing safe entry to Azure. Solely methods with a verified and permitted safety configuration are granted entry.
To reinforce safety and efficiency, Azure Enhance offloads management airplane providers from the host CPU to a devoted Azure Enhance system controller. This setup creates a {hardware} separation between Azure’s management airplane—working on the Azure Enhance controller—and buyer workloads—working on the CPU—guaranteeing sturdy isolation and safety.
Azure Built-in HSM is a server native {Hardware} Safety Module (HSM) for high-assurance workloads. It’s designed to satisfy the stringent necessities of the Federal Data Processing Requirements (FIPS) 140-3 Stage 3 safety necessities, requiring sturdy isolation, tamper-resistant {hardware}, identity-based authentication, and automated zeroization. Azure Built-in HSM protects keys in-use, by guaranteeing keys at all times stay inside the bounds of the HSM.
Not like centralized distant HSM providers, Azure Built-in HSM eliminates community roundtrips for key operations and avoids the necessity to launch keys into the workload atmosphere. As an alternative of counting on distant entry, the Azure Built-in HSM is securely sure to the native workload and offers oracle-style key utilization to licensed providers inside the native atmosphere.
Azure Datacenter Safe Management Module (DC-SCM)—DC-SCM is a safety and server management module that comprises Hydra—a security-focused Board Administration Controller (BMC) design, with an built-in root-of-trust and hardware-based safety safety on all administration interfaces. This root of belief restricts unauthorized entry to BMC firmware and ensures the firmware is authenticated and cryptographically measured.
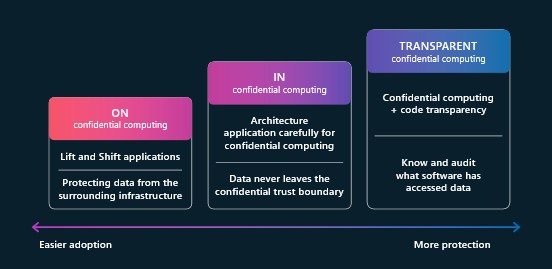
Confidential Computing affords a spectrum of ensures
Confidential computing makes use of hardware-based Trusted Execution Environments (TEEs) to guard workloads—similar to digital machines—from different system software program, together with the hypervisor.
Microsoft, a founding member of the Confidential Computing Consortium, works intently with CPU and GPU producers to design and combine confidential computing applied sciences straight into their {hardware}. Earlier this 12 months on the Confidential Computing Summit we outlined a spectrum of ensures customers can allow with confidential computing after they port their functions, together with:
- On by default, is the carry and shift current functions with minimal change.
- Construct in confidential computing by designing providers and functions that make deeper use of hardware-based protections.
- Leverage clear confidential computing to achieve deeper insights into how confidential providers work together and function securely.
Azure has probably the most complete portfolio of confidential computing options, together with confidential digital machines, containers, generative AI, and providers like Azure Confidential Ledger, Azure Attestation, and Managed HSM—every designed to guard code and information all through its lifecycle utilizing hardware-backed safety.
{Hardware} Safety Transparency
Caliptra is a {hardware} root of belief that performs a vital function in securing gadgets. It anchors the chain of belief straight in silicon, establishing foundational safety properties that assist the integrity of higher-level options. This basis offers workloads the power to confirm the code and configuration of the underlying platform, enabling workloads set up belief within the {hardware} platform.
Caliptra is a completely open-source silicon root of belief developed by means of a collaboration between Microsoft, AMD, Google, and NVIDIA. In April, we launched Caliptra 2.0, which included Adams Bridge—an open-source accelerator designed for post-quantum resilient cryptography. This integration made Caliptra the primary open-source root of belief to function hardened post-quantum cryptography, driving broader adoption throughout the {hardware} ecosystem.
Systematic Safety Critiques play a vital function in defending {hardware} infrastructure, which depends on each low-level {hardware} options and the firmware that runs on prime of them. Guaranteeing firmware safety entails rigorous code scanning, steady safety evaluations, and hardware-based attestation.
Traditionally, Microsoft performed these evaluations internally. To reinforce transparency and prolong safety assurance past Microsoft, we partnered with Google and the Open Compute Undertaking in 2023 to determine OCP SAFE—a framework for systematic safety evaluations.
Underneath OCP SAFE, permitted Safety Overview Suppliers (SRPs) carry out unbiased evaluations and difficulty verifiable endorsements of a producer’s safety compliance. These endorsements function trusted proof, supporting safe gadget attestations and reinforcing confidence within the {hardware} provide chains.
Enhancing safety with Code Transparency Companies
Code Transparency Companies (CTS) is an immutable ledger expertise constructed to satisfy the requirements of Provide Chain Integrity, Transparency, and Belief (SCITT). It operates completely inside confidential computing environments, enhancing belief in Azure’s {hardware} and firmware by guaranteeing that each part is verifiably safe .
CTS addresses key challenges in firmware provenance, integrity, and auditability throughout each first-party and third-party provide chains. When paired with a silicon root of belief like Caliptra, and supported by audits similar to OCP-SAFE, CTS ensures that {hardware} and firmware are licensed, non-repudiable, and immutably auditable.
Right now, CTS is a central part in Azure’s confidential cloud providers. Along with Azure’s personal utilization, CTS might be out there as a managed service—permitting Azure clients to create and function their very own transparency service cases.
Staying safe with Microsoft
Microsoft’s Safe Future Initiative (SFI) offers a guiding framework for constructing safe and reliable cloud infrastructure. By embedding safety into each layer—from silicon to methods to providers—Azure takes a defense-in-depth strategy to cloud safety. By means of improvements like Azure Enhance, Azure Built-in HSM, and confidential computing, and thru collaborative efforts similar to Caliptra, OCP SAFE, and SCITT, Microsoft is just not solely securing right now’s workloads but additionally laying the muse for a safer and clear future.

