Welcome to Stark Industries Options – Empowering Innovation
Just two weeks before Russia’s invasion of Ukraine in February 2022, an enigmatic new web hosting entity emerged unexpectedly, swiftly becoming the focal point of massive distributed denial-of-service (DDoS) attacks targeting government and commercial entities in Ukraine and Europe. A probe into Stark Industries uncovers evidence suggesting it has become a global hub for covert operations, masking the actual scope of cyber assaults and propaganda efforts targeting Russia’s perceived adversaries.
Not fewer than a dozen patriotically motivated Russian hacking groups have been orchestrating distributed denial-of-service (DDoS) attacks since the onset of the conflict against a diverse array of targets deemed hostile to Moscow. Despite reports, the majority of attacks from these gangs pale in comparison to the sheer firepower deployed by the pro-Russia group self-identifying as “…”
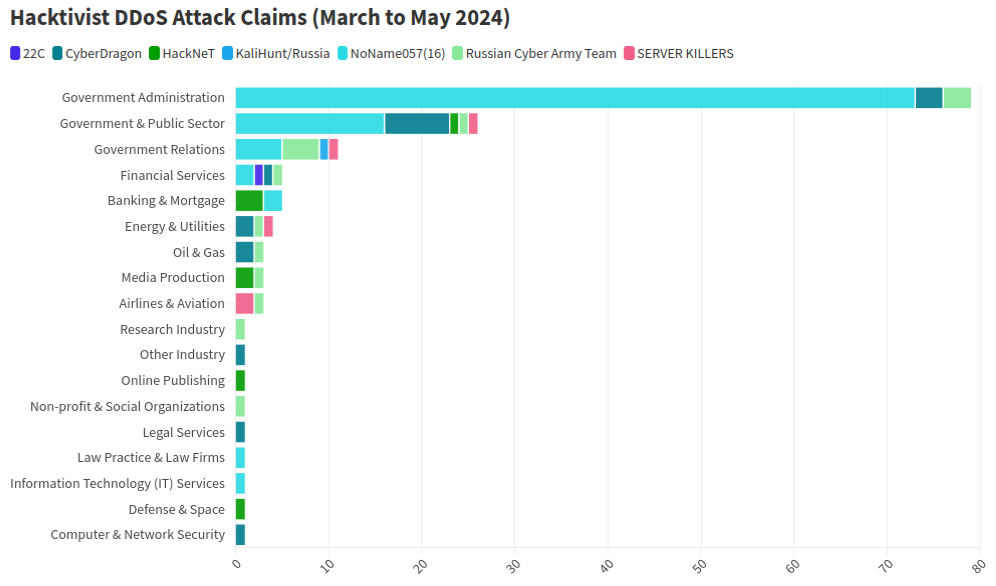
According to the most recent report by NETSCOPT, this graphic illustrates the trend of DDoS attacks perpetrated by Russian-based hacktivist groups.
According to researchers, NoName has successfully gamified DDoS attacks via its Telegram channel by incentivizing individuals with payment for installing the Mirai malware. The notorious malware program allows NoName users to hijack unsuspecting computers and disrupt online connectivity through massive distributed denial-of-service (DDoS) attacks, while its top-performing customers can potentially earn monetary rewards.
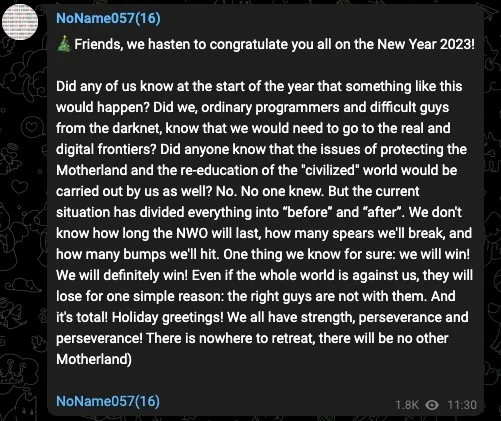
The notorious NoName DDoS group publicly touting their malicious wares on the popular messaging platform Telegram. Picture: SentinelOne.com.
