Researchers at ESET have shed light on the recent activities of threat actor CosmicBeetle, unveiling a fresh variant of ScRansom ransomware and uncovering ties to established ransomware groups.
The CosmicBeetle malware has been observed deploying ScRansomware to small and medium-sized businesses (SMBs) globally. While not being top-notch, a skilled attacker is prepared to compromise vulnerable targets.
CosmicBeetle has replaced its previously used ransomware, Scarab, with ScRansom, which undergoes regular updates. We’ve recently detected a threat actor leveraging the compromised LockBit builder, attempting to capitalize on LockBit’s notoriety by mimicking their ransomware gang in both ransom notes and leak websites.
With moderate certainty, we believe that CosmicBeetle is likely a fledgling affiliate of the emerging ransomware group RansomHub, which has been active since March 2024 and has seen rapid growth in its operations.
This blog post examines the activities of CosmicBeetle over the past 12 months, delving into potential links with established ransomware groups. We provide further insight into ScRansom.
- CosmicBeetle remains remarkably resilient in 2024, consistently refining and disseminating its bespoke ScRansom malware.
- We emphasize that reviving certain encrypted data is fundamentally impossible, underscoring the inherent limitations of ScRansom’s capabilities.
- CosmicBeetle has been probing the limits of a recently disclosed LockBit builder, endeavouring to exploit its capabilities for malicious purposes.
- CosmicBeetle may have recently affiliated with RansomHub, a notorious ransomware-as-a-service operator.
- CosmicBeetle leverages years-old vulnerabilities to compromise small and medium-sized businesses globally.
Overview
ESET researchers have attributed the moniker CosmicBeetle to a high-energy threat actor that emerged as early as 2020, with its malicious activities intensifying in 2023. This notorious threat actor is best recognized for employing a bespoke suite of Delphi-based tools, dubbed Spacecolon, which comprises ScHackTool, ScInstaller, ScService, and ScPatcher. In August 2023, ESET researchers shared their insights into CosmicBeetle. Recently, just prior to publication, a newly developed, tailored ransomware strain called ScRansom emerged and bears striking resemblance to the notorious CosmicBeetle malware. With the discovery of further underlying factors, our conviction in this correlation has increased, and it appears that ScRansom has become the preferred ransomware for that group, having replaced the previously used Scarab ransomware.
By the time our publication was released in 2023, no evidence of exercise had been observed in its natural habitat. That, nevertheless, modified shortly thereafter. The notorious CosmicBeetle malware has continued its relentless onslaught against small-to-medium-sized businesses (SMBs), predominantly targeting organizations in Europe and Asia with the devastating ScRansom strain.
Despite its lack of subtlety, ScRansom has managed to catch attention by targeting notable entities and inflicting significant harm on them, while CosmicBeetle’s cunning tactics have allowed it to successfully breach the defenses of prestigious organizations. As a novice player in the ransomware ecosystem, CosmicBeetle’s inexperience has led to significant challenges hindering the effective rollout of ScRansom. Individuals affected by ScRansom who decide to pay must exercise extreme caution. While the decryptor’s functionality operates as intended at this juncture, it is essential to note that some decryption keys may be needed to restore files and a few records might be irretrievable, depending on the encryption process employed by CosmicBeetle. We delve deeper into specific details in a subsequent segment of this blog post. According to our specialized knowledge on CosmicBeetle, a compelling study by GuidePoint Security recently revealed comparable findings, highlighting the emergence of immature ransomware groups.
While attempting to address these issues, CosmicBeetle may have made some efforts to emulate or conceal its identity by impersonating LockBit, one of the most infamous and prominent ransomware groups in recent history? By exploiting the LockBit ransomware model’s reputation, CosmicBeetle attempted to deceive victims into paying a ransom. Utilizing a leaked LockBit Black builder, CosmicBeetle crafted bespoke malware samples featuring a Turkish-language ransom note, underscoring its adaptability and exploitation of readily available tools.
Recently, our team has been examining an intriguing scenario that raises the possibility that CosmicBeetle may be a previously unknown associate of RansomHub. RansomHub emerged as a ransomware-as-a-service group relatively recently, rapidly gaining public attention after Notchy, infamous affiliate of the BlackCat gang, claimed responsibility for the Change Healthcare attack, only to have his ransom demand stolen by BlackCat, prompting an unlikely partnership with rival gang RansomHub.
The blog post chronicles the development of ScRansom over the past year and details CosmicBeetle’s tactics for compromising targets, exploring the group’s increasing sophistication in their attack strategies and techniques. While we further scrutinize the risk actor’s connections to various ransomware groups.
Attribution
With unwavering certainty, we surmise that ScRansom is the most recent innovation in CosmicBeetle’s arsenal of bespoke utilities. To establish a clear understanding of our thought process,
The ESET telemetry reveals a notable overlap between ScRansom deployments and other tools commonly employed by CosmicBeettle, suggesting potential collaboration or shared infrastructure between these malicious actors. Uploaded to VirusTotal, this file comprises two nested archives, likely housing specimens from a cyber intrusion. The archives further substantiate our suspicions, containing a collection of tools typically employed by CosmicBeetle, including ScRansom, ScHackTool, and other instruments that strengthen the correlation.
There appears to be a considerable degree of code similarity between ScRansom and its predecessor, the CosmicBeetle toolkit, particularly in regards to:
- Delphi remains a popular choice for developers seeking a robust and efficient programming language.
- library for encryption,
- The code contains:
“Aşağıdaki kodda benzer Türkçe karakter dizileri mevcuttur.”
- Utilising areas after colons in strings, which earned the Spacecolon toolset its distinctive reputation and
- GUI similarity with ScHackTool.
These shared characteristics further solidify our connection. While Zaufana Trzencia Strona’s recent blog post attempted to attribute the origin of “CosmicBeetle” to a specific individual – Turkish software developer, ESET researchers disagree with this attribution. The attribution is premised on the tailored encryption protocol employed by ScHackTool, rather than ScRansom. Notably, researchers uncovered a suspicious signature (SHA-1:) linked to the SHA-1 algorithm, which was issued by Turkish software development company VOVSOFT, headquartered at an unusual location.
