Researchers probing cyber safety have identified a vulnerability in the RADIUS protocol, codenamed BlastRADIUS. Although there’s no evidence of malicious exploitation, it’s still imperative that all RADIUS servers are promptly updated.
A Blast Radius assault involves the attacker intercepting traffic between a user’s device, such as a router, and the RADIUS server. The attacker can subsequently manipulate the MD5 hashing algorithm to convincingly represent an Entry-Denied community packet as an Entry-Settle packet. Without proper authentication, this grants unauthorized access to the consumer system.
A group of researchers from Boston College, , BastionZero, Microsoft Analysis, Centrum Wiskunde & Informatica and the College of California, San Diego first found the vulnerability in February and notified Alan DeKok, chief government officer of InkBridge Networks and RADIUS knowledgeable.
A newly tracked vulnerability, dubbed CVE-2022-26809 ( ) and CVE-2022-26810 ( ), has been identified as resulting from an “elementary design flaw of the RADIUS protocol”, according to a statement issued by FreeRADIUS, maintained by DeKok. Not limited to a solitary product or provider.
“Community technicians are tasked with implementing firmware updates and reconfiguring approximately every switch, router, GGSN, BNG, and VPN concentrator globally,” he explained during an interview. “We expect a surge in discussions and activity surrounding RADIUS security over the next few weeks.”
What’s the RADIUS protocol?
RADIUS (Remote Authentication Dial-In User Service) is a widely-used networking protocol that provides centralized authentication, authorization, and accounting (AAA) services for users accessing a network or system from a remote location. Extensively used by web service providers and enterprises to manage switches, routers, gateways, firewalls, and virtual private network (VPN) solutions.
Organizations and individuals leveraging Radius-based authentication protocols for network access control are impacted by the BlastRADIUS vulnerability.
Researchers have identified vulnerabilities in RADIUS deployments employing PAP, CHAP, MS-CHAP, and RADIUS/UDP transmission over the internet, suggesting that these configurations may be impacted by the newly discovered BlastRADIUS flaw. ISPs, cloud identity providers, telecommunications companies, and internal network operators are vulnerable to attack and must act promptly, especially if using RADIUS for administrative login authentication.
Individuals accessing the internet from home are not inherently vulnerable, yet they do rely on their Internet Service Provider (ISP) addressing the Blast Radius vulnerability, lest their traffic be redirected to a system under the attacker’s control.
Enterprises leveraging PSEC, TLS, and 802.1X protocols, as well as organizations partaking in networks such as eduroam and OpenRoaming, are widely regarded as secure.
BlastRADIUS assaults are a type of attack that utilizes explosive energy to disorient and damage enemies. When initiated, this ability releases a shockwave that radiates outward from the player, dealing moderate damage to all targets within its range.
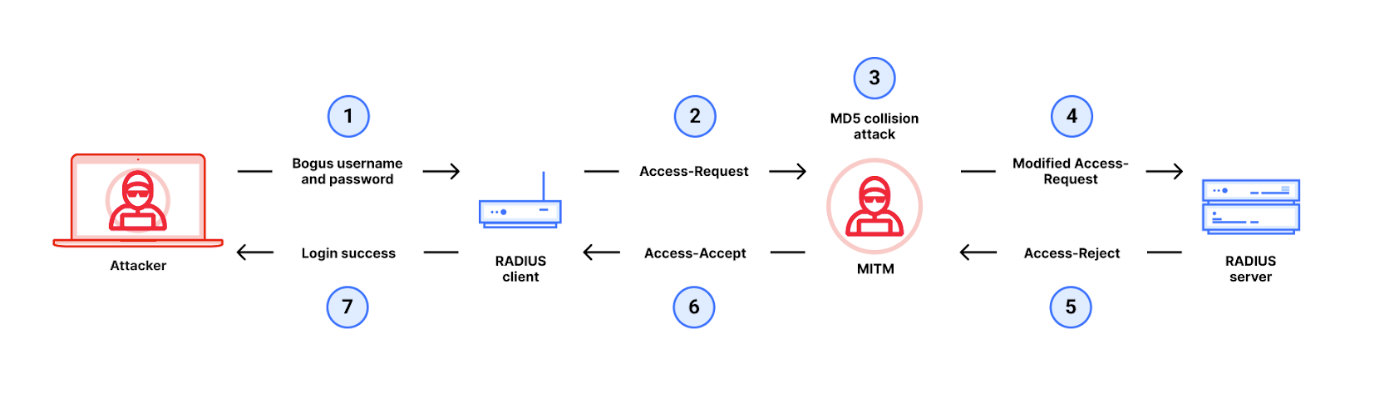
Exploiting this vulnerability enables an attacker to launch a man-in-the-middle attack against the RADIUS authentication process. Within the RADIUS protocol, a crucial aspect is that certain Entry-Request packets ought to bypass authentication and forego integrity checks altogether.
