
Background
ClickFix has shortly turn out to be a rampant social-engineering tactic. First noticed again in October 2023, it goals to trick customers into pasting instructions into the run dialog field underneath the guise of verifying the consumer’s connection and authenticity to the area. Given its ease of use and talent to bypass technical safety measures, adoption of ClickFix has been rising at an alarming price. [1]
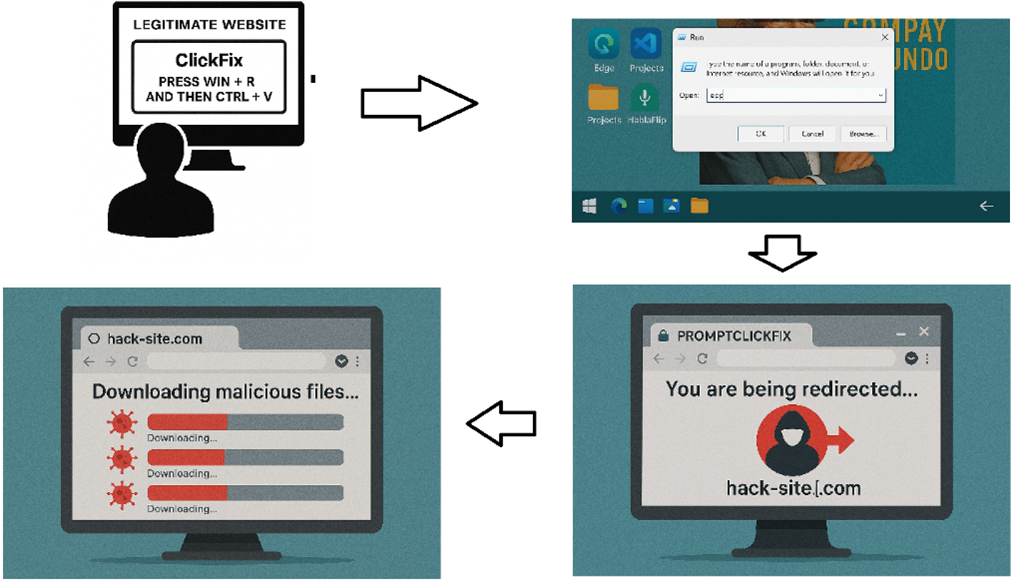
Government Abstract
This investigation started after a consumer was noticed navigating to a authentic web site that prompted the consumer with a pretend Captcha immediate. As soon as the Faux Captcha immediate directions had been carried out, a command to a malicious area led to malicious scripts and file downloads on the consumer’s asset.
The Interlock ransomware group was first noticed in September 2024. In contrast to most ransomware teams seen at this time that make use of Ransomware as a Service (RaaS) fashions, this was an unbiased group. They gained notoriety again in October 2024 after they claimed duty for the Texas Tech College Well being Sciences Middle incident that compromised the information of roughly 1.5 million sufferers.
In January 2025, researchers at Sekoia noticed Interlock increasing their ways and leveraging the Social Engineering method now referred to as ClickFix. [2]
Investigation
The Degree Blue MDR group noticed two alarms on the identical endpoint from Sentinel One which prompted additional investigation. In the course of the investigation, our analysts uncovered the menace actors’ ways, methods, and procedures (TTPs) and recognized indicators of compromise (IOCs) related to the Interlock ransomware group. Because of the swift motion of the LevelBlue MDR group, the assault was contained, and the hashes from the investigation had been added to the blocklist inside SentinelOne.
Learn the complete weblog and study key takeaways from LevelBlue’s investigation, together with suggestions to stop these assaults from affecting your group.
[2] https://weblog.sekoia.io/interlock-ransomware-evolving-under-the-radar
The content material offered herein is for common informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals concerning particular obligations and threat administration methods. Whereas LevelBlue’s Managed Risk Detection and Response options are designed to assist menace detection and response on the endpoint stage, they don’t seem to be an alternative choice to complete community monitoring, vulnerability administration, or a full cybersecurity program.