Despite claims that the pattern belongs to VOVSOFT, it is actually a maliciously modified version of one of the company’s products, specifically signed correctly with SHA-1 hash . Moreover, the digital signature, lifted from a reputable source, was seamlessly appended to the modified version, effectively validating the manipulated code as if it originated from that trusted entity, despite lacking authenticity.
It appears that ScHackTool’s encryption method is also employed in the reputable Disk Monitor Gadget as well. A seemingly plagiarized algorithm was discovered by Zaufana Trzencia Strona analysts, tracing its origins back to a 13-year-old Stack Overflow thread. As MohsenB has been an avid Stack Overflow user since 2012, and his profile photos suggest he is not the VOVSOFT developer himself, it is likely that this algorithm was custom-crafted by VOVSOFT, with CosmicBeetle discovering and utilizing it for ScHackTool years later.
Preliminary entry and victimology
CosmicBeetle typically relies on forceful and direct methods to overcome its adversaries. The next set of vulnerabilities are currently being exploited by the risk actor.
Small- to medium-sized businesses (SMBs) across various industries globally are disproportionately affected by this threat actor due to their tendency to utilize the impacted software without robust patch management procedures in place, making them vulnerable targets. The CosmicBeetle’s leak website is notoriously unreliable and inconsistent in its offerings, prompting us to verify its claims through ESET’s trusted telemetry data. The prevalence of Determine 1’s victims as reported by ESET telemetry data is illustrated.
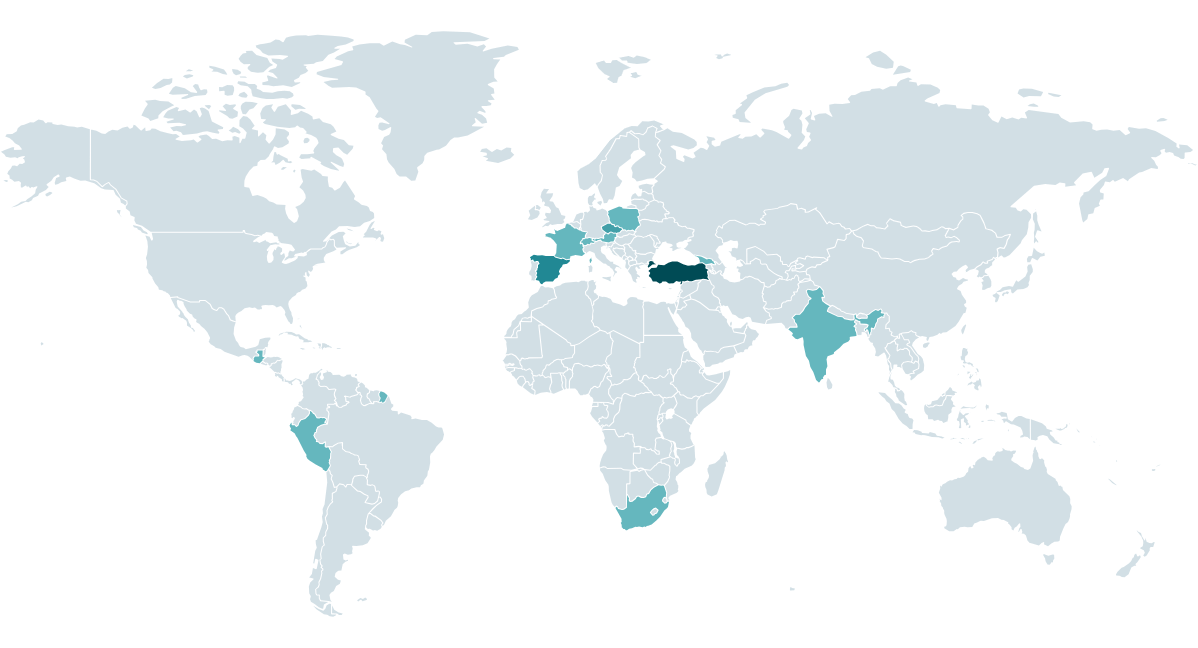
Recent investigations have uncovered a disturbing trend of attacks targeting small and medium-sized businesses (SMBs) across specific industry sectors.
- manufacturing,
- prescription drugs,
- authorized,
- schooling,
- healthcare,
- expertise,
- hospitality leisure,
- monetary providers, and
- regional authorities.
Model
While most ransom demands from ScRansom do not attribute a reputation to the malware itself, CosmicBeetle relies heavily on electronic mail and a prompt messaging software popular among ransomware groups, mainly due to its adoption of the P2P (Peer-to-Peer) protocol. The Tox protocol provides secure, peer-to-peer end-to-end encryption for direct communications.
Here’s a revised version: The ransomware created by CosmicBeetle was aptly named NONAME, a satirical title that belies the real-world threat posed by this type of cyber attack. Due to the inherent chaos surrounding the brand’s identity, we will approach the concept of ransomware in this blog post by rechristening it as ScRansom, thereby simplifying our discussion and facilitating a more focused exploration of its implications.
LockBit copycat
In September 2023, CosmicBeetle resolved to establish a dedicated leak website (DLS) within the Tor network, dubbing it NONAME. The website, as depicted in Figure 2, bears striking similarities to the leak site of LockBit (refer to Figure 3), suggesting it may be an imitation.
