Authored by SangRyol Ryu
Just lately, McAfee’s Cellular Analysis Crew uncovered a brand new kind of cell malware that targets mnemonic keys by scanning for photographs in your system that may include them. A mnemonic key’s primarily a 12-word phrase that helps you recuperate your cryptocurrency wallets. It’s a lot easier to recollect than the everyday advanced “non-public key” it stands for.
This Android malware cleverly disguises itself as numerous reliable apps, starting from banking and authorities companies to TV streaming and utilities. Nevertheless, as soon as put in, these faux apps secretly collect and ship your textual content messages, contacts, and all saved photographs to distant servers. They usually distract customers with infinite loading screens, surprising redirects, or temporary clean screens to cover their true actions.
McAfee has recognized over 280 faux purposes concerned on this scheme, which have been actively focusing on customers in Korea since January 2024. Fortunately, McAfee Cellular Safety merchandise are already looking out for this menace, often known as SpyAgent, and are serving to to maintain your system protected from these misleading ways.
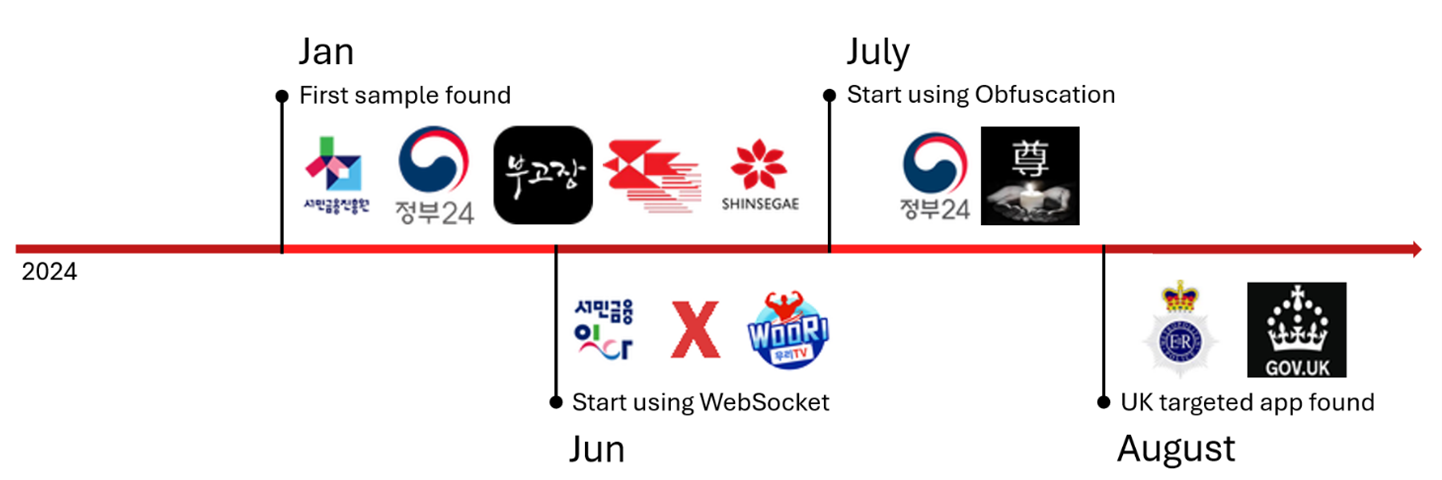
Determine 1 Timeline of this marketing campaign
Distribution Mechanism
Cellular malware that targets customers in Korea is principally unfold via intelligent phishing campaigns. These campaigns use textual content messages or direct messages on social media to ship out dangerous hyperlinks. The attackers behind these messages usually faux to be organizations or individuals you belief, tricking you into clicking on their hyperlinks. As soon as clicked, these hyperlinks take you to faux web sites that look extremely actual, mimicking the looks of reputable websites. These misleading websites normally immediate you to obtain an app, which is how the malware will get put in in your system. Be cautious and at all times confirm the authenticity of any message or hyperlink earlier than clicking.
