On October 28thIn January 2024, the Dutch Nationwide Police Force, in collaboration with the FBI, Eurojust, and multiple law enforcement agencies, conducted a major operation targeting the notorious RedLine Stealer malware-as-a-service (MaaS), along with its clone, META Stealer. The global operation, dubbed , culminated in the shutdown of three Dutch-based servers, the confiscation of two domains, the arrest of two suspects in Belgium, and the public release of charges against a key player in the United States.
In April 2023, cybersecurity firm ESET collaborated with law enforcement to disrupt the RedLine malware operation by taking down several GitHub repositories that served as command and control centers for the malicious actors’ management panel. Around that time, prior to our investigation, we had collaborated with colleagues at to document and reverse-engineer previously unknown backend components within the malware ecosystem. While these modules do not seamlessly integrate with malware, they effectively handle authentication and provide performance enhancements for the management panel.
As RedLine has been taken offline, we are releasing our 2023 findings publicly, along with newer insights gleaned from supply code and samples provided to us by the Dutch National Police.
Despite the takedown, RedLine’s pre-existing capabilities allowed it to maintain limited functionality, enabling existing panels to access and process data, albeit with restricted capacity to generate new samples or reestablish connections upon logging out. Additionally, older versions of the malware that have already been cracked could still function effectively. Because of these factors, our description of the RedLine operation implies whether it is a continuous endeavour.
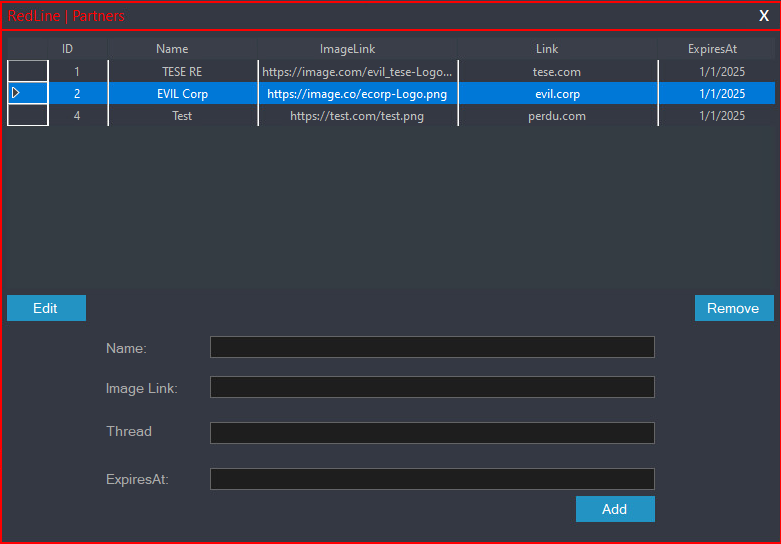
- In February 2023, ESET researchers, in conjunction with law enforcement agencies, gathered and analyzed a collection of malicious modules instrumental in operating the command infrastructure powering RedLine Stealer.
- By scrutinizing these previously unexamined modules, we gained valuable insights into the inner mechanics of this malicious-for-hire organization.
- Over 1,000 unique IP addresses have been identified as hosting RedLine management panels, demonstrating our ability to detect and track malicious activity.
- We examined the 2023 editions of RedLine Stealer in depth and found they leveraged Windows Communication Foundation (WCF) for intercomponent communication, whereas its 2024 counterpart employs a RESTful Application Programming Interface (API).
- Our analysis of the provided source code and backend examples suggests a common origin for both Redline Stealer and META Stealer, with evidence pointing to a single creator.
RedLine Stealer, a notorious info-stealing malware, was initially discovered in 2020 by cybersecurity researchers. Instead of relying on centralized operation, RedLine functions on a MaaS (Managed Application Services) model, whereby individuals can procure a turnkey infostealer solution from various online forums and Telegram channels. Shoppers, referred to as associates, can go for a month-to-month subscription, or a lifetime license; in trade for his or her cash, they get a management panel that generates malware samples and acts as a C&C server for them. The generated samples can collect a substantial amount of data, including native cryptocurrency wallets, cookies, stored credentials, and stored banking information from browsers, as well as saved data from Steam, Discord, Telegram, and various desktop VPN applications.
By leveraging a pre-established resolution, it simplifies the process for team members to integrate RedLine Stealer into more extensive marketing initiatives. Notable instances have seen ChatGPT emulate human-like personas in 2023, while others have leveraged its capabilities to develop online gaming hacks during the initial six months of 2024.
Because of its Mobility-as-a-Service (MaaS) model, every comprehensive scenario in RedLine will incorporate multiple distinct components and layers of community infrastructure. To avoid any potential confusion, we will utilize these phrases consistently throughout the text:
- The RedLine Stealer Malware or Its Variants
- GUI-based Malware Management Panel for Effective Infostealing Campaign Handling.
- Authentication and Performance Modules for RedLine Panel.
- : The entire malware operation. This comprises the RedLine malware, the RedLine panel, and the RedLine backend modules.
- A machine hosting a RedLine backend instance.
- The entity was compromised by the malicious RedLine malware.
- The entity responsible for creating RedLine, offering licenses, and managing the associated technology infrastructure.
- Organisation that orchestrates sophisticated information theft operations via the RedLine platform on a specific occasion. While some users typically obtain a legitimate licence from the operator, others may also employ an unauthorised or “cracked” version of the panel to access its features.