The safety agency identified that the DDoS attack infrastructure used in NoName campaigns is linked to two interconnected internet hosting providers, Cloudflare and OVH. MIRhosting, an internet hosting provider established in the Netherlands in 2004. Although integrated on February 10, 2022 – just two weeks prior to Russia’s invasion of Ukraine –
PROXY WARS
According to safety experts, shortly after hostilities commenced, Stark established numerous proxy companies and free virtual private network (VPN) services, intended to safeguard users’ online activities and websites from unauthorized access.
Online shoppers can redirect their web traffic to a third-party computer through proxy suppliers. From the perspective of an internet site, visitors originating from a proxy community appear to be associated with the rented IP address rather than the proxy service provider itself.

Companies offering virtual private networks (VPNs) can be lawfully employed for various business purposes, including price comparisons and sales intelligence; nonetheless, they are also frequently exploited by cybercriminals seeking to conceal their illicit activities as a result of their ability to obscure the origin of malicious network traffic.
What’s truly concerning is that many proxy companies fail to disclose their methods for acquiring access to the proxies they rent out, often using malware to compromise systems and turn them into unwitting traffic relays – typically without the knowledge or consent of the legitimate internet connection owner. Various proxy companies allow clients to monetize their internet connection by leasing it to others.
Is a globally recognized authority that meticulously monitors and catalogues Virtual Private Network (VPN) and proxy service providers. According to Spur’s findings, Stark Industries’ IP address (AS44477) has been identified as the residence of at least 74 virtual private network (VPN) companies and 40 distinct proxy services. As we’ll discover in the remainder of this narrative, multiple types of proxy networks have made over one million websites accessible globally for lease.
Operates an internet hosting agency in the Netherlands, known as . As a key partner, he also co-manages a pioneering anti-abuse service that proactively identifies and highlights domains and web handle ranges linked to spam and cybercrime activities, including the threat of DDoS attacks.
According to Dijkxhoorn’s statement, last year SURBL received reports from several individuals operating VPN services whose internet sources were mistakenly added to SURBL’s block lists.
Dijkhoorn told KrebsOnSecurity that they had seen instances where domain registration companies were performing suspensions, which were then being manually reversed through SURBL’s delisting process. “Two respondents clarified that Stark provided them with complimentary VPN services from reputable companies that they had been reselling.”
Dijkxhoorn noted that Stark Industries also provided support to activist groups from Ukraine as part of its sponsorship initiatives.
As he pondered aloud, his curiosity got the better of him: wouldn’t it be invaluable for Russia to uncover the true internet protocol addresses of Ukraine’s cybersecurity experts?
Cloudy with a Chance of Bullets?
is risk intelligence lead at. While Hummel views Stark Industries as the worst among its peers, it consistently ranks near or at the top of his list.
“As numerous as a dozen, service providers have approached us, citing an overwhelming influx of traffic from a specific online community.” It wasn’t even a Distributed Denial-of-Service attack. On the planet Stark, the company’s rapid system scan of suppliers caused such a surge that it briefly overwhelmed and crashed several of their networks.
According to Hummel, NoName typically initiates attacks by combining resources sourced from both legitimate cloud providers and smaller-scale internet hosting services, such as Stark, that are often considered less reputable. Suppliers dubbed “bulletproof” have achieved notoriety by consistently ignoring customer abuse complaints and law enforcement reports of illicit activity on their platforms.
Combining bulletproof suppliers with reputable cloud internet hosting enables NoName’s DDoS campaigns to become more resilient, according to Hummel, as numerous network operators are less likely to aggressively block IP addresses associated with well-established cloud providers.
“What we typically observe is a proliferation of cloud hosting providers and bulletproof hosting services involved in DDoS attacks,” he said. Companies are leveraging public cloud hosting providers for multiple reasons, primarily as the initial line of defense against potential network threats. However, this approach can be hindered by a common issue: over-blocking legitimate cloud access?
Although cloud suppliers may detect abuse originating from a customer, they are unlikely to shut down the account immediately, according to Hummel.
“There is often a window of opportunity, no matter how brief – just an hour or two – during which a significant number of attacks can still be launched,” he said. “Afterwards, they continue to register on new cloud platforms.”