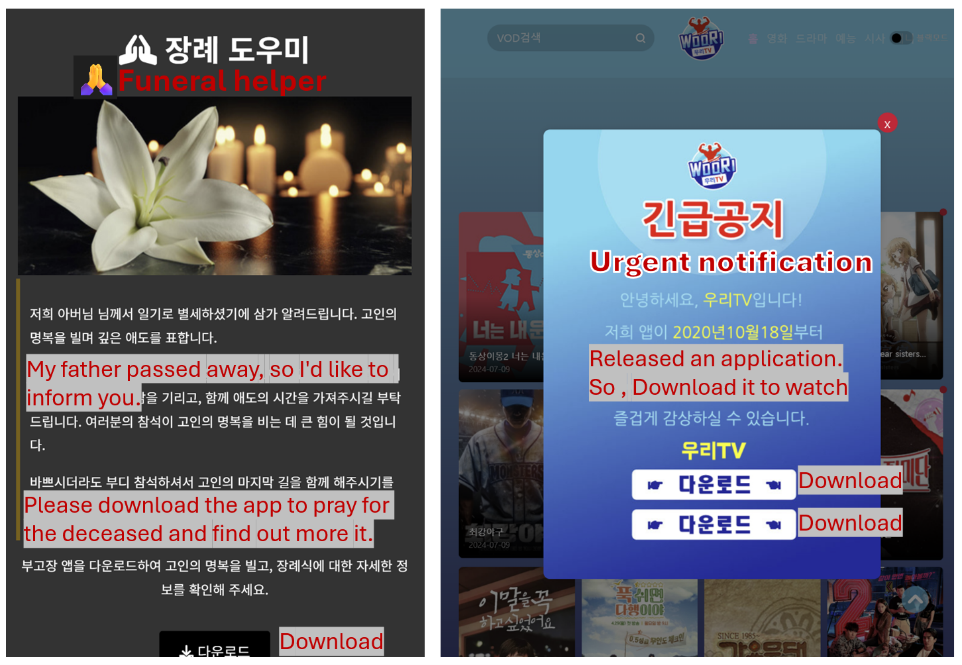
Determine 2 Faux Web sites
When a consumer clicks on the obtain hyperlink, they’re prompted to obtain an APK (Android Bundle Package) file. Though this file seems to be a reputable app, it’s truly malicious software program. As soon as the APK is downloaded, the consumer is requested to put in the app. Throughout set up, the app requests permission to entry delicate data akin to SMS messages, contacts, and storage, and to run within the background. These permissions are sometimes introduced as obligatory for the app to operate correctly, however in actuality, they’re used to compromise the consumer’s privateness and safety.
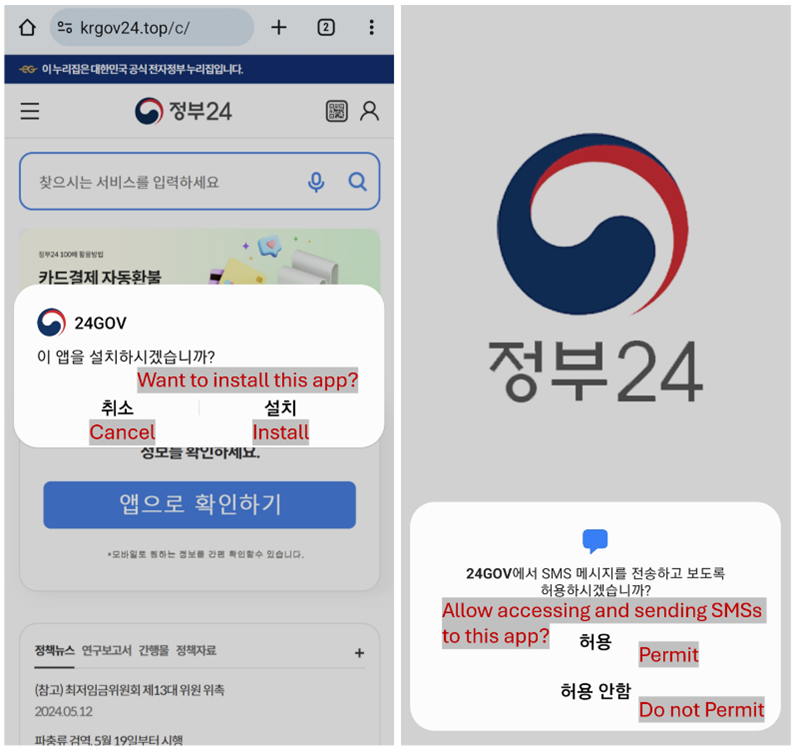
Determine 3 App set up and requesting permissions
Malware Capabilities and Habits
As soon as the app is put in and launched, it begins its most important operate of stealing delicate data from the consumer and sending it to a distant server managed by the attackers. The sorts of knowledge it targets embody:
- Contacts: The malware pulls the consumer’s complete contact record, which may very well be used for additional misleading practices or to unfold the malware even additional.
