In recent years, the UEFI threat landscape has undergone significant development, particularly with regards to UEFI bootkits. The concept of a primary UEFI bootkit proof-of-concept (PoC), introduced by Andrea Allievi in 2012, marked the beginning of deploying bootkits on contemporary Windows systems based on UEFI firmware. This initial innovation sparked a series of subsequent PoCs from various researchers. It wasn’t until 2021 that the first two actual UEFI bootkits were discovered in the wild, with credits going to both ESET and Kaspersky. Two more years passed before a notorious variant emerged, notable for being the first able to bypass UEFI Safe Boot on up-to-date systems, which was detected by ESET in 2023.
The bootkit’s primary objective is to circumvent the kernel’s signature verification mechanism, thereby allowing it to load and execute two arbitrary ELF binaries through the Linux boot process, which is the sequence of events initiated upon system startup. During our assessment, we discovered an unsigned kernel module with characteristics indicating potential connections to the same developers who created the original bootkit, which loads an unknown kernel module via an ELF binary.
- In November 2024, an previously unknown UEFI utility, dubbed ” “, was unexpectedly uploaded to the .
- Preliminary analysis revealed that it’s a UEFI bootkit, specifically “Bootkitty” as designated by its developers, with the notable distinction of being the first and only UEFI bootkit primarily targeting Linux, including various Ubuntu distributions.
- As Bootkitty relies on self-signed certificates, it should not be capable of functioning on systems utilizing UEFI’s Safe Boot feature unless the attacker’s certificates are installed first.
- Bootkitty is engineered to integrate seamlessly with the Linux kernel, regardless of whether UEFI Safe Boot is enabled or disabled, as it patches and verifies the necessary features prior to GRUB execution.
- Incorporates numerous artifacts implying that this is more akin to a proof-of-concept than the handiwork of a skilled and calculated threat actor.
- We discovered a potentially linked kernel module, designated as BCDropper, responsible for deploying an ELF executable capable of loading another kernel module.
Bootkitty overview
Given the discussion in the introduction, evidence suggests that Bootkitty may comprise multiple artifacts indicating a proof-of-concept rather than actively employed malware. Upon examining these artifacts, as well as other foundational information regarding the bootkit,
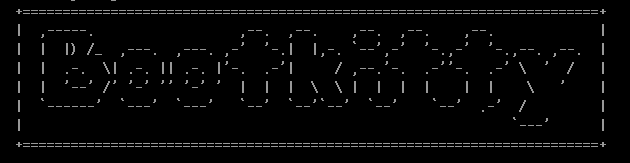
Bootkitty incorporates two underutilized functionalities, enabling the printing of specific strings to the display screen throughout its operation. The primary function’s output, as visualized in Figure 1, enables the printing of ASCII art that we deem represents a hypothetical representation of the bootkit, dubbed “Bootkitty.”
The second performance note prints textual content as depicted in Figure 2, outlining a list of suspected bootkit authors and other individuals who may have contributed to its development. The profile mentioned in the image can be found on GitHub, yet it lacks public repositories referencing or discussing a UEFI bootkit project. Consequently, we cannot confirm or refute the legitimacy of the names presented in the bootkit.
During each iteration of the boot process, Bootkitty displays the strings outlined in Table 3 on the screen.
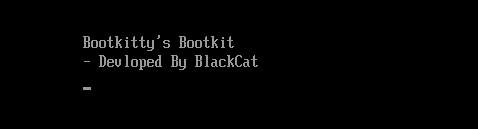
The reference to the term “BlackCat” is also mentioned in further detail within a subsequent loadable kernel module discussed later on. Despite the uncertainty surrounding the perpetrator’s identity, experts conclude that no evident link exists between the unknown actor and the notorious ALPHV/BlackCat ransomware gang. The distinction stems from BlackCat being a moniker employed by researchers, whereas ALPHV, the actual group, created Bootkitty in C and exclusively crafts its malware in Rust.
As discussed previously, BootKitty currently supports a limited number of protocols. To identify the desired changes, it leverages predefined byte patterns. While byte-pattern matching is a conventional approach in dealing with bootkits, the researchers’ utilization of suboptimal patterns for concealing various kernel and GRUB versions resulted in the bootkit being functional only within a limited scope of configurations. The limitations on bootkit usage are primarily due to its method of patching the decompressed Linux kernel, as illustrated in Figure 4; upon decompression of the kernel image, Bootkitty simply duplicates the malicious modifications at predetermined offsets within the kernel image.