Overview
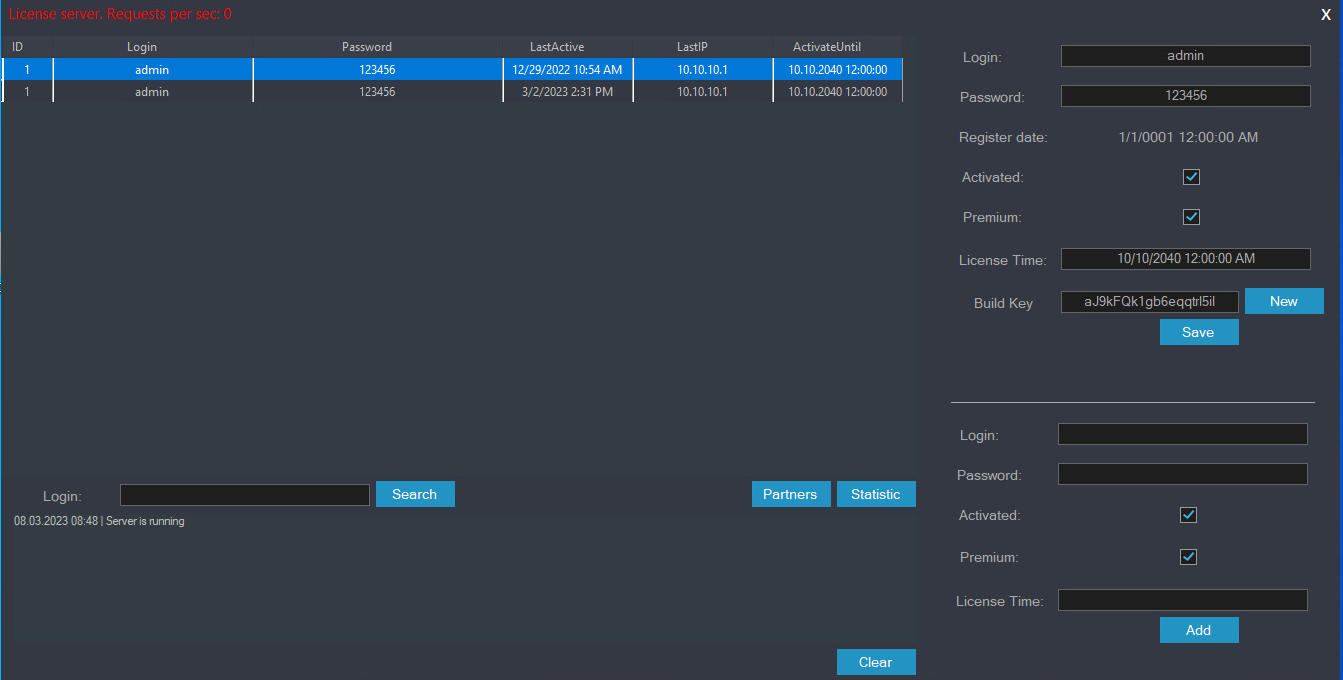
This blog post delves into the inner mechanics of RedLine’s backend servers, providing readers with a deeper comprehension of the company’s robust infrastructure and capabilities as a Managed Application Service (MaaS) provider. Additionally, we provide information about the RedLine panel. Determining 1: A Simplified Overview of RedLine’s Entire Operation?
Typically, samples of RedLine panels are compactly packaged and virtually replicated following the initial application of encryption. By leveraging our telemetry data, we were able to analyze exercise related to RedLine Stealer and its associated panel, which led us to uncover an earlier version of the RedLine panel that was merely obfuscated with encryption, significantly simplifying our investigation.
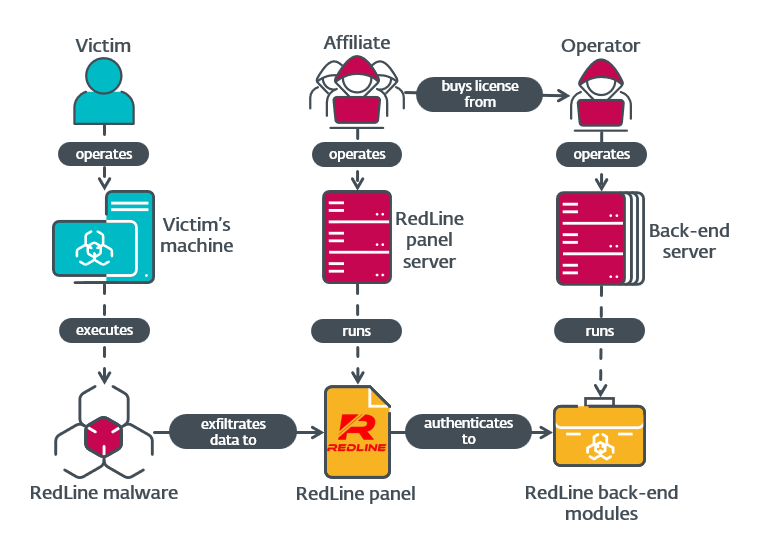
RedLine’s toolset
Developed entirely within a .NET ecosystem, all components of RedLine – encompassing both the malicious code itself and its supporting authentication infrastructure – are constructed using C#. We examined implementations that leveraged the Windows Communication Foundation (WCF) infrastructure for inter-communication purposes. This framework enables developers to define mappings, which are statements used to specify how objects and actions are translated between their representation within the code and external communication. Packages leveraging this framework should synchronize their understanding of these information structures through shared definitions. These shared fashions have proven invaluable in our deconvolution of obscure features.
The latest 2024 RedLine model leverages a RESTful API as a replacement for traditional WCF communication, seamlessly connecting with the backend infrastructure.
RedLine panel
Associates are encouraged to acquire this management panel for seamless interactions on various platforms, including boards and Telegram channels. Licenses are available for a monthly fee of US$150 per 30 days or a one-time payment of US$900 for a lifetime subscription. Associates receive compensation in exchange for access to a user-friendly graphical interface that enables them to manage their campaigns, featuring options to customize data collection parameters, generate malware samples, review and control gathered information, and integrate with a Telegram bot to disseminate stolen data.
By leveraging the 2023 iterations of our panel, which were thoroughly cloaked using a well-established .NET obfuscator and an enterprise-grade packer and virtualisation library, we gained valuable insights. Fortunately, RedLine’s utilisation of the Windows Communication Foundation (WCF) framework allowed the panel to seamlessly integrate with other components by sharing courses and interfaces across various elements. Through a meticulous examination of the shared components between the malware and unshielded backend elements, it was possible to gain valuable insights into the panel’s functionality despite the implemented security measures.
All 2023 RedLine panels bore certifications issued by Sectigo, later revoked following our exposé. The company, allegedly based in Armenia, lacks a web-based footprint, which is unusual for a self-proclaimed software development firm.
Authentication
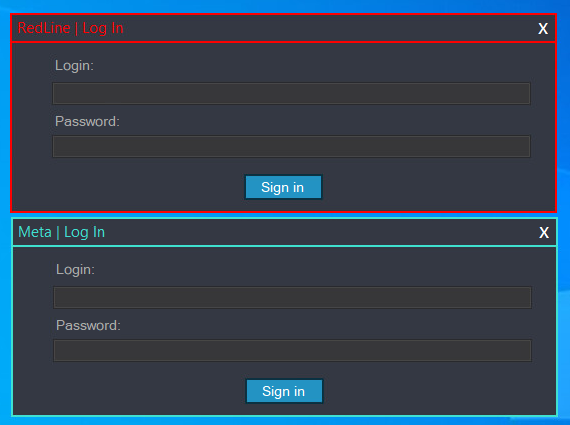
To utilize a RedLine panel effectively, associates must initially authenticate themselves. Determine 2 immediately reveals the login process.
