Cybercriminals are aggressively marketing hundreds of thousands of compromised credentials stolen using a cracked version of a powerful industrial network application vulnerability scanner, according to recent research. Hackers are peddling a compromised software application, repackaging it as a cloud-based attack tool, and at least two separate entities have fallen victim to this tactic – one of them linked to an information technology firm headquartered in Turkey, according to KrebsOnSecurity investigations.

Araneida Scanner.
According to cyber menace analysts, recent acquisition of reviews from a collaborating group revealed an aggressive scanning effort against their website using an IP address previously linked to a campaign by Avaddon, a notorious Russia-based hacking group.
Upon closer examination, they discovered that the agreement included an HTML title of “undefined” and, upon investigating this text string, they were able to uncover numerous unique addresses hosting the same service by searching for it.
As it became evident, the shady operation, masquerading as Araneida, exploited a compromised version of Acunetix, offering customers a cloud-based platform to facilitate malicious activities such as reconnaissance, data scraping, and vulnerability identification on unsuspecting targets.
Silent Push also found that Araneida bundles its services with a robust proxy provider, allowing buyers’ searches to appear as if they originate from randomly selected websites within a large pool of available traffic relays.
Texas-based software safety vendor Acunetix has corroborated Silent Push’s discovery, revealing that someone has found a way to bypass the free trial model of their software, allowing it to run without a legitimate license key.
“As our ongoing game of cat and mouse with these adversaries has unfolded over several months,” said the chief information security officer at Invicti, “we’ve developed a keen understanding of their tactics.”
Araneida, a notorious malware, is reportedly being peddled by an anonymous individual on several underground cybercrime forums. The Telegram channel, boasting nearly 500 subscribers, openly documents the potential misuse of the service’s instrument, highlighting its capacity for harmful exploitation.
In a “Fun Facts” update posted to the channel in late September, Araneida shared their impressive track record, revealing that their service successfully took over more than 30,000 websites within just six months. Notably, one satisfied customer used this capability to treat themselves to a Porsche, leveraging the valuable credit card information (“dumps”) they acquired through the service.
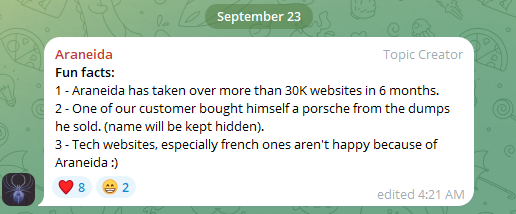
Araneida Scanner’s notorious Telegram channel touting its tools as being exploited by nefarious individuals to facilitate malicious activities.
According to a senior threat researcher at Silent Push, “Criminals are literally flaunting their exploits and boasting about the financial gains they’ve made from these crimes in their neighborhoods.” “They’re also touting bulk knowledge and dumps that appear to have originated from the tool itself or stemmed from vulnerabilities uncovered through its use.”
Researchers at Silent Push uncovered a previously unknown instance of Acunetix’s cracked model, which was found powering at least 20 instances of a similar cloud-based vulnerability testing service catering specifically to Mandarin-speaking users; intriguingly, they were unable to locate any apparent sales threads related to this phenomenon on the dark web.
Rumors have been circulating about the alleged use of an allegedly compromised model of Acunetix by malicious actors, which emerged following an investigation by cybersecurity experts.
According to a PDF issued by the Health and Human Services department, Acunetix, allegedly a compromised version, is one of several tools employed by APT31, a notorious Chinese state-sponsored hacking collective frequently targeting healthcare organizations.
THE TURKISH CONNECTION
Silent Push notes that the website where Araneida is being sold first launched online in February 2023, marking its debut as a digital platform. Although an evaluation of this Araneida nickname on cybercrime boards indicates that they have been active within the legal hacking scene since at least 2018.