- SMS Messages: It captures and sends out all incoming SMS messages, which could embody non-public codes used for two-factor authentication or different essential data.
- Pictures: The app uploads any photographs saved on the system to the attackers’ server. These may very well be private photographs or different delicate photographs.
- Gadget Info: It gathers particulars in regards to the system itself, just like the working system model and telephone numbers. This data helps the attackers customise their malicious actions to be more practical.
The malware features like an agent, able to receiving and finishing up directions from the distant server. These instructions embody:
- ‘ack_contact’: A affirmation sign that the server has obtained the contacts record.
- ‘ack_sms’: A affirmation sign that the server has obtained SMS messages.
- ‘ack_image’: A affirmation sign that the server has obtained photographs.
- ‘sound_mode_update’: A command that adjustments the sound settings of the system.
- ‘send_sms’: A command that allows the malware to ship SMS messages from the system, which may very well be used to distribute phishing texts.
Command and Management Servers Investigation
In the course of the investigation, the crew found a number of key insights:
Insecure Command and Management Server: A number of C2 servers had been discovered to have weak safety configurations, which allowed unauthorized entry to particular index pages and information without having credentials. This safety lapse supplied a deeper perception into the server’s features and the sorts of knowledge being gathered.
Upon examination, it was famous that the server’s root listing included a number of folders, every organized for various sides of the operation, akin to mimicking banking establishments or postal companies.
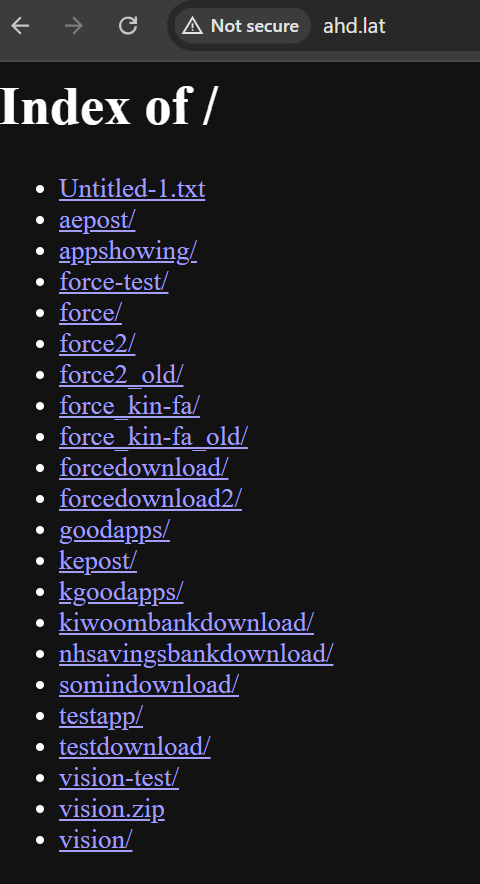
Determine 4 Uncovered Indexing web page of the foundation previous to the location being taken down
As a result of server’s misconfiguration, not solely had been its inside parts unintentionally uncovered, however the delicate private knowledge of victims, which had been compromised, additionally grew to become publicly accessible. Within the ‘uploads’ listing, particular person folders had been discovered, every containing photographs collected from the victims, highlighting the severity of the information breach.
