Cybercrime
While it’s unlikely you’ll completely prevent your personal data from being compromised, you can still take measures to secure yourself against criminal exploitation.

Why did nearly half of Europe’s lawmakers and two-thirds of UK politicians inadvertently reveal their personal information? Many unsuspecting individuals have registered for online services using their official email addresses, unwittingly exposing sensitive personal information to potential cyber threats. With their data compromised, they would have been left defenseless against the malicious actions of cybercriminals who exploited a breach in a third-party supplier’s systems, potentially sharing or selling the stolen information to other nefarious actors operating on the dark web.
Unbeknownst to many, this phenomenon transcends the realm of public figures and permeates online discourse, allowing anyone’s personal data to fall prey to the darknet’s insidious grasp. Occasionally, even the most meticulous individuals may still experience this phenomenon. And often, it does occur. It’s essential to cultivate a heightened sense of awareness about the matters that concern you most, as this vigilance can ultimately lead to greater rewards.
The darkish net is prospering
While counterintuitive at first glance, the darknet is not inherently illegal and does not exclusively house cybercriminals, debunking popular misconceptions about its nature.
This refers to components of the internet that are not indexed by traditional search engines, such as areas accessible only when using the Tor browser.
Despite this, it is undeniable that today’s cybercrime economy thrives on a robust darknet, where numerous dedicated forums and marketplaces are frequented by cybercriminals in droves, largely evading law enforcement detection. (Nefarious actions have increasingly occurred in recent times.)
Within the shadows of the digital world, notorious darknet platforms provide a haven for malicious actors to freely buy, sell, and trade in stolen data, illicit hacking tools, and DIY tutorials on nefarious activities, all while evading accountability. Despite intermittent efforts by law enforcement to crack down on illicit activities, online platforms continue to evolve and mutate, with fresh sites emerging to capitalize on the opportunities created by the removal of their predecessors.
Researchers from Proton and Constella Intelligence went searching, only to find that an astonishing 40% of British, European, and French parliamentarians’ email addresses were publicly exposed on the dark web. Almost 44% of potential email accounts have been utilized, leaving roughly 1,280 unused. Furthermore, a staggering 700 email accounts were found to have associated passwords stored in unencrypted text, only to be publicly exposed on the dark web. Uncovering sensitive data, combined with dates of birth, residential addresses, and social media handles, yields a wealth of identifiable information vulnerable to exploitation in subsequent phishing attacks and identity fraud schemes.
Your personal data may inadvertently end up on the dark web through various means, such as:
Numerous methods exist whereby your personal information may inadvertently wind up on a darknet forum or website. While some outcomes may stem from neglect, many others remain unexplained. Take into account the next:
- Your personal data was compromised after collaborating with the company, whose own databases had previously stored your confidential details. According to data within the United States, more than 3,200 reported incidents at various organizations have resulted in the unauthorized disclosure of sensitive information affecting over 353 million individuals.
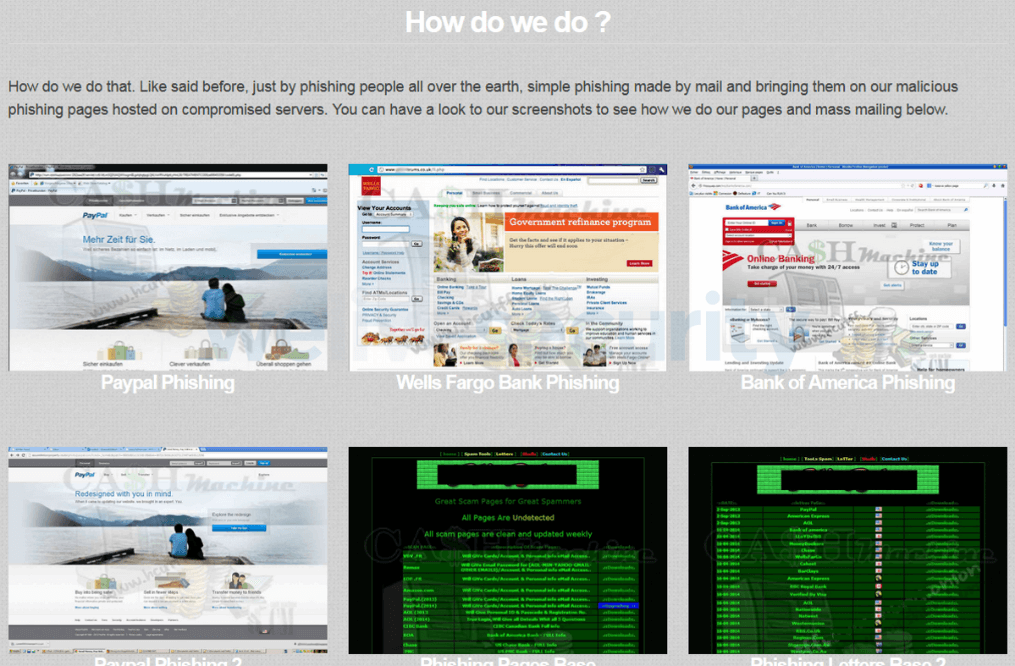
- One of your online accounts – whether an email address, financial institution login, or social media profile – has likely been breached as the result of a sophisticated phishing attack. A seemingly authentic electronic communication, such as an email, direct message, text message, or WhatsApp transmission, may incorporate a hyperlink that could deceive or trick you into accessing a spoofed login webpage for Microsoft 365.