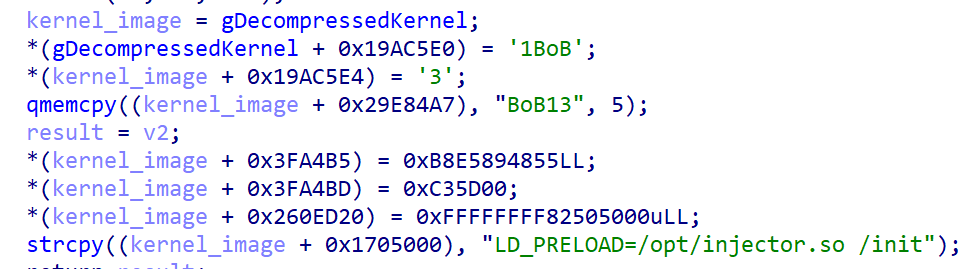
We will delve into the nuances of bootkit kernel patching later; for now, note that the absence of kernel-version checks in the performed exploit (illustrated in Figure 4) enables Bootkitty to potentially overwrite arbitrary code or data at these hardcoded offsets, resulting in a system crash rather than successful exploitation. These details serve as crucial evidence for substantiating one’s concept. While potentially a non-production-ready prototype of malicious software crafted by threat actors,
Ultimately, the bootkit binary is signed with a self-signed certificate, as demonstrated in Figure 5.
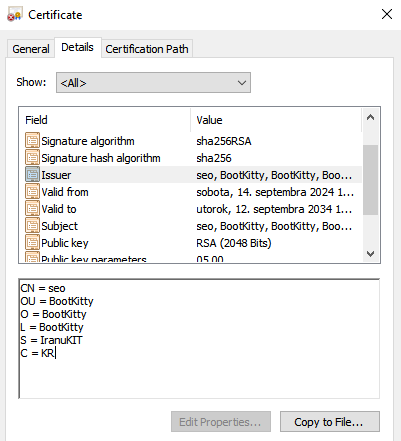
Techical evaluation
Three key components that receive our undivided attention are:
- Execution of the bootkit and patching of the authentic GRUB bootloader: Critical factors 4 and 5 determining successful deployment.
- Patching the Linux kernel’s EFI stub loader: key considerations for factors six and seven.
- Patching the decompressed Linux kernel image: factors 8 and 9 in Determine 6.
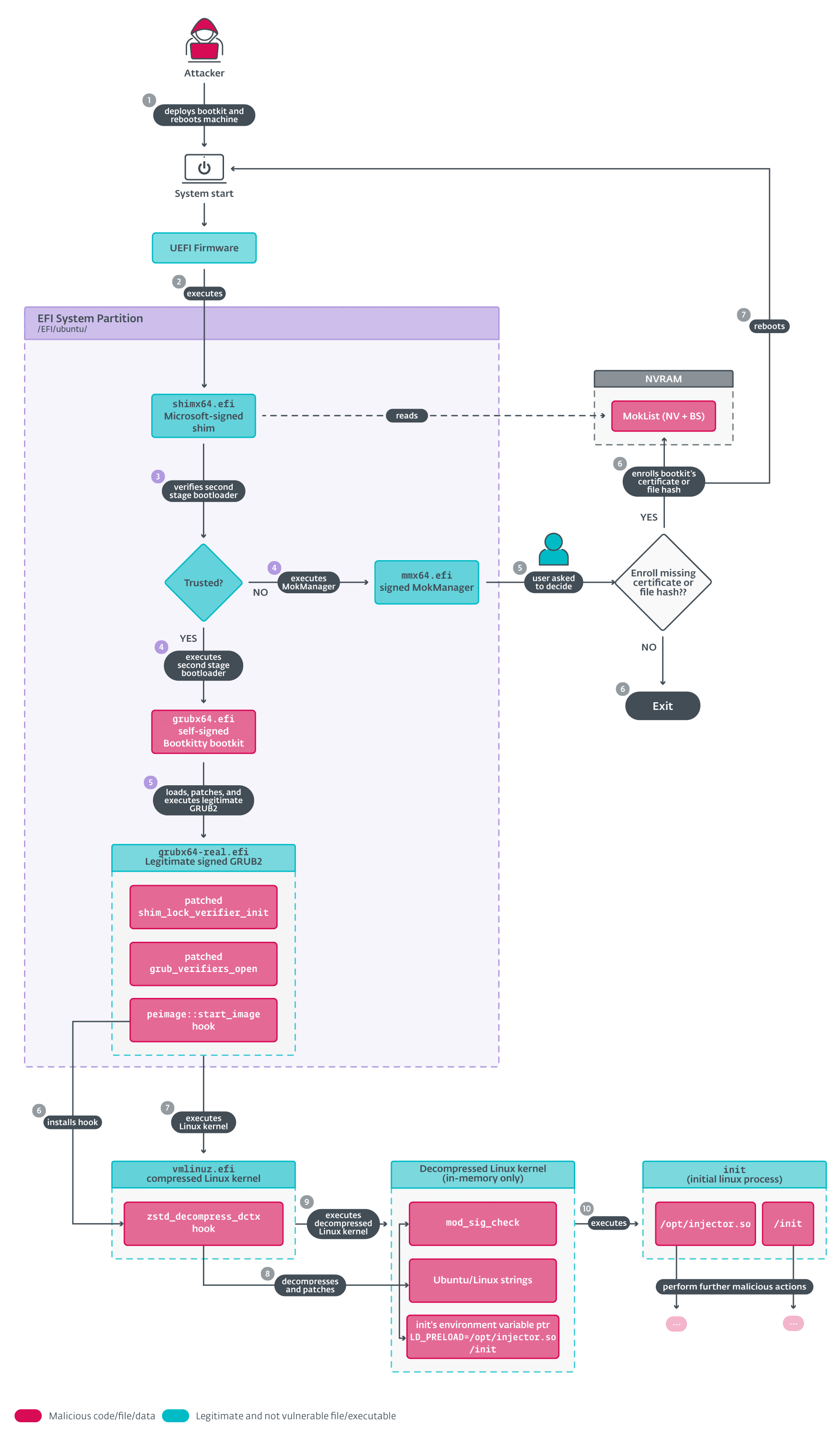
Initialization and GRUB hooking
After being executed by the shim, Bootkitty checks whether UEFI Safe Boot is enabled by examining the value of the relevant UEFI variable. If enabled, it proceeds to hook two features from the UEFI authentication protocols as outlined in Figure 7.
- The hash check algorithm is employed by the firmware to verify the authenticity of UEFI PE images. Bootkitty’s hook performs modifications to ensure the output always indicates a successful verification, thereby returning.