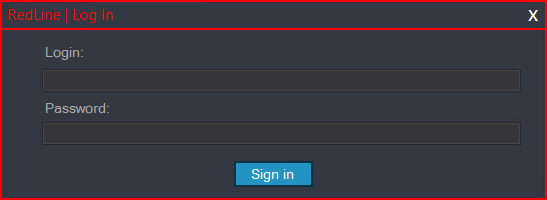
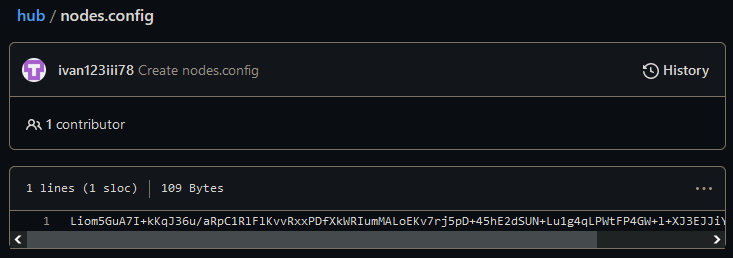
The RedLine panels examined utilize GitHub repositories, analogous to those depicted in Figure 3, as dead-drop resolvers for their authentication servers. While the configuration of the repository’s deal-with process is indeed hardcoded within the control panel, this setup does not remain consistent across all versions of the panel. Through collaborative efforts with GitHub, we successfully identified and eliminated numerous suspicious repositories, allowing us to temporarily suspend RedLine operations in April 2023. Despite the elimination having no impact on the malware’s core functionality, it forced the operators to disseminate fresh iterations of the malicious code. Following the disruption, they temporarily relocated dead-drop resolvers to new locations before opting for their own domain usage in May 2023, as outlined in our joint discussion with Flare on . In the latest RedLine panel iteration, threat actors abandoned traditional dead-drop resolvers in favor of a straightforward, hardcoded URL. Information regarding dead-drop resolvers might be found in that section.
We successfully established backend server components within a digital community, allowing us to create affiliate accounts and authenticate our personal presence without requiring a subscription purchase.
Upon login, the main display screen displays a plethora of advertisements, as depicted in Figure 4. While the exact type of ads presented by genuine authentication servers remains unknown to us, we managed to develop a few prototypes on our own backend server for testing purposes. The backend server does not host the exact photos currently featured in these advertisements, but rather stores their URLs instead.

The tab allows associates to dismiss incoming data by country, IP address, Build ID, or Hardware ID (a unique identifier calculated from a user’s machine location, username, and serial number), thereby facilitating targeted communication. Samples of RedLine Stealer malware include code that prevents execution if the target system’s locale matches any of the following countries: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, Uzbekistan, Ukraine, or Russia?
The tab, demonstrated in Determination 5, enables administrators to customize a Telegram bot for disseminating pilfered data to specific groups or channels. The affiliate must provide a valid API token to access the bot, following which they can selectively share entries based on criteria such as country, construct ID, operating system version, and domains stored in cookies or login data. The bot will be configured to share both total logs and specific information outlined in the designated area, as well as share statistics with designated recipients according to Determine 6.
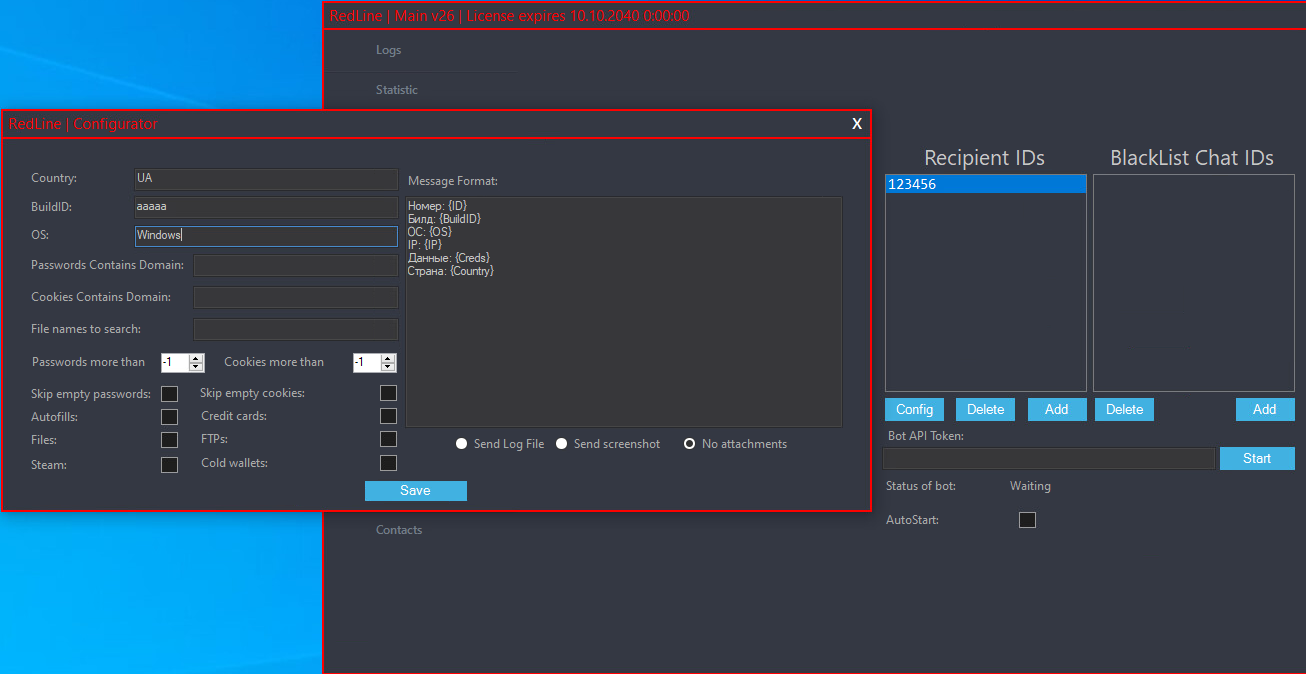
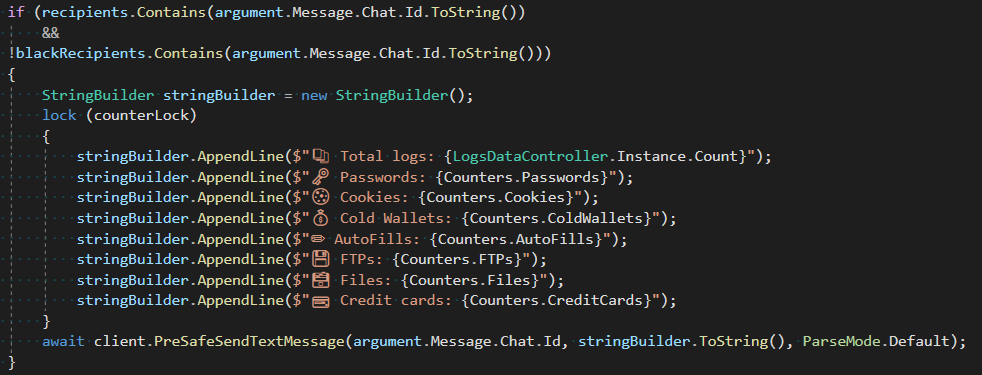
What drives individuals to create malware samples?
