
A big-scale botnet is concentrating on Distant Desktop Protocol (RDP) providers in america from greater than 100,000 IP addresses.
The marketing campaign began on October 8 and based mostly on the supply of the IPs, researchers imagine the assaults are launched by a multi-country botnet.
RDP is a community protocol that permits distant connection and management of Home windows techniques. It’s sometimes utilized by directors, helpdesk employees, and distant staff.
Attackers typically scan for open RDP ports or attempt to brute-force logins, exploit vulnerabilities, or carry out timing assaults.
On this case, researchers at menace monitoring platform GreyNoise discovered that the botnet depends on two kinds of RDP-related assaults:
- RD Net Entry timing assaults – Probes RD Net Entry endpoints and measures response-time variations throughout nameless authentication flows to deduce legitimate usernames
- RDP internet consumer login enumeration – Interacts with the RDP Net Consumer login stream to enumerate consumer accounts by observing the distinction in server habits and responses
GreyNoise detected the marketing campaign after an uncommon visitors spike from Brazil, adopted by comparable exercise from a wider geography, which incorporates Argentina, Iran, China, Mexico, Russia, South Africa, and Ecuador.
The corporate says that the complete listing of nations with compromised units within the botnet exceeds 100.
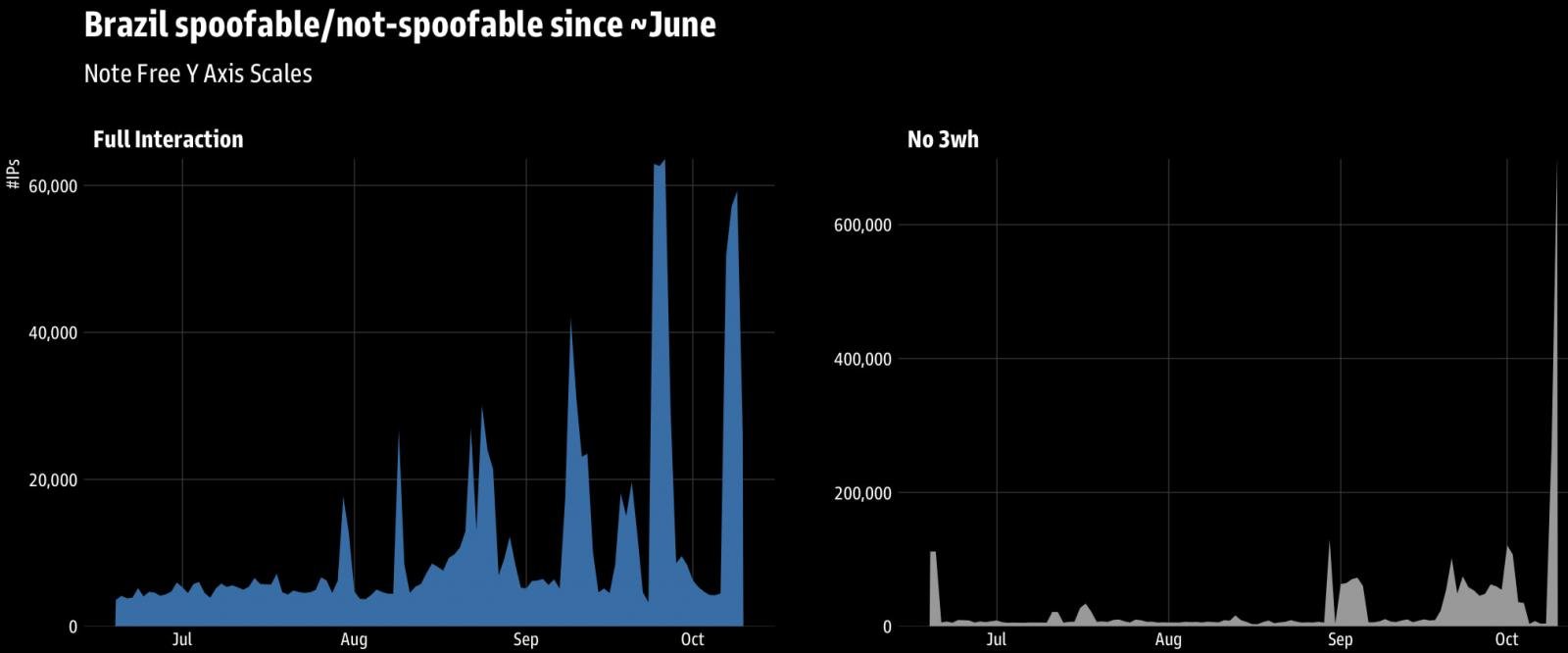
Supply: GreyNoise
Practically all IP addresses share a typical TCP fingerprint, and though there are variations within the (Most Phase Measurement), the researchers imagine that these are because of the clusters forming the botnet.
To defend towards this exercise, system directors are advisable to dam the IP addresses that launch the assaults and to examine the logs for suspicious RDP probing.
As a normal advice, a distant desktop connection shouldn’t be uncovered to the general public web and including a VPN and multi-factor authentication (MFA) provides a layer of safety.