- The firmware leverages this mechanism to implement platform-specific coverage strategies based on various authentication status values. The bootkit’s hook is designed to always return a valid response, enabling the firmware to access the file regardless of its exact authentication status.
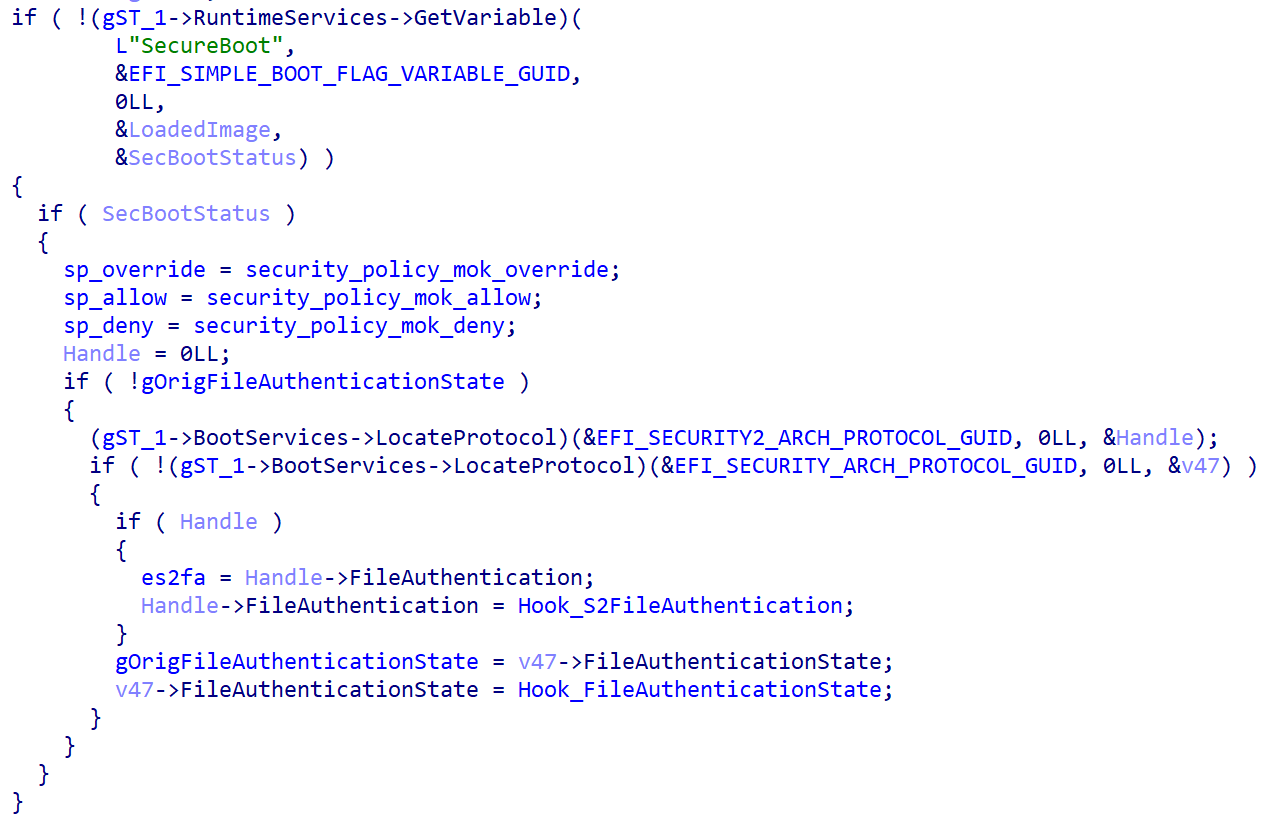
Upon verifying the status of UEFI’s Safe Boot mode, Bootkitty then proceeds to load the genuine GRUB configuration from its pre-defined location on the EFI system partition. This file serves as a malicious backup, created by the perpetrator, of an authentic GRUB. As soon as GRUB is loaded, the bootkit commences modifying and intercepting the subsequent code within GRUB’s memory space:
- The performance metrics are calculated and displayed within the GRUB module, a self-contained component of GRUB. The performance of this code segment is responsible for initializing a pre-existing PE image, which is subsequently invoked by GRUB to initiate the Linux kernel’s EFI stub binary, commonly referred to as efi.stub. The hook performs by exploiting the fact that, during its execution, vmlinuz has already been loaded into memory (although not yet executed), and modifies the function responsible for decompressing the Linux kernel image within vmlinuz; note that, in some cases, due to how the Linux kernel is compiled, it may be quite challenging to identify the precise function being patched; however, we assume that this time it should be the function. Details regarding the decompression hook can be found within this section.
