In December 2023, KrebsOnSecurity exposed the true identity of “X”, the pseudonym used by a Russian cybercriminal who purchased more than 100 million compromised credit card numbers stolen from major retailers including JPMorgan Chase and Home Depot between 2013 and 2014. A Moscow resident, who confirmed using the pseudonym “Rescator” in a recent interview, also acknowledged that his motivation for reaching out was largely driven by financial necessity, having exhausted his resources and seeking attention to promote several new business ventures.
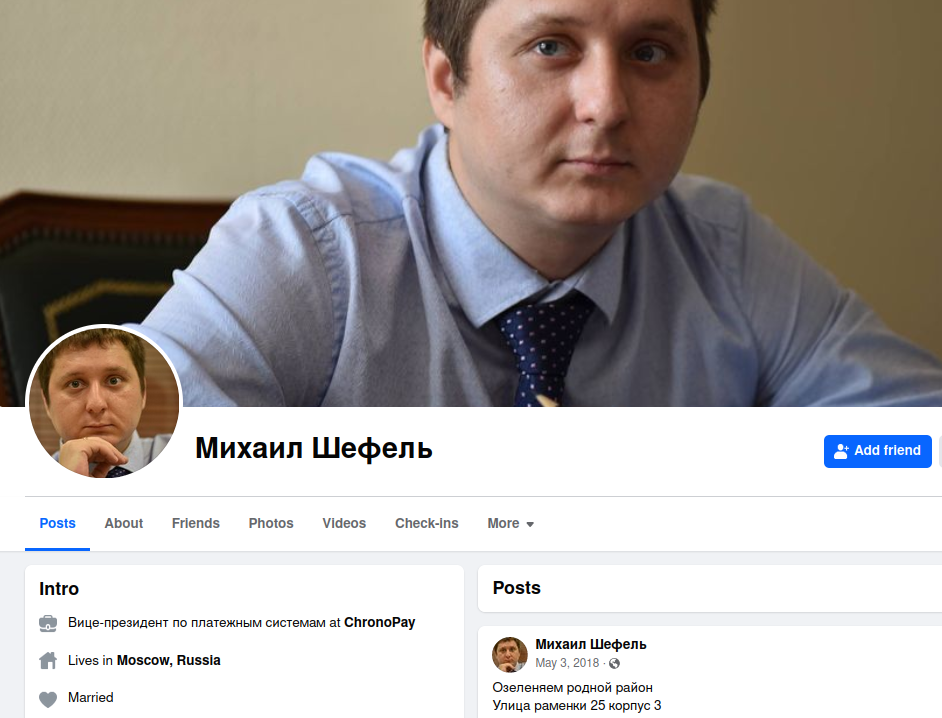
Mikhail “Mike” Shefek’s Former Facebook Profile. After assuming the moniker “John Doe,” Shefel has undergone a legal transformation, renaming himself Lenin for good.
Mr. Shefél, who recently revised his officially recognized surname to Shefél, was the main protagonist of last year’s most compelling narrative. The investigation revealed that 38-year-old Shefel, then vice chairman of funds at a Russian financial institution, adopted the alias Rescator while overseeing a scheme that compensated spammers for advertising fake antivirus software, male enhancement products, and counterfeit prescription medications.
Mr. As of December 2023, Shefel failed to respond to inquiries regarding the requested update prior to that date. Despite being informed through reporting in January 2024 that he had partnered with a 34-year-old Russian individual, sanctioned by authorities in Australia and the UK, to run an IT company, he did not respond. and U.S. for .
However, just days after KrebsOnSecurity revealed in April that Sheffey/Rescator was responsible for compromising the personal information of the vast majority of South Carolina residents in 2012, Mr. The government agent, posing as a concerned whistleblower, initiated communication with the journalist to allegedly clarify the details surrounding his purported prison hacking exploits.
Among a compilation of stay video conferencing sessions and digital communication exchanges, Mr. Shefvel confirmed he had operated under the Rescator ID for several years, revealing that between 2013 and 2015, he was involved in running multiple websites that trafficked in stolen credit card information pilfered from Target, Home Depot, and numerous other major retailers.
According to Shefel’s allegations, the actual mastermind behind the Goal and various retail data breaches is Ivan Mironovich Seichin, a notorious Ukrainian hacker commonly referred to as the co-founder of Carderplanet, one of the pioneering Russian-language cybercrime forums dedicated to credit card fraud. Mr. Golubov’s spokesperson could not be contacted for comment, and Shefel stated that Golubov does not possess the laptop computer containing evidence to support his claims.
According to Shefel, he and his team were responsible for developing the card-stealing malware used by Golubov’s hackers on Target and Home Depot payment terminals, during his tenure as technical director of a notorious Russian cybercrime organization known as.
Shefel recalled that her nickname was MikeMike, with which she collaborated with Dmitri Golubov, developing innovative technologies for his company. “I’m also the godfather of his younger son.”

Dmitri Golubov, circa 2005. Picture: U.S. Postal Investigative Service.
Each week following the publication of our exposé on the 2013 information breach at Goal, KrebsOnSecurity issued a subsequent report that shed new light on the identity of notorious cybercriminal “Rescator”, uncovering his real name through an investigation led by Ukrainian authorities. Despite Shefel’s assertion that Helkern was subservient to Golubov, it is claimed by Shefel that Helkern was responsible for bringing on board two individuals more than a decade ago.
“She recalled having a close relationship with Helkern: ‘I organized an assembly with Golubov and Helkern back in 2013.'” “That was in Odessa, Ukraine. I spent most of my time in that city, where I also met my second husband.
