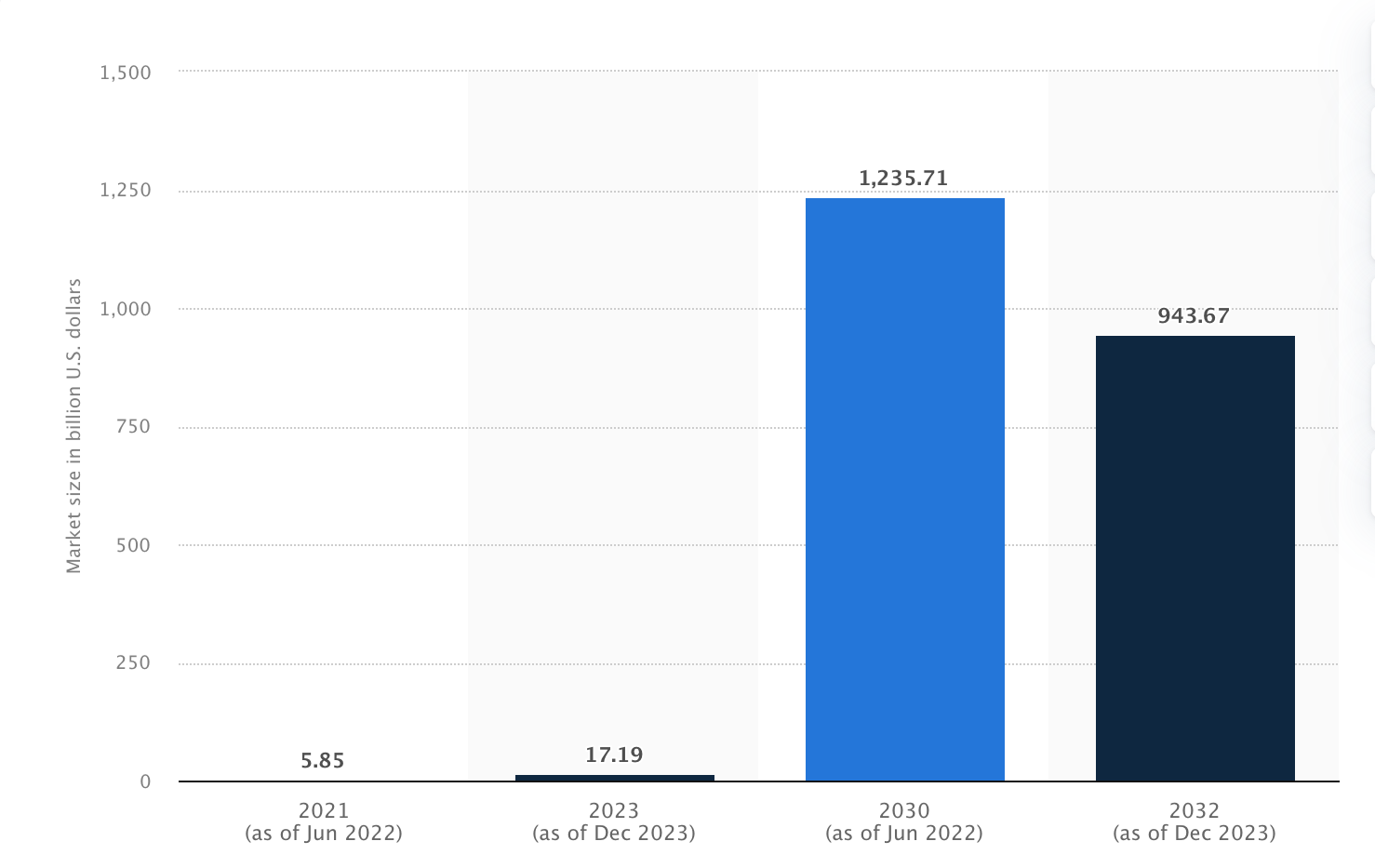
By 2032, the value of blockchain technology is forecasted to reach $1 trillion, according to a report focused on the application of blockchain solutions across various business sectors.
By 2030, the global blockchain in cloud market size is forecasted to reach approximately $15.9 billion.
The significance of decentralized technologies has recently been elevated due to the extensive adoption across various sectors, including gaming, real estate, logistics, healthcare, and finance.
The surge in popularity may be attributed to the fact that knowledge is typically regarded as exceptionally secure. However what stands behind it?
A fundamental component in ensuring blockchain security is a robust hash function that meets the encryption requirements necessary to safeguard data effectively.
What Is a Hash? Blockchain’s trifecta of definition, clarification, and function has become a cornerstone of its fundamental architecture. The concept of blockchain originated from the early days of cryptocurrency, specifically Bitcoin. Initially, blockchain was described as an immutable distributed ledger technology that enabled peer-to-peer transactions without intermediaries.
However, as the industry evolved, it became crucial to clarify the true nature of blockchain beyond just being a decentralized record-keeper. In reality, blockchain is a more complex system comprising three primary functions: data storage, transaction processing, and consensus mechanism.
Data Storage refers to the ability of blockchain to store and manage data in an immutable manner. This feature ensures that all transactions are recorded chronologically, allowing users to track the history of assets or information.
Transaction Processing encompasses the entire process of creating, verifying, and recording transactions on a blockchain network. This includes smart contracts that automate specific actions based on predefined conditions.
Consensus Mechanism is the mechanism by which nodes on a blockchain network agree on the state of the ledger. This ensures that all participants are in sync, thereby maintaining the integrity of the entire system.
In conclusion, understanding the definition, clarification, and function of blockchain is vital for its widespread adoption.
Blockchain hashing is the process of converting any type of digital information – files or transactions alike – into a fixed, unique sequence of characters.