- When UEFI Safe Boot is enabled, the Perform function must be manually activated as part of the verifier mechanism within GRUB. The boot loader is responsible for determining whether to verify the information provided (such as GRUB modules, Linux kernels, and configurations) during the boot process. The put-in hook, however, is complicated and its creator’s intentions are unclear due to its modification of ‘s output, setting the output flag to 2 for any file type provided, which should, according to the documentation, enhance security further. Because the subsequent level’s hook precludes the need for shim_lock_verifier_init to run during boot, it becomes redundant and irrelevant.
- The perform. When invoked by GRUB, this performer is responsible for verifying whether any GRUB file verifiers, including those previously described, demand integrity checks on the file being loaded. The performer is hijacked by the bootkit, bypassing typical protocol and immediately returning without initiating further signature checks; this implies it does not even execute the previously hooked function.
Linux kernel picture decompression hook
This script is responsible for applying a decompressed Linux kernel image. Before the kernel image is decompressed, the hook is executed. It reinitializes the decompression routine’s original byte count and then executes the original decompression function to decompress the kernel image before proceeding with kernel patching.
Because the kernel has been decompressed and remains unaltered in memory, the hook code modifies it at predetermined offsets, making changes exclusive to the memory space. Notably, as demonstrated in Determination 8, it:
- The rewritten kernel model seamlessly integrates with existing frameworks to optimize system performance, rendering this textual content largely irrelevant.
- Hooks the perform.
- Set the patch pointer to the primary surrounding variable of the course.