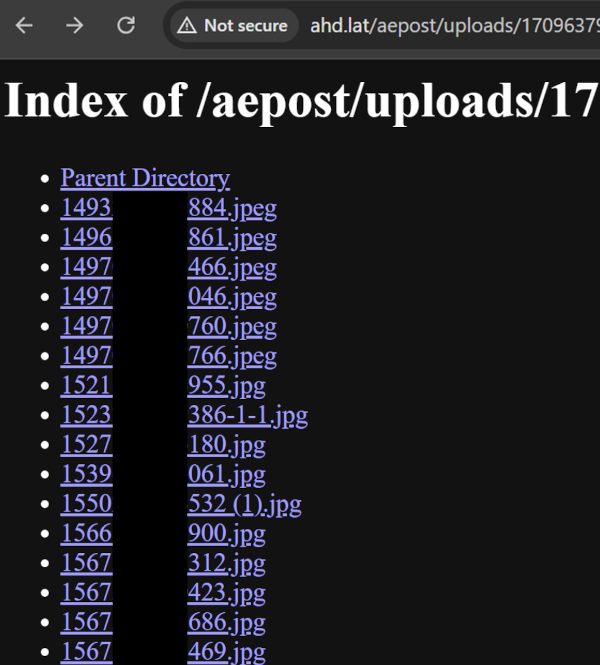
Determine 5 Leaked photographs record from one of many victims of the ‘aepost’ marketing campaign previous to the location being taken down
Admin Pages: Navigating from the uncovered index pages led to admin pages designed for managing victims. These pages displayed an inventory of units, full with system data and numerous controllable actions. Because the variety of victims rises, the record of units on these pages will increase accordingly.
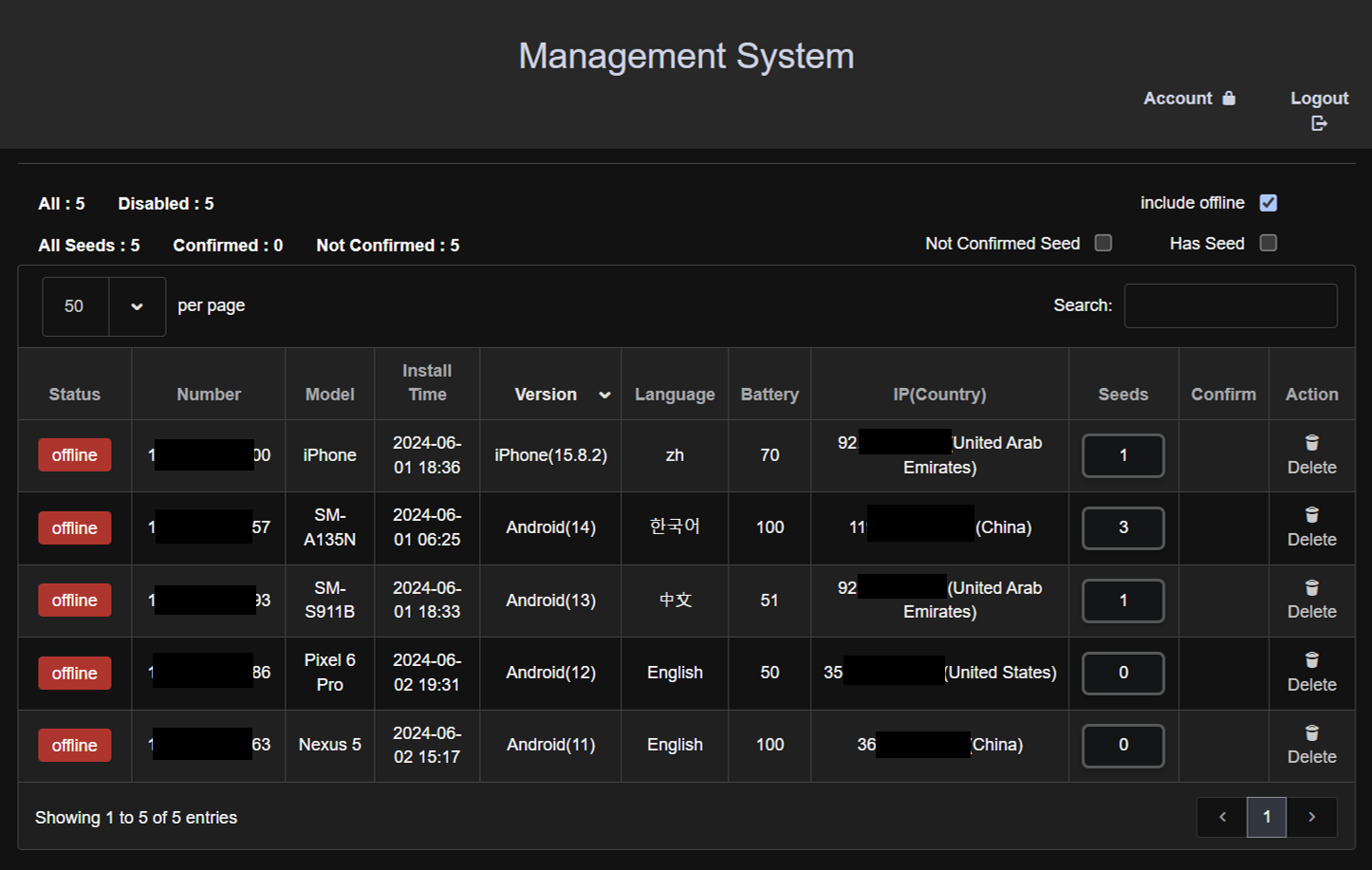
Determine 6 Admin management panel
Focusing on Cryptocurrency Wallets: Upon analyzing the web page, it grew to become clear {that a} major objective of the attackers was