Datadog’s apex safety advocate is cautioning Australian and APAC businesses to hasten the retirement of legacy credentials linked to prominent hyperscale cloud providers, citing ongoing risks associated with their widespread use.
According to an interview with TechRepublic, Andrew Krug drew attention to key takeaways from Datadog’s latest research, underscoring the pervasive danger posed by lingering credentials. While credential administration practices have been improving, Krug notes that they are not advancing as quickly or effectively as desired to mitigate risks.
Extended lifecycles for credentials pose a significant threat to cloud security.
According to the report, nearly half (46%) of companies leveraging Amazon Web Services (AWS) rely on Identity and Access Management (IAM) customers, specifically a type of persistent credential known as “long-lived credentials”, per Datadog’s terminology. Despite the use of centralized identity management systems allowing access through multiple channels by organizations, this remained a reality.
Despite the widespread adoption of Identity and Access Management (IAM) solutions, approximately one-quarter of respondents continued to rely solely on IAM customer implementations without adopting centralized federated authentication mechanisms. While efforts to standardize centralized identity management are gaining momentum, the persistence of unmanaged users holding onto outdated credentials remains a pressing security concern.

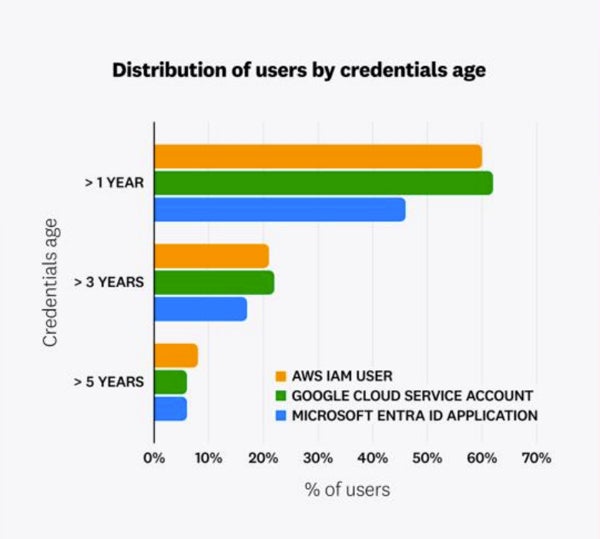
The persistence of lingering credentials often comprises dormant or obsolete entry points. A staggering 62% of Google Cloud’s service accounts, 60% of AWS IAM customers and 46% of Microsoft Azure Active Directory Identity (AAD) functions revealed the alarming presence of legacy entry keys – those exceeding one year in age?
Old records pose a significant risk of data compromises.
According to Datadog, cloud credentials that persist indefinitely are prone to being compromised through unsecured supply code, container images, build logs, and software artefacts, ultimately exposing organisations to significant security risks. Despite efforts to strengthen security measures, misconfigured cloud services have consistently emerged as the leading cause of publicly documented cloud-related security breaches.
Existing mature tooling provides robust mechanisms to prevent secrets and techniques from inadvertently entering production environments, such as advanced static code analysis tools. According to Datadog’s report, there has been a notable uptick in the enforcement of IMDSv2 for AWS EC2 instances, a crucial security measure designed to prevent credential theft and safeguard against potential attacks.
Despite a scarcity of enduring credentials, progress remains frustratingly slow.
Strikes have been implemented to address the problem, evoking parallels with AWS’ launch of its Identity and Access Management (IAM) Identity Centre, which enables organizations to centrally manage access to AWS resources. While corporations adapt to the evolving service landscape, Krug expressed uncertainty, saying, “I’m not convinced that…”
As he underscored, long-standing entry key pairs, coupled with excessively lenient access controls, have been the primary catalysts behind these high-profile security incidents. “If we eliminate just one aspect, we significantly diminish the likelihood of success for the venture.”
The lingering issue of outdated credentials is a global challenge that transcends geographical boundaries, affecting organizations across the globe.
APAC isn’t inherently distinct from the rest of the world in its nature. Without standardized regulations governing the management of long-lived credentials across multiple cloud jurisdictions, global corporations often employ similar strategies when working with various cloud providers, frequently spanning multiple international territories?
What’s hindering the shift from prolonged authentication methods?
Difficulty in transitioning groups to single sign-on and short-term credentials has hindered the widespread adoption of these practices. The transition of migration workflows to a single sign-on system will significantly benefit from addressing the “carry and shift” concerns raised by Krug. The gradual adoption of new approaches is largely hindered by the need for a paradigmatic mindset shift, with organisations being equally responsible for providing sufficient guidance and support to facilitate group adaptation.
Notwithstanding his fame, instruments like the AWS Identification Centre, available for three years, have facilitated this shift. By simplifying the authentication process, minimizing the need for frequent multi-factor authentication (MFA) logins, and ensuring seamless workflows while preserving eco-friendliness.
“AWS Identification Centre has proven its value by facilitating smooth customer experiences, but many of us are still in the process of transitioning to this platform,” Krug said.
With your esteemed reputation, you must leverage your credentials to advance in your career and take on more significant challenges.
According to Datadog’s report, it is unrealistic to expect that long-lived credentials will be managed in a secure manner. The seller advises leveraging short-lived credentials and proactively monitoring updates to APIs commonly exploited by attackers.
The organisations should capitalise on systems that offer timely, temporary certifications.
Workloads. Datadog noted that achieving this workload visibility will require the implementation of IAM roles for EC2 instances or EKS pod identification in AWS, managed identities in Microsoft Azure, and service accounts linked to workloads for Google Cloud, assuming organizations utilize the major hyperscale cloud providers.
Datadog recommends that companies centralize identity administration for human customers using solutions like AWS IAM Identity Center, Okta, or Microsoft Entra ID. It advises against the use of individual cloud accounts for each employee, labeling this approach as “extremely inefficient and risky.”