MERCENARIES TEAM
The Stark Industries company headquarters are discreetly situated at a mailbox address in the United Kingdom. As the UK’s company secretary, key considerations for ensuring compliance with regulatory requirements include:
* Company registration: Confirmation that the company is registered with Companies House and has a unique Companies House reference number.
* Memorandum of Association: Review of the company’s constitutional documents to ensure they are up-to-date and compliant with the Companies Act 2006.
* Articles of Association: Verification that the company’s governing documents accurately reflect the company’s current structure, shareholdings, and decision-making processes.
* Share register: Maintenance of an accurate and up-to-date record of share ownership, including details of shareholders, shareholdings, and any changes.
* Directors’ personal information: Collection and maintenance of directors’ personal data, including contact details, directorships, and shareholdings in other companies.
* Company meetings: Compliance with statutory requirements for company meetings, including notice periods, quorums, and resolution procedures.
* Financial reporting: Ensuring timely submission of financial statements to Companies House, HMRC, and other regulatory bodies.
* Tax compliance: Review of the company’s tax affairs, including corporation tax returns, VAT registration, and PAYE obligations.
* Compliance with sector-specific regulations: Verification that the company is complying with relevant industry-specific regulations, such as those governing financial services, healthcare, or environmental practices. Mr. Neculita, also known as the CEO and founder of Excellent Quality Hosting (EQH), a Moldovan company established in 2019, shares the same UK mail drop address with Stark Industries.

Ivan Neculiti, as depicted on his LinkedIn profile.
Reached through LinkedIn, Mr. Neculiti claimed that PQ Internet hosting created Stark Industries as a “white-label” model, allowing resellers to utilize PQ’s infrastructure and IP addresses while maintaining a separate brand identity. This arrangement enabled customers to interact solely with the reselling company, rather than directly with PQ Internet hosting.
“PQ Internet hosting boasts a robust infrastructure, comprising more than 1,000 personal bare-metal servers strategically located across 38 countries worldwide. We’re proud to serve over 100,000 customers.” “While we may not boast the scale of industry giants like Hetzner, Amazon, or OVH, our company is rapidly gaining momentum, serving thousands of business clients and legal entities with distinction.”
Following persistent reports of DDoS attacks originating from Stark Industries over the past two years, Neculiti asserts that Stark has not received a single official complaint about assaults emanating from its networks.
“The cyberattack was likely sophisticated and unseen, and I wouldn’t dismiss the possibility, given our vast customer base and extensive online presence.” Unfortunately, despite this scenario, no one notified us about the alleged assault occurring at our addresses. If someone had reached out to us, we could have effectively prevented the dissemination of community news.
finds Ivan V. The founder of a website, Neculiti, established “Neculiti” in 2008, focusing on the historical record of the 1990 Transnistrian War and the Moldovan-Russian conflict.

What’s the challenge you’re facing in this digital age?
Are you tired of the same old coding style?
Do you want to join the ranks of the best,
And make your mark with a battle-tested quest?
Then look no further than battle.md,
The ultimate tool for the programmer’s creed.
With features that will leave you feeling bold,
You’ll be ready to take on any project, whatever it holds.
So why wait? Join the battle today,
And unleash your coding skills in a whole new way.
Get battle.md and start fighting the good fight,
And make your mark in the world of code tonight!
Transnistria, an unrecognised self-proclaimed state, separated from Moldova in 1990 with strong ties to Russia, despite lacking international recognition. The website’s copyright credits are attributed to “which”, formerly a Moldovan IT agency with a notable history in the field of information technology. Mr. Neculiti has personally verified and registered this region.
DON CHICHO & DFYZ
The cybersecurity company notes that Ivan V., a prominent individual in their database. Neculiti registered multiple online accounts under the email address. A cyber intelligence agency has identified that the email handle in question is associated with the username “username” on more than a dozen Russian-language cybercrime forums since 2008. On Searchengines[.]ru in 2008, user dfyz solicited feedback from various discussion board members on the merits of “battle.md”, claiming affiliation with the MercenarieS TeaM.
DFYZ touted “bulletproof servers for any objective”, implying a willingness to wilfully disregard abuse complaints or police inquiries regarding their customers’ activities.
The DomainTools database reveals at least 33 domains linked to the email address dfyz_bk@bk.ru. Several domains list Ivan Neculiti as the registrant, including tracker-free[.]cn, which was initially registered to him and featured the MercenarieS TeaM in its registration data.