The Tab, as demonstrated in Determine 7, enables users to generate novel RedLine Stealer samples by providing a RedLine panel server address, a construct identifier, an error message to display, and a picture to serve as the icon for the created template. Two optional add-ons exist: an image that serves as the iconic representation of the RedLine software, impersonating its identity; and an error message designed to deceive users about the reason their expected utility failed to launch.
The Construct ID serves as a marketing campaign identifier, accompanying sample shipments along with pilfered information. While earlier versions of RedLine included a panel with an executable for creating regional builds, more recent iterations have shifted this responsibility to the backend server. With this modification, any compromised RedLine panel is significantly diminished in value as colleagues can no longer generate test samples using it. The concept of describing a course’s internal structure and components?
RedLine backend
The RedLine backend, which was assessed in 2023, comprises two distinct modules. The primary individual, responsible for managing affiliate and commercial information, plays a crucial role in the organization’s operations. This module eschews traditional databases, instead employing a novel approach to store data as serialized objects within distinct folders, each dedicated to a specific type of information. The second module, dubbed with the moniker, leverages its capabilities by seamlessly integrating with the server to optimize performance, thereby rendering the RedLine panel even more potent in its utilization.
We also uncovered a module dubbed, potentially serving as the progenitor of and. The later versions were reorganized as distinct modules, each focusing on individual or business data respectively.
In the revamped 2024 backend model, a solitary module has undergone significant transformations.
RedLine.Nodes.DbController
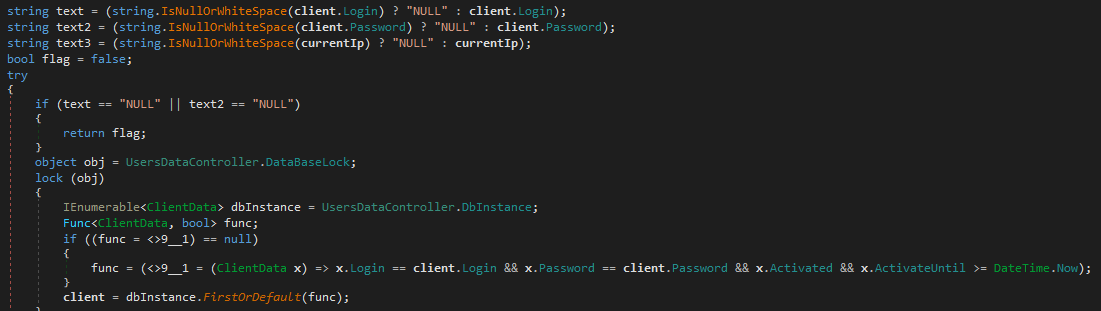
According to affiliate information, a specific category, as outlined in Desk 1, provides the necessary details.
| Distinctive numeric ID. | |
| Username. | |
| Password. | |
| Creation date of the affiliate account? | |
| Regardless of whether an affiliate has procured a licence. | |
| What is the timestamp for the affiliate’s conclusive exercise? | |
| The IP address from which the affiliate’s final exercise took place. To prevent unauthorized access, this feature is designed to block authentication attempts if the affiliate’s account shows activity from a different IP address within the last five minutes? To prevent account sharing. | |
| Expiry date of the affiliate’s licence. | |
| Unique identifier employed to track and distinguish samples generated by affiliates. |
While that is largely straightforward, there are some intriguing nuances, particularly regarding the handling of passwords and lifetime licenses.
The code utilised for authenticating associates, as illustrated in Determine 8, reveals that passwords are stored in plaintext. The provided password does not match the stored one, as no hashing process was applied during submission.
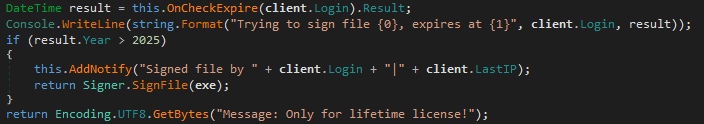
The Determine 9 tool enables users to represent a lifetime license, valued at $900, by simply setting the expiration date to any point in time after December 31st, 2025. This license is also referred to as a Professional Licence in other parts of the code.
RedLine.Nodes.LoadBalancer
As determined by Determine 10, the module listens on port 11. The screenshot further discloses the handlers explicitly defined within the WCF contract. The handlers associated with affiliate and commercial information, specifically those for payment gateway, order processing, and promotional content, delegate requests to their respective handlers within the system. The handler is utilized by the Redline panel to test whether or not its C&C server is reachable from the outside. All remaining handlers pertain to generating malware sample creations.
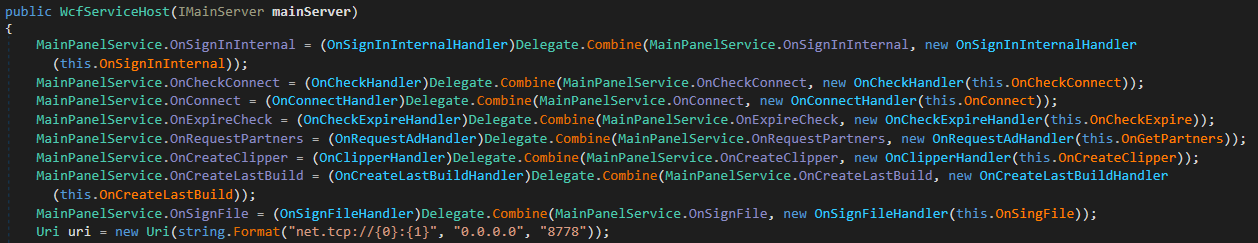
Pattern creation in Redline backend
Since its inception in 2020, RedLine Stealer has undergone significant modifications, transitioning from WCF framework to a REST API for seamless communication with the community. As previously established in Figure 11, the revised headings for these rewritten versions appear to be.
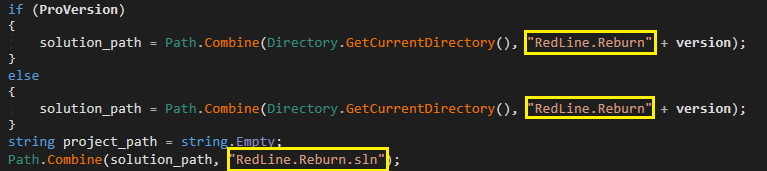
To generate samples of the RedLine Stealer malware, the author relied on the methodology outlined in Chapter 10, employing a tailored approach defined by the custom class. Upon receipt of a request, the plaintext password associated with the affiliate’s account is recorded in the system logs. This apparent flouting of established safety protocols betrays a cavalier attitude towards cautionary measures.