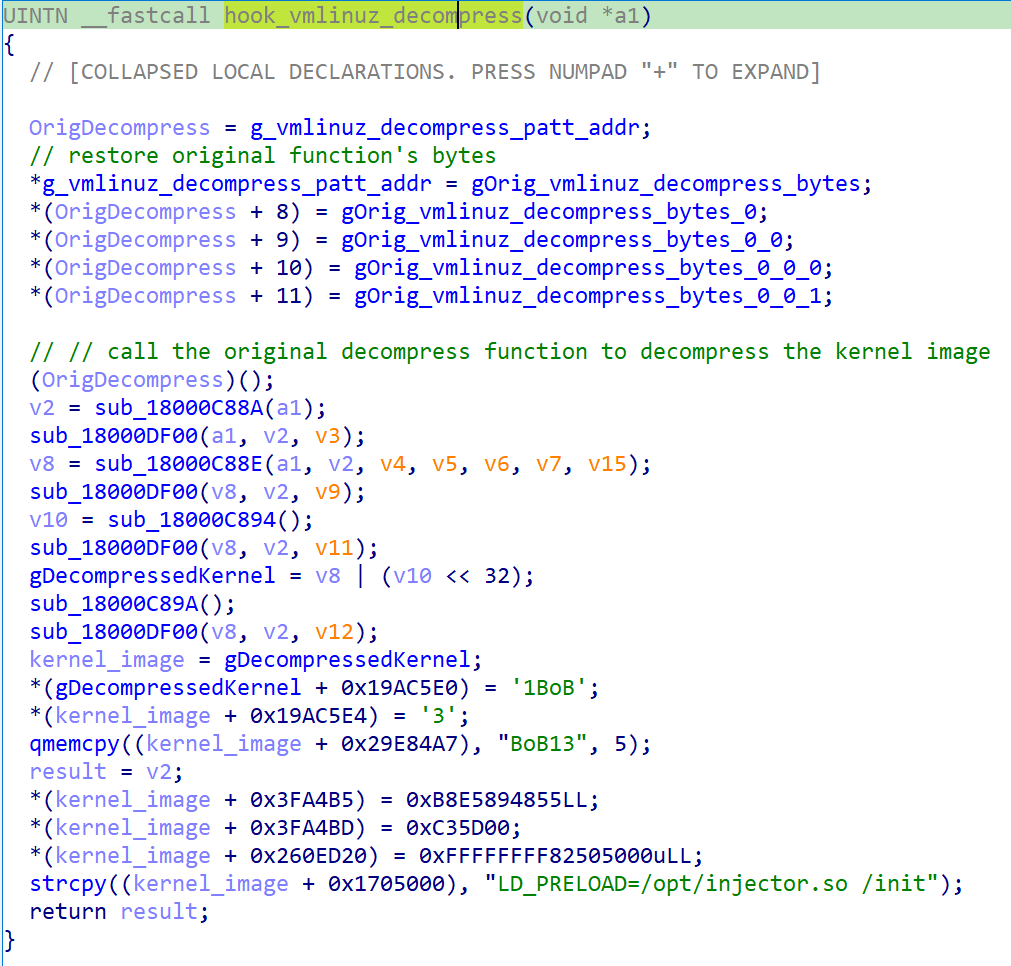
The performer is patched to operate at all times effectively. The performer responsible is accountable for verifying whether a module is correctly authenticated. When patching the kernel’s performance to return, the system will load any module without verifying its digital signature. On Linux systems utilizing UEFI’s Secure Boot feature, kernel modules intended for loading must be digitally signed. When constructing the kernel, this is also true if enabled or passed as a kernel command-line argument, as outlined in the relevant documentation. The possible scenario is that a minimum of one malicious kernel module is loaded subsequently, as a result of the dropper’s analysis having been undertaken.
When a Linux kernel boots, its primary executable is init, sourced from a hardcoded path starting with /sbin/init, accompanied by command-line arguments and environmental variables. The `primary` surroundings variable is replaced by a dot (`.`). The LD_LIBRARY_PATH environment variable is used to load ELF shared objects earlier than others, allowing for the overriding of certain features. A popular method used by cybercriminals to deploy harmful software executables. When the initialization process starts, both the 32-bit and 64-bit ELF shared objects are loaded. This ambiguity stems from the fact that the purpose behind the inclusion of the second component is unclear.