A search of the Menace Intelligence Platform reveals that an individual identified as Araneida advertised the scanner on at least two cybercrime forums since 2022. Araneida informed fellow Breached members in 2022 that they might be contacted on Discord using the handle “”
According to Intel 471, this identical Discord account was promoted in 2019 by an individual on a cybercrime discussion forum who operated under the pseudonyms “ori0n” and “”. The poster, also known as “ori0n”, discussed his availability on Telegram via the username “.
What’s new with Araneida Scanner this February? The year 2023 was marked by a lively discussion on the popular online forum Cracked. Picture: Ke-la.com.
According to online chatter, a user on the Nulled cybercrime forum is marketing website development services, citing Araneida.co as an initiative. The Sirorny Telegram identification was also mentioned as a point of contact for a current customer. The consumer, who has had a relationship with someone since August 2018, still maintains that connection.
In January 2020, Exorn touted an online platform dubbed ” “, which they touted as a solution for streamlining web-based vulnerability scanning. A passive DNS lookup in this region indicates that email traffic was previously routed through a domain ending in dot.
A cybersecurity organization that monitors data from knowledge breaches discovered that an email address was used to register an account at a specific platform in July 2024 under the pseudonym “Anonymous.” The same email was also found to have been registered on the website netguard[.]codes in 2021 using the password “123456” [full disclosure: the cybersecurity organization is currently an advertiser on KrebsOnSecurity].
Upon identifying a password breach involving ‘ceza2003’, a thorough examination of Constella reveals approximately 12 compromised email accounts, nearly all sharing common denominators like “title” and “.”. An investigation uncovered that the email address altugsara321@gmail.com was employed to establish an account on a malicious online platform, known as “cybercrime neighborhood,” under the pseudonym “” from an internet protocol address located in Istanbul.
In accordance with DomainTools, altugsara321@gmail.com registered the domain name in 2020. The platform showcased the talents of an 18-year-old individual from Ankara, Turkey, as far back as 2021 through its online presence.
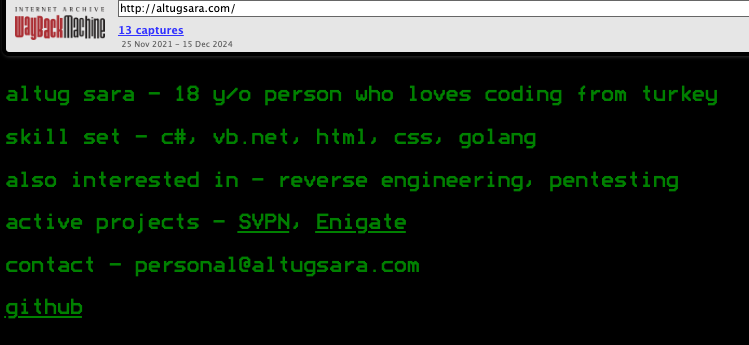
Archived at Archive.org, a snapshot from 2021 reveals what altugsara.com considered significant then.
Identifies this identical area listed within the “Contact Information” section of his profile as an individual from Ankara, who claims to have spent the past two years working as a senior software development specialist at a prominent Turkish IT firm named.
Neither Altug Sara nor Bilitor Yazilim responded to requests for comment.
The Invicti website claims to have offices in Ankara, yet the company’s CEO surprisingly fails to mention any employees holding both titles.
“We maintain a modest presence in Ankara, but to date, our only tie to this individual is their shared location.”
According to Silent Push researchers, despite Araneida employing an ostensibly boundless supply of proxies to conceal the actual location of its users, it is a relatively “noisy” scanner that can initiate a significant volume of requests to various API endpoints and randomly target URLs linked to distinct content management systems, thereby rendering the masking effort ineffective.
Cybersecurity researchers at Silent Push have discovered that the cracked version of Acunetix being resold to cybercriminals is reviving legacy SSL certificates on active management panels, providing a stable foothold for identifying some of this infrastructure, particularly from Chinese-speaking threat actors.
Additional studying: .

