
Microsoft’s 365 Admin Portal has been exploited to send sextortion emails, which appear authentic and evade electronic mail security measures.
Sextortion attempts masquerade as dire warnings that hackers have breached the security of your personal devices, pilfering compromising content featuring intimate moments or explicit performances. The scammers subsequently extort $500 to $5,000 from you, threatening to disseminate compromising photographs to your family and friends unless payment is made.
Despite seemingly insurmountable odds, these cons proved surprisingly effective when initially implemented. Up to this day, BleepingComputer remains committed to responding promptly to messages from individuals who reach out for assistance following our initial contact with them.
Since then, various variants of extortion email scams have emerged, including those that feign to possess or embody threats aimed at frightening you into paying the extortionist in Bitcoin.
Notwithstanding, electronic mail security systems have proven effective in identifying fraudulent emails and typically isolate them in the spam folder.
Microsoft 365 administrators beware: scammers are exploiting vulnerabilities in the admin portal to launch devastating attacks. A new wave of phishing emails and social engineering tactics targets unsuspecting admins, tricking them into divulging sensitive information or installing malware. Don’t fall prey – stay vigilant and update your knowledge on the latest best practices for securing the Microsoft 365 Admin Portal.
In recent days, recipients on Outlook, Yahoo, and Gmail have been targeted by a wave of sextortion emails, cleverly disguised as legitimate messages that evade spam filters and directly land in their inboxes via Microsoft 365’s Message Middle.
I recently received a fraudulent email attempting to extort money from me. While some messages are frequently relegated to junk or spam folders, this particular email managed to bypass the filters and reach its intended recipient, courtesy of being sent by Microsoft 365’s Message Center.
What theories can they have proposed to achieve that?
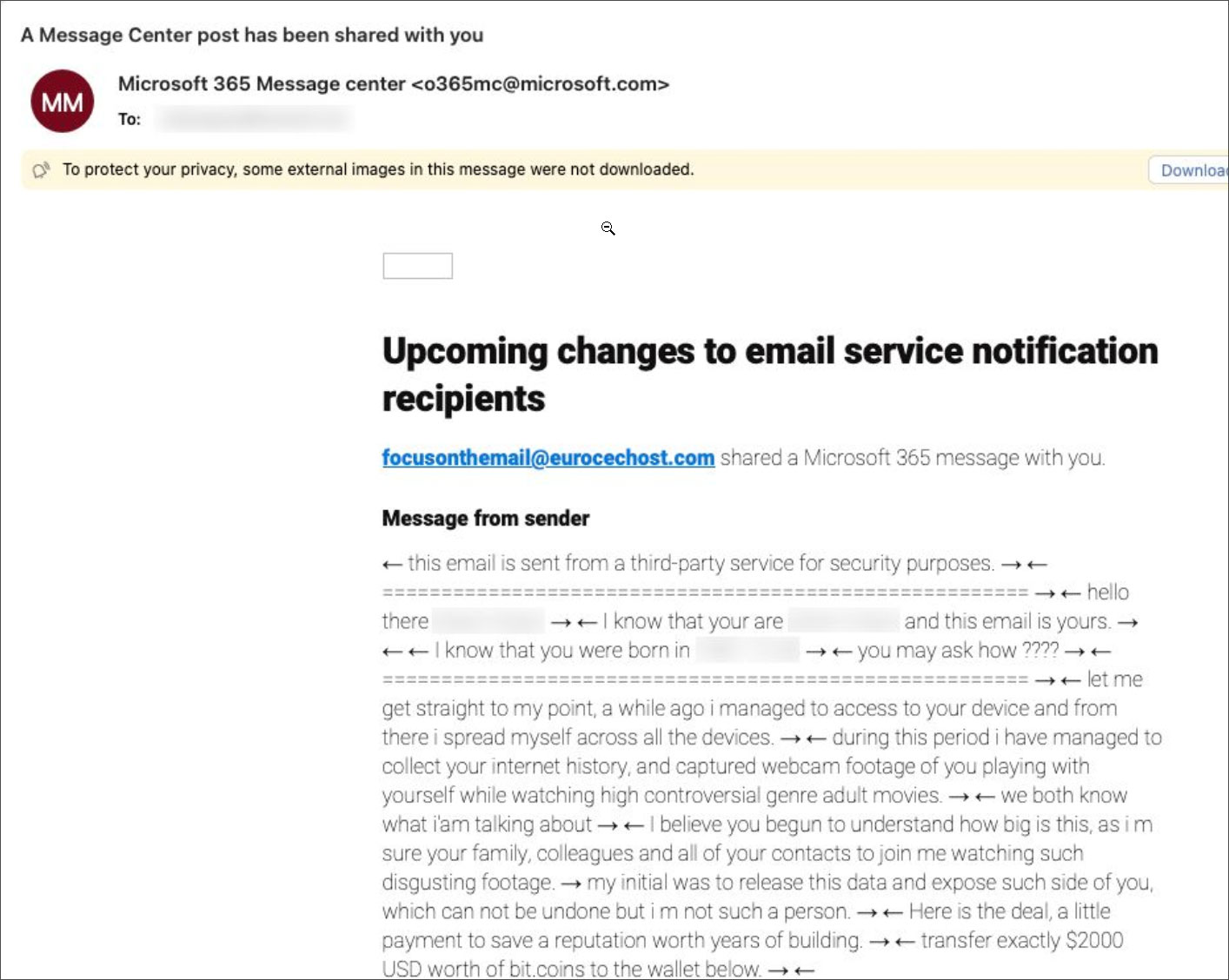
The sextortion emails originate from “o365mc@microsoft.com”, initially appearing like a phishing attempt but actually utilized by Microsoft 365’s Messaging Center to deliver messages and notifications.