to acquire the mnemonic restoration phrases for cryptocurrency wallets. This means a serious emphasis on gaining entry to and probably depleting the crypto belongings of victims.
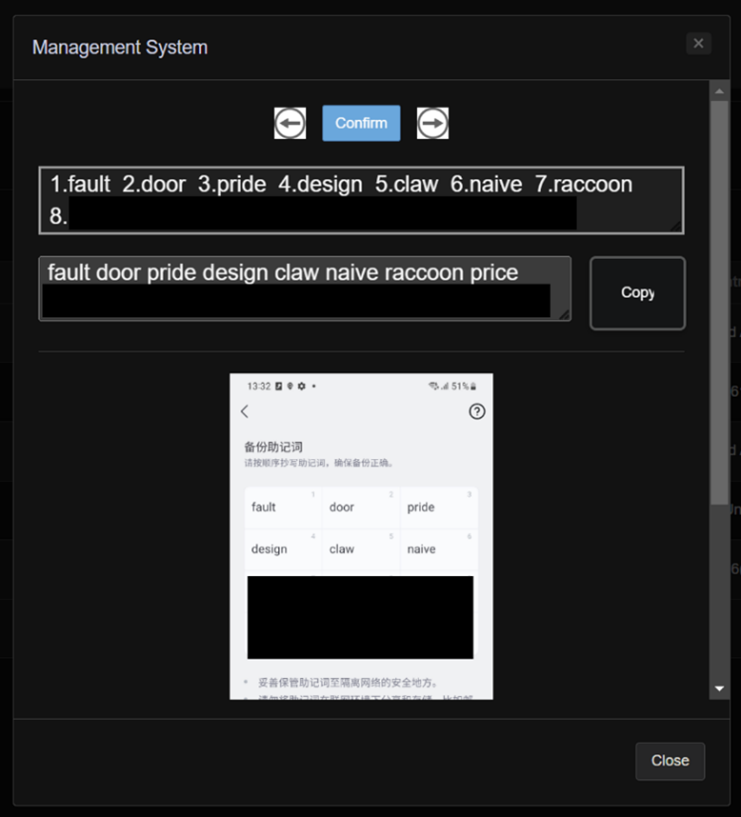
Determine 7 OCR particulars on Admin web page
Knowledge Processing and Administration: This menace makes use of Python and Javascript on the server-side to course of the stolen knowledge. Particularly, photographs are transformed to textual content utilizing optical character recognition (OCR) strategies, that are then organized and managed via an administrative panel. This course of suggests a excessive degree of sophistication in dealing with and using the stolen data.
