“How might they see something however the shadows in the event that they had been by no means allowed to maneuver their heads?” — Plato, The Republic, E book VII
Introduction: The Shadows of Governance
Within the allegory of Plato’s Cave, prisoners are chained in darkness, mistaking shadows solid on a wall for actuality. Solely by breaking free can they uncover the reality outdoors the cave. Fashionable organizations face an analogous problem notably in cybersecurity governance and enterprise digital transformation. The shadows on this digital cave are inflexible hierarchies, performative compliance, fear-based management, and alter resistance. These distort the reality, sabotage threat administration, and create false safety postures. This weblog explores the “darkish aspect” of cybersecurity governance utilizing Plato’s Cave as a metaphor, exhibiting how these hidden forces hurt organizations, and the way Cybersecurity Warrior Leaders (CWLs) may help lead them out of the cave and into governance transformation and maturity.
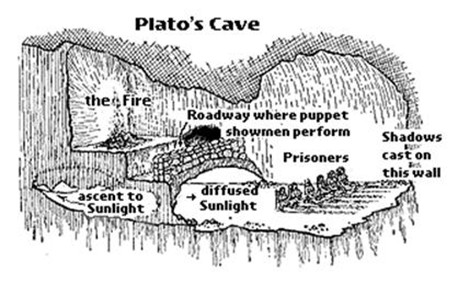
From Nice Dialogues of Plato (Warmington and Rouse, eds.) New York, Signet Classics: 1999. p. 316.
Cybersecurity Governance
Cybersecurity governance refers back to the constructions, insurance policies, and processes that guarantee a company’s info safety technique helps its enterprise targets, complies with rules, and manages threat successfully (NIST, 2024). In fashionable digital enterprises, governance should evolve from static, compliance-driven fashions to adaptive, risk-informed approaches aligned with technological disruption, evolving world threats, and strategic agility. A digital enterprise is a corporation that makes use of digital applied sciences not simply to reinforce operations however to rework enterprise fashions, worth supply, and decision-making (Kane et al., 2015). These enterprises function in real-time, deal with information as a strategic asset, and combine digital technique into tradition, individuals, and processes. Not like conventional enterprises, which depend on static processes, top-down management, and legacy techniques, digital enterprises operate as advanced adaptive ecosystems. These operational modifications profoundly have an effect on cybersecurity governance. The normal, siloed mannequin provides strategy to intelligence-driven, risk-aligned, and built-in approaches. Because of this, management should evolve from command-and-control to Cybersecurity Warrior Leaders (CWLs) who embody digital fluency, emotional intelligence, and cyber risk-informed decision-making.
Digital Enterprise Change
Digital enterprise change includes the deep and steady transformation of a company’s management, tradition, capabilities, and working mannequin by way of the strategic integration of digital applied sciences. It’s not restricted to adopting new instruments or platforms however encompasses how the group evolves its decision-making, collaboration fashions, and buyer engagement in response to fast-moving digital ecosystems (Kane et al., 2015). Change should be proactive, iterative, and inclusive of all ranges of the group. This transformation impacts cybersecurity governance considerably. As digital enterprises turn into extra advanced and interconnected, conventional siloed approaches to cybersecurity governance show insufficient. Success requires agile, cross-functional governance fashions able to integrating cybersecurity into each stage of digital transformation. Governance should hold tempo with modifications in third-party threat administration (TPRM), DevSecOps, cloud infrastructure, synthetic intelligence, and evolving buyer expectations. Strategic, technological, and cultural transformation in digital enterprises additionally requires robust change management. CWLs should turn into champions of digital enterprise change by aligning governance fashions with innovation, supporting safe experimentation, and embedding cyber resilience into transformation roadmaps, as a result of CWLs play a crucial function in overcoming resistance, cultivating safety tradition, and making certain steady governance maturity.
Desk 1: Conventional vs. Digital Enterprises
| | | | | |
| | | | | |
| | | | | |
| | | | | |
| | | | | |
From Shadows to Technique: 5 Core Governance Illusions
1. Chained in Compliance: False Safety in Governance
The Shadow: Many organizations equate compliance with safety. This phantasm turns into a cushty shadow on the wall: one which leaders are reluctant to show away from.
Affect: Field-checking behaviors suppress innovation, restrict resilience, and blind organizations to rising threats not lined by current frameworks like NIST, HITRUST, or ISO.
The CWL Means: A Cybersecurity Warrior Chief cultivates adaptive governance, aligning frameworks with real-time risk intelligence, and remodeling compliance into cyber resilience.