If within the request no port is specified for the C&C server, the builder defaults to port . The code in Determine 12 derives a token by combining the marketing campaign’s unique Construct ID with the affiliate account’s corresponding Construct Key. This correspondence aligns with the value attributed to the header used in communication between samples and panels. The header appears to serve as a mechanism for the panel to exclude connections originating from samples that are not associated with the current account.
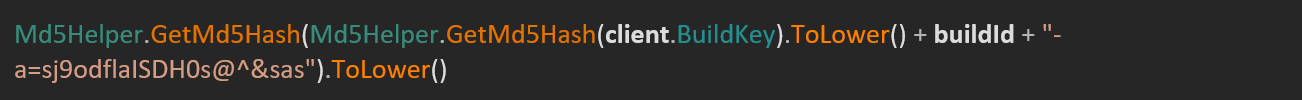
The methodology leverages a neighbourhood-based C# approach to generate samples. Several pieces of supply data are cached in memory before being written back to disk with updated values. Although initial attempts to acquire the venture’s details were unsuccessful, the combination of decompiled output and RedLine Stealer pattern provided sufficient insight to reveal that the revised values are:
- C&C deal with (encrypted),
- Construct ID (encrypted),
- pretend error message (encrypted),
- decryption key,
- Should flags be used to dictate whether to swiftly dispatch pilfered data as individual components or make a sudden departure?
- authentication token, and
- meeting title.
As soon as these values are modified, Visual Studio is launched to build the project.
The affiliate’s chosen option for licensing is matched with the lifetime license; consequently, the resulting compiled executable is encrypted using a widely available . Within the 2024 model, all customers are now subject to obfuscation, which is achieved seamlessly through a novel approach.
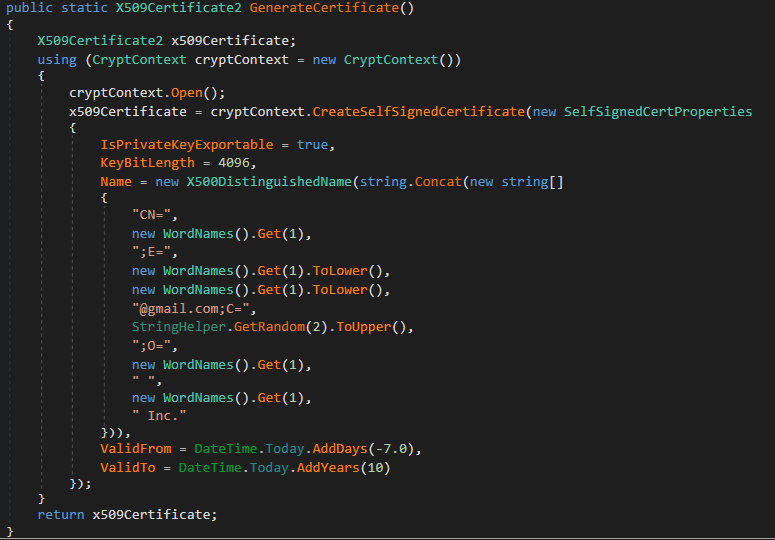
A self-signed certificate is generated using the code from Determine 13, which serves as a signature for the executable. The fields of its distinguished identity (DNI) are replete with seemingly arbitrary lexical entries from a dictionary. Certificates generated in this manner employ a predefined password and boast a validity period spanning seven days prior to the technology’s inception to a maximum of 10 years post-launch.
The module further provided a robust handler.
The malicious code, as its name implies, was designed to facilitate clipboard hijacking attacks. In this particular instance, it was leveraged to intercept and manipulate cryptocurrency transactions, substituting the intended recipient’s wallet address with that of an attacker-controlled wallet. The performance enhancement has been successfully integrated into the latest iterations of the Redline backend, rendering the previous variation obsolete.
Intriguingly, the class harboured dormant code capable of crafting a malware signature from a minimalistic executable shell. This leftover from our previous strategy for generating variations of RedLine Stealer remains unaddressed. The latest iteration of the Redline backend no longer includes the relevant code.
One additional handler, named, allows associates with lifetime licenses to transmit arbitrary information via certificates stored on the backend server. Although we’ve yet to obtain these certificates, it’s plausible they may be identical to those utilized in signaling RedLine panels, given their association with various RedLine Stealer and other malware samples. One additional potential contender is the certificates with a thumbprint, issued to individuals. The following stolen certificates have been exploited to signify numerous RedLine Stealer specimens and various malicious activities. It has already been revoked.
RedLine.MainServer
This module integrates the key functionalities of its predecessors with a Graphical User Interface (GUI), empowering administrators to efficiently manage affiliate accounts and commercial data. Despite the enhanced capabilities, several components suggest that this model may be an antecedent of and , rather than a successor:
- Samples are compiled using an outdated version of the .NET Framework (4.6.2 instead of 4.8).
- The meeting’s copyright year is 2020, instead of 2021?
- Samples do not always include performance data for advertisements.
- The primary WCF service’s contract does not encompass the current handler located within the same class. This handler is used by all of the latest RedLine panels that have been analyzed to date.
The RedLine backend’s GUI administration panel was subsequently segmented into a distinct module, aptly titled.
The examination of the GUI model provided a profound insight into the management of RedLine’s administrative processes. As outlined in Section 14, the tool provides a means to generate and modify affiliate account details. The fields correspond precisely to the class definition outlined earlier.
A specific type of advertisement, as described in Section 15, is designed to manage advertisements similarly.
The original Determine 16’s basic dashboard provides the user with a summary of licensing revenue figures.
Nodes.Api
A comprehensive evaluation of samples provided by the Dutch law enforcement reveals that the latest RedLine iterations have merged the capabilities of the and modules into a novel entity, aptly designated as Nodes.Api. This backend module, packaged as a DLL, leverages the ASP.NET framework’s robust `System.Web.Http` class to provide a RESTful API that seamlessly integrates with the associated panels. As revealed in Determination 17, the module processes requests routed to both RedLine and META servers, thereby confirming that the two info-stealers are operated by the same entity.
