
Mishaal Rahman / Android Authority
TL;DR
- Android 15 bars untrusted applications from scrutinizing sensitive notifications, even when they have permission to access all notifications.
- Prior to Android 15, applications with notification access could capture all incoming notifications, including those containing one-time password (OTP) codes, potentially compromising users’ sensitive information.
- Now, while trusted apps are solely able to learn one-time password (OTP) codes from notifications.
The notifications panel on your cellphone holds a rich repository of sensitive information, comprising not only personal messages, but also crucial security codes dispatched by online services you’ve authorized. That’s why numerous malicious applications consistently try to deceive users into providing them with access to notifications, thereby enabling the theft of those highly valuable two-factor authentication codes. Fortunately, replacing this feature makes it significantly more resilient against malicious applications attempting to extract two-factor authentication codes from notifications.
Since Android introduced its Notification Listener API, third-party apps have had access to users’ notifications. Since sensitive information may be included in notifications, app developers cannot access the Notification Listener API without obtaining user consent first. To enable an app’s notification access, you must manually grant it permission through the Settings app; conversely, apps can facilitate this process by opening the relevant Settings webpage where you can grant the necessary permissions.
Mishaal Rahman / Android Authority
Upon gaining notification access, an app can learn, respond to, dismiss, or manage either all phone notifications or the specific subset to which it was granted permission. While that notification might contain something as sensitive as a two-factor authentication code, the Notification Listener API enables applications to identify and extract such information.
The Android operating system has introduced a series of modifications designed to enhance the security of sensitive information, such as two-factor authentication codes, by categorizing these notifications as “delicate” and restricting access to authorized “trusted” Notification Listener providers only? Any unauthorised Notification Listener attempting to acquire sensitive information, including two-factor authentication codes, will be met with a blunt response: “sensitive data protected.”
Here’s a concise video illustrating the implications of this variation on Notification Listeners in Android 14 compared to Android 15. Watch as we demonstrate the vulnerability on a tool-working Android 14 device, where an app with notification access learns two-factor authentication codes embedded within notifications. While sharing the same permissions, an app on an Android 15 device fails to receive notifications containing two-factor authentication codes when running on a physical machine.
Beneath the surface, the ASI application processes all notifications before forwarding them to Notification Listener services. When ASI identifies that a notification contains a two-factor authentication code, it will trigger the system to flag it as “delicate” and prevent untrusted Notification Listener entities from receiving it. Companies offering “untrusted” notification listener services cater to apps that struggle to uphold their brand reputation. RECEIVE_SENSITIVE_NOTIFICATIONS Permission that Google has introduced in Android 12.
This permission can be granted exclusively to apps that are digitally signed with the system-issued certificates or possess specific system-defined roles. Many of the positions that could potentially receive the RECEIVE_SENSITIVE_NOTIFICATIONS Permission to access certain Android features and functionalities can be held exclusively by system apps; however, some permissions may also be granted to third-party apps, such as those requiring camera or microphone access. COMPANION_DEVICE_WATCH, COMPANION_DEVICE_GLASSES, and HOME. Respectfully, we examine companion apps for companions, smart glasses’ companion apps, and the default launcher. Third-party apps capable of learning notifications with two-factor authentication codes on Android 15 include those that integrate with your smartwatch, your augmented reality glasses, and your default home screen launcher application.