- A web-based account has been successfully breached via a relentless brute-force attack. Hackers exploit vulnerabilities in online systems through tactics like credential stuffing, dictionary assaults, and other techniques to gain unauthorized access across various websites. As soon as users log into their accounts, cybercriminals exploit the opportunity to pilfer additional private information stored within, subsequently leveraging it for promotional or nefarious purposes.
- Your private information may have been compromised by stealthy malware concealed within seemingly innocuous applications or files, just like , deceitful email attachments, treacherous ads, and tainted websites.
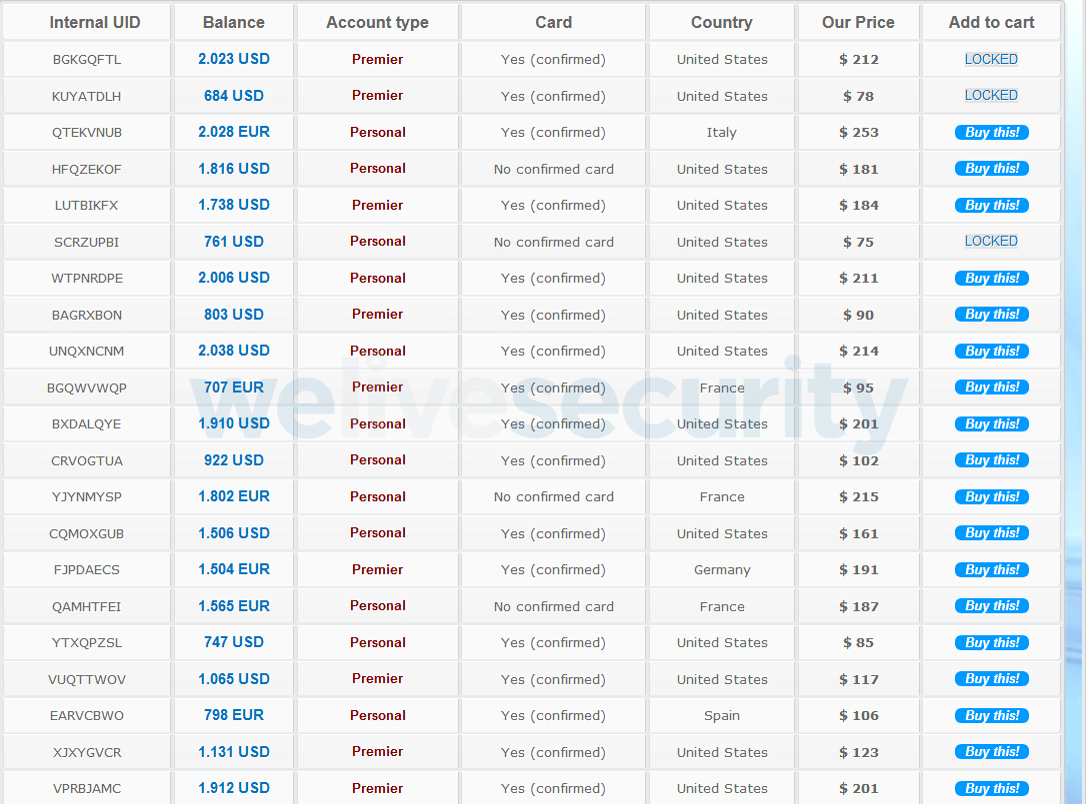
 Despite the questionable ethics, individuals willing to compromise their privacy are prepared to pay for this sensitive information, only to see it potentially resold or compromised further once posted on a darknet criminal platform for the highest bidder. Utilizing the provided data, authorized individuals may employ logins and personally identifiable information to:
Despite the questionable ethics, individuals willing to compromise their privacy are prepared to pay for this sensitive information, only to see it potentially resold or compromised further once posted on a darknet criminal platform for the highest bidder. Utilizing the provided data, authorized individuals may employ logins and personally identifiable information to:
- Utilize compromised access to infiltrate customers’ financial institution accounts and extract sensitive information, including financial details and card particulars.