Unfamiliar with the Microsoft 365 Admin Portal’s Message Center, users are presented with a section that aggregates vital communications from Microsoft regarding service advisories, newly introduced features, and impending changes.
Viewing an advisory offers the opportunity to share it with others via a convenient “Share” hyperlink, easily accessible below.
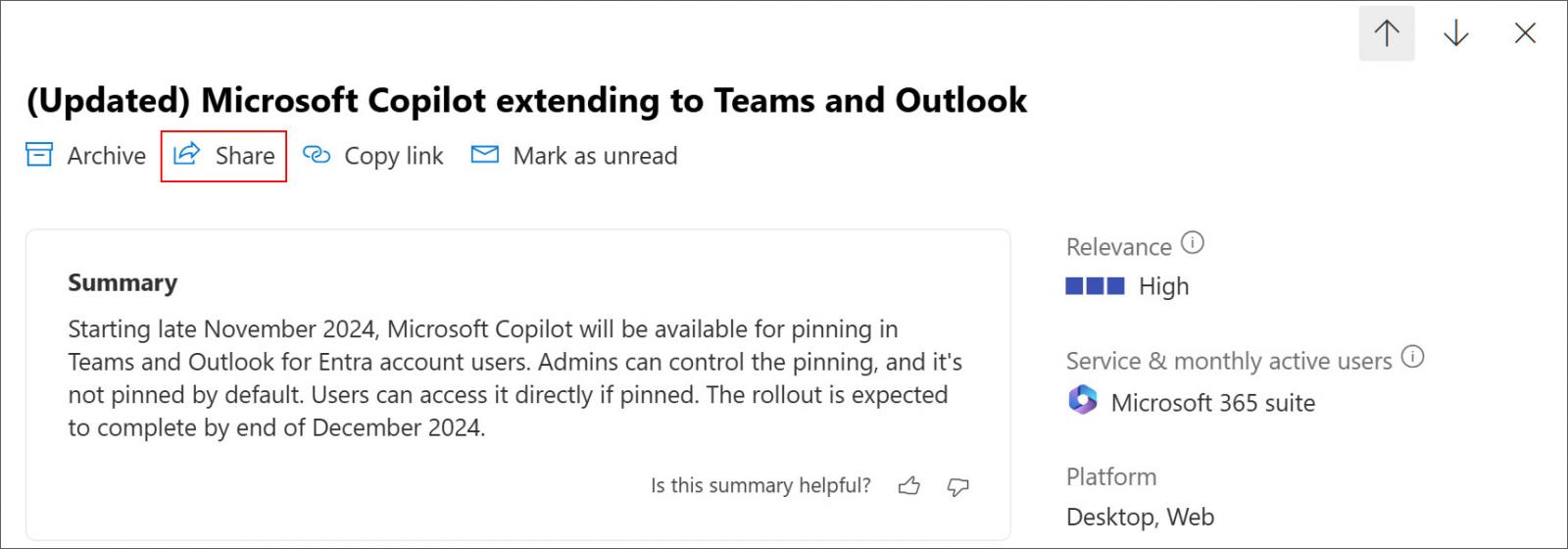
When clicking the Share button, a dialog appears prompting users to input up to two email addresses where the notification should be sent, whether these are internal or external to their organization.
The display screen also features an optional “Private Message” field that can be included in the emailed advisory if desired.