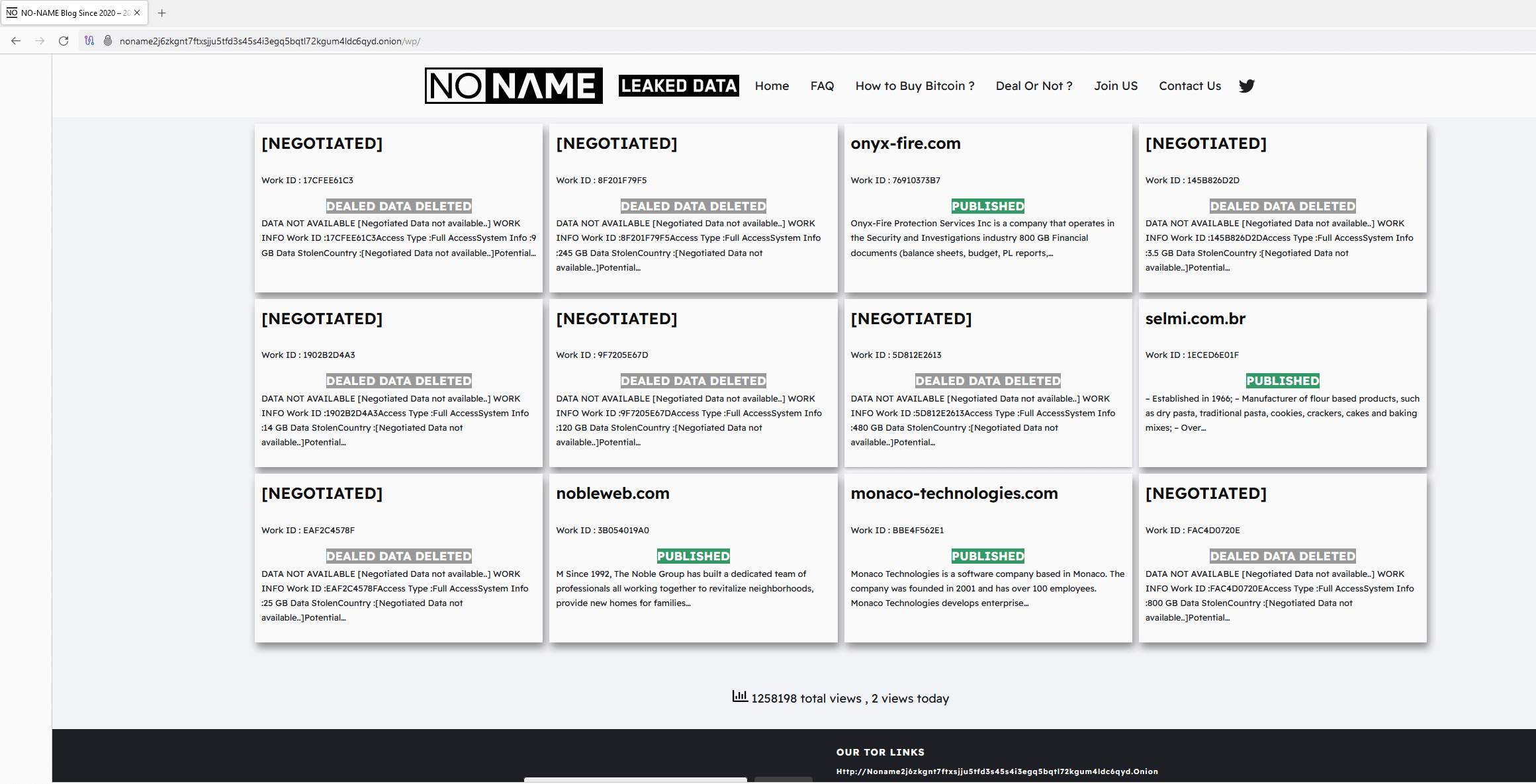
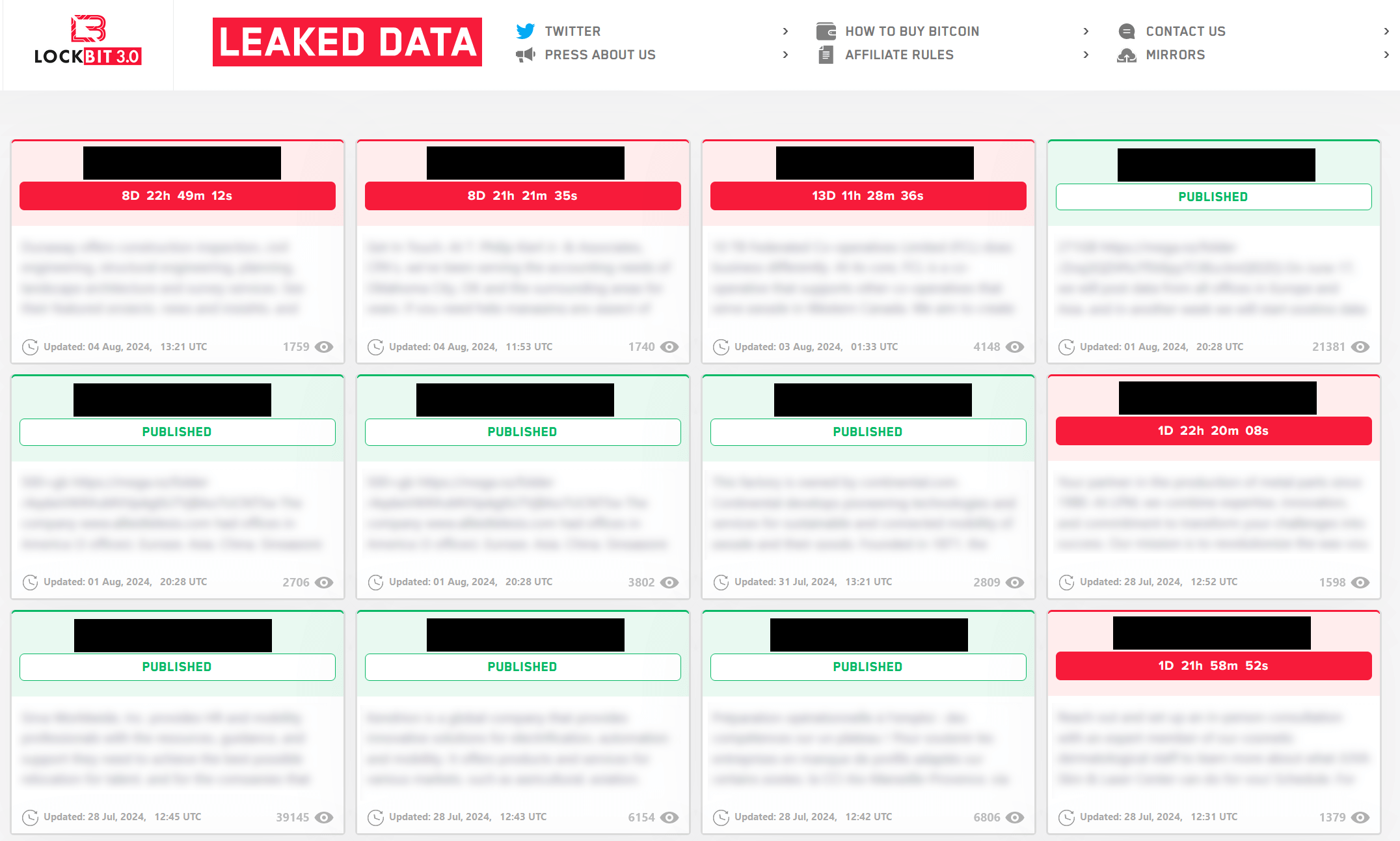
While some visual adjustments have been implemented, the underlying concept still requires clarification. The ransomware’s design shares no similarities with LockBit? All victims depicted in Figure 2 have been severely impacted by LockBit, not ScRansom. This verification can be achieved through DLS monitoring services. All identified victims were publicly exposed on LockBit’s data leak site, with the majority being published in September 2023, just preceding the emergence of the NONAME DLS. The string is appended to amplify the phantom of association with ScRansom, thereby enabling the recognition of victims in ransom notes.