A malicious actor initiates a login attempt against the end-user’s account using invalid authentication credentials, generating an Entry-Request message sent to the server for processing. The message is shipped along with a 16-byte entity known as the Request Authenticator, which is produced through the application of an MD5 hash function.
The Request Authenticator serves as a mechanism for the recipient server to calculate its response in conjunction with a shared secret, known only to the consumer and server. When a consumer receives the response, they likely utilize their Request Authenticator and shared secret to decipher the packet, thereby confirming that it originated from a trusted server.
In a Blast Radius attack, the aggressor intercepts and alters the Entry-Request message before it can reach the server, exploiting an MD5 collision vulnerability. When an attacker supplies deliberately inaccurate data in an Entry-Request message, it is ensured that any subsequent Entry-Denied response from the server will also incorporate these invalid details. By exploiting this Entry-Denied response, attackers modify it to masquerade as an acceptable Entry-Approved message, thereby gaining unauthorized access.
While MD5’s vulnerabilities permit attacks to produce collisions or invert the hash, the researchers assert that the newly discovered BlastRADIUS attack surpasses existing weaknesses in terms of speed and scalability. That was the initial instance where a MD5 attack was successfully demonstrated against the RADIUS protocol.
Researchers at Cloudflare conducted an attack on RADIUS devices with a 5-minute timeout interval. Despite these limitations, there still exists room for sophisticated hackers leveraging modest computational resources to execute this attack within a remarkably shorter timeframe, potentially as brief as 30-60 seconds – a timing threshold that aligns with many RADIUS devices’ default timeout intervals.
“The significance of this vulnerability lies in the fact that many Entry-Request packets lack essential authentication and integrity checks.” An attacker can subsequently execute a targeted prefix attack, allowing them to alter the Entry-Request in order to substitute a genuine response with one of their own choosing.
“While authentication and integrity checks are in place, a clever attacker can exploit the chosen prefix vulnerability to manipulate the response packet with remarkable flexibility.”
You probably can learn anything.
The BlastRADIUS vulnerability can be exploited with moderate complexity.
While the BlastRADIUS vulnerability is widespread, exploiting it requires significant capabilities; attackers must be able to capture, inspect, block, and manipulate both incoming and outgoing community packets, rendering publicly available exploits irrelevant. The attacker should also possess current community access, which can be obtained by leveraging an organization’s infrastructure to send RADIUS/UDP packets over the open internet or by compromising a portion of the enterprise network.
Researchers warn that even when RADIUS visitors are isolated within a secure internal network, misconfigured routing or errors can still inadvertently compromise their security. An attacker with partial community access may potentially exploit DHCP or alternative protocols to coerce victim devices into routing traffic outside of a dedicated VPN.
The attacker would need significant funding, as orchestrating a large-scale BlastRADIUS attack necessitates substantial cloud computing resources to execute effectively. According to InkBridge Networks, such prices may constitute a mere “drop in the bucket” for nation-states seeking to target specific audiences.
Organisations must proactively fortify their digital perimeters to safeguard against the ever-evolving threats of a BlastRadius assault. Firstly, implement robust network segmentation and strict access controls to confine potential vulnerabilities within isolated environments. Secondarily, conduct meticulous vulnerability assessments and penetration testing to identify exploitable weaknesses, thereby enabling prompt remediation.
The safety research team provides organizations utilizing the RADIUS protocol with the following recommendations:
- Recent Updates to All RADIUS Purchasers and Servers Installed by Our Organization:
As part of our ongoing commitment to providing top-notch support and security for our customers, we have recently pushed out a series of updates to all RADIUS purchasers and servers installed by our organization.
The primary focus of these updates was to address any lingering issues with the previous versions, as well as introduce new features designed to further enhance the overall performance and reliability of your installations. Patches have been successfully deployed to ensure that Message-Authenticator attributes are consistently dispatched and mandated for both request and response communications. Available are tools for obtaining, and Palo Alto Networks has also offered third-party support for its PAN-OS firewalls.
- Don’t rush to replace all RADIUS tools at once, as this could lead to potential mistakes. Ideally, prioritize upgrading the RADIUS servers upfront.
- Assess the public’s exposure to BlastRADIUS and diverse community infrastructure nodes?
For comprehensive guidance on best practices and protocols for system directors, refer to https://www.systemdirectors.com/guidance.