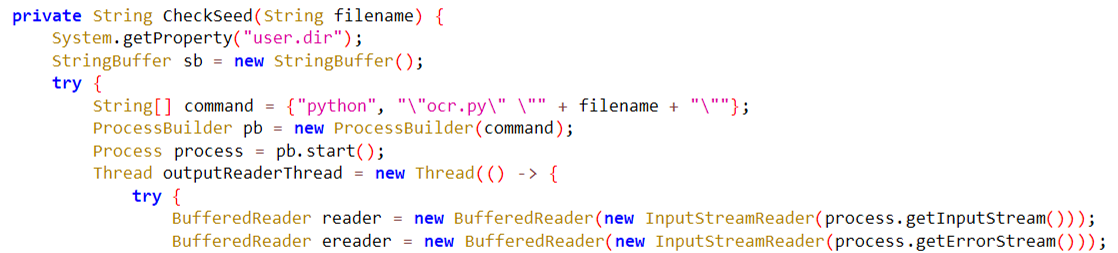
Determine 8 Server-side OCR code
Evolution
Initially, the malware communicated with its command and management (C2) server by way of easy HTTP requests. Whereas this technique was efficient, it was additionally comparatively simple for safety instruments to trace and block. In a big tactical shift, the malware has now adopted WebSocket connections for its communications. This improve permits for extra environment friendly, real-time, two-way interactions with the C2 server and helps it keep away from detection by conventional HTTP-based community monitoring instruments. This variation additionally makes it tougher for safety researchers to investigate visitors and intercept malicious communications.
The malware has additionally seen substantial enhancements in its obfuscation strategies, which additional complicates detection efforts by safety software program and researchers. APK obfuscation now conceals malicious code utilizing methods like string encoding, the insertion of irrelevant code, and the renaming of features and variables to confuse analysts. These strategies not solely create confusion but additionally delay the detection course of, successfully masking the malware’s true operations.
Furthermore, the malware’s utility and focusing on methods have advanced. Current observations point out that the malware has tailored and begun to unfold inside the UK. This improvement is important because it reveals that the menace actors are increasing their focus each demographically and geographically. The transfer into the UK factors to a deliberate try by the attackers to broaden their operations, possible aiming at new consumer teams with localized variations of the malware.
Conclusion
The continual evolution of this malware highlights the ever-changing and complex nature of cyber threats right now. Initially masquerading as apps for cash loans or authorities companies, it has now tailored to take advantage of private feelings by mimicking obituary notices. The analysis crew has found that the perpetrators are using OCR know-how to investigate and misuse the stolen knowledge for monetary advantages. Because the malware advances, using extra intricate strategies, forecasting its subsequent strikes turns into more and more difficult. Cybercriminals are continuously enhancing their ways to higher infiltrate and manipulate consumer environments, escalating the hazard posed by these threats over time.