The ensuing thread is dubbed the hash value, a solitary embodiment of the entire dataset regardless of its magnitude. Regardless of whether you’re processing a brief piece of text or an extensively detailed transaction document, the output of hashing will consistently be of uniform size.
The hash value is typically referred to as a “digital fingerprint.” A distinctive feature of this fingerprint is its sensitivity: even a single modification to the original data results in a significantly altered hash.
The most widely used hashing algorithm in blockchain technology is SHA-256 (Secure Hash Algorithm 256-bit). Because data integrity is crucial, metadata becomes the fundamental building block for anyone seeking to ensure wholeness and safeness in their information.
While various hash algorithms exist, they won’t be limited to MD5 and SHA-3; nonetheless, each has distinct requirements for security, meaning not all are sufficiently robust for use in blockchain applications.
Some Primary Details About Hashes
A crucial role in secure blockchain technology is played by hashes, which derive their significant influence from numerous key properties:
Fastened-Size Output
Despite the scale of the input data, the hashing technique consistently produces a fixed-size output. SHA-256 consistently generates a 256-bit hash value regardless of the input size, whether it’s a short phrase or a large document.
Predictable
The same input will always yield the same hash. Because of its inherent uniqueness, blockchain applications are able to verify data through the process of hash matching. Even a slight change in one determining factor can result in an entirely unique hash.
Collision-Resistant
No two distinct and unrelated areas of knowledge should ever produce the same digital fingerprint. Each piece of information possesses a distinct digital signature, ensuring a negligible likelihood of collision – a rare occurrence where two identical hash values coexist.
Non-Reversible
As a fundamental concept in cryptography, hashing is a one-way operation due to its inherent difficulty in generating a hash from data, but not feasible to reverse-engineer the original information from the resulting hash alone.
How Blockchain Hashing Fortifies Safety
Blockchain technology employs hashing algorithms to generate a unique digital identifier for each piece of data, ensuring the seamless preservation of information integrity.

Even modifying a single letter within this data drastically alters the final result. When employing this approach, it’s relatively simple to detect attempts to manipulate data—simply check whether the hashed value corresponds to the expected outcome.
Hashing instils confidence in a blockchain system by making the entire process verifiable through its unique digital fingerprint. In this era of digital transparency, there’s little need for governments to scrutinize every transaction, as individuals can independently verify the accuracy of the data.
On the blockchain, hashing plays a crucial role in the Proof of Work mechanism, initially deployed on Bitcoin and subsequently adopted by many other networks.
In proof-of-work (PoW) networks, miners are challenged to find a specific hash value that satisfies predetermined criteria.
The computational effort required to rectify such problems is staggering, rendering tampering with a blockchain extremely challenging due to the need to reprocess every block and recalculate the entire network’s state for anyone seeking to do so.
What Happens When Hash Functions Meet Blockchain Technology
A transaction of two Bitcoins was sent to another individual. Particulars of numerous transactions are recorded, including details on senders, receivers, and the quantities transferred between them.
This block also incorporates additional details, including a contemporaneous document and a reference back to the preceding block.
The subsequent block in the chain is processed through a cryptographic hash function, such as SHA-256, resulting in a unique digital fingerprint, or hash value.
The blockchain’s core mechanism operates by linking each block to its predecessor through a unique digital fingerprint, known as a hash, thereby establishing a chronological record. Here’s the improved text: That is; Block 1 possesses its own unique hash, whereas Block 2 not only contains its own hash but also references the hash of Block 1.
Blocks are arranged in a hierarchical structure, with each block accommodating the hash of its preceding block, extending backwards through Block 2’s hash and further still. Blocks are linked together in a secure manner, earning the label “blockchain”.
If anyone attempts to modify the details in Block 1 – such as changing the amount involved in a transaction – the unique digital fingerprint, or hash, associated with that block would need to be recalculated and updated. Since Block 2 relies on Block 1’s hash value, it will no longer align, thereby compromising the integrity of the entire blockchain.
To verify the validity of the intervention, the attacker would need to recomputed every subsequent block from Block 1 onwards, an impractically immense computational undertaking.
Despite its touted security, blockchain hashing has several limitations and counterarguments. For instance?
While hashing techniques are remarkably efficient, they do not come without their inherent limitations? While rare, collisions may occur between distinct data inputs producing identical hashes due to limitations in modern hash functions like SHA-256, which could potentially lead to collision assaults.

Theoretically, it’s nonetheless a threat. Cryptographic consultants labor tirelessly to enhance the security of hashing algorithms, striving to prevent collisions with utmost diligence.
Will quantum computing ultimately pose a significant threat? If the most brilliant researchers are correct, these cutting-edge computers could potentially compromise current hash functions by solving their underlying mathematical problems, thereby enabling efficient reversal of hashes or finding identical data collisions.
Researchers are actively developing quantum-resistant algorithms to counter emerging threats.
Cryptographic proof-of-work mechanisms heavily depend on efficient hashing algorithms in the mining process, where competing miners strive to solve intricate computational challenges utilizing hash-based cryptographic primitives.
As a direct result, the immense energy requirements of these systems are increasingly scrutinized; hence, the environmental impact of Bitcoin’s blockchain, in particular, has become a pressing concern.