As we finalize this blog post, it’s reassuring to note that our search for potentially malicious ELF shared objects has yielded no matches. Now it’s evident that they’re employed solely as a means of progressing to the next level.
Impression and remediation
Aside from dynamically loading unknown ELF shared objects, Bootkitty leaves a trail of evidence within the system. The primary objective appears to be the optional, non-essential adjustment of the kernel model and Linux banner strings. The previous may be seen by operating Determine 9, and the latter by operating Determine 10.
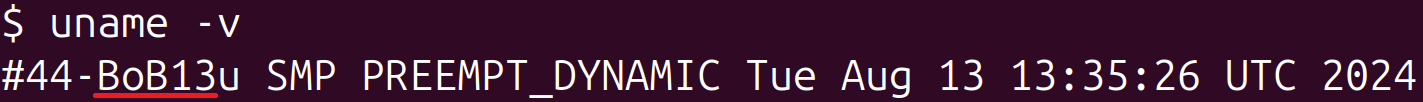
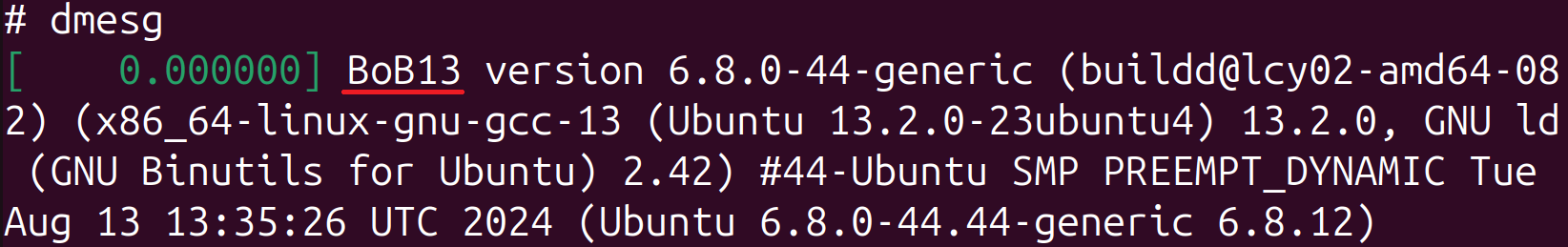
During our assessment, the command’s output also provided details regarding the execution of the initialization process. As shown in Figure 11, the method was executed with the surrounding variable initially set to _______________ and subsequently modified by the bootkit to ___________________.
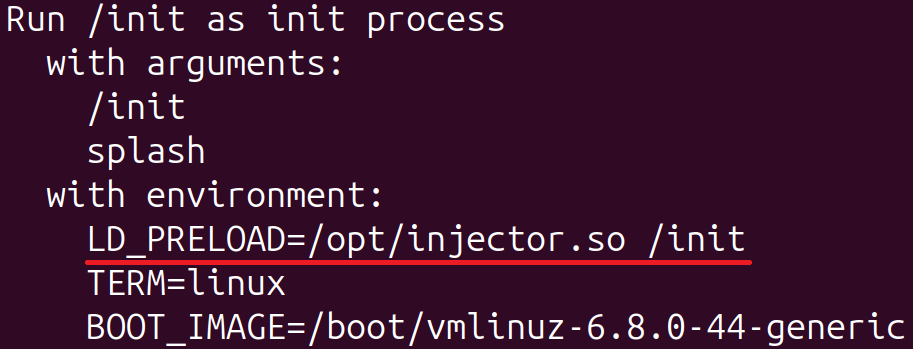
Determine whether the phrase within the initial line matches the original program in initramfs, which ultimately transfers control to systemd by default in Ubuntu installations. The existence of the surroundings variable can be confirmed by examining the file.
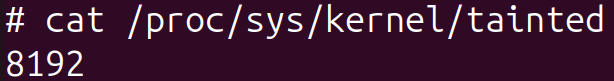
Upon booting the system with Bootkitty in our controlled environment, we observed that the kernel was flagged as a specific value, verifiable through the command from Determinate 12, whereas this scenario did not occur in the absence of the bootkit. When determining whether a bootkit is up-to-date on a system equipped with UEFI’s Safe Boot feature, another viable method involves attempting to load an unsigned dummy kernel module during runtime. When the module is up-to-date, the system loads it without issue; if outdated, the kernel rejects its installation.