The table summarises the endpoints identified through the REST API alongside their equivalent WCF handlers from previous iterations.
| N/A | In most likelihood, a process was employed to verify network connections. This simply calculates the value. | |
| Handles logins from the panel. | ||
| Retrieves the advertisements to be displayed within the panel. | ||
| The rise of the Stealer malware: A catastrophic cyber event. | ||
| Verifies the external reachability of a deal with and port by pinging them. | ||
| N/A | Renders updated affiliate data to ensure seamless integration with relevant platforms. The transaction is conclusively finalized when the request originates from a local network connection. | |
| N/A | The affiliate management system creates a brand-new affiliate account, assigning a unique username and password for seamless access. | |
| N/A | Renews the license term for a designated affiliate, thereby prolonging its period of operation. | |
| N/A | Retrieves a file from its storage location on the disk. The password-protected digital archive contains the latest version of the panel design. |
Unlike past iterations of our 2023 backend analysis, lifetime licenses do not appear to be embedded within the new module’s code. As such licenses continued to be offered, we conclude that they could have been simply managed by expiring them at an earlier or later date. Code signing performance-related issues have been entirely resolved.
Samples created by the module are obfuscated, using a hardcoded path to determine whether they are current. This correspondence aligns with its predetermined setup pathway.
Options that were current in older versions behave largely unchanged from their earlier iterations. Despite this, a handful of captivating features have been incorporated.
Affiliate administration
Three key touchpoints for processing affiliate data come to light. While intended for sole use by the operator, these measures are addressed in two distinct manners elsewhere. The endpoint triggers a server refresh of person data from disk storage. The Determine 18 module outlines the algorithm used to update entries each time a new one is added or an existing one is altered. The operation is severely restricted when requests originate from a loopback address, effectively preventing Panel customers from accessing this feature.
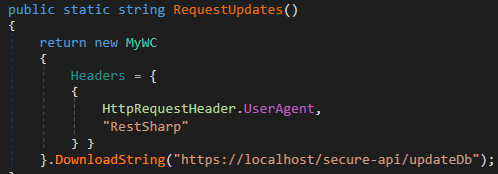
The two end points, and, utilize a unique approach to prevent unauthorised access. As revealed in Determine 19, these callbacks will only be triggered if the incoming request contains a custom HTTP header with a predefined, seemingly arbitrary value.
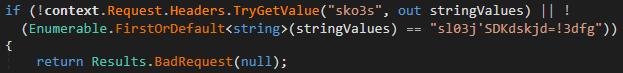
Backups
The enhanced functionality includes the capability to backup affiliate data, a feature previously absent from earlier versions of the code. The information is stored sequentially on disk and backed up as a ZIP file containing the data in a single package. The archived data is subsequently transmitted via Telegram, utilizing a fixed Chat ID specified in Determination 20.
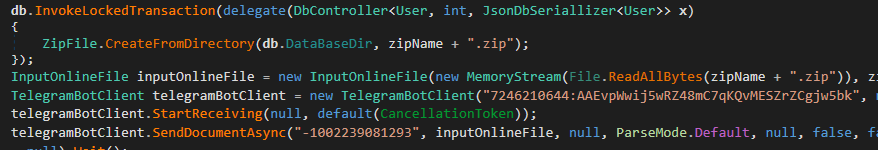
Hyperlinks with META Stealer