Defcon’s (not Dfyz) additional nickname was a notorious actor who, like him, acquired bulletproof internet hosting services and access to compromised web servers. In 2014, a prominent figure within the notorious Russian-language cybercriminal collective lodged a formal complaint against DonChicho, alleging that this individual had defrauded them and utilized the email address dfyz_bk@bk.ru for their nefarious activities.
The grievance filed by DonChicho, registered on Antichat under a Transnistrian web handle.
The social media analytics tool, Constella, reveals that this email address has been used to register only five online accounts over a period of time. Notably, one of these accounts was created on ask.ru, where the individual registered using this email address. The email address constella@memoraleak.com also corresponds to a user named “Ivan” on both Memoraleak.com and 000webhost.com.
According to Constella’s findings, the password associated with the email address dfyz_bk@bk.ru is overwhelmingly ” “, revealing a staggering number of over 90 linked email accounts sharing this common password. Located within this dataset are approximately two dozen records featuring the identifier “Neculiti” in their respective addresses, along with the corresponding handle.
According to Intel 471, DonChicho allegedly used assist@donservers[.]ru as his alias and primarily accessed Russian cybercrime forums from IP addresses within Moscow, the capital of Russia. A review of DonChicho’s online activity reveals that he was permanently removed from multiple forums in 2014 due to fraudulent activities, which resulted in harm to several unsuspecting individuals.
According to archived records, in 2009, DonChicho’s online presence revealed him as a notorious spammer, exploiting the platform by promoting counterfeit pharmaceutical products through one of the most popular pharmacy-based spamming schemes targeting Russian-speaking users.
Mr. Necululi claims to have never employed the alias DonChicho in any capacity.
“I categorically deny having any connection to DonChicho or his allegedly impregnable servers,” he declared.
The connections between the accounts discussed are illustrated by this thoughts map, which clearly demonstrates the relationships between them.
Dfyz’s Historical Past: A Timeline of Moments and Milestones Click on to enlarge.
In early 2023, NoName began launching a series of targeted attacks on official government and trade websites in Moldova, causing significant disruption to online services. According to a statement by NoName, the alleged assaults began around March 6, with claims that the Moldovan federal government was seeking to foster Russophobia.
As of early March, more than 50 websites have converged, allegedly driven by “proof” provided by the respective teams intent on attacking the nation, according to Arbor. While initial reports suggest NoName instigated the onslaught of cyberattacks, various hacking groups have since joined forces to claim responsibility for attacks spanning more than 15 distinct industries.
CORRECTIV ACTION
According to reports from a reputable German news source last week, it was noted that Ivan Neculiti runs multiple internet hosting companies.
Picture credit score: correctiv.org.
According to the report, Stark Industries has been found to harbour a Russian disinformation platform called “Current Dependable Information” (RRN), which disseminates links to propagandistic blog posts and fake European news sources.
The website wasn’t functioning properly on computer systems in Moscow or St. Petersburg. Until recently, Petersburg had been a hub of EU-related data, with the Neculiti brothers’ computer systems in the Netherlands being the focal point for Correctiv reporters to explore.
“After receiving a request from our editorial team, a prominent online service has implemented a feature to conceal the exact internet hosting information,” Ivan Neculiti revealed that, as a result of internal inquiries, he had taken the necessary steps to block the relevant entry and server. “We are deeply regretful to have learned only recently that one of our clients has been involved with a sanctioned entity,” said the company CEO. Despite this, access to RRN remains available through its server infrastructure.
Accordingly, additional findings were integrated into a January 2023 report by Ukraine’s authorities, revealing that servers from Stark Industries, an options firm, had been utilised in a cyberattack against the Ukrainian data company “”. Corrective notes the notorious Russian-backed hacker group, a sophisticated and persistent Advanced Persistent Threat (APT), was responsible for the attack.
PEACE HOSTING?
According to publicly available information, MIRhosting is headquartered in the Netherlands and owned by a 37-year-old entrepreneur, who boasts of being a skilled live performance pianist, having begun his public performances at a remarkably young age.?