A simple solution to eradicate the malware is to restore the genuine file to its original directory, typically found in. This can ensure shim executes the genuine GRUB, thereby allowing the system to boot without the bootkit’s interference.
BCDropper and BCObserver
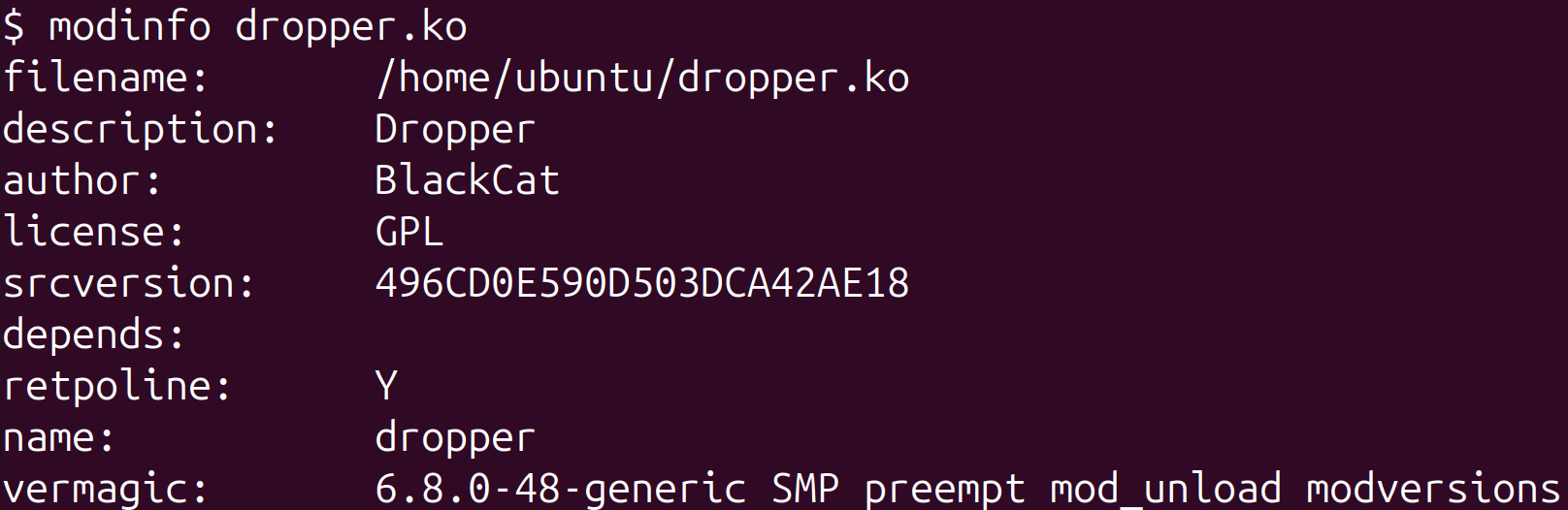
The investigation uncovered a likely associated unsigned kernel module, which we dubbed BCDropper. We uploaded this module to VirusTotal simultaneously with the bootkit, using the same submitter ID, suggesting that it may have been developed by the same creator as the bootkit, evidenced by similarities such as:
- A specific substring within the command’s output, as demonstrated in Section 13.
- One notable presence of the string within the debug paths within the module’s binary is demonstrated in Figure 14, and it is further substantiated.
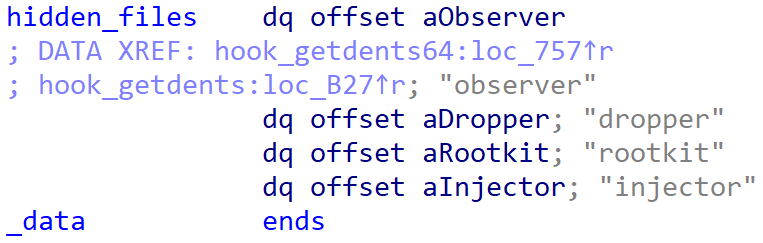
- The feature enables the concealment of specific directory entries from display in directory listings. As demonstrated in Figure 15, one of several hardcoded filename string prefixes utilised to exclude these entries is notable; Bootkitty attempts to preload a shared library from the trail.
Despite the provided proof, it remains uncertain whether the kernel module was designed for or developed by the same person responsible for Bootkitty. The kernel model discussed in Section 13 should not be supported by the bootkit.