In early November 2023, Cybercriminals at CosmicBeetle aimed to escalate their operations by mimicking the tactics employed by the notorious LockBit group. By mirroring their approach to that of the Noname DLS, they registered the area, but with a key difference: the inclusion of the LockBit logo (refer to Figure 4). For a period, Ransom’s ransom demands were connected to this online platform. The identical inspiration is evident in its resemblance to the noname DLS (Figure 2), displaying simplicity.
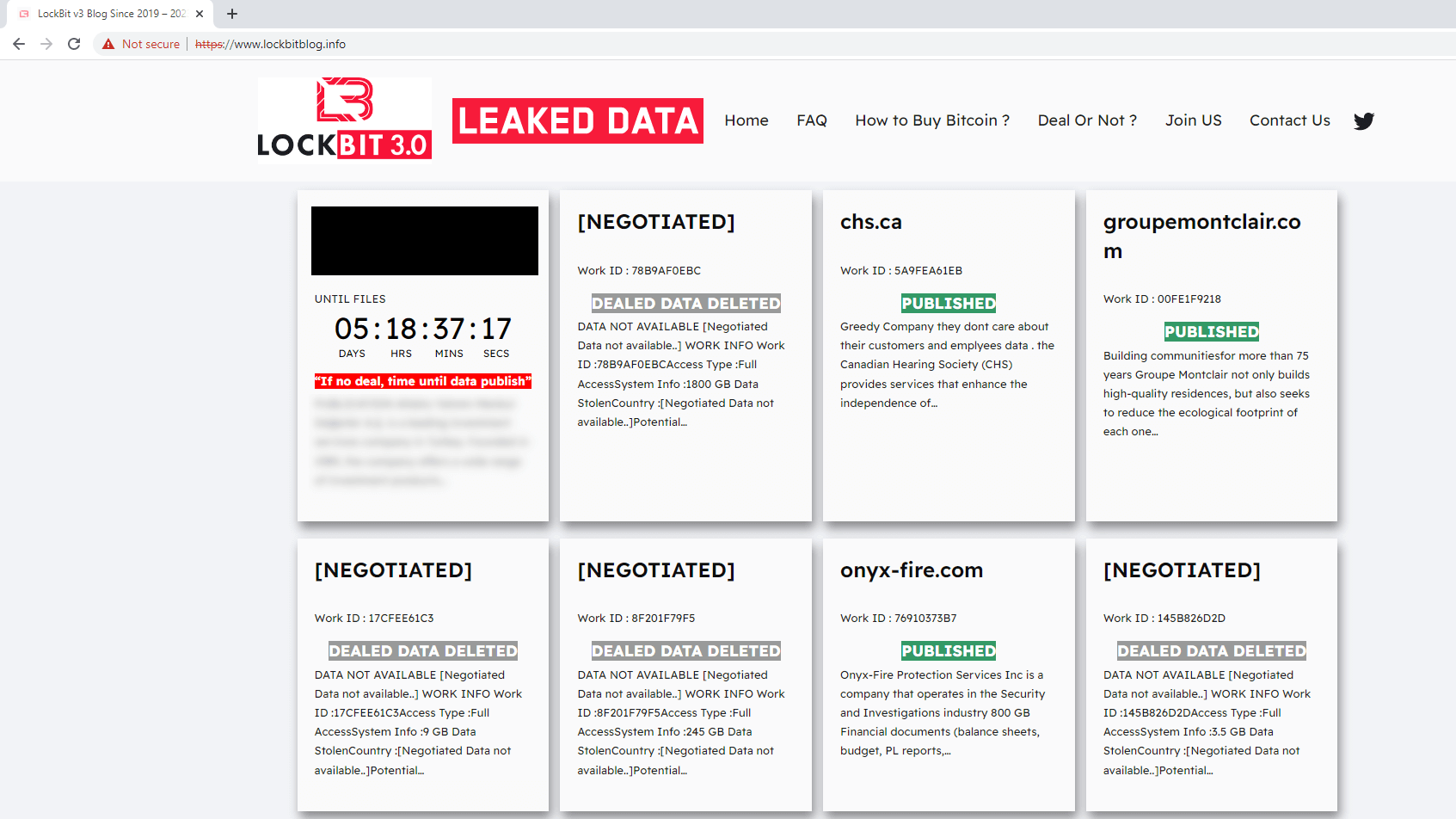
A malware pattern constructed using the leaked LockBit 3.0 builder emerged in August 2022 from Turkey. The distinctive characteristic of this pattern is its incorporation of a ransom message, written in Turkish (refer to Determine 5), which references a specific qTox ID directly connected to CosmicBeetle. According to ESET telemetry, our investigation into a specific instance revealed an intriguing overlap between LockBit and CosmicBeetle’s toolsets, further supporting the suspected connection.
