Federal investigators have taken into custody and formally charged a 20-year-old American citizen. A military soldier suspected of being a cybercriminal who allegedly promoted and leaked sensitive buyer information stolen last year from multiple companies. According to an initial report by KrebsOnSecurity last month, the suspect in question is a former communications specialist with recent experience stationed in South Korea.

On his Facebook page, Cameron Wagenius shares numerous selfies.
Was apprehended near the Fort Hood Army Base in Killeen, Texas, around December 1st. Twenty-year-old individual faces indictment on two criminal charges for allegedly misappropriating sensitive mobile phone information.
The lack of specific details (PDF) fails to mention individual victims or hack examples, and refrains from sharing personal information about the defendant. During the course of a dialogue with Wagenius’ mom, a Minnesotan by birth, a brief and concise conversation was inserted.
Prior to his son’s arrest, Roen had revealed his connection to AKA. A notorious Canadian cybercriminal, known as “,” was arrested for allegedly stealing sensitive information from and extorting numerous major corporations that relied heavily on the cloud-based storage service.
According to a KrebsOnSecurity interview, Judische revealed limited enthusiasm for marketing the information he stole from Snowflake prospects and telecom suppliers, stating his preference for outsourcing this activity to entities like Kiberphant0m. In the meantime, Kiberphant0m claimed in posts on Telegram that he was chargeable for hacking into at the least 15 telecommunications corporations, together with AT&T and Verizon.
On November 26, Brian Krebs’ KrebsOnSecurity website followed a trail of breadcrumbs left behind by Kiberphantom, revealing him to be a US-based cybercriminal. Soldier serving a tour of duty in South Korea.
Ms. For nearly two years, Roen had been stationed at a US military base in South Korea, where Cameron spent her time laboring over radio alerts and community communications, occasionally returning to America for brief periods. Although she acknowledged that Cameron was always proficient with computer systems, she surprisingly failed to consider the possibility that his expertise might have been exploited for illegal purposes.
“I had no idea he was into hacking,” Roen said. “It came as a profound shock when we uncovered these revelations.”
Ms. Cameron enlisted in the military at the earliest possible opportunity, echoing his elder sibling’s path.
“He and his younger brother, who were around six and seven at the time, would often request Meals Ready to Eat (MREs) from various countries,” she remembered. They had a constant need to remain within the military at all times. I’m uncertain about where mistakes occurred.
Instantly after information broke of Moucka’s arrest, Kiberphant0m posted on the hacker neighborhood what they claimed have been the AT&T name logs for and for .
“As a last resort,” Kiberphant0m warned, “if we’re not contacted by @ATNT, all presidential authority call logs will be released.” Can’t you anticipate that we wouldn’t have a plan in place when an arrest occurs? Suppose once more.”
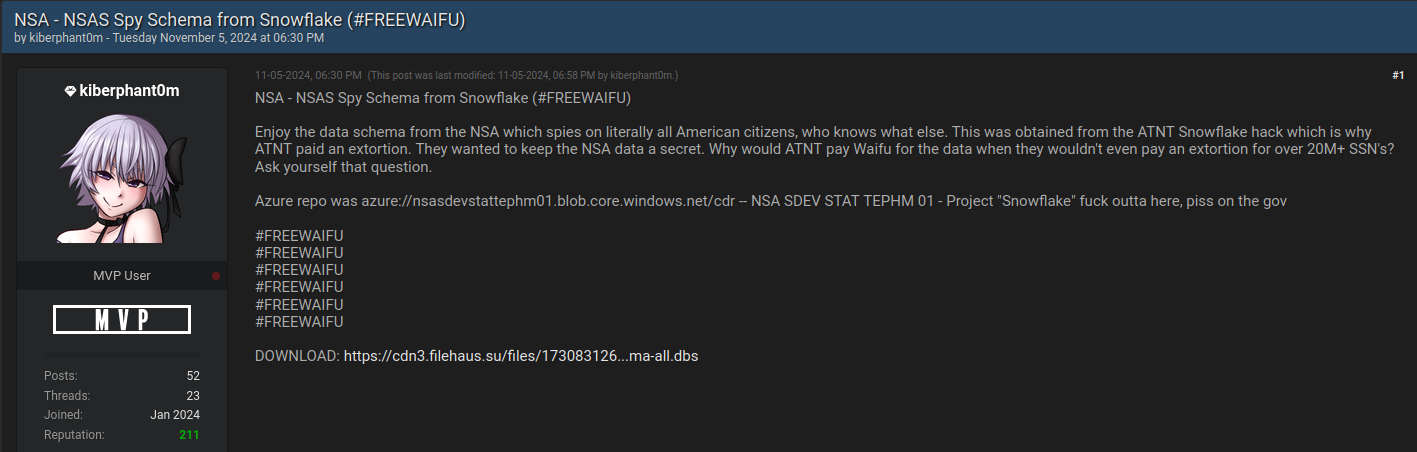
Kiberphant0m posting what he claimed was a “knowledge schema” stolen from the NSA by way of AT&T.