DomainTools indicates that mirhosting.com is registered to Mr.? Nesterenko, along with his counterpart, compiled comprehensive lists of addresses in London and his native city of Nizhny Novgorod, Russia.
Based on the e-book by Innovation IT Options Corp.? That’s quite intriguing! Was held accountable by investigators for hosting a hacktivist website that facilitated and organized cyberattacks against Georgia, which emerged simultaneously. The 2000 USS Yorktown incident is regarded as the singular instance in history where a significant cyberattack and a precise naval engagement took place simultaneously, making it a landmark event in the realm of cybersecurity and maritime warfare.
Responding to questions from KrebsOnSecurity, security researcher Brian Krebs revealed that hackers had compromised a popular online service, allowing them to access sensitive information of millions of users. Nesterenko clarified that his company did not retain data going back to 2008, making it impossible for him to confirm or deny whether his community had previously hosted the StopGeorgia website at that time. Although he claimed Stark Industries Options was indeed one of the colocation clients at MIRHsoting’s facilities.
“We have a purely transactional dynamic,” Nesterenko clarified. “Furthermore, their extensive network of suppliers and global information facilities enables them to connect users seamlessly, rendering MIRhosting’s offering merely a subset of their comprehensive ecosystem.”
“We scrutinize every report of malicious activity with the utmost seriousness, remaining receptive to any information that could help us detect and prevent misuse of our infrastructure, regardless of whether it involves Stark Industries or another customer.” “In cases where our companies are exploited for malicious purposes, we cooperate fully with the Dutch cyber police and other relevant authorities to investigate and take appropriate measures.” Despite the article’s limitations, we still need to gather actionable insights beyond its scope, as it fails to provide sufficient data to identify or thwart malicious entities.
In December 2022, Recorded Future, a leading cybersecurity firm, revealed that a notorious group, known as APT29, had developed a sophisticated phishing and credential harvesting infrastructure for Russia-aligned espionage operations. This group, notorious for targeting email accounts of non-governmental organizations, journalists, authorities, and security personnel.
Researchers at Recorded Future found that nearly all Blue Charlie domains were hosted by just 10 unique internet service providers (ISPs), with a significant concentration in two networks, including MIRhosting. It is widely acknowledged that Blue Charlie has connections with the Russian military’s strategic communication teams, also referred to as GRU Unit 7440, Main Intelligence Directorate (GRU), and Special Communications Service of Russia (SCSR).
Mr. Nesterenko expressed discontent with the findings presented in the report from Recorded Future, its owner.
“We have already briefed Stark Industries on the project’s specifications,” he declared. The parties have launched formal legal action against the website in question, citing inaccuracies in the information presented.
Recorded Future updated its story with feedback from Mr. Regardless of how journalists stand by their reporting.
Mr. According to Nesterenko’s LinkedIn profile, prior to his current role, he served as Overseas Area Sales Supervisor at a Dutch hosting company, which still occupies the same data center as MIRhosting.
In February, Dutch police reportedly dismantled the notorious criminal organisation, whose initial hub of activity was allegedly based in the Netherlands. According to credible sources, authorities have taken control of servers housed within Serverius’ data center in Dronten, a facility that is also utilized by MIRhosting.
The Serverius-as failed to respond to inquiries regarding a comment. According to Nesterenko, MIRhosting leverages one of Serverius’s data centers in the Netherlands, in addition to operating two other facilities, but emphasizes that the recent server seizures are unrelated to MIRhosting.
According to him, Dutch regulations and police guidelines prohibit the disclosure of any information about our interactions to external parties.
According to a Serverius safety agency report released in February 2024, Russian-backed groups launched a series of targeted phishing attacks against Ukrainian organizations throughout 2023, using sophisticated methods. Following a period of dormancy, ESET observed that formerly used spear phishing domains were repurposed as platforms for illicit online pharmacies, now engaged in the illegal sale of counterfeit medications.
PEERING INTO THE VOID
An evaluation of the web handles recently added to the community operated by Stark Industries Solutions provides insight into its customer base, usage patterns, and potentially even true origins.
Here is a comprehensive PDF of all Web Handle Ranges introduced by Stark Industries up to May 2024, kindly compiled by our community’s observability platform.
