
Microsoft has introduced that the Home windows Administration Instrumentation Command-line (WMIC) software will likely be eliminated after upgrading to Home windows 11 25H2 and later.
WMIC is a legacy built-in Home windows command-line software that enables customers to work together with the Home windows Administration Instrumentation (WMI) system utilizing textual content instructions.
In a Microsoft 365 message middle replace, Microsoft now advises IT directors to change to Home windows PowerShell for WMI, scripts, and different instruments as a result of later Home windows releases will now not embody WMIC by default.
“Microsoft recommends utilizing PowerShell and different fashionable instruments for any duties beforehand accomplished with WMIC. You possibly can think about programmatic alternate options equivalent to WMI’s COM API, .NET libraries, or scripting languages. When you resolve in your approach ahead, please replace your inside IT documentation and processes,” the corporate stated.
Nonetheless, this alteration solely applies to the outdated WMIC element, because the Home windows Administration Instrumentation (WMI) itself stays unaffected.
Additional steering for many who use WMIC for administrative duties is accessible on this separate assist doc printed by Microsoft on Friday.
Microsoft deprecated WMIC in Home windows Server 2012 (in 2016) and in Home windows 10 21H1 (2021). Redmond transformed it right into a Function on Demand (FoD) beginning with Home windows 11 22H2 (in 2022) and introduced in January 2024 that it will be eliminated altogether after first disabling it by default.
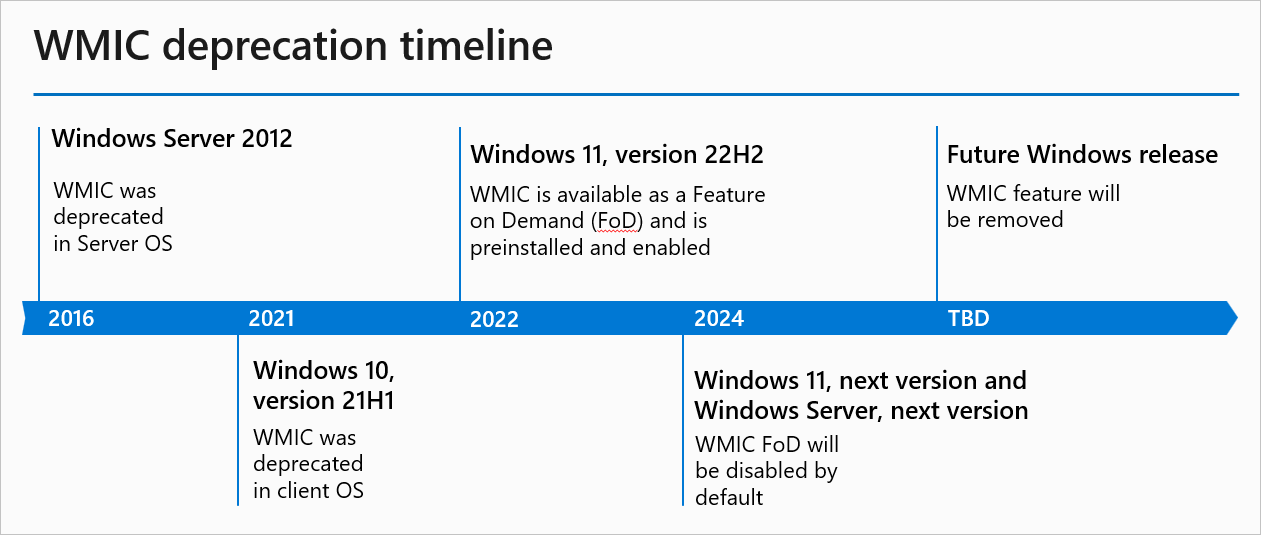
“We have been closely investing in PowerShell prior to now few years. The brand new instruments present a extra environment friendly approach of querying WMI. Eradicating a deprecated element helps cut back complexity whereas maintaining you safe and productive,” Microsoft stated in January 2024.
WMIC’s elimination may also enhance total safety by thwarting a variety of malware and assault techniques that can now not perform accurately.
The software has lengthy been thought of a LOLBIN (living-off-the-land binary), a Microsoft-signed executable that menace actors exploit for a variety of malicious actions throughout assaults.
For example, ransomware encryptors generally use the WMIC command to delete Shadow Quantity Copies, guaranteeing that victims cannot use them to get better encrypted information. Different menace actors have used WMIC to question for the checklist of put in antivirus software program and uninstall it.
Malware has additionally been noticed utilizing WMIC so as to add exclusions to Microsoft Defender, evading detection when launched.