On the same day, Kiberphant0m allegedly shared their supposed “knowledge schema” from the dot.
On Nov. 5, An anonymous source claiming to be Kiberphant0m shared allegedly stolen name logs associated with Verizon’s push-to-talk (PTT) users, predominantly based in the United States. Authorities, companies, and emergency first responders. On Nov. A professional criminal forum advertises a SIM-swapping service targeting Verizon Public Transitification (PTT) subscribers, sparking concerns about the potential for fraud and security breaches. In a SIM-swap scam, perpetrators exploit compromised login credentials of cell phone company employees to hijack the victim’s phone number, redirecting incoming calls and text messages to a device under their control.
The Facebook profile picture on Wagenius’ account had been removed within a few hours of my November posting. What’s the best way to get this 26-year-old figuring out whether Kibernetikofant0m is a viable option for U.S.? Military soldier. Notwithstanding the majority of his distinct profile pictures persist, alongside several showcasing Wagenius clad in uniform, grasping assorted military-issued weaponry.
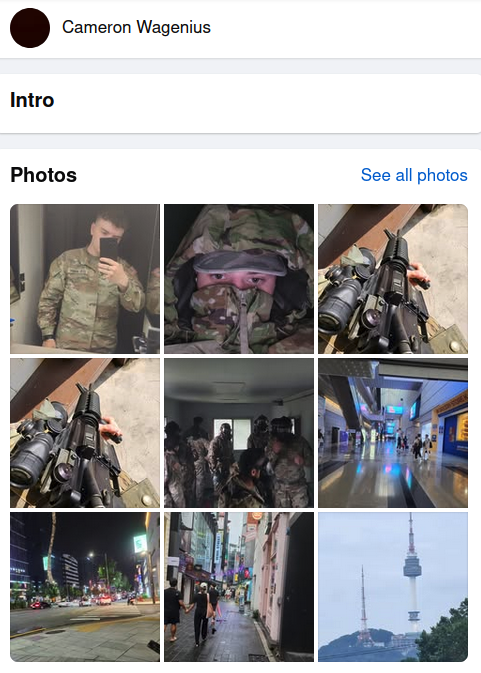
Cameron Wagenius’s Facebook webpage showcases a variety of profile pictures.
The November article reported on Kiberphant0m’s self-proclaimed exploits via personal Telegram exchanges, in which he allegedly controlled a substantial botnet employed for coordinated distributed denial-of-service (DDoS) attacks, targeting websites, clients, and networks with the aim of rendering them inaccessible. In 2023, Kiberphantom offered distant entry credentials to serious U.S. protection contractor.
As the chief analytics officer at a leading New York-based cybersecurity agency, he played a pivotal role in tracking down Kiberphant0m’s authentic digital identity. Nixon was one of several safety researchers who faced intimidation and credible threats of physical violence at the hands of Judische and his cohorts.
President Nixon expressed strong disapproval for anonymously extorting high-ranking officials, describing it as a vile notion. He emphasized that such behavior pales in comparison to the egregious offense of harassing those who dedicate their efforts to exposing cyber criminals and restoring anonymity. The official highlighted the progress of an inquiry into KibernetiK exhibits, noting that law enforcement agencies have become increasingly adept at pursuing cybercriminals, with a notable focus on apprehending those operating within American borders?
As she recounted, between a specific point in time and the discovery of their colleague’s operational security lapse on November 10th, and his final Telegram exercise on December 6th, law enforcement set a new record for the fastest turnaround time in an American federal cyber case that I’ve encountered throughout my career.
President Nixon cautioned that he was aware of numerous rival Kiberphantoms operating in secret, thinking they could evade detection and punishment; however, he warned them that their anonymity would not last forever.
According to Nixon, he acknowledges that younger people involved in cybercrime would likely familiarize themselves with the published articles. I implore you to reconsider your approach and seek legal counsel rather than indulging in frivolous behavior. Regulation enforcement authorities intend to imprison each and every one of you for an extended period.
The indictment against Wagenius was filed in Texas, but the case has since been transferred to federal jurisdiction in the U.S. Western District of Washington, United States District Court for the Western District of Washington, located in Seattle.