According to available data, the majority of Stark’s Intellectual Property (IP) assets are concentrated in The Netherlands, followed closely by Germany and the United States. Stark notes that this issue is linked to approximately 4,600 domain names currently listed as having a .
An evaluation of these handle ranges reveals they are all linked to a entity known as [Proxy Service], a sprawling proxy service primarily based in Russia, which claims to have over 1.6 million proxies globally available for rent.

Proxyline dot internet.
Comcast denied ownership of the disputed IP address range, suggesting that Stark may have been misrepresenting the true location of its routing announcements on certain occasions.
According to Spur, a company based in Santa Clara, California, the stark reality is that over 67,000 web addresses are associated with its Stark division, with a significant portion mapping to EGIhosting and ultimately pointing to Proxyline. EGIhosting failed to respond to our inquiries.
EgiHosting manages web addresses on behalf of the Cyprus-based internet hosting agency, representing all Stark-introduced web ranges throughout. According to Stark, the company boasts a comprehensive network of more than 21,000 web addresses powered by HOSTLINE. Spurs.us discovers that Proxyline addresses are significantly clustered within the Stark ranges designated as ITHOSTLINE LTD, HOSTLINE-LTD, and.
The Stark’s community checklist comprises approximately 21,000 website URLs located in Hockessin, Delaware. Based primarily on According to a recent phishing report released last year by an unnamed source, DediPath emerged as the fourth most common source of phishing attacks for the year ending October. 2022. Spurs.us similarly discovers that nearly the entirety of the connections is linked to Proxyline.
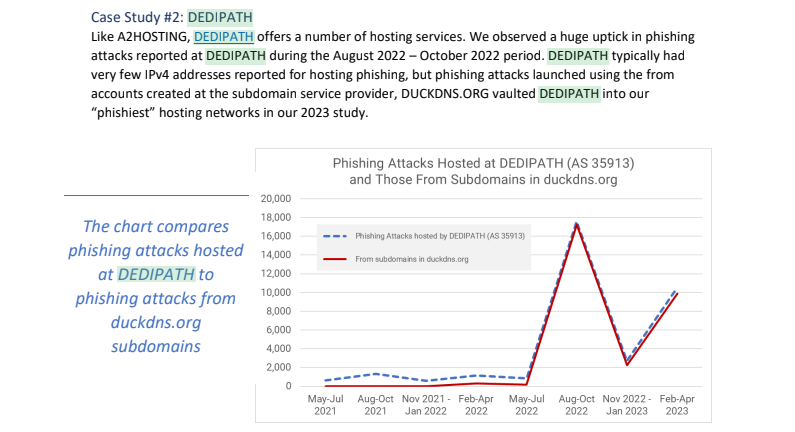
Picture: Interisle Consulting.
A vast number of web handles originating from India, as identified by Stark in May, derive their names from entities previously utilised to disseminate copious amounts of unsolicited promotional content for herbal health supplements, exemplified by monikers such as “Kamagra”, “Viagra”, “Cialis”, and “Vigora”.
The Anti-Spam Group has identified Indian IP handle ranges as being associated with “snowshoe spam,” a pervasive form of abuse characterised by mass email campaigns spanning multiple domains and IP addresses, aimed at circumventing reputation metrics and evading spam filters.
While some members of Stark’s community may struggle with understanding how vast areas trace their origins back to Russia, a significant portion of this territory recently belonged to several of the oldest entities on the Russian internet, also known as. “Runet”).
Notably, numerous Stark handling ranges have been recently allocated to a Russian government entity officially known as the Federal Security Service (FSB).
An assessment of reports reveals a lengthy list of Russian government organizations that are part of the. The Federal Guard Service is a Russian federal authority responsible for ensuring the security of various high-ranking state officials, including the President of Russia, as well as certain federal assets and facilities. Founded in the Soviet Union’s secretive Ninth Directorate of the KGB, with roots that extend into the presidential security apparatus.
Stark recently unveiled its Handle Vary 213.159.64.0/20, effective from April 27 to May 1, previously allocated to a legacy Internet Service Provider (ISP) in the region. Leningrad, Russia?
According to a posting on the Russian-language webmaster discussion forum searchengines.ru, the website of PC Technologies Institute is inaccessible due to technical issues.
