In an amended criticism to current civil litigation, Microsoft is naming the first builders of malicious instruments designed to bypass the guardrails of generative AI companies, together with Microsoft’s Azure OpenAI Service. We’re pursuing this authorized motion now in opposition to recognized defendants to cease their conduct, to proceed to dismantle their illicit operation, and to discourage others intent on weaponizing our AI know-how.
The people named are: (1) Arian Yadegarnia aka “Fiz” of Iran, (2) Alan Krysiak aka “Drago” of United Kingdom, (3) Ricky Yuen aka “cg-dot” of Hong Kong, China, and (4) Phát Phùng Tấn aka “Asakuri” of Vietnam. These actors are on the middle of a world cybercrime community Microsoft tracks as Storm-2139. Members of Storm-2139 exploited uncovered buyer credentials scraped from public sources to unlawfully entry accounts with sure generative AI companies. They then altered the capabilities of those companies and resold entry to different malicious actors, offering detailed directions on the best way to generate dangerous and illicit content material, together with non-consensual intimate photos of celebrities and different sexually express content material.
This exercise is prohibited beneath the phrases of use for our generative AI companies and required deliberate efforts to bypass our safeguards. We aren’t naming particular celebrities to maintain their identities non-public and have excluded artificial imagery and prompts from our filings to forestall the additional circulation of dangerous content material.
Storm-2139: A worldwide community of creators, suppliers and finish customers.
In December 2024, Microsoft’s Digital Crimes Unit (DCU) filed a lawsuit within the Jap District of Virginia alleging numerous causes of motion in opposition to 10 unidentified “John Does” collaborating in actions that violate U.S. legislation and Microsoft’s Acceptable Use Coverage and Code of Conduct. By means of this preliminary submitting, we have been capable of collect extra details about the operations of the prison enterprise.
Storm-2139 is organized into three predominant classes: creators, suppliers, and customers. Creators developed the illicit instruments that enabled the abuse of AI generated companies. Suppliers then modified and provided these instruments to finish customers usually with various tiers of service and fee. Lastly, customers then used these instruments to generate violating artificial content material, usually centered round celebrities and sexual imagery.
Under is a visible illustration of Storm-2139, which shows web aliases uncovered as a part of our investigation in addition to the nations by which we imagine the related personas are positioned.
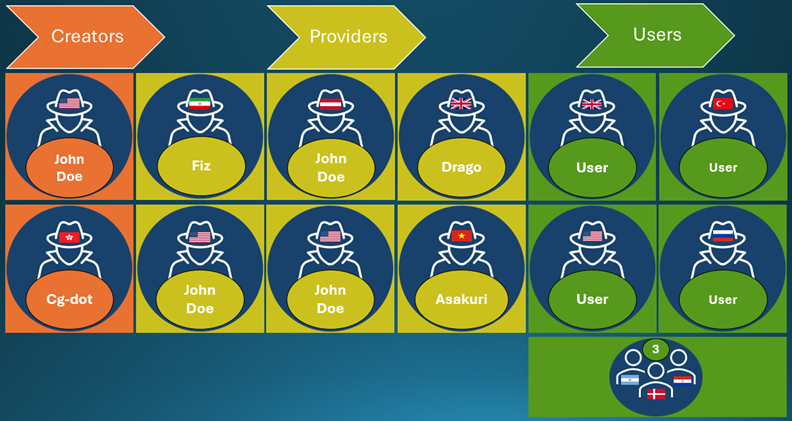
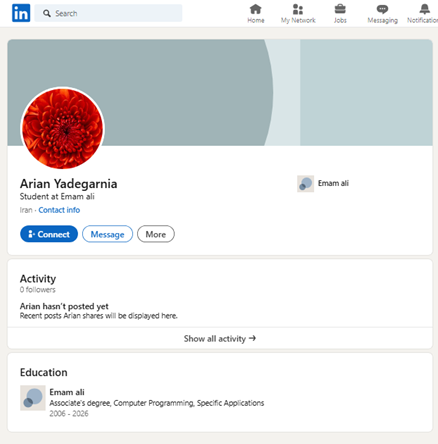
By means of its ongoing investigation, Microsoft has recognized a number of of the above-listed personas, together with, however not restricted to, the 4 named defendants. Whereas we’ve got recognized two actors positioned in the US—particularly, in Illinois and Florida—these identities stay undisclosed to keep away from interfering with potential prison investigations. Microsoft is getting ready prison referrals to United States and overseas legislation enforcement representatives.
