
A massive global campaign of the Magniber ransomware has been launched, infecting devices worldwide, including those of residential customers, and extorting thousands of dollars in exchange for a decryption key.
Here is the rewritten text:
MAGNIBER emerged as the apparent successor to Cerber, following its detection being distributed via the Magnitude exploitation kit.
The ransomware operation has experienced intermittent activity over time, as threat actors have employed diverse tactics to disseminate Magniber and encrypt devices. The key to unlocking successful project management lies in embracing the trifecta of time management: prioritization, focus, and workflow optimization.
Unlike larger-scale ransomware operations, Magniber has typically targeted individual consumers who procure malicious software and run it on their home or small business networks.
In 2018, security experts at AhnLab successfully developed a solution to counteract the Magniber ransomware threat. However, the current solution fails to operate effectively due to the swift action of malicious actors, who exploited a previously identified vulnerability, thereby allowing for unimpeded file decryption.
Ongoing Magniber marketing campaign
Since July 20, BleepingComputer has witnessed a significant surge in the number of victims affected by the Magniber ransomware.
The Ransomware identification website ID-Ransomware has witnessed a significant uptick in activity, receiving almost 720 submissions since July 20, 2024.
It remains unclear how victims are becoming infected, although multiple victims have reported that their systems were subsequently encrypted after using software cracking tools or key generators – a tactic previously employed by threat actors.
Upon activation, this ransomware variant swiftly encrypts system data and adds a seemingly arbitrary extension of 5-9 characters to the filenames, often appearing as .oaxysw or .oymtk.
The ransomware may generate a ransom note, typically named “READ_ME.htm”, containing particulars on the incident, including affected data, alongside a new URL linking to the threat actor’s Tor-based ransom website.
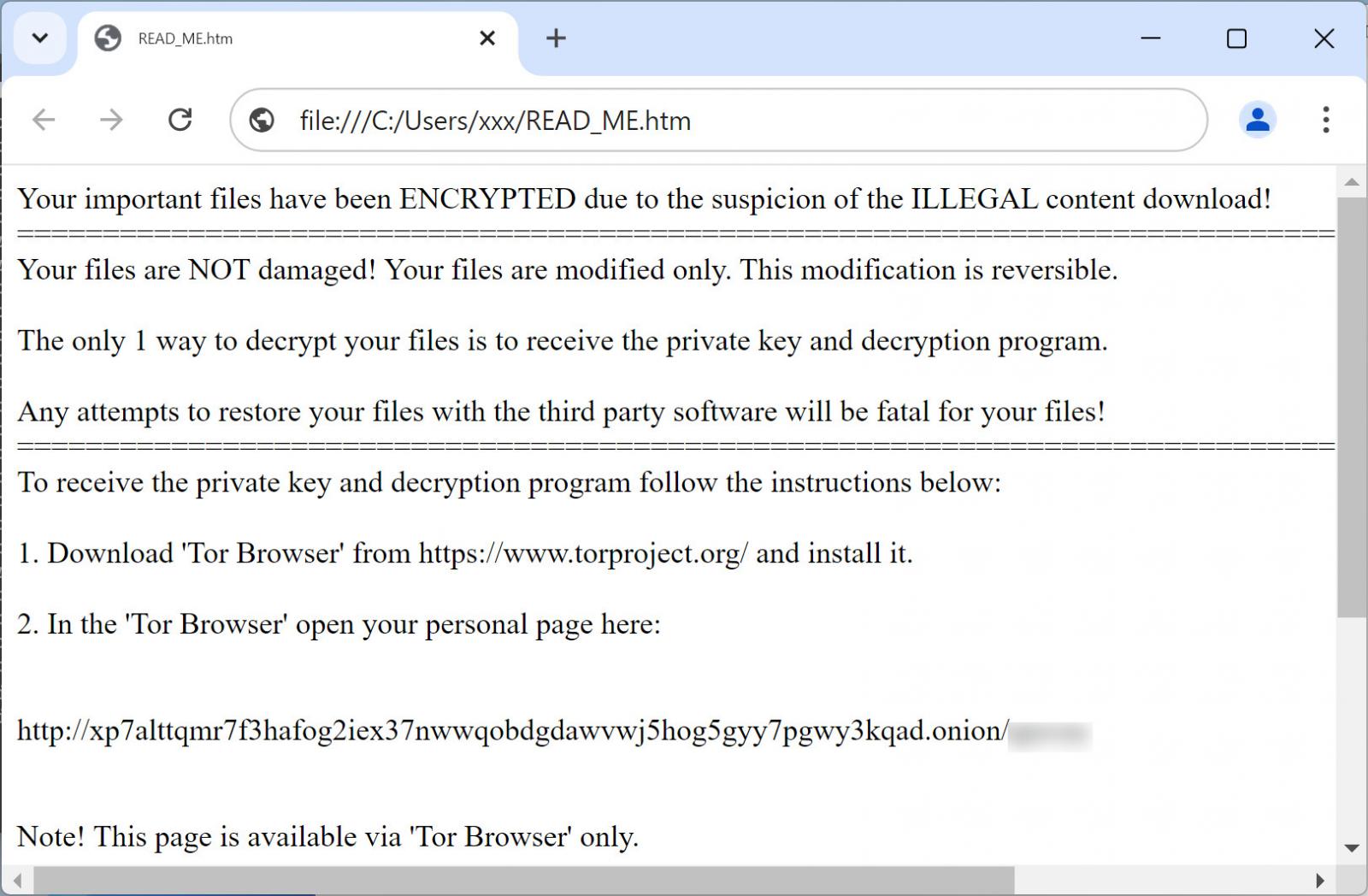
As Magniber malware occasionally targets unsuspecting customers, it initiates ransom demands that escalate from $1,000 to $5,000 within three days unless a Bitcoin payment is made.
