
A brand new Spectre-like assault dubbed VMScape permits a malicious digital machine (VM) to leak cryptographic keys from an unmodified QEMU hypervisor course of working on fashionable AMD or Intel CPUs.
The assault breaks the isolation between VMs and the cloud hypervisor, bypassing present Spectre mitigations and threatening to leak delicate information by leveraging speculative execution.
The researchers spotlight that VMScape doesn’t require compromising the host and works on unmodified virtualization software program with default mitigations enabled on the {hardware}.
They word {that a} menace actor may deploy such an assault in opposition to a cloud supplier by merely renting a digital machine to leak secrets and techniques from the hypervisor or different VMs.
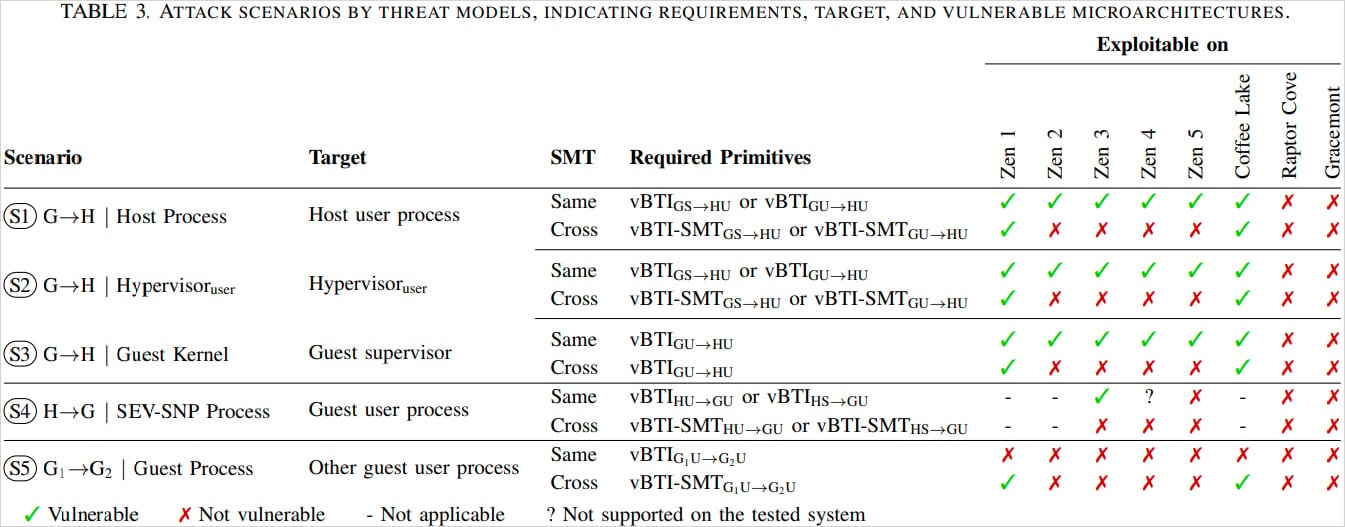
VMScape was developed by a group of researchers at ETH Zurich public college in Switzerland, who found that it impacts all AMD processors from Zen 1 to Zen 5, in addition to Intel’s “Espresso Lake” CPUs. The newer, “Raptor Cove” and “Gracemont” will not be impacted.
Leaking secrets and techniques from QEMU
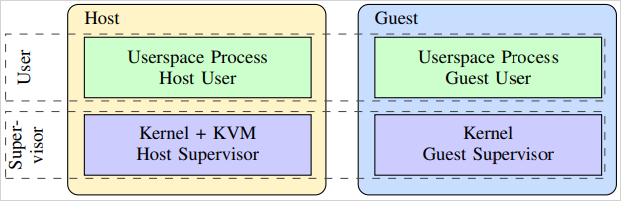
Fashionable CPUs shield in opposition to speculative assaults by extending isolation to department prediction models (BPU) between the visitor and host, however the researchers found that this isolation is incomplete.
Supply: ETH Zurich
A visitor person can affect oblique department prediction in a bunch person course of as a consequence of shared BPU constructions just like the BTB (Department Goal Buffer), IBP/ITA, and BHB (Department Historical past Buffer).
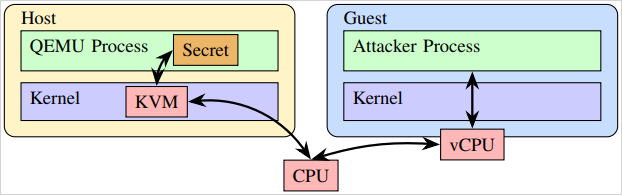
The assault targets QEMU, the user-mode hypervisor part, which maps visitor reminiscence into its deal with area, enabling using a ‘FLUSH+RELOAD’ cache aspect channel.
ETH Zurich researchers used a Spectre-BTI (Department Goal Injection) assault to misguide a goal oblique department in QEMU so it speculatively executes a disclosure gadget that leaks secret information into the shared reload buffer.
Supply: ETH Zurich
To increase the speculative execution window, the attacker evicts related cache entries from contained in the visitor by constructing eviction units concentrating on the Final-Stage Cache (LLC) on AMD Zen 4 CPUs.
ASLR (Deal with House Format Randomization), a safety characteristic that randomizes the reminiscence addresses the place information is loaded in a course of, is defeated by probing for department collisions to find the sufferer gadget and brute-forcing the digital deal with of the reload buffer.
ETH Zurich researchers confirmed that VMScape leaks arbitrary reminiscence information from QEMU at a fee of 32 bytes/second, with a byte-level accuracy of 98.7%, and an total exploit success fee of 43%.
At this fee, a 4KB secret, akin to a disk encryption key, could possibly be leaked in 128 seconds. The full end-to-end time, together with the ASLR bypassing course of, can be 772 seconds, or simply beneath 13 minutes.
Impression and response
Virtualization is the spine of cloud computing, and if one visitor machine can learn reminiscence from the host, it threatens multi-tenant cloud safety.
Nonetheless, it’s important to emphasise that assaults like VMScape require superior data, deep technical experience, and sustained execution time. Due to this, such assaults, even when doable, don’t symbolize a menace to the bigger userbase.
Supply: ETH Zurich
The ETH Zurich group reported their findings to AMD and Intel on June 7, and the situation acquired the identifier CVE-2025-40300. AMD has launched a safety bulletin about the issue.
Linux kernel builders launched patches that mitigate VMScape by including an IBPB (Oblique Department Prediction Barrier) on VMEXIT, successfully flushing the BPU when switching from visitor to host. The researchers say that this mitigation has minimal efficiency impression in frequent workloads.