Though this malware isn’t extensively prevalent, its affect intensifies when it leverages a sufferer’s contacts to ship misleading SMS messages. These phishing messages, seemingly despatched by a well-recognized contact, usually tend to be trusted and acted upon by recipients. As an example, an obituary discover showing to come back from a good friend’s quantity may very well be perceived as genuine, vastly elevating the chance of the recipient participating with the rip-off, particularly in comparison with phishing makes an attempt from unknown sources. This technique introduces a misleading layer that considerably enhances the effectiveness and stealthiness of the assault. Early detection of such malware is vital to stop its proliferation, reduce potential hurt, and curb additional escalation. In response, the crew has taken proactive steps by reporting the lively URLs to the related content material suppliers, who’ve promptly eliminated them.
The invention of an merchandise labeled “iPhone” within the admin panel signifies that the subsequent stage of this malware’s improvement may goal iOS customers. Whereas no direct proof of an iOS-compatible model has been discovered but, the potential for its existence is real. Our crew has beforehand documented data-stealing actions affecting each Android and iOS platforms, suggesting that the menace actors could be engaged on an iOS variant. That is significantly alarming as a result of, regardless of iOS’s popularity for safety, there are nonetheless strategies for putting in malicious apps outdoors of the App Retailer, akin to via enterprise certificates and instruments like Scalet. This potential shift to iOS highlights the necessity for vigilance throughout all cell platforms.
In such a panorama, it’s essential for customers to be cautious about their actions, like putting in apps and granting permissions. It’s advisable to maintain essential data securely saved and remoted from units. Safety software program has grow to be not only a advice however a necessity for safeguarding units. The McAfee Cellular Analysis crew continues to remain alert, implementing sturdy safety measures to counter these superior threats. McAfee Cellular Safety merchandise are designed to detect and defend in opposition to not solely malware but additionally different undesirable software program. For additional particulars, please go to our McAfee Cellular Safety web site.
Indicators of Compromise
SHA256 Hash(es):
- 5b634ac2eecc2bb83c0403edba30a42cc4b564a3b5f7777fe9dada3cd87fd761
- 4cf35835637e3a16da8e285c1b531b3f56e1cc1d8f6586a7e6d26dd333b89fcf
- 3d69eab1d8ce85d405c194b30ac9cc01f093a0d5a6098fe47e82ec99509f930d
- 789374c325b1c687c42c8a2ac64186c31755bfbdd2f247995d3aa2d4b6c1190a
- 34c2a314dcbb5230bf79e85beaf03c8cee1db2b784adf77237ec425a533ec634
- f7c4c6ecbad94af8638b0b350faff54cb7345cf06716797769c3c8da8babaaeb
- 94aea07f38e5dfe861c28d005d019edd69887bc30dcc3387b7ded76938827528
- 1d9afa23f9d2ab95e3c2aecbb6ce431980da50ab9dea0d7698799b177192c798
- 19060263a9d3401e6f537b5d9e6991af637e1acb5684dbb9e55d2d9de66450f2
- 0ca26d6ed1505712b454719cb062c7fbdc5ae626191112eb306240d705e9ed23
- d340829ed4fe3c5b9e0b998b8a1afda92ca257732266e3ca91ef4f4b4dc719f8
- 149bd232175659434bbeed9f12c8dd369d888b22afaf2faabc684c8ff2096f8c
- f9509e5e48744ccef5bfd805938bf900128af4e03aeb7ec21c1e5a78943c72e7
- 26d761fac1bd819a609654910bfe6537f42f646df5fc9a06a186bbf685eef05b
- 0e778b6d334e8d114e959227b4424efe5bc7ffe5e943c71bce8aa577e2ab7cdb
- 8bbcfe8555d61a9c033811892c563f250480ee6809856933121a3e475dd50c18
- 373e5a2ee916a13ff3fc192fb59dcd1d4e84567475311f05f83ad6d0313c1b3b
- 7d346bc965d45764a95c43e616658d487a042d4573b2fdae2be32a0b114ecee6
- 1bff1823805d95a517863854dd26bbeaa7f7f83c423454e9abd74612899c4484
- 020c51ca238439080ec12f7d4bc4ddbdcf79664428cd0fb5e7f75337eff11d8a
Area(s):