META Stealer is a counterintuitive malware that diverges from typical information-stealing tactics, simultaneously targeted alongside the infamous RedLine Stealer. The MetaStealer malware was initially spotted on cybercriminal forums in March 2022. The writer claimed to have employed identical code to RedLine Stealer, guaranteeing equivalent performance and functionality. Although Meta Stealer has not undergone a thorough investigation comparable to that of RedLine Stealer, our research confirms the initial claims regarding its capabilities. Based on the source code, the two info-stealers appear to have been crafted by the same individual. While some code exhibits deviations, much of it shares similarities, differing primarily in string case modifications achieved through dot notation. As evident from Determine 21, the inactive code in RedLine remains active in its corresponding META counterpart.
As previously discussed, another key indicator that RedLine and META share the same operators can be found within the code that manages requests sent to both RedLine and META servers, as illustrated in Figure 17.
Two additional samples were found bearing METAs, certified and used to verify the authenticity of corresponding RedLine panel samples. The panel employed the same dead-drop resolution methods, replicating the exact use of AES and RSA encryption keys in a separate GitHub repository, thereby maintaining consistency across implementations. Despite what Determine 22 shows, the comparison between META’s and RedLine’s panel choices reveals only subtle aesthetic differences.
A cleverly designed anti-debugging mechanism employs a combination of DNGuard and BoxedApp to safeguard its interface from analysis. Despite this, attempts to execute META’s authentication process failed when tested against our instance of the RedLine backend from 2023, suggesting that the process has likely undergone modifications since then.
Community infrastructure
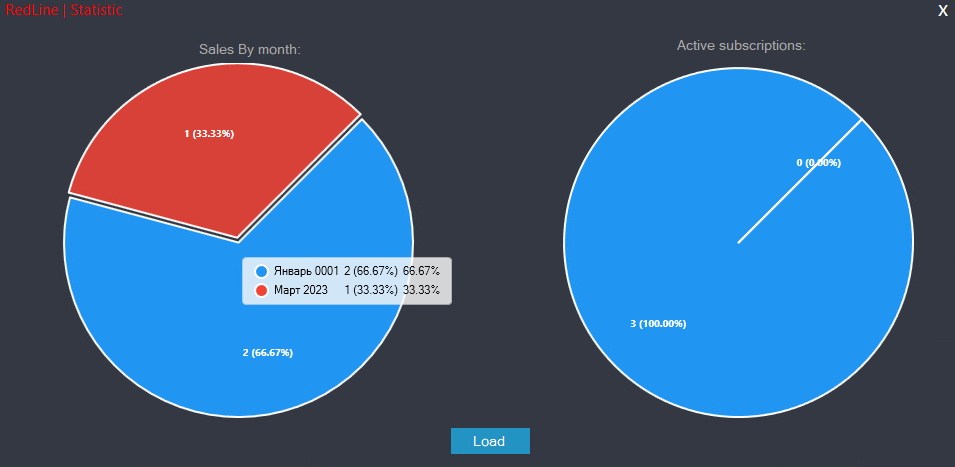
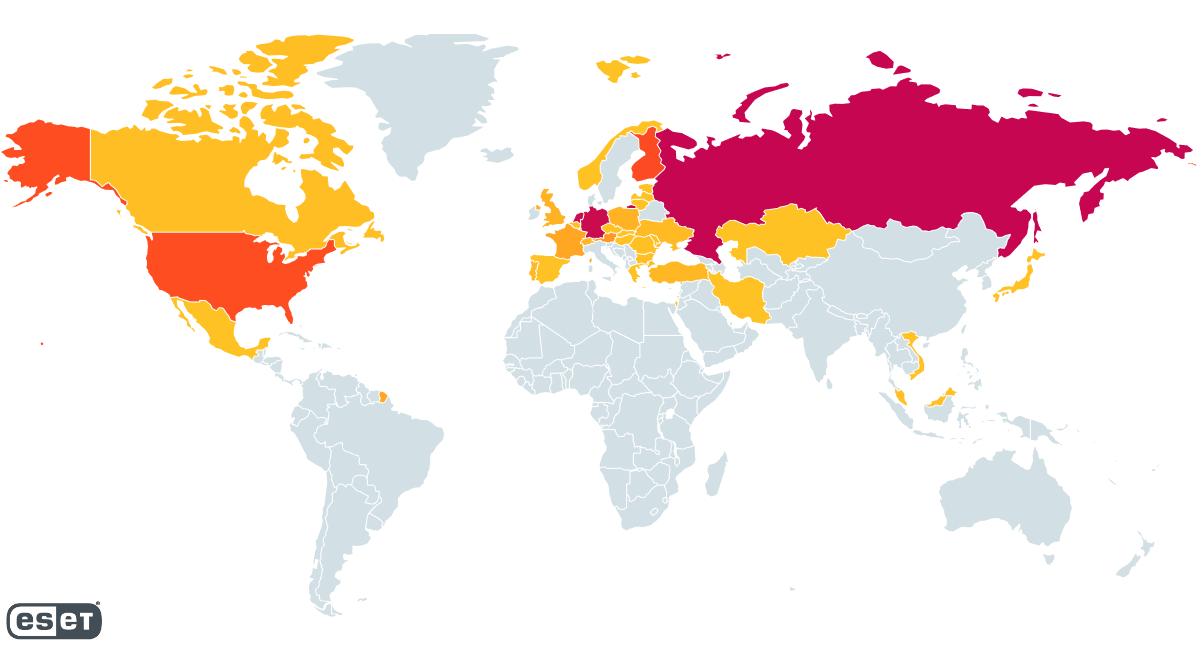
By analyzing samples of RedLine malware that we identified between November 30th, 2022 and March 23rdBy early 2023, our analysis revealed that more than 1,000 unique IP addresses were utilized to host RedLine panels. The findings of Determine 23 are presented in a manner that illustrates the spatial dispersion of the hosted panels. Russia, Germany, and the Netherlands collectively account for approximately 20% of the total, while Finland and the USA each represent around 10%. Although based solely on sample data focused on prospective targets, this information still provides a generally accurate representation of the malware’s overall distribution.
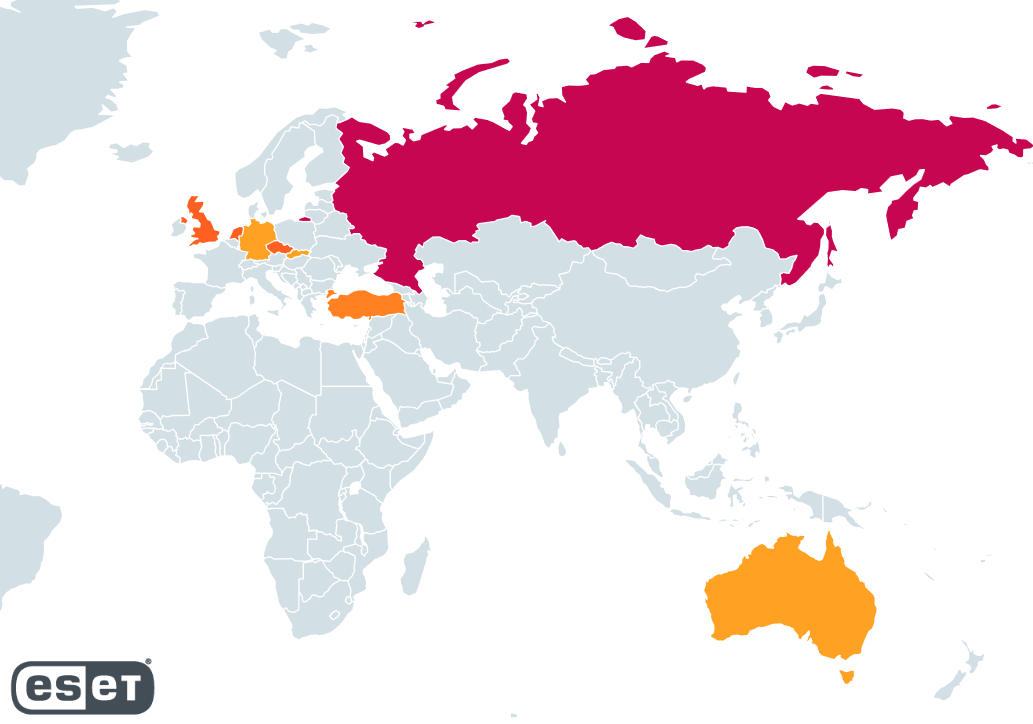
We successfully identified and configured multiple distinct backend servers. It’s possible that residual data remains within the dead-drop resolvers that we were unable to decipher. As depicted in Figure 24, a significant proportion of servers are situated in Russia, comprising approximately one-third of the total. Meanwhile, the United Kingdom, the Netherlands, and the Czech Republic each account for roughly 15% of the identified servers.
Lifeless-drop resolvers
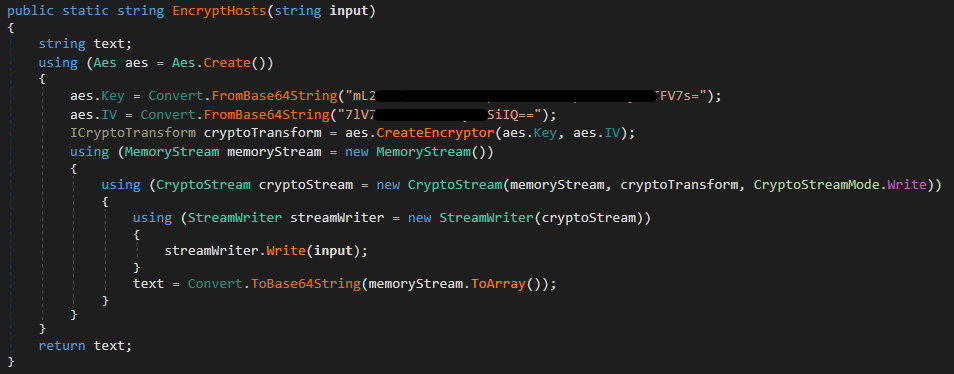
The 2023 iterations of the RedLine panel leveraged GitHub repositories as secure dead-drop resolvers for its authentication servers, bolstering overall system integrity and security. The repositories housed files containing encrypted records of server IP addresses. The file was encrypted using a custom-built module simply referred to as “.”. In one specific instance of this module, documented in Determine 25, encryption was performed using AES-CBC with a hardcoded key and initialization vector (IV), and stored in a file designated by the extension.
