
A newly discovered vulnerability, Blast-RADIUS, enables malicious actors to bypass authentication and compromise networks and devices through man-in-the-middle attacks leveraging MD5 collisions within the widely used RADIUS/UDP protocol.
Thousands of networked units, including switches, routers, and other routing infrastructure, rely heavily on the RADIUS (Remote Authentication Dial-In User Service) protocol for authentication and authorization in enterprise and telecommunications networks.
Among its diverse array of functions, the protocol is employed for authentication purposes in DSL and FTTH fibre-optic connections, as well as in 802.1X and Wi-Fi networks, facilitating secure mobility across 2G, 3G and 5G mobile roaming scenarios, non-public APN and VPN configurations, and demanding infrastructure networks.
Exploiting a newly discovered protocol vulnerability and a sophisticated MD5 collision attack, malicious actors can manipulate RADIUS traffic to seize control of server responses, inject arbitrary protocol attributes, and subsequently gain administrative access to affected RADIUS devices without resorting to brute-force tactics or pilfered login credentials.
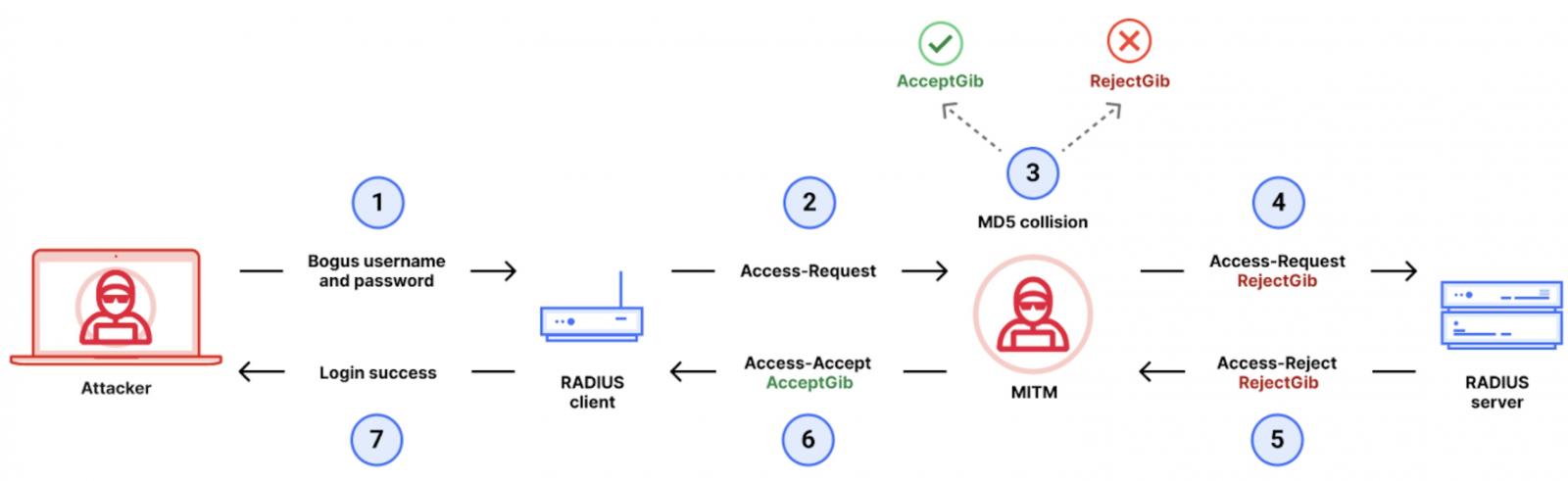
Researchers behind the Blast-RADIUS attack have discovered that this vulnerability allows a man-in-the-middle attacker to fabricate an apparently authentic response to a failed authentication attempt, rendering existing security protocols ineffective.
The lack of authentication on this system creates a vulnerability that allows an unauthorized user to gain access to critical community resources, potentially compromising sensitive information without needing to guess or forcefully crack passwords or shared keys. The attacker does not possess valid individual credentials.
An attacker exploiting this vulnerability can rapidly elevate privileges from limited access to full control over any device utilizing RADIUS-based authentication, or assume arbitrary administrator permissions.
The RADIUS protocol relies on MD5 hashed requests and responses during authentication processes, using tools as the medium. A proof-of-concept exploit developed by researchers calculates an MD5 chosen-prefix hash collision to create a forged “Entry-Accept” response, indicating a successful authentication request. This injected MD5 hash allows an attacker to execute a man-in-the-middle attack on the community’s communication system, enabling unauthorized login capabilities.
The exploit requires a duration of three to six minutes to generate the forged MD5 hash, exceeding the typical 30- to 60-second timeframes commonly implemented in RADIUS applications.
Despite this, each stage of the collision algorithm employed within the attack could be successfully parallelized and is well-suited for hardware optimization, which would enable a well-resourced attacker to implement the attack utilizing GPUs, FPGAs, or other advanced and faster hardware to achieve operating times potentially tens or hundreds of times faster.
While a demonstration of MD5 hash collisions was achieved as early as 2004, initial assessments deemed it impractical to leverage this phenomenon within the scope of the RADIUS protocol.
The attack exploits a weakness in RADIUS’s MD5-based authentication, permitting an attacker to insert a customised attribute into the protocol stream, thereby inducing a hash collision between the authenticator generated by the server and the malicious response crafted by the adversary.
As part of their online attack, the assailant seeks to calculate a chosen-prefix MD5 collision within a timeframe of mere minutes or seconds. Previous records of chosen-prefix collision attacks required hours to execute, yielding collusions incompatible with the RADIUS protocol.
Although this type of assault does not jeopardize user authentication, users may still lack the means to protect themselves from its effects. Nonetheless, distributors and system administrators who configure and manage RADIUS units are advised to monitor these settings closely.
To effectively counteract assaults on community infrastructure, administrators can implement a robust RAD-SEC solution by modifying network settings to include restricted-access administrative VLANs, thereby isolating sensitive RADIUS connections and ensuring secure communication through the utilization of TLS and/or IPsec tunneling protocols.