Cybercriminals react to Microsoft’s web site seizure and courtroom submitting.
As a part of our preliminary submitting, the Courtroom issued a short lived restraining order and preliminary injunction enabling Microsoft to grab a web site instrumental to the prison operation, successfully disrupting the group’s means to operationalize their companies. The seizure of this web site and subsequent unsealing of the authorized filings in January generated a direct response from actors, in some circumstances inflicting group members to activate and level fingers at each other. We noticed chatter in regards to the lawsuit on the group’s monitored communication channels, speculating on the identities of the “John Does” and potential penalties.
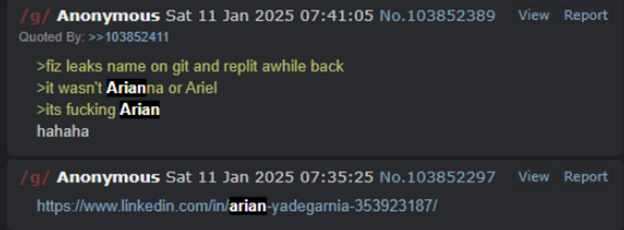
In these channels, sure members additionally “doxed” Microsoft’s counsel of file, posting their names, pDoxing may end up in real-world hurt, starting from id theft to harassment.
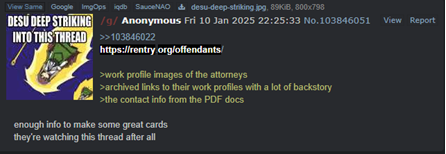
Because of this, Microsoft’s counsel acquired quite a lot of emails, together with a number of from suspected members of Storm-2139 making an attempt to forged blame on different members of the operation.
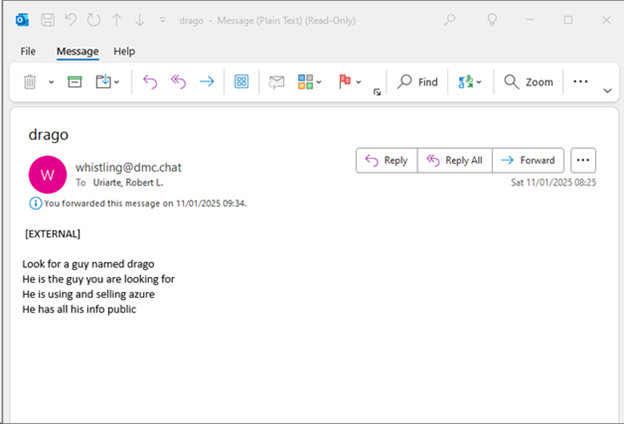
This response underscores the influence of Microsoft’s authorized actions and demonstrates how these measures can successfully disrupt a cybercriminal community by seizing infrastructure and create a robust deterrent influence amongst its members.
Persevering with our dedication to combatting the abuse of generative AI.
We take the misuse of AI very severely, recognizing the intense and lasting impacts of abusive imagery for victims. Microsoft stays dedicated to defending customers by embedding sturdy AI guardrails and safeguarding our companies from unlawful and dangerous content material. Final yr, we dedicated to persevering with to innovate on new methods to maintain customers secure by outlining a complete method to fight abusive AI-generated content material. We revealed a whitepaper with suggestions for U.S. policymakers on modernizing prison legislation to equip legislation enforcement with the instruments essential to carry unhealthy actors to justice. We additionally offered an replace on our method to intimate picture abuse, detailing the steps we take to guard our companies from such hurt, whether or not artificial or in any other case.
As we’ve mentioned earlier than, no disruption is full in at some point. Going after malicious actors requires persistence and ongoing vigilance. By unmasking these people and shining a light-weight on their malicious actions, Microsoft goals to set a precedent within the battle in opposition to AI know-how misuse.