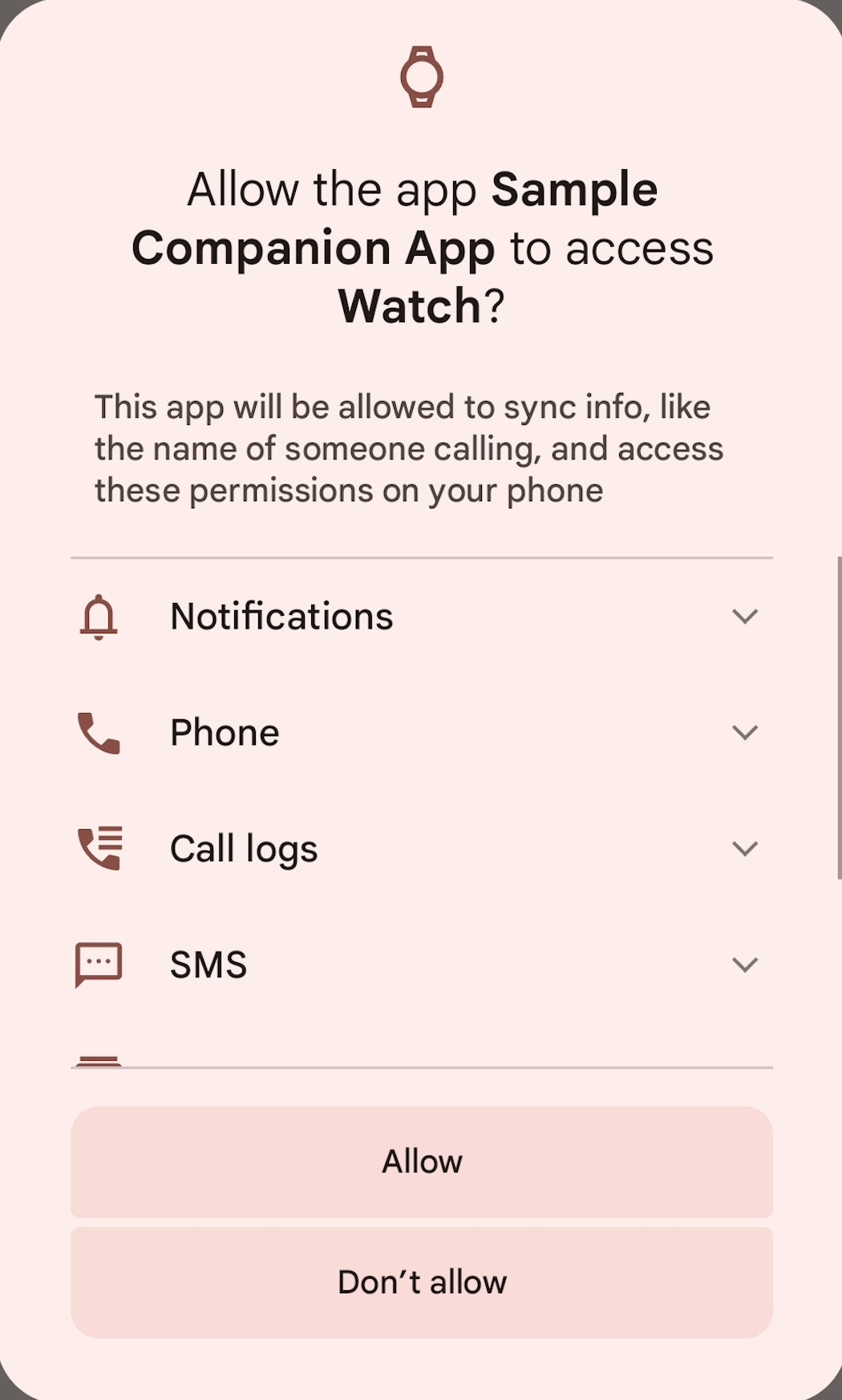
What kind of request are you making to this companion device? Please select one: WATCH?
Implementing measures to prevent third-party apps from accessing two-factor authentication notifications, a vital step in thwarting hacking attempts, will inevitably also disrupt certain automation and convenience tools like “Copy SMS Code,” a free and open-source app that I previously relied on to document these changes. While there’s a straightforward workaround to revive previous habits, I’m not fond of suggesting it. This process involves disabling the Wi-Fi settings on devices. While this code prevents ASI from parsing notifications and incorrectly labeling ones containing two-factor authentication codes, it also has the unintended consequence of disabling all urged actions or replies. One alternative solution involves leveraging and utilising Android Debug Bridge (ADB) to manually assign the RECEIVE_SENSITIVE_NOTIFICATIONS permission utilizing the next command:
Code
adb shell cmd appops set --user 0 <PACKAGE> RECEIVE_SENSITIVE_NOTIFICATIONS enableRight here, <PACKAGE> Is the bundle identified as the one requiring permission to proceed with the application? While it’s crucial for influential consumers to carefully evaluate the impact of changes on their instruments or systems, it’s often best to make adjustments with caution to avoid disruptions.
While Android’s subtle updates to improve safety are welcome, it would be beneficial for Google to formally document these changes, considering their potential impact on app behavior. Android could potentially refine its notification system by introducing selective blocking of sensitive notifications from appearing on the lock screen, a feature Google has been experimenting with since my initial reporting in February; we may see this innovation in an upcoming Android update.