Here is the rewritten text:
The kernel module, designed to drop a specifically named embedded ELF file, dubbed BCObserver, does so with the intention of executing it via (Determine 17). On top of that, the module conceals itself by. The kernel module incorporates various rootkit-oriented capabilities, such as concealing information (as described in Section 15), processes, and open ports; although these features are not currently leveraged by the dropper.
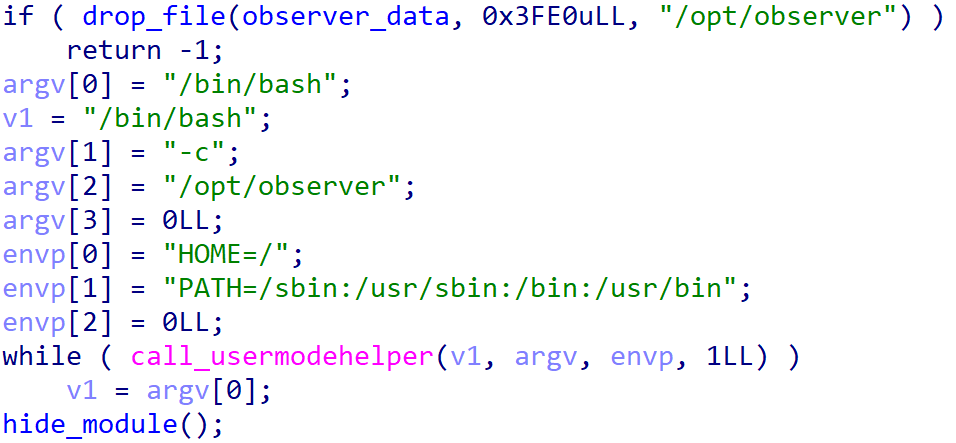
The BCObserver is a straightforward tool that waits until the show supervisor is active, then loads an unknown kernel module into the system via its name. By waiting for the show supervisor to begin, the code guarantees that the kernel module is loaded once the system has completed its boot-up process entirely.
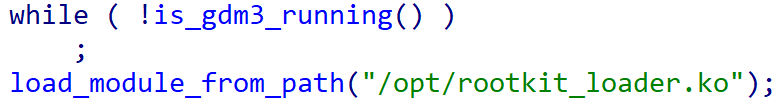
While there’s no conclusive evidence linking the dropper to the bootkit, it’s plausible that the dropper is designed to facilitate its execution. Notably, the bootkit’s ability to load unsigned kernel modules – as demonstrated by the presented dropper – seems a logical purpose for such patches.
Conclusion
BootKitty’s emergence marks a landmark shift in the UEFI threat landscape, upending the notion that UEFI bootkits are exclusively Windows-based attacks. Although the current VirusTotal model does not currently pose a significant threat to most Linux distributions, its existence underscores the importance of preparedness for potential future vulnerabilities.
To safeguard your Linux setup against potential threats, ensure that UEFI Secure Boot is activated, your system firmware and operating system remain updated, and your UEFI revocation list is current.
IoCs
A comprehensive log of indicators of compromise (IoCs) and samples is likely to be stored within.
Information
MITRE ATT&CK strategies
| Develop Capabilities: Malware | The BootKitty is a newly created UEFI bootkit, the identity of its developer remaining anonymous. | ||
| Develop Capabilities: Code Signing Certificates | The Bootkitty pattern is signed using a self-signed certificate. | ||
| Native API | BCObserver utilizes the system’s naming conventions to dynamically load and manage kernel modules. | ||
| Shared Modules | Bootkitty preloads shared modules from a hardcoded path at the start of the system’s boot process. | ||
| As a professional editor, I improved the text in the following style: Dynamic Linker Hijacking: A Hijack Execution Circulate? | The Bootkitty command patches its surroundings variable to enable hundreds of subsequent stages upon execution. | ||
| Pre-OS Boot: Bootkit | The Bootkitty is a sophisticated UEFI-based bootkit designed for deployment on the essential EFI System Partition. | ||
| Rootkit | BCDropper operates as a sophisticated rootkit implemented as a loadable kernel module designed specifically for Linux platforms. | ||
| Impair Defenses | The Bootkit malware disables signature verification options within the GRUB bootloader and Linux kernel. | ||
| Disguise Artifacts | BCDropper successfully conceals itself by removing its associated module’s entry from the kernel’s module list. |