Relation to RansomHub
The practice of leveraging pre-existing malware, commonly known as builder leaks, has become a hallmark technique employed by novice ransomware groups. By doing so, attackers are able to exploit and mimic the attack patterns used by established adversaries, while also gaining access to a reliable ransomware template. We’ve identified a range of ransomware connections beyond the LockBit case alone.
In June, our team conducted a thorough investigation into a significant event related to ScRansom. Based on our comprehensive telemetry data, we have successfully gathered and analyzed the following insights.
- On June 3rdIn February 2024, hackers affiliated with the CosmicBeetle group attempted to extort an Indian production company by threatening to release sensitive data if their demands were not met.
- CosmicBeetle attempted to disable EDR security through an array of process-killing tools.
- On June 8thBy mid-2024, RansomHub’s EDR-killer payload was successfully executed on the very same machine.
- On June 10thIn January 2024, RansomHub was executed on the same machine.
It’s possible that the most effective approach to neutralizing RansomHub’s EDR killer is relatively unconventional. The file was manually extracted from a compressed archive using WinRAR, which had been previously saved to a storage device. It’s rare for RansomHub associates to witness such an execution. Alternatively, this attacker habitually employs the folder to manually extract and execute payloads, a characteristic trait of CosmicBeetle tactics.
According to available data, no public disclosures have been made regarding the RansomHub code or its author; it is possible that RansomHub may be utilizing code acquired from another ransomware group, Knight. Subsequently, with moderate confidence, it appears likely that CosmicBeetle registered as a new RansomHub affiliate.
Technical evaluation
Developed within a framework of precision, ScRansom, part of CosmicBeettle’s curated arsenal, is crafted with the robust programming language Delphi at its core. The earliest available samples were collected by us as of March 31, 2023; however, according to our knowledge, in-the-wild attacks did not commence before August of that year. ScRansom is beneath ongoing growth.
While the graphical user interface appears conventional for Delphi programming, its utility in the context of ransomware is somewhat limited. All Ransom.ScRansom malware variants feature a consistently formatted graphical user interface (GUI). While older samples, dubbed “Static” by builders, necessitate consumer engagement to effectively encrypt data. While the sample’s evasion of detection might seem complicated, it’s actually one reason ScRansom remained undetected for some time; its innocuous appearance when run in evaluation sandboxes belies its potential malicious behavior.
A successful launch of this type of encryptor necessitates a threat actor gaining access to the victim’s device and possessing the ability to control their mouse cursor. While not the first instance of CosmicBeetle employing this approach, it is crucial to note that ScHackTool demands direct interaction with the user’s machine, necessitating manual execution and installation. While the exact method employed by CosmicBeetle to accomplish this goal remains unclear, it’s likely that they exploited VPN access using previously compromised credentials and Remote Desktop Protocol (RDP) connection.
CosmicBeetle has also explored an uncommon variation, specifically the “SSH” type. The encryption mechanism bears resemblance to its counterpart variants; instead of encrypting local files, this variant encrypts files transferred via FTP.
While newer builds leverage automation effectively, this is primarily achieved through a coding process that mimics button clicks. Automated builds, dubbed “Auto” by their creators, typically arrive packaged within a Microsoft Installer (MSI) package alongside compact tools or scripts designed to purge shadow copies. The graphical user interface (GUI) is concealed by default, as depicted in Figure 6, showcasing the most current iteration of this design.
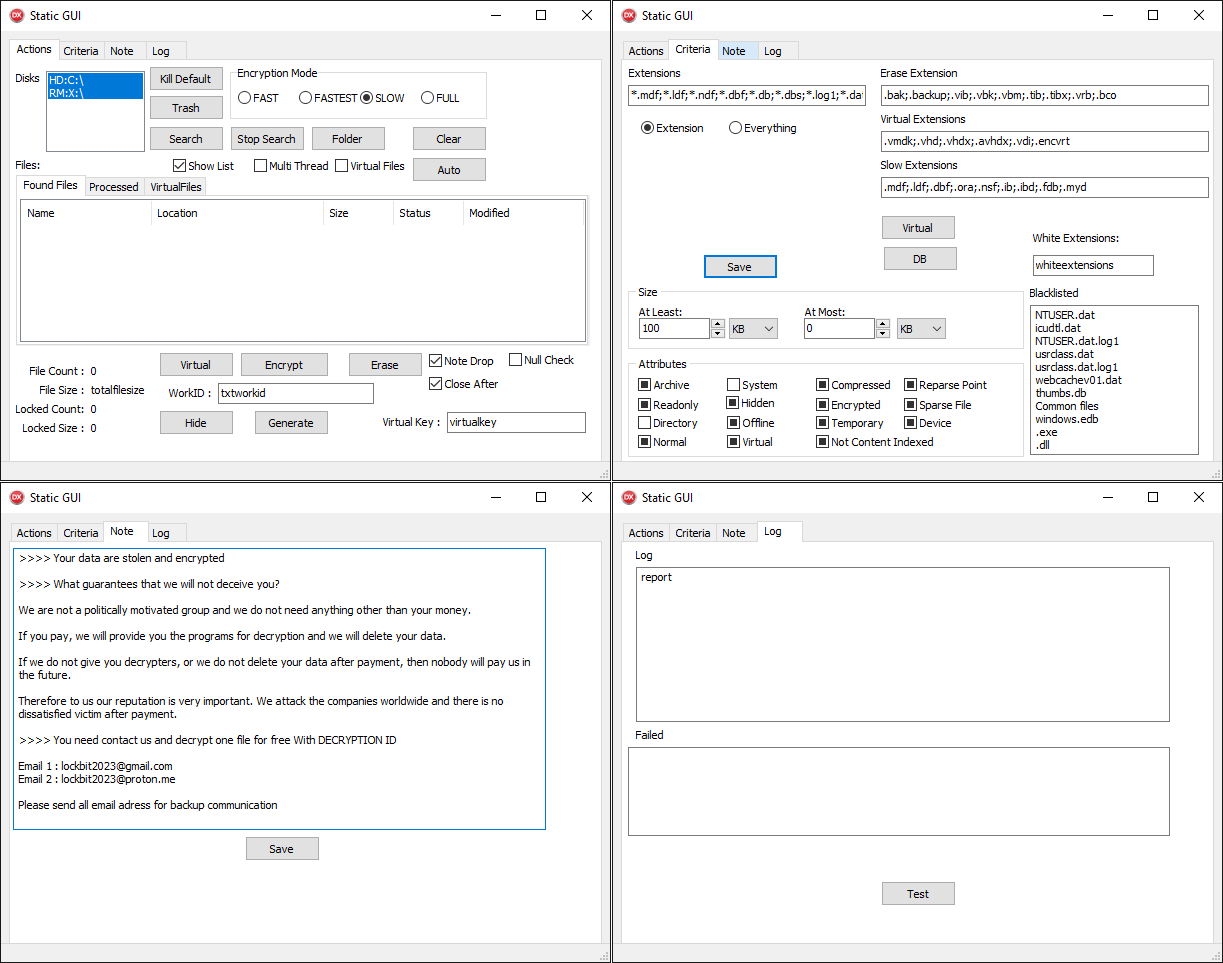
CosmicBeetle’s signature interface often features an elaborate graphical user interface replete with numerous buttons, some of which serve no discernible purpose. Although the graphical user interface’s four-tab design may seem sophisticated at first glance, its underlying performance capabilities are surprisingly straightforward. ScRansom, a ransomware, encrypts data on all mounted, remote, and removable drives, relying on a predefined list of file extensions. This list can be altered via the corresponding text field labeled ” “.