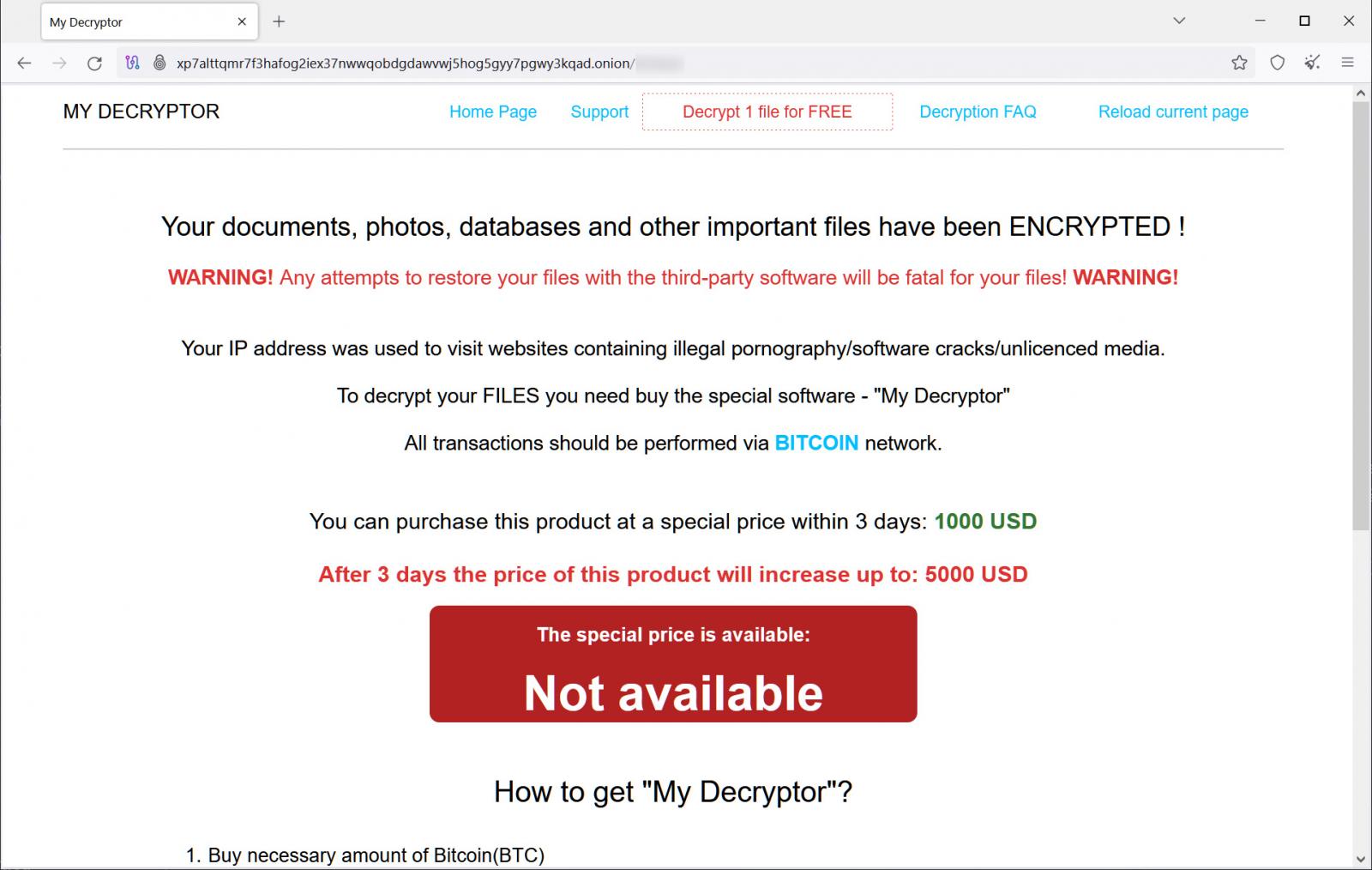
Unfortunately, there is currently no available option to decrypt information encrypted by modern variations of Magniber without incurring a cost.
While it may seem convenient to access software without paying, it’s crucially important to steer clear of software cracks and key generators, as not only is it illegal, but it also frequently serves as a vector for distributing malicious malware and ransomware.
For those affected by ransomware, please leverage our dedicated support channel to receive assistance or find answers to your queries.