OLDER variations, utilising RSA encryption until mid-2024, employed RSA as an alternative (refer to Figure 26); the output was written to a file denoted by . The bottom line is to learn from files rather than being hard-coded within an executable. Notwithstanding, the RSA encryption category can be instantiated within the module using hardcoded default values for both private and public keys. Verify connectivity by re-communicating with backend servers through established nodes.
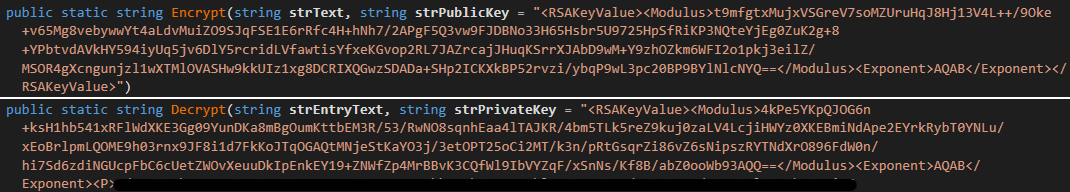
Multiple GitHub repositories have been found to contain at least one encrypted file. With the demonstrated keys, we were able to extract an RSA private key from the panel’s pattern. By acquiring lists of authentication servers, we were able to share them with law enforcement agencies.
Conclusion
Prior to Operation Magnus, RedLine emerged as one of the most prevalent forms of infostealer malware, boasting a massive network of affiliates utilizing its command center. Despite this, evidence suggests that the sophisticated malware operation is controlled by a small group of individuals, some of whom have already been identified and taken into account by law enforcement agencies.
The META Stealer, a malicious actor’s latest creation, emerged on the threat landscape in 2022, posing as a clone of RedLine Stealer and likely developed by the same nefarious actors responsible for the original malware. The lack of clear succession to RedLine is evident, as household growth persists in tandem. The malware, a notorious strain of code, was simultaneously dismantled from servers alongside its infamous counterpart, RedLine Stealer.
Our comprehensive examination of the underpinning elements of RedLine – including its management panel and backend infrastructure – aims to provide a more comprehensive comprehension of this risk.
IoCs
A comprehensive log of indicators of compromise (IoCs) and samples may exist within a .
Information
| N/A | RedLine backend single-file utility. | ||
| N/A | RedLine Backend Person and Commercial Administration Module (2024 Model)? | ||
| N/A | RedLine backend foremost module. | ||
| MSIL/Spy.RedLine.O | META stealer panel (2024 model). | ||
| MSIL/Spy.RedLine.H | RedLine stealer panel (2024 model). | ||
| MSIL/Spy.RedLine.O | RedLine stealer panel (2024 model). | ||
| N/A | RedLine backend licensing server GUI. | ||
| N/A | Instrument to encrypt the record of C&C servers. | ||
| N/A | RedLine backend server module. | ||
| MSIL/Spy.RedLine.Okay | WCF (Windows Communication Foundation) frameworks are designed to simplify the process of building service-oriented applications. They provide a set of APIs for creating web services, as well as tools for debugging and testing these services. The key components of WCF include endpoints, contracts, and bindings. Endpoints represent the communication interface that clients use to access the service. Contracts define the operations that can be performed by the service, including input parameters and return types. Bindings specify how data is serialized and transmitted over the network. For instance, consider a simple web service that provides weather forecasts for different cities. The endpoint would likely include methods such as GetForecast() which takes city name as an input parameter and returns current forecast details. | ||
| Win32/GenCBL.ATC | RedLine panel (v22.4). | ||
| MSIL/Spy.RedLine.H | RedLine panel (non-virtualized). | ||
| MSIL/Spy.RedLine.J | RedLine fashions and contracts definitions. | ||
| MSIL/Spy.RedLine.H | META Stealer Panel. | ||
| N/A | Redline’s backend server personnel and commercial administration modules? | ||
| MSIL/Spy.RedLine.H | RedLine panel (v26). | ||
| MSIL/Spy.RedLine.H | RedLine Panel (leaked cracked model). |
Community
Notice that the domains within the desk, underserved by law enforcement, have been seized by legislation authorities. The opposite panel and server addresses collected were regularly shared with law enforcement agencies to facilitate their efforts and are no longer active.
| N/A | N/A | 2024-06-02 | META backend REST server. | |
| N/A | N/A | 2024-08-03 | RedLine backend REST server. |
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Purchase Infrastructure: Digital Personal Server | Situations where the RedLine data finally comes to a close are stored on leased digital private servers. | ||
| Purchase Infrastructure: Server | The situations of RedLine’s data archives are housed on custom-built servers, designed specifically for RedLine’s needs and optimized for efficient storage and retrieval. | ||
| Purchase Infrastructure: Internet Providers | The operators at RedLine have established multiple GitHub accounts and repositories. | ||
| Develop Capabilities: Malware | The operators of RedLine have created their proprietary malware infrastructures, comprising custom-built command centers, control panels, and server architectures. | ||
| Develop Capabilities: Code Signing Certificates | The Red Line again finishes generating self-signed certificates robotically when creating samples? | ||
| Receive Capabilities: Code Signing Certificates | RedLine panels are certified with authentic certificates issued to authorized professionals. | ||
| Stage Capabilities: Add Malware | Again, confidential elements of RedLine are securely transferred to designated, restricted-access servers. | ||
| Debugger Evasion | If the RedLine panel robotically detects a debugger or evaluation instrument, it promptly self-terminates. | ||
| What is Obfuscated Information or Info? | The RedLine panel samples are packaged using DNGuard and BoxedApp technology. | ||
| Information Encoding: Commonplace Encoding | RedLine leverages heavy-duty base64 encoding to fuel robust communication within its community ecosystem. The WCF framework’s standard binary encoder is utilized in community communication. | ||
| Encrypted Channel: Symmetric Cryptography | All communications between the panel and back-end server are securely encrypted using AES technology. In certain situations, the content of a dead-drop resolver is encrypted using AES-CBC encryption. | ||
| Encrypted Channel: Uneven Cryptography | RSA encryption is used to secure communications between the panel and the back-end server. When certain situations arise, dead-drop resolver contents are sometimes encrypted using RSA encryption methods. | ||
| Software Layer Protocol: Internet Protocols | Community communication in the present day takes place via a robust REST API, securely transmitted over HTTPS connections. | ||
| Non-Software Layer Protocol | Community communication is successfully facilitated through the Windows Communication Foundation (WCF) framework over Transmission Control Protocol (TCP). | ||
| Internet Service: Lifeless Drop Resolver | The RedLine panel leverages GitHub repositories as dead-drop resolvers to obtain the addresses of back-end servers. | ||
| Non-Commonplace Port | By default, the RedLine panel’s performance runs an HTTP server on a designated port. |