The ScRansom malware uses a partial encryption approach, encrypting only specific parts of a targeted file. 5 encryption modes are supported:
The four primary modes vary solely in their approach to selecting which file components are encrypted by the ransomware. While their usage seems to be still developing, not all available modes are being utilized. While the final mode is indeed necessary, it’s crucial to note that its use can result in unintended consequences: certain sections of targeted files will remain unencrypted, albeit their contents will be altered by an ongoing value, effectively making them irretrievable. The mode used for a given file is determined by a combination of factors, including the radio buttons available in the relevant tab and the file’s extension, which can also influence the selected mode. The listed extensions trigger a unique encryption process, akin to yet distinct from its traditional counterpart. While it is probable that a list of excluded extensions should be compiled for the purposes of encryption, this particular functionality has not been implemented.
When used in conjunction with encryption, ScRansom also terminates a range of processes and services. Recently, a novel Delphi pattern emerged, diverging from the original ScRansom framework and coalescing into a distinct component dubbed ScKill, specifically designed to terminate processes. ScRansom also leverages debug-like features, such as loading extension lists from a file to encrypt data from and customizing ransom note content using a file.
Encryption
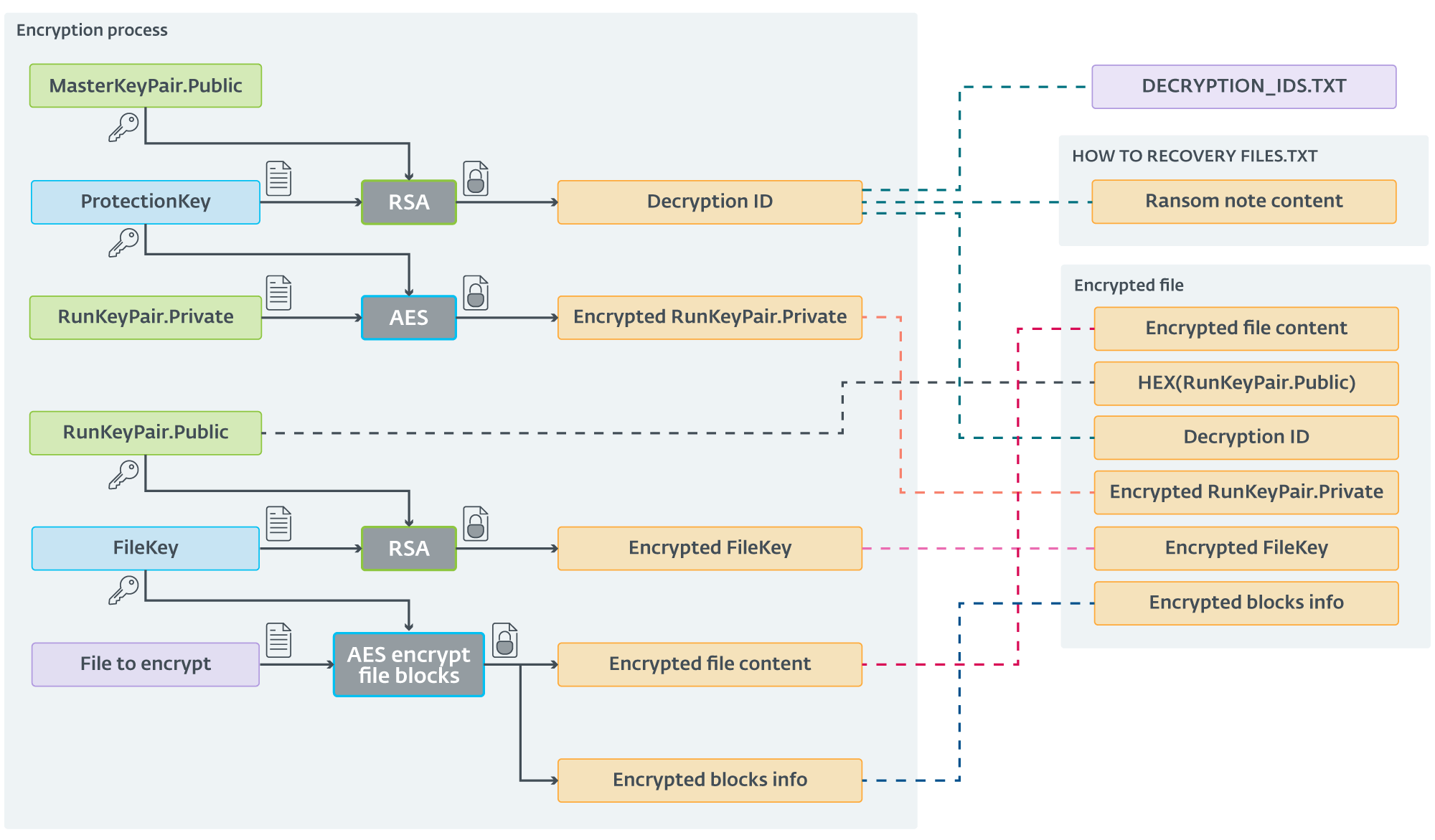
Initial ScRansom samples employed straightforward symmetric encryption with AES-128 in CTR mode. Since December 2023, our encryption scheme has remained current and up-to-date. While the brand-new scheme may seem overly complex at first glance, its innovative approach yields surprisingly effective results. Initially, ScRansom creates a 256-bit AES key labeled ProtectionKey, as well as an RSA-1024 key pair referred to as RunKeyPair.