2. Concern-Primarily based Management and Data Hoarding
The Shadow: Authoritarian management or turf safety suppresses collaboration and transparency. This mirrors the prisoners’ reluctance to share information about the actual world outdoors the cave.
Affect: Data silos and fear-based reporting distort threat consciousness, delay breach response, and degrade cross-functional alignment between safety, authorized, IT, and enterprise models.
The CWL Means: CWLs act as trusted guides and boundary spanners, constructing horizontal bridges and training leaders to interact by way of psychological security, visibility, and shared accountability.
3. Change Aversion and Legacy Pondering
The Shadow: Legacy techniques and sunk-cost biases lock organizations into outdated safety fashions comforting but dangerously out of date shadows.
Affect: Organizations fail to evolve controls and capabilities for AI, zero belief, cloud-native, and IoT environments. Cybersecurity governance stagnates.
The CWL Means: Warrior leaders develop e-organizational change muscle tissues: they champion digital transformation roadmaps, prepare change brokers, and shift governance to real-time, data-driven decision-making.
4. The “Shadow Reporting” Drawback
The Shadow: Poor KPIs, self-importance metrics, or governance theater (e.g., over-reporting inexperienced dashboards) obscure actuality from senior management and the Board.
Affect: Executives are lulled right into a false sense of safety. Safety groups burn out whereas actual threats go unaddressed.
The CWL Means: CWLs floor “onerous truths,” promote truth-telling cultures, and use KPIs that mirror risk-adjusted efficiency: not PR spin.
5. Shadow Puppeteers: Distributors and Framework Fetishism
The Shadow: Overreliance on distributors or blind adherence to frameworks creates exterior dependency; another person defines your governance for you.
Affect: Organizations turn into reactive, not strategic. Governance is formed by what’s purchased, not what’s wanted.
The CWL Means: CWLs personal the governance story, customizing frameworks to enterprise fashions, balancing purchase/construct choices, and making certain governance is internalized not outsourced.
Desk 2: From Shadows to Technique
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
Conclusion: Rising from Plato’s Cave
The best risk to cybersecurity will not be exterior attackers, it could be the inner governance shadows organizations refuse to confront. Cybersecurity Warrior Leaders usually are not merely compliance enforcers, they’re change brokers, educators, and strategists. Just like the freed prisoner in Plato’s Cave, CWLs should threat discomfort to see clearly and assist others do the identical. By embracing fact, integrity, transparency, and adaptive governance, CWLs lead organizations out of the cave and into the sunshine of adaptive, resilient, built-in, moral, and intelligence pushed cybersecurity applications that make sure the confidentiality, integrity, and availability of knowledge and defend individuals, tradition, processes, and know-how.
References
- Glover, J., Rainwater, Ok., Jones, G., & Friedman, H. (2002). The dynamics of adaptive management: A theoretical framework and coaching mannequin for reworking organizations. Middle for Inventive Management.
- HITRUST. (2023). HITRUST CSF v11.0 Necessities and Implementation Information.
- Kane, G. C., Palmer, D., Phillips, A. N., Kiron, D., & Buckley, N. (2015). Technique, not know-how, drives digital transformation. MIT Sloan Administration Overview and Deloitte College Press.
- Kotter, J. P. (1996). Main Change. Harvard Enterprise College Press.
- NIST. (2024). Cybersecurity Framework 2.0. Nationwide Institute of Requirements and Know-how. https://www.nist.gov/cyberframework
- Plato. (1991). The Republic (A. Bloom, Trans.). Primary Books. (Authentic work revealed c. 380 B.C.)
- Schein, E. H. (2010). Organizational Tradition and Management (4th ed.). Jossey-Bass.
- Weill, P., & Woerner, S. L. (2015). Thriving in an more and more digital ecosystem. MIT Sloan Administration Overview, 56(4), 27–34.
- Westerman, G., Bonnet, D., & McAfee, A. (2014). Main Digital: Turning Know-how into Enterprise Transformation. Harvard Enterprise Overview Press.
- Bevett, D. L. (2025). Cybersecurity Warrior Management and the American Warrior Custom [Unpublished work].
The content material supplied herein is for normal informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals concerning particular obligations and threat administration methods. Whereas LevelBlue’s Managed Risk Detection and Response options are designed to help risk detection and response on the endpoint stage, they aren’t an alternative choice to complete community monitoring, vulnerability administration, or a full cybersecurity program.