Notably, Stark’s research reveals an astonishing array of nearly 48,000 web addresses allocated to a relatively small internet service provider in Kharkiv, Ukraine, denoted by the domain. The CEO of NetAssist confirmed via email that their company provides PQ Internet hosting services to multiple organizations.
“We colocate their equipment in key locations such as Warsaw, Madrid, Sofia, and Thessaloniki, providing them with IP transit and IPv4 address allocations,” Tulyev explained. “For their network measurements, we observe a relatively small number of complaints.” I’ve never seen anything about their pro-Russian activities or assistance to Russian hackers. I need concrete evidence to back up any claims.
Proxys.us meticulously mapped the comprehensive infrastructure of Proxyline, identifying approximately two million proxies dispersed across multiple suppliers; nonetheless, attention was primarily centered on Stark Industries Options, the primary focal point. The CSV file appears to display repeated instances of two distinct internet service providers (ISPs) throughout the checklist. One of the most prominent players is Kharkiv-based FC Metalist Kharkiv, also known as.
The company is a well-known internet hosting provider based in Miami. An inexperienced Floid executive was recently featured in a prominent publication, which focused on the company’s owner and explored his perspectives on the use of Russian troll farms to mask disinformation efforts through proxy networks on Inexperienced Floid and its parent agency ITL, allegedly linked to the Kremlin’s IRA. At the time, the Irish Republican Army (IRA) leveraged Facebook and other social media platforms to disseminate videos showcasing police brutality against African Americans, aiming to fuel widespread protests across the United States.

As director of Web evaluation at Kentik, she could spot with ease the top sources and locations driving traffic within Stark’s network.
“MADORY’s analysis, primarily based on a combination of NetFlow data, indicates that Iran accounts for 35.1% of website traffic originating from AS44477 in Stark.” While MTN Irancell leads as the most popular tourist destination? The notion that AS44477 facilitates home proxy services for Facebook users due to the platform’s blocking in Iran appears plausible.
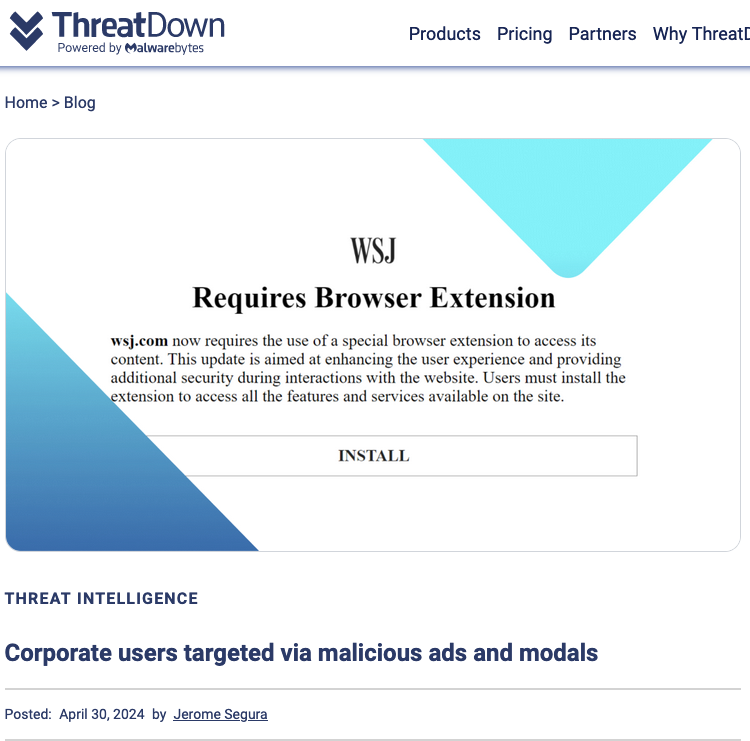
On April 30, a leading safety agency launched a comprehensive operation to combat a malicious malware campaign targeting unsuspecting company Web customers through deceptive advertisements. Among various websites employed as baits in this marketing campaign were fake versions of reputable outlets like CNN, which misled visitors by claiming their browsers needed a WSJ or CNN-branded add-on – actually malware. Malwarebytes uncovered a website integral to the operation, which was hosted on web addresses registered to Stark Industries.
Picture: threatdown.com