With each ScRansom pattern employing this novel approach, a predefined public RSA key is embedded from the designated MasterKeyPair combination. The encryption of this public secret utilizes RSA algorithms to generate a unique Decryption ID, as referred to by CosmicBeetle.
A unique AES-CTR-128 key, designated as the FileKey, is generated for every file. The portions of the file are subsequently encrypted using AES encryption with a FileKey. When ScRansom completes encryption of a file, it adds relevant details to the end.
- The data contained in this string – whether a single piece of information or an entire file – has been successfully encrypted.
- The string (“in older builds”), encrypted using AES encryption with a FileKey.
- Transactions denoted by: $
- Hex-encoded RunKeyPair.Public,
- Decryption ID,
- Run Key Pair. The non-public, encrypted portion utilizes AES-CTR-128 with a Protection Key, and
- The file key is encrypted using RSA encryption with the public key from the RunKeyPair.
- Information regarding the commencement of encrypted blocks along with their respective sizes; this detail is omitted in cases where the entire file is encrypted.
The decryption ID is saved in a text file, specifically named, alongside the ransom note titled. Decryption ID . On subsequent executions, the decryption IDs are appended to the file.
The filename, including its extension, is base64-encoded and subsequently combined with the extension itself. Despite the complexity of the entire course, we have succinctly summarized it in seven determinate sections.
Decryption
With the ability to secure a decryptor developed by CosmicBeetle, we are now poised to tackle the most recent encryption scheme that has been puzzling us. The CosmicBeetle app surreptitiously reveals non-public keys to unsuspecting users, only providing the already decrypted ProtectionKey, which demands entry into a designated area. The decryption process relies on the provision of a valid Decryption ID, but since the personal key remains inaccessible, this expectation is rendered ineffective, with the decryptor effectively disregarding its significance. The graphical user interface (GUI) of the decryptor is depicted in Figure 8.
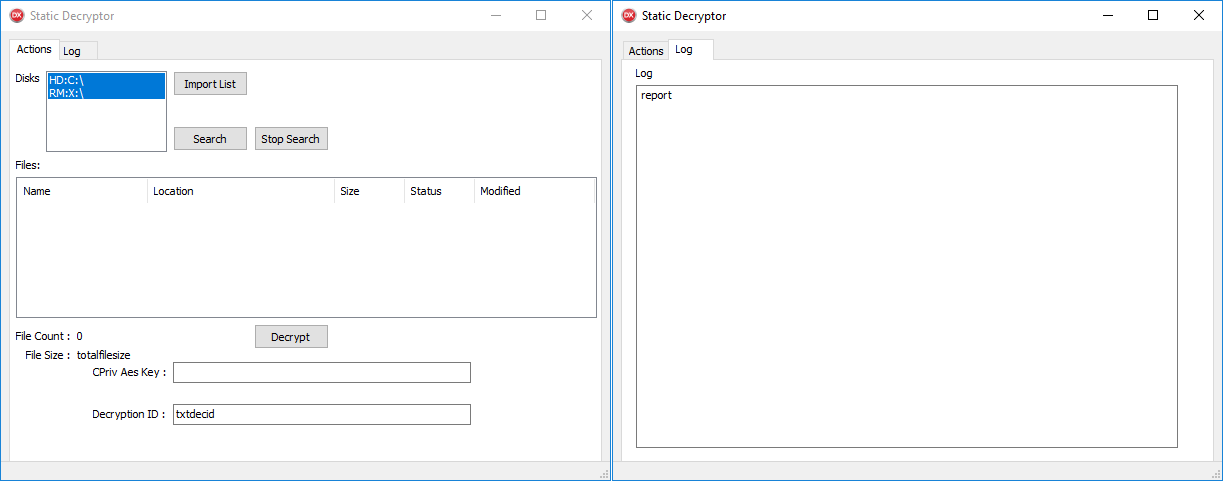
When the correct ProtectionKey is provided, the decryption process unfolds as expected. Victims who opt to pay the ransom must obtain Decryption IDs from the machines where ScRansom was run. CosmicBeetle proposes issuing a singular Protection Key covering all Decryption IDs to provide comprehensive protection. When a ransomware attack occurs, victims are forced to manually execute the decryption tool on each affected device, input the correct Protection Key or authenticate multiple keys, select the decrypt option, and patiently await the completion of the decryption process.
Moreover, our investigation revealed that ScRansom was simultaneously executed on multiple machines, yielding a significantly larger number of Decryption IDs. The individual in question amassed a total of thirty-one unique Decryption IDs, necessitating the procurement of thirty-one distinct ProtectionKeys from CosmicBeetle. Despite efforts, they have struggled to fully improve all their record data. Assuming the encrypted data remained uncompromised, potential causes for these issues may include a lack of sufficient Decryption IDs, incomplete provision of necessary ProtectionKeys by CosmicBeetle, or irreversible damage to files due to ScRansom’s encryption mode usage. This decryption methodology is characteristic of a novice ransomware threat actor.
Experienced criminal organizations strive for a simplified decryption process to maximize successful decryption rates, thereby enhancing their reputation and increasing the likelihood of receiving payment from victims. Typically, when a ransomware attack occurs, such as in cases like the leaked LockBit Black builder, a custom-built decryptor is created simultaneously with the encryptor. Without requiring additional user interaction, the solution seamlessly integrates with the end-user’s existing workflow, leveraging the embedded secrets within the binary itself. Moreover, a single master key is sufficient to unlock and decrypt all compromised data files, regardless of their location within the affected network.