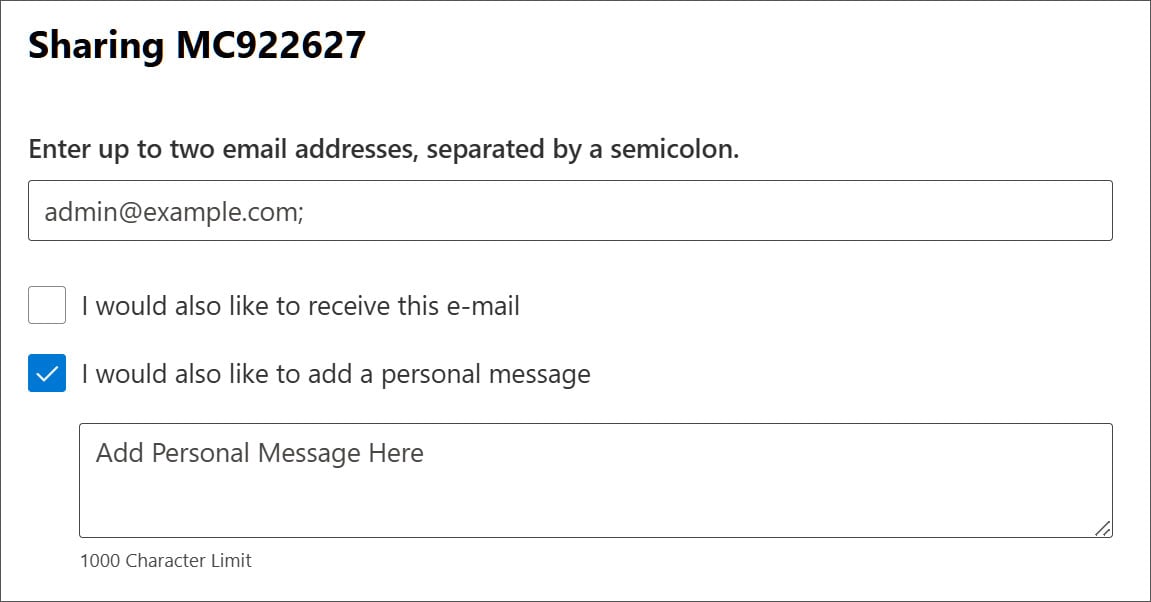
Cybercriminals are exploiting the Private Message feature to disseminate sextortion scams, posing a significant threat to online users. Despite its limitations, the private messaging feature still accommodates up to 1,000 characters before truncation occurs, as dictated by the user interface constraints.
It’s astonishing that the spam messages, exceeding the 1,000-character limit, managed to evade detection and reach my inbox.
The reply is easy. They only open up the browser’s dev instruments and alter the utmost size area of the <textarea> tag to an arbitrary variety of their alternative.
This revised version allows users to submit their entire sextortion message without truncation in the “Private Message” field.
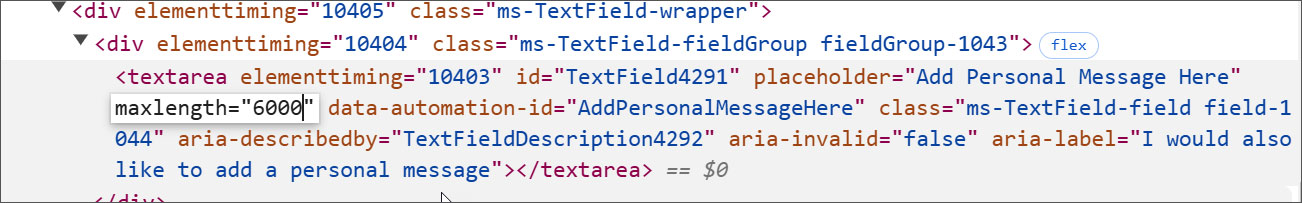
Since Microsoft does not perform server-side checks on character sizes, your full extortion message has been sent along with the advisory as intended.
Scammers likely employ automated processes to generate “Share” requests, allowing them to bypass standard server-side checks on private message length.
Microsoft has reportedly been informed of the scams by BleepingComputer, with a spokesperson confirming that the company is actively investigating the fraudulent activity.
Thank you for sharing your thoughts with us; we appreciate your input. Microsoft emphasizes the importance of prioritizing both safety and privacy in its interactions with customers, stating: “We take safety and privacy extremely seriously.”
“We’re thoroughly examining these claims and are prepared to take swift action to safeguard the well-being of our stakeholders.”
Although Microsoft has not implemented server-side measures to block messages exceeding 1,000 characters, BleepingComputer’s analysis corroborates this fact.
While this system may have enabled sextortion emails to evade initial spam checks, it’s essential for recipients to recognize these messages as nothing more than elaborate scams, prompting them to promptly delete the unwanted communications.
Fortunately, sextortion scams have become so prevalent over the past six years that nearly everyone is aware of their illegitimacy and swiftly deletes most of these emails.
For those unfamiliar with this phenomenon, unsolicited emails of this nature can be unsettling and even frightening.
It is imperative to emphasize that these emails are fraudulent, presenting misleading information, and you should not engage with any links or send funds to the specified cryptocurrency addresses.