- Your sensitive information has been compromised, but don’t worry – we’re here to help! We’ve already taken steps to secure your personal data, and we want to make sure everything is in order.
Here’s what we know so far:
* Your name: John Doe
* Email address: johndoe@email.comPlease confirm the following details to ensure your account remains safe:
* Last four digits of your social security number: XXXX
* Password: [insert password hint]Once you’ve verified this information, we’ll guide you through the process of changing your password and adding extra layers of security.
- Hack into your email or social media accounts to bombard acquaintances with unwanted spam messages and wreak havoc on ebook connections by exploiting them with insidious links.
- Perpetuating identity fraud, for instance, involves opening new lines of credit in someone else’s name, fabricating phony tax returns to secure a refund, or illicitly procuring medical services under another person’s identity.
How do I test?
Should your identity protection service or dark web monitoring solution be configured to alert you about any Personally Identifiable Information (PII) or other sensitive data discovered on the dark web? Tech companies, along with security software and operating systems, may also alert you when a stored password has been compromised or recommend updating it to a more secure, less vulnerable alternative.
Vitally, monitoring the dark web is often also an integral component of a comprehensive online security strategy, whose products undeniably offer numerous benefits and serve as a vital building block for ensuring personal digital protection.
Alternatively, you can leverage websites like PubMed, which offers comprehensive databases that can be securely accessed.
If your personal information has been stolen, take immediate action to minimize potential harm.
If the worst occurs and, like a British politician, you discover that your sensitive information has been compromised and is being traded on the dark web, you must act swiftly to mitigate the damage. Within a brief window of opportunity, consider taking swift and decisive actions akin to:
- Immediately update all compromised login credentials to cryptographically strong, one-of-a-kind combinations.
- Can you really trust your browser’s password management features?
Instead, consider using a dedicated password manager like LastPass, Dashlane, or 1Password. These tools can securely store and generate complex passwords, making it easy to recall them whenever you need to log in to a website or app.
Not only do they offer robust security features, such as encryption and two-factor authentication, but they also allow you to share access with trusted individuals, such as family members or colleagues, should the need arise.
By centralizing your password management, you’ll reduce the likelihood of password reuse, minimize the risk of data breaches, and enjoy greater peace of mind knowing that your sensitive information is well-protected.
- Implement two-factor authentication (2FA) on all accounts that offer this security feature.
- Inform relevant agencies (law enforcement, social media platforms, etc.)
- Ensure that all computer systems and devices are equipped with robust security software solutions provided by reputable vendors.
- Suspend all financial institution transactions and request fresh card replacements. Closely scrutinize all transactions to identify any unusual buying patterns.
- Vigilantly monitor variations in account activity, including instances of failed login attempts, modifications to security configurations, notifications or updates from unfamiliar sources, and unexplained logins from unexpected locations and times.
Staying secure within the long-term
In order to avoid getting hit in the long run, consider:
- Being extremely vigilant when online.
- Ensuring the security and confidentiality of your online presence by reviewing and updating your social media account settings.
- When creating an account, consider using anonymous email addresses or disposable options that allow you to maintain privacy without having to continually share personal information.
- When dealing with unsolicited communications, always exercise extreme caution and refrain from responding impulsively. This is especially true for messages that aim to prompt swift action without allowing adequate consideration of the potential consequences.
- Utilize intricate and unguessable passwords across all platforms that require them, and enable advanced two-factor authentication to bolster security.
- By subscribing to a darknet monitoring service, individuals can receive timely alerts about newly disclosed personal details on the internet’s illicit underground and potentially take proactive measures to prevent cybercriminals from exploiting the information.
The distress of having one’s personal identity compromised. This period of uncertainty may prove to be a prolonged and chaotic experience that can last for weeks or even months before a resolution is reached. What lurks in the shadows of the darknet is a constant reminder that some things are better left unseen, with no possibility of escalating to such a dire level.