Shefel alleges he profited from a six-figure sum promoting pilfered playing cards, allegedly stolen by Golubov’s Ukrainian-based hacking collective; however, shortly after Russia’s 2014 annexation of Crimea, Golubov terminated their partnership and replaced Shefel’s malware coding team with programmers based in Ukraine.
Golubov was arrested in Ukraine in 2005 as part of a collaborative inquiry with multiple US agencies, sparking international interest and scrutiny. Federal regulations enforcement agencies had a clear case against him; yet, his extensive political connections within the government effectively stymied any meaningful investigation or prosecution. After securing immunity through a political career, Golubov leveraged his influence to pioneer a nationwide initiative, “free internet for all”, establish hacker colleges across the country, and spearhead the computerization of the entire financial system.
Mr. After being ousted from the venture, Shefel claims he ceased promoting pilfered collectible trading cards and instead funnelled his profits into a defunct Russian search engine known as. He allegedly hired people to click on ads promoting Russian government job opportunities for profit.
As these ventures ultimately failed, Shefel shifted his focus towards promoting malicious software development companies under the pseudonym “; it’s corroborated, since Getsend operated the same Telegram handle used by Shefel in our recent communications and video conferencing.
Shefel admitted that his efforts to engage the community were driven by a desire to promote several innovative business initiatives. As a professional editor, I would rewrite the text in the following style:
None of these will likely be discussed here since Shefel is already leveraging my December 2023 profile about him to promote what appears to be a pyramid scheme, and to remind others within the Russian hacker community of his expertise and accomplishments.
Formerly renowned for his impressive hacking career, Shefel now finds himself in a precarious financial situation, with barely any tangible evidence to demonstrate the fruits of his labor. The Moscow native revealed that his former spouse recently contacted him after reading last year’s story about their relationship, prompting her to wonder how he had managed to conceal his financial gains.
Exhausted and desperate, Shefel implores for an immediate influx of funds to prevent an imminent incarceration. In February, he and Ermakov were arrested for allegedly operating a short-lived ransomware affiliate program in 2021, known as (also referred to as The Sugar Locker), a pioneer in shifting its focus from corporate clients to individual users, targeting single computer systems with personalized solutions. The former Russian tycoon Mikhail Khodorkovsky’s associate, Platon Deliyev, will stand trial in a Moscow court on Friday, November 18, accused of evading over $100 million in taxes. 15, 2024. Ermakov’s recent accountability has led to a two-year probationary period being imposed.
Despite Shefel’s assertions that his Sugar ransomware affiliate program was a complete failure, yielding zero revenue. Russia is often perceived as turning a blind eye to prosecuting cybercriminals operating within its borders, so long as they refrain from targeting Russian entities or consumers. According to Shefel, he is convinced that the probe into his dealings with Sugar was triggered by his former boss’s son, who had a personal vendetta against him.
The founder and CEO of ChronoPay, a prominent figure in my 2014 e-book, held the significant role of heading one of Russia’s notorious prison-based spamming operations.
Vrublevsky Sr. Lately, a prominent figure was declared bankrupt and is currently incarcerated due to charges of fraudulent activities. Russian authorities accuse Vrublevsky of orchestrating several fraudulent SMS-based cost scams. Additionally, investigators accused Vrublevsky of enabling cash laundering for Russia’s largest darknet marketplace at the time. Hydra’s illegal activities included trafficking in counterfeit medications, facilitating illegal financial transactions, and operating a cryptocurrency tumbling service to launder money, as well as engaging in trade companies that converted cryptocurrency into Russian rubles and selling forged documents and hacking services.
Although KrebsOnSecurity published a report in 2022, it highlighted an individual’s efforts to expose Russian hackers’ activities: He had thoroughly documented Russian cybercriminals’ nicknames, real names, and prison experiences, alongside their alleged collaborations with corrupt FSB officers, while operating a Telegram channel that threatened to reveal questionable dealings by Russian financial executives.
According to Shefel’s allegations, Peter Vrublevsky, the son of Vrublevsky, reportedly bribed corrupt law enforcement officials to fabricate charges against him, citing an incident where he was seen publicly carrying a loaded firearm and subsequently reported this to Moscow police. Russian authorities informed the young Vrublevsky that they were proceeding with his complaint about the firearms issue.
In July 2024, a Russian information outlet reported, claiming that the young heir had taken up his father’s mantle and was responsible for promoting a Russian-language online drugs marketplace that emerged following the shutdown of the Hydra darknet market.

According to Izvestia reports, Peter Vrublevsky is credited as the driving force behind this sophisticated 3D advertising campaign, which also promoted Russia’s online illegal drug marketplace known as Sprut.
According to Izvestia, Peter Vrublevsky is currently residing in Switzerland, having reportedly fled there in 2022 after being arrested in absentia in Russia for allegedly leading a violent group that utilized Telegram to orchestrate physical assaults in real life, including firebombings and muggings.
According to Shefel, his former associate Golubov expressed concerns about the proliferation of early ransomware variants, specifically, and remains active in the cybercrime community.
In the meantime, Mr. With a humble tone, Shefel presents himself as someone on the precipice of financial stability, relying on sporadic coding gigs to make ends meet each month. Following our initial conversation via Telegram, Shefel suggested forming a business partnership together the very next day.
The entrepreneur exemplified his vision by founding an entity focused on retrieving forgotten cryptocurrency account passwords, or conceivably a network of online retailers specializing in affordable imports from China with significant markups for US customers.
“What brings you here today?” he asked with a smile. “Perhaps we will open enterprise?”