Conclusion
Throughout this blog post, a comprehensive analysis has been conducted on CosmicBeetle’s exercise regimen over the past 12 months. The threat actor has persisted in deploying ransomware, having recently shifted from the Scarab variant to a novel, custom-built strain dubbed ScRansom. It is likely that CosmicBeetle attempted to capitalize on LockBit’s reputation by using a modified version of the malware, possibly to conceal its own vulnerabilities and increase the likelihood that victims would be willing to pay the demanded ransom.
The analysts observed a brief attempt by CosmicBeetle to utilize LockBit samples built with the leaked builder before reverting back to ScRansom. The threat actor dedicates resources to perpetually enhancing ScRansom, refining its encryption mechanics and introducing new features.
Recently, our monitoring revealed a consistent pattern: each week, a single machine was compromised by both ScRansom and RansomHub payloads simultaneously. The atypical execution of RansomHub deviated significantly from the norm, as revealed by ESET’s telemetry data on typical RansomHub instances. Given the lack of public information on RansomHub, it is reasonable to speculate with moderate certainty that CosmicBeetle may have ties to RansomHub as one of its affiliates.
ScRansom experiences sustained growth, a relatively rare occurrence for ransomware. The intricacy of the encryption and decryption process renders it susceptible to errors, thereby casting doubt on the feasibility of restoring all data. Decryption profitability hinges on the decryptor functioning accurately and CosmicBeetle providing vital decryption keys; however, even with these factors in place, certain records may still be irreparably damaged due to the malicious actor’s actions. Despite ideal circumstances, decryption can still prove laborious and intricate.
IoCs
Information
| Win32/Filecoder.Spacecolon.A | Auto variant of ScRansom. | ||
| Win32/Filecoder.Spacecolon.B | Auto variant of ScRansom. | ||
| Win32/Filecoder.Spacecolon.A | Static variant of ScRansom. | ||
| Win32/Filecoder.Spacecolon.B | Turkish-speaking cybercriminals now have a custom-made ransomware at their disposal, dubbed Auto Encryptor variant of ScRansom, designed to target victims in Turkey and potentially other countries where the language is spoken. | ||
| Win32/Filecoder.Spacecolon.A | Novel SSH encryption module in ScRansom’s repertoire. | ||
| Win32/Filecoder.Spacecolon.A | Decryptor variant of ScRansom (oldest). | ||
| Win32/Filecoder.Spacecolon.A Win32/Filecoder.Spacecolon.B BAT/DelShad.E BAT/Agent.OPN | Malicious software package comprising a MSI installer file with embedded ScRansom and ScKill components, as well as two BAT scripts designed to disrupt operations by ceasing provider services and deleting shadow copies respectively. |
Community
| Namecheap, Inc. | 2023‑11‑04 | Pretend LockBit leak website. |
Ransom notice fragments
E mail addresses
Tox IDs
Tor hyperlinks
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Lively Scanning: Vulnerability Scanning | CosmicBeetle methodically surveys its targets to catalog potential weaknesses that might be leveraged for exploitation. | ||
| Data collection on sufferer communities can provide valuable insights into the impact of online hate speech. To achieve this, we require a comprehensive list of internet protocol (IP) addresses associated with perpetrators and victims of online harassment. | CosmicBeetle actively probes the internet landscape to identify and target IP addresses vulnerable to potential exploits, capitalizing on its ability to capitalize on security weaknesses. | ||
| Purchase Infrastructure: Domains | CosmicBeetle has established a dedicated personal leak website portal. | ||
| Develop Capabilities: Malware | CosmicBeetle has developed a tailored toolkit called Spacecolon. | ||
| Get hold of Capabilities: Device | CosmicBeetle leverages a substantial array of third-party tools and scripts to optimize its performance. | ||
| Get hold of Capabilities: Exploits | CosmicBeetle leverages publicly available proof-of-concepts (PoCs) to utilize identified exploits. | ||
| Get hold of Capabilities: Malware | CosmicBeetle is believed to have acquired ransomware from RansomHub, leveraging the leaked LockBit 3.0 builder in this illicit endeavour. | ||
| Exploit Public-Dealing with Utility | Cosmic Beetle exploits weaknesses in FortiOS SSL-VPN and other publicly accessible features to identify potential advantages. | ||
| Person Execution | While CosmicBeetle relies on consumer involvement to operate certain tools, this typically occurs when a malicious actor exploits Remote Desktop Protocol (RDP) vulnerabilities. | ||
| Windows Command Prompt: A Command and Scripting Interpreter | CosmicBeetle successfully automates a variety of tasks by executing multiple BAT scripts and instructions with ease. | ||
| Command and Scripting Interpreter: PowerShell | CosmicBeetle efficiently executes a multitude of PowerShell scripts and commands. | ||
| Create Account: Native Account | CosmicBeetle typically establishes a maliciously controlled administrative account for the attacker’s benefit. | ||
| Legitimate Accounts | Cybercriminals behind CosmicBeetle exploit genuine user accounts with ease, leveraging obtained login credentials to wreak havoc. | ||
| Deobfuscate/Decode Information or Data | ScRAMbled Ransomware samples effectively defend public RSA keys through encryption. | ||
| Brute Drive: Password Guessing | The CosmicBeetle malware employs brute-force tactics to breach remote desktop protocol (RDP) and Server Message Block (SMB) connections. | ||
| Exploitation for Credential Entry | The Cosmic Beetle exploits identified vulnerabilities to obtain sensitive credentials, leveraging its cunning tactics to gain unauthorized access. | ||
| Information Destruction | Cosmic Beetle occasionally fails to recover certain encrypted data files. | ||
| Information Encrypted for Affect | CosmicBeetle encrypts sensitive records data on compromised devices. |
Appendix A: Focused file extensions
This configuration is hard-coded within each ScRansom pattern and is susceptible to frequent changes. As of the current date, this content incorporates the most recent settings at the time of composition.
Filename masks to encrypt
| | | | | |